SWR2310 Series Technical Reference
Firmware revision: Rev.2.04.01
Thank you for your purchase of the Yamaha SWR2310 Series.
Please read this manual carefully, correctly installing the unit and making the proper settings before use.
Make sure to observe the warnings and cautions listed in this manual, in order to use the unit correctly and safely.
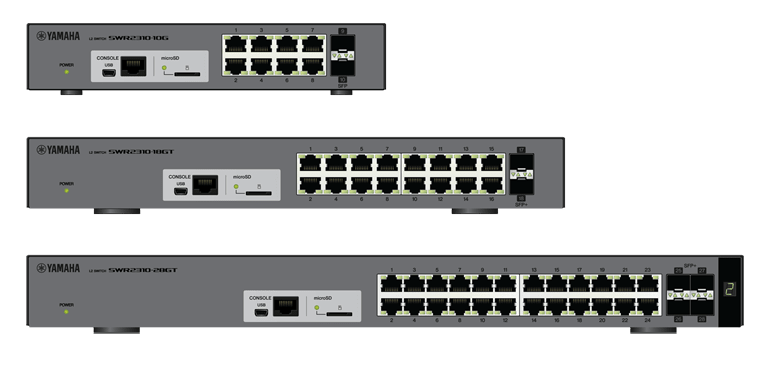
Startup guide
This explains the procedure for preparing to set up the SWR2310 Series that you purchased.
Settings for the SWR2310 Series can be made using the following four methods.
- Make settings via the Web GUI
- Make settings via commands using the CONSOLE port
- Make settings via commands using Telnet
- Make settings via commands using SSH
This document explains “Preparing to make settings via the Web GUI” and “Preparing to make settings via the CONSOLE port.”
Preparing to make settings via the Web GUI
You’ll log into the Web GUI from Yamaha LAN Monitor, so install Yamaha LAN Monitor before you proceed.
Before you log in, connect the computer to the same network.
For details on supported web browsers, refer to the Yamaha Pro Audio website.
http://www.yamaha.com/proaudio/
- Prepare the computer and other items you’ll need when making settings.
- Obtain an Enhanced Category 5 cable (CAT5e) for connecting to this unit.
- The following web browsers are recommended for use.
- Windows
- Internet Explorer 11, EDGE, Google Chrome, Mozilla FireFox
- Mac, iOS
- Apple Safari 7.0 or later
- Connect this unit to the computer via an Enhanced Category 5 cable (CAT5e).
- Power-on this unit. This unit takes approximately 70 seconds to start up.
When startup is completed, the indicator of the LAN port to which the Ethernet cable is connected will light according to the communication speed and mode. - Start Yamaha LAN Monitor.
- Select the device for which you want to make settings, and in the “Device details” view, click the Web GUI button.
When access succeeds, a dialog box asking you to enter a user name and password appears. - If you have previously specified them, enter a user name and password, and click the [Login] button.
With the factory settings, no user name or password have been specified, so you don’t need to enter a user name or password. - Subsequently, make settings as appropriate for the system in which this unit is being used.
- For details on settings via the Web GUI, refer to Help within the GUI that you accessed.
Preparing to make settings via the CONSOLE port
- Prepare the computer and other items you’ll need when making settings.
When making settings via the CONSOLE port, use a USB cable or RJ-45/DB-9 console cable.
As the USB cable for connection to the mini-USB CONSOLE port, use a USB cable that supports data transfer and is equipped with a USB Type A connector and a mini-USB Type B (5-pin) connector. Charging-only cables cannot be used.
You’ll also need terminal software for controlling the serial (COM) port of the computer.
Set the communication settings of the console terminal as follows.- Baud rate
- Data
- Parity
- Stop bit
- Flow control
: 9600 bps
: 8 bits
: none
: 1 bit
: Xon/Xoff - For the connection between the computer and this unit, use a USB cable or a RJ-45/DB-9 console cable.
- In order to use the mini-USB CONSOLE port, you must first install the USB serial driver.
- For details on how to install the USB serial driver, refer to “Yamaha Network Device USB Serial Driver Installation Guide.”
The Yamaha Network Device USB Serial Driver Installation Guide and the installer can be downloaded from the following website.
https://usa.yamaha.com/products/contents/proaudio/downloads/firmware_software/index.html?k=&c=proaudio
- Power-on this unit. This unit takes approximately 70 seconds to start up.
Immediately after startup, the serial console screen appears as follows.SWR2310-28GT BootROM Ver.1.00 Starting ............................. SWR2310-28GT Rev.2.04.01 (Thu Sep 26 17:35:20 2019) Copyright (c) 2018-2019 Yamaha Corporation. All Rights Reserved. - Log in to this unit.
In the initial state, a user name and password have not been specified, so you’ll be able to log in by pressing the “Enter” key at the user name input prompt and the password input prompt.Username: (Input the “Enter” key) Password: (Input the “Enter” key) SWR2310-28GT Rev.2.04.01 (Thu Sep 26 17:35:20 2019) Copyright (c) 2018-2019 Yamaha Corporation. All Rights Reserved. SWR2310>
- Subsequently, make settings as appropriate for the system in which this unit is being used.
- For details on settings via the serial console, refer to Command Reference.
Firmware Updates
For stable operation, we recommend that you apply the latest firmware updates, which include new functionality and bug fixes.
Please confirm your system version before applying updates.
- Use the show environment command to check the system version.
Web GUI Function
The latest firmware for this unit supports the following settings and functions.
- Detailed settings
- Interface settings
- Link aggregation
- VLAN
- MAC address table
- Routing
- DNS client
- IGMP Snooping
- Access list
- QoS
- Mail notification
- Terminal monitoring
- Management
- Unit settings
- Time settings
- Access management
- User settings
- Server settings
- External device linking
- microSD
- Dante optimization settings
- Maintenance
- Command execution (For details on the commands, refer to the Command Reference.)
- Firmware update
- CONFIG file management
- Statistical data management
- SYSLOG management
- Restart and initialization
- Web GUI language
- Unit settings
Precautions
- Do not touch the inside of ports with fingers or metallic objects, etc. Doing so might cause malfunctions.
- Do not use this unit in locations of direct sunlight (such as inside a car located in the sun), in extremely hot locations such as near a stove, in extremely cold locations, nor in locations that are excessively dusty or are subject to strong vibration. Such conditions might cause this unit’s panel to deform or internal components to malfunction, or might cause unstable operation.
- Products made of vinyl, plastic, or rubber should not be placed on this unit. Such objects might cause this unit’s panel to be discolored or damaged.
- To clean this unit, use a soft dry cloth. Do not use benzene, thinner, detergent, or a chemically treated cloth, such things might cause discoloration or damage.
- If the ambient temperature in which this unit is located undergoes extreme change (such as when the unit is moved or is subject to aggressive air-conditioning or heating), and there is a danger that condensation has formed within the unit, leave the unit unpowered for several hours to ensure that condensation has disappeared before using the unit. Using the unit when condensation is present might cause malfunctions.
- Before touching this unit, remove static charge from yourself and your clothing. Static charge might cause malfunctions.
- Do not place this unit in locations where there is a strong magnetic field. Such conditions might cause malfunctions.
- Do not connect equipment that generates noise to the same electrical power supply line as this unit. Such conditions might cause malfunctions or faulty operation.
- Do not route communication cables near power cords. High voltages might be induced, causing faulty operation.
- When using a 1000BASE-T connection, use enhanced category 5 (CAT5e) or better LAN cable.
- Do not connect any SFP module to the SFP port other than the separately sold SFP-SWRG-SX or SFP-SWRG-LX. Operation cannot be guaranteed if any other SFP module is connected.
- Do not connect any SFP module or DAC other than the separately sold SFP-SWRT-SR, SFP-SWRT-LR, SFP-SWRG-SX, SFP-SWRG-LX, DAC-SWRT-1M, DAC-SWRT-3M in the SFP+ port. Operation cannot be guaranteed if any SFP module or DAC other than the above is connected.
- Attach the dust cover to SFP ports that are not in use. Foreign objects that enter the port might cause malfunctions. Keep the dust covers in a safe place so that they will not be lost.
- SFP modules and optical fiber cables can suffer problems such as loss of accuracy caused by damage or abrasion to their connector, or dirty contacts, causing insufficient light reception or failure to link up.
- The legs (rubber feet) included with this unit are to prevent slipping. Use them when placing this unit on a table or stand that is prone to slipping.
- SWR2310 Series Technical Data (Basic Functions)
- Maintenance and operation functions
Maintenance and operation functions
- User account management
- LED control
- Using external memory
- Boot data management
- Viewing unit information
- Config management
- Remote access control
- Time management
- SNMP
- RMON
- SYSLOG
- Firmware update
- L2MS control
- Mail notification
- LLDP
- Terminal monitoring
- Performance observation
- Dante optimization setting function
- Stack function
- List of default settings
- SWR2310 Series Technical Data (Basic Functions)
- Maintenance and operation functions
- User account management
User account management
1 Function Overview
This product provides the functions shown below for managing user accounts.
- Functions for setting user information
- Functions for user authentication by user name and password
2 Definition of Terms Used
- Unnamed user
A user who does not have a user name.
If an unnamed user logs into the console or Web GUI, they can log in without specifying a user name.
- Guest privileges
Users that have guest privileges can use the Web GUI to view the device settings and status.
- Administrator privileges
Users that have administrator privileges can perform the following actions in the Web GUI.
- View and modify the settings
- Restart the device
- Initialize the device
- Update the firmware
3 Function Details
3.1 User information settings
Use the username command to specify user information.
Specify the following as user information.
- User name
- Password
- Privileges
A user to whom privileges are granted has the following differences compared to a normal user.
- Password entry is not required when executing the enable command from the console.
- When logging into the Web GUI, the user can log on with administrator privileges.
Use the password command to specify the password for unnamed users.
In the factory-set state, this is unset.
You can use the password-encryption command to encrypt the specified password.
If you want to encrypt the password, specify password-encryption enable.
Once a password has been encrypted, it will not be returned to an unencrypted text string even if you specify password-encryption disable.
Encryption applies to the passwords specified by the following commands.
- password command
- enable password command
- username command
3.2 User authentication
3.2.1 When logging in to the console
When you connect to the console, the following login prompt appears.
Username: Password:
Enter a specified user name and password to log in.
If you want to log in as an unnamed user, press the Enter key at the user name prompt to omit it, and then enter the password that was specified by the password command.
Only if you connected via the serial console, you can log in using the special password.
To log on using the special password, you must previously have specified force-password enable.
3.2.2 When logging in to the Web GUI
When you access the Web GUI, the following login form appears.

Enter a specified user name and password to log in.
If you want to log in as an unnamed user, leave the user name entry field blank, and in the password entry field, enter the password specified by the password command or the enable password command.
In this case if you enter the password specified by the password command, you will log in with Guest privileges.
If you enter the password specified by the enable password command, you will log in with Administrator privileges.
If the password that was entered matches both the password specified by the password command and by the enable password command, you will log in with Administrator privileges.
4 Related Commands
The related commands are shown below.
For details, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Set login password | password |
| Set administrator password | enable password |
| Encrypt password | password-encryption |
| Allow login using special password | force-password |
| Set user | username |
| Show user information | show users |
5 Examples of Command Execution
5.1 Specifying the password for unnamed users
Specify yamaha as the login password for unnamed users.
Specify yamaha_admin as the administrative password.
Yamaha>enable Yamaha#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Yamaha(config)#password yamaha Yamaha(config)#enable password yamaha_admin
5.2 Adding a user
Grant privilege options to the user yamaha, and assign the password yamaha_pass.
Yamaha#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Yamaha(config)#username yamaha privilege on password yamaha_pass Yamaha(config)#exit Yamaha#exit Username: yamaha Password: SWR2310-28GT Rev.2.04.01 (Thu Sep 26 17:35:20 2019) Copyright (c) 2018-2019 Yamaha Corporation. All Rights Reserved. Yamaha>enable Yamaha#
6 Points of Caution
None
7 Related Documentation
LED control
1 Function Overview
This product’s chassis features the following LEDs.
LED type
| LED type | Description |
|---|---|
| POWER LED | Indicates the power status. |
| microSD LED | Indicates the microSD card connection and usage status. |
| Port LEDs | Indicate the LAN/SFP cable connection and usage status. |
| Stack ID display LED (7SEG LED) | Displays the stack number. |
The location of each LED is shown below.
2 Definition of Terms Used
Explanation of port LED illumination
The port LED illumination used in subsequent explanations is described below.
Port LED illumination
3 Function Details
3.1 POWER LED
The POWER LED indicates the power status of this product.
The illumination pattern of the POWER LED and the corresponding statuses are as follows.
POWER LED illumination pattern and status
| POWER LED illumination pattern | Status |
|---|---|
| Unlit | Power is off. |
| Blinking green | Power is on, and system is starting up. |
| Lit green | Power is on, and system is operating normally. |
3.2 microSD LED
The microSD LED indicates the connection and usage status of the microSD card.
The illumination pattern of the microSD LED and the corresponding statuses are as follows.
microSD LED illumination pattern and status
| microSD LED illumination pattern | Status |
|---|---|
| Unlit | A microSD card is not inserted, or is unmounted, and cannot be used. |
| Blinking green | The microSD card is being accessed. |
| Lit green | A microSD card is inserted, and can be used. |
Do not remove the microSD card while this is blinking green, since the microSD card is being accessed.
3.3 Port LEDs
3.3.1 Switching between display modes
This product provides the three display modes shown below.
| Mode name | Switch user | Function overview |
|---|---|---|
| LINK/ACT mode | ✓ | The left LED of the LAN/SFP port shows the link status, and the right LED shows the connection speed. |
| STATUS mode | - | The error status of the LAN/SFP port is shown. |
| OFF mode | ✓ | The LAN/SFP port LEDs are unlit in order to decrease the power consumption. |
The display mode can be switched by setting the initial LED mode (LED mode at system startup) using the led-mode default command.
However, the STATUS mode is an automatic transition only mode and cannot be switched manually by the user.
Display mode transition follows the flow shown below.
Transition of display mode
*1 ... When the initial LED mode is LINK/ACT mode
*2 ... When the initial LED mode is OFF mode
The display mode after system boot and the display mode after error resolve depend on the default LED mode setting.
When an error is detected by the following functions, the port LED display automatically switches to STATUS mode.
- Loop detection
- SFP optical reception level monitoring
The system will not transition from STATUS mode to LINK/ACT mode or OFF mode until all errors are resolved.
3.3.2 LED display in LINK/ACT mode
The port LEDs will display as shown below in LINK/ACT mode.
- LAN/SFP port link status
- LAN/SFP port connection speed
The LED display for the link status is shown below.
LAN/SFP port link status LED display
| Linking down | Linking up | Forwarding data | |
|---|---|---|---|
| LAN port |  (unlit) |  (lit green) |  (flashing green) |
| SFP port |  (unlit) | 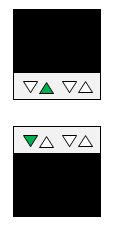 (lit green) | 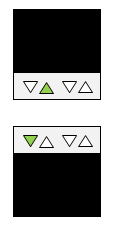 (flashing green) |
The LED display for the connection speed is shown below.
LAN/SFP port connection speed LED display
| 10M Link | 100M Link | 1000M Link | 10000M Link | |
|---|---|---|---|---|
| LAN port |  (unlit) |  (lit orange) | (lit green) | (none) |
| SFP port | (none) | (none) |  (lit green) |  (lit green) |
3.3.3 LED display in STATUS mode
In STATUS mode, the port LEDs indicate error statuses generated by the following functions of this product.
- Loop detection
- SFP optical reception level monitoring
Port LED display when an error occurs
| Normal state | An error has occurred | |
|---|---|---|
| LAN port |  (unlit) |  (flashing orange) |
| SFP port |  (unlit) |  (flashing orange) |
When this product detects an error, it forcibly switches to STATUS mode.
An error is determined by each function in the following cases.
- Loop detection
- A loop was detected and the port was blocked.
- A loop was detected and the port was shut down.
- SFP optical reception level monitoring
- The SFP optical reception level fell below the normal range.
- The SFP optical reception level exceeded the normal range.
To determine the cause of the error, you can use the show error port-led command.
In STATUS mode when an error has occurred, the LEDs will automatically switch to the default LED mode in the following states.
- All of the following errors were resolved.
- Blocked status due to loop detection was resolved.
- Shutdown status due to loop detection was resolved.
- The monitoring time has elapsed following shutdown due to loop detection.
- In a shutdown state due to loop detection, the unit linked up after the no shutdown command was executed.
- SFP optical reception level recovered.
3.3.4 LED display in OFF mode
If the default LED mode is OFF mode, the port LEDs are all unlit regardless of the link status.
Even if the default LED mode is OFF mode, the unit automatically transitions to STATUS mode when an error occurs, indicating the error status.
3.3.5 Changing the LED mode after system boot
The LED mode after system boot (the default LED mode) for this product can be specified.
The default value for the default LED mode is set to LINK/ACT mode, but can be changed using the led-mode default command.
Use the show led-mode command to check the default LED mode and the LED mode currently displayed.
When STATUS mode is cleared during error detection, the unit will switch to the default LED mode that was set.
3.3.6 Other port LED displays
Regardless of the LED mode status, the LEDs of all ports will display as follows during initialization at startup and during firmware update.
Other port LED displays
| Updating firmware | Initializing | |
|---|---|---|
| LAN port |  (flashing green) |  (lit orange) |
| SFP port |  (flashing green) |  (lit orange) |
3.4 Stack ID display LED
The stack ID display LED (7SEG LED) displays the stack ID when the stack is being configured after the countdown display at startup.
If the stack is not being configured, ’1’ is displayed.
If an error occurs during stack configuration, ’E’ indicating the error is displayed.
When the initial LED mode is in OFF mode, the stack ID display LED also turns off.
4 Related Commands
Related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Show LAN/SFP port status | show interface |
| Show setting status of loop detection | show loop-detect |
| Set default LED mode | led-mode default |
| Show LED mode | show led-mode |
| Show port error status | show error port-led |
5 Examples of Command Execution
5.1 Check LAN/SFP port status
Use the show interface command to check the LAN/SFP port status.
Yamaha#show interface
show interface
Interface port1.1
Link is UP
Hardware is Ethernet
HW addr: ac44.f23d.0b2c
ifIndex 5001, MRU 1522
Speed-Duplex: auto(configured), 1000-full(current)
Auto MDI/MDIX: on
Vlan info :
Switchport mode : access
Ingress filter : enable
Acceptable frame types : all
Default Vlan : 1
Configured Vlans : 1
Interface counter:
input packets : 317111
bytes : 31387581
multicast packets: 317074
output packets : 162694
bytes : 220469213
multicast packets: 162310
broadcast packets: 149
drop packets : 0
:
(Information for all LAN/SFP ports is shown)
5.2 Check LAN/SFP port loop detection status
Check the LAN/SFP port loop status.
Yamaha#show loop-detect loop-detect: Enable loop-detect: Enable port loop-detect port-blocking status ------------------------------------------------------- port1.1 enable enable Normal port1.2 enable enable Normal port1.3 enable enable Normal port1.4 enable enable Normal port1.5 enable enable Normal port1.6 enable enable Normal port1.7 enable enable Normal port1.8 enable enable Normal port1.9 enable enable Normal port1.10 enable enable Normal ------------------------------------------------------- (*): Indicates that the feature is enabled.
5.3 Set the default LED mode
Set the default LED mode to OFF mode.
Yamaha#configure terminal Yamaha(config)#led-mode default off … (Set default LED mode) Yamaha(config)#exit YamahaW#show led-mode … (Show LED mode) default mode : off current mode : off
- SWR2310 Series Technical Data (Basic Functions)
- Maintenance and operation functions
- Using external memory
Using external memory
1 Function Overview
This product provides the following functions using external memory.
- SD card boot (firmware, config)
- The system can be started using a firmware file and config file from an SD card.
- Firmware update
- This unit’s firmware can be updated by loading a firmware file from an SD card.
- Saving and copying a config file
- The running-config that is currently running on the system can be saved to an SD card, and config files can be copied from the SD card to the unit’s flash ROM or from the unit’s flash ROM to the SD card.
- Saving a log file
- By executing the save logging command you can back up the log file to an SD card.
- Saving technical support information
- Technical support information (the result of executing the show tech-support command) can be saved to an SD card.
- Saving statistical information
- Observations of resource information and traffic information are backed up regularly.
- This statistical information can be saved as a CSV format file.
- Backing up and restoring system information
- System information (including configurations) can be backed up to an SD card.
- Backed up system information can be restored into the unit’s flash ROM.
2 Definition of Terms Used
None
3 Function Details
3.1 External memory that can be used
Requirements for external memory that can be used are as follows.
- Card type: microSD card / microSDHC card
- File format: FAT16/FAT32
3.2 Folder structure
The SD card must contain the following folder structure.
Device name +-- firmware Firmware file storage folder | | +-- startup-config Startup config storage folder | | +-- log SYSLOG storage folder | | +-- techsupport Technical support information storage folder | | +-- data System-wide folder | | +-- backup-system System backup folder
3.3 Mounting and unmounting the SD card
If the SD card is inserted when starting up or after startup, it is automatically mounted and becomes available.
To prevent loss of files, execute the unmount sd command or execute the unmount operation from the Web GUI before removing the SD card.
If the SD card is unmounted, it cannot be used.
If you want to once again use the SD card after executing the unmount sd command, you must execute the following.
- Remove and reinsert the SD card
- Execute the mount sd command
- Execute mount from the Web GUI
3.4 SD card boot (firmware, config)
The system can be started using a firmware file and config file from an SD card.
In order to use SD card boot, the following conditions must be satisfied.
- SD card using a firmware file
- The SD card is connected when the system starts up.
- The following files exist in the SD card.
- /swr2310/firmware/swr2310.bin
- boot prioritize sd enable is specified.
* With the factory settings, boot prioritize sd enable is specified.
- SD card boot using a config file
- The SD card is connected when the system starts up.
- The various files exist in the following directory of the SD card.
- /swr2310/startup-config
- startup-config select sd is specified.
* With the factory settings, startup-config select sd is specified.
You can use the show environment command to check whether SD card boot was successful.
- In the case of SD card boot using a firmware file, “Startup Firmware” will indicate “exec(SD).”
- In the case of SD card boot using a config file, “Startup Configuration” will indicate “config(SD).”
In the case of SD card boot using a config file, executing the write and copy running-config startup-config commands will update the config file on the SD card.
If SD card boot using a config file fails, startup config #0 is loaded.
Also, the following message is shown in the console and in SYSLOG.
Loading config0 because can't read config in SD card.
3.5 Firmware update
This unit’s firmware can be updated by loading a firmware file from an SD card.
In order to use this function, the following conditions apply.
- The following files exist in the SD card.
- /swr2310/firmware/swr2310.bin
If the above file exists on the inserted SD card, executing the firmware-update sd execute command updates the firmware in flash ROM using the firmware in the SD card.
When the firmware-update sd execute command is executed, the user will be asked whether to maintain the mounted state of the SD card when the firmware file has finished loading. Remove the SD card as necessary after it is unmounted.
Note that if the SD card is left inserted during the automatic reboot in conjunction with firmware update, the system will start up with the firmware file on the SD card.
The firmware of the stack slave can be updated by executing the firmware-update sd execute command from the stack master during stack configuration.
3.6 Saving and copying a config file
The running-config that is currently running on the system can be saved to the SD card. ( copy running-config startup-config command, write command)
You can copy the config file from the SD card to internal flash ROM, or from internal flash ROM to the SD card. ( copy startup-config command)
You can erase or show the startup-config in the SD card. ( erase startup-config command, show startup-config command)
The following folder in the SD card is affected.
- /swr2310/startup-config
3.7 Saving a log file
By executing the save logging command you can back up the log file to an SD card.
The logging backup sd command enables SYSLOG backup to the SD card.
If SYSLOG backup to the SD card is enabled, executing the save logging command will save the following log file with its save date to the SD card.
- /swr2310/log/YYYYMMDD_log.txt *YYYYMMDD=year month day
The log files in the SD card cannot be viewed or erased.
3.8 Saving technical support information
Technical support information (the result of executing the show tech-support command) can be saved to an SD card.
Executing the copy tech-support sd command will save the following technical support information file with its save date to the SD card.
- /swr2310/techsupport/YYYYMMDDHHMMSS_techsupport.txt *YYYYMMDD=year month day, HHMMSS=hours minutes seconds
The technical support information files in the SD card cannot be viewed or erased.
If the copy tech-support sd command is executed from the stack master during stack configuration, a file containing the technical support information of the stack slave is saved.
3.9 Saving statistical information
Observations of resource information and traffic information are backed up regularly.
To enable backup of statistical information to the SD card, you must make settings via the Web GUI in [Administration]–[Maintenance]–[Statistical information management].
This statistical information for the observed data can be saved via the Web GUI as a CSV format file.
3.10 Backup and restore of system information
This unit’s system information can be backed up to an SD card, and the backed up system information can be restored to a desired switch.
With an SD card connected to this unit, executing the backup system command will create a system information backup in the following folder.
- /swr2310/backup-system
If the file swr2310.bin exists in the /swr2310/firmware/ folder when backup is executed, it is backed up as a firmware file.
To restore the backed up system information, connect the SD card containing the system information backup to the desired switch, and execute the restore system command.
If the firmware file was backed up, a firmware update is also performed using that file.
When restore is completed, the system will restart.
The system information backup contains the following.
- Settings associated with the unit
- startup-config #0 - #4 and associated information
- startup-config select command setting values
- boot prioritize sd command setting values
- Firmware file
* Only if the specified folder of the SD card contained a firmware file when the backup was executed.
For this reason, when replacing a unit due to malfunction or another reason, the replacement unit can be returned to the same condition as the original unit simply by restoring the backed up system information.
Do not edit or delete the backed up system information.
4. List of related commands
The related commands are shown below.
For details, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Mount SD card | mount sd |
| Unmount SD card | unmount sd |
| Set SD card backup of log | logging backup sd |
| Back up log | save logging |
| Save technical support information | copy tech-support sd |
| Save running config | copy running-config startup-config |
| Save running config | write |
| Copy startup config | copy startup-config |
| Erase startup config | erase startup-config |
| Show startup config | show startup-config |
| Back up system information | backup system |
| Restore system information | restore system |
5 Examples of Command Execution
5.1 Unmount SD card
Unmount the SD card.
Yamaha>unmount sd
5.2 Mount SD card
Mount the SD card.
Yamaha>mount sd
5.3 Back up log file
By executing the save logging command you can back up the log file to the SD card as well.
Yamaha(config)#logging backup sd enable... (Enable SD card backup of log) Yamaha(config)#exit Yamaha#save logging ... (Back up log)
5.4 Saving technical support information
Save technical support information.
Yamaha#copy tech-support sd
6 Points of Caution
None
7 Related Documentation
- SWR2310 Series Technical Data (Basic Functions)
- Maintenance and operation functions
- Boot data management
Boot data management
1 Function Overview
As system boot information, this product manages the information shown in the table below.
System boot information: items managed
| Management item | Description |
|---|---|
| System boot time | Time that the system booted up |
| Run-time firmware update | Firmware version currently running, and date generated |
| Firmware information for previous startup | Version and generated date of the firmware for the previous startup |
| Reason for boot | Reason why the system booted up. The following reasons for boot are recorded:
|
This product stores the current boot information and information on the previous four boots, for a total of five boot records.
2 Related Commands
The related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Show boot information | show boot |
| Clear boot information | clear boot list |
3 Examples of Command Execution
3.1 Show boot information
This shows the current boot information.
Yamaha>show boot 0 Running EXEC: SWR2310 Rev.2.04.01 (Thu Sep 26 17:35:20 2019) Previous EXEC: SWR2310 Rev.2.04.01 (Thu Sep 26 17:35:20 2019) Restart by reload command
This shows a list of the boot history.
Yamaha>show boot list No. Date Time Info --- ---------- -------- ------------------------------------------------- 0 2018/03/15 09:50:29 Restart by reload command 1 2018/03/14 20:24:40 Power-on boot --- ---------- -------- -------------------------------------------------
3.2 Clear boot information
This clears the boot information.
Yamaha#clear boot list
4 Points of Caution
If creation of the system information storage area at startup fails, the following message is output to the serial console screen.
At this time, all logs saved in the product are deleted.
- Message list
Message Output conditions Failed to create partition. When the system information storage area could not be created Succeeded to re-create partition. When the system information storage area was successfully recreated Boot sequence is interrupted by partition creation failure. When the system information storage area could not be created and the system could not start up
5 Related Documentation
None.
- SWR2310 Series Technical Data (Basic Functions)
- Maintenance and operation functions
- Viewing unit information
Viewing unit information
1 Function Overview
1.1 Show unit information via command
This product provides the display functions shown in the table below.
List of unit information display items
| Display item | Explanation | Commands |
|---|---|---|
| Inventory information | Shows information for this product, such as inventory name, model number, and product ID. If an SFP module has been inserted, the inventory information for the module will also be shown. | show inventory |
| Operating information | Shows the operating information for this product’s programs, such as running software information, CPU usage, memory usage, boot time. | show environment |
| Disk usage status | Shows the usage status of the disks used in the system. | show diskusage |
| Technical support information | Outputs all data relevant to the operating state that might be necessary as analytic information for technical support. For stack-compatible models, stack slave technical support information is also output when executed on the stack master in stack configuration. | show tech-support |
1.2 Remote retrieval of technical support information
A TFTP client installed on a PC or other remote terminal can be used to obtain the technical support information (the output results of “show tech-support”) from this product.
In order to operate this product’s TFTP server, use the steps shown below to set up a network environment that allows remote access.
- Decide on the VLAN that will be used for maintenance.
- Set the IPv4 address on the maintenance VLAN. Use the “ip address” command for this setting.
- Permit access from the maintenance VLAN to the TFTP server. If you want to specify a different VLAN than specified by the “management interface” command, use the “tftp-server interface” command to specify it.
When using a TFTP client, specify “techinfo” for the remote path from which technical support information is obtained.
1.3 Saving technical support information to external memory
You can use the copy tech-support sd command to save this product’s technical support information (the output result of “show tech-support”) on an SD card.
Before executing this command, you must insert an SD card.
The information is saved in the SD card with the following file name.
- /swr2310/techsupport/YYYYMMDDHHMMSS_techsupport.txt
* YYYYMMDDHHMMSS … year, month, day, hour, minute, and second that the command was executed
2 Related Commands
The related commands are shown below.
For details, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Show inventory information | show inventory |
| Show operating information | show environment |
| Disk usage status | show disk-usage |
| Show technical support information | show tech-support |
| Save technical support information | copy tech-support sd |
3 Examples of Command Execution
3.1 Show inventory information
This checks the following inventory information for this unit and for the SFP modules.
- Name (NAME)
- Description (DESCR)
- Vendor Name (Vendor)
- Product ID (PID)
- Version ID (VID)
- Serial number (SN)
Yamaha>show inventory NAME: L2 switch DESCR: SWR2310-10G Vendor: Yamaha PID: SWR2310-10G VID: 0000 SN: S00000000 NAME: SFP1 DESCR: 1000BASE-LX Vendor: YAMAHA PID: SFP-SWRG-LX VID: 0000 SN: 00000000000 NAME: SFP2 DESCR: 1000BASE-SX Vendor: YAMAHA PID: SFP-SWRG-SX VID: 0000 SN: 00000000000
3.2 Show operating information
This checks the system operating information (as shown below).
- Boot version
- Firmware revision
- Serial number
- MAC address
- CPU usage ratio
- Memory usage ratio
- Firmware file
- Startup config file
- Serial baud rate
- Boot time
- Current time
- Elapsed time from boot
Yamaha>show environment
SWR2310-10G BootROM Ver.1.00
SWR2310-10G Rev.2.04.00 (Mon Jul 8 00:00:00 2019)
main=SWR2310-10G ver=00 serial=S00000000 MAC-Address=ac44.f200.0000
CPU: 7%(5sec) 8%(1min) 8%(5min) Memory: 18% used
Startup firmware: exec0
Startup Configuration file: config0
selected file: config0
Serial Baudrate: 9600
Boot time: 2019/07/09 11:13:44 +09:00
Current time: 2019/07/10 16:19:43 +09:00
Elapsed time from boot: 1days 05:06:04
Yamaha>3.3 Show technical support information
The following commands show information that is useful for technical support.
- show running-config
- show startup-config
- show environment
- show disk-usage
- show inventory
- show boot all
- show logging
- show process
- show users
- show interface
- show frame-counter
- show vlan brief
- show spanning-tree mst detail
- show etherchannel status detail
- show loop-detect
- show mac-address-table
- show l2ms detail
- show qos queue-counters
- show ddm status
- show errdisable
- show auth status
- show auth supplicant
- show error port-led
- show ip interface brief
- show ipv6 interface brief
- show ip route
- show ip route database
- show ipv6 route
- show ipv6 route database
- show arp
- show ipv6 neighbors
- show ip igmp snooping groups
- show ip igmp snooping interface
Yamaha#show tech-support # # Information for Yamaha Technical Support # *** show running-config *** ! dns-client enable ! ! ... # # End of Information for Yamaha Technical Support #
4 Points of Caution
None
5 Related Documentation
None
Config management
1 Function Overview
This product uses the following config information to maintain the value of settings.
Table 1.1 Config types
| Config type | Description | User operations possible |
|---|---|---|
| Running config (running-config) | The currently-running setting values. Managed in RAM. | View / Save to startup config |
| Startup config (startup-config) | Saved setting values. Two config files are maintained in ROM, and one on the SD card. When the system starts up, either the config from ROM that is selected by the startup-config select command or the config from the SD card is loaded. The one config on the SD card is maintained in the “/swr2310/startup-config” folder. | View / delete / copy |
| Default config (default-config) | The default setting values. Managed in ROM. | No operations possible |
2 Definition of Terms Used
None
3 Function Details
3.1 Running config
running-config is the settings that are currently operating; since it is maintained in RAM, it is destroyed at reboot.
On this product, commands executed in configuration mode are immediately applied to running-config, and the unit operates according to these settings.
The contents of running-config can be viewed by using the show running-config command.
3.2 Startup config
startup-config is settings that are saved in flash ROM or on the SD card, and the contents are preserved through reboot.
When this product is started, the settings of startup-config are applied as the initial settings of running-config.
This product can maintain two startup configs in flash ROM and one startup config on the SD card.
The startup-config data in the internal flash ROM is managed with an ID of 0–1, and the config on the SD card is managed with the keyword “sd”.
To specify which of the five types of config in the unit’s flash ROM are used, use the startup-config select command.
- By default, sd is used.
- When executing the startup-config select command, the user selects whether to restart. If you don’t restart, no change occurs in the command setting.
If you choose to restart, the unit restarts with the startup-config of the ID specified by the user’s command.
For easier management, you can use the startup-config description command to give each config a Description (explanatory text).
If you attempt to start up in a state where startup-config does not exist, such as after executing the cold start command, the default-config is automatically applied.
The running-config settings can be saved in startup-config by the copy running-config startup-config command or the write command.
The contents of startup-config can be erased by the erase startup-config command, viewed by the show startup-config command, and copied by the copy startup-config command.
3.3 Default config
default-config contains settings saved in internal flash ROM that are needed for this product to operate minimally as a switch. Like startup-config, the contents are preserved even after a restart.
The factory settings are maintained as default-config.
If startup-config does not exist when the system starts, default-config is copied to startup-config, and applied to running-config.
The contents of default-config cannot be viewed.
3.4 Deciding the config file at startup
The following describes the flow for deciding the config file used when this product starts up.
- The startup-config select command setting is referenced to determine the startup-config that will be used.
If the startup-config select command has specified sd, and an SD card on which startup-config is saved is not inserted, then startup-config #0 is selected.
- If the determined startup-config exists, the corresponding data is applied as running-config in RAM.
If the startup-config determined according to the value of the startup-config select command does not exist in ROM, then default-config is applied to RAM.
If startup using the config in the SD card fails, the following message is shown in the console and in SYSLOG.
Loading config0 because can't read config in SD card.
3.5 Controlling the config file via TFTP
If this product’s TFTP server function is enabled, a TFTP client installed on a PC or other remote terminal can be used to perform the following.
- Acquire the currently running running-config and startup-config
- Apply a previously prepared settings file as startup-config
In order for the TFTP server to function correctly, an IP address must be specified for the VLAN.
Acquisition and settings of the settings file from the remote terminal is done in binary mode, specifying the following as the remote path for acquiring or sending the settings file.
Table 1.2 Remote path for applicable files
| Settings file to be acquired/set | Remote path for acquisition/transmission |
|---|---|
| running-config | config |
| startup-config # 0 | config0 |
| startup-config # 1 | config1 |
- The startup-config settings are applied as running-config when the system restarts.
4 Related Commands
The related commands are shown below.
For details, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Save running config | copy running-config startup-config |
| Save running config | write |
| Copy startup config | copy startup-config |
| Erase startup config | erase startup-config |
| Show startup config | show startup-config |
| Select startup config | startup-config select |
| Set description for startup config | startup-config description |
5 Examples of Command Execution
5.1 Select startup config
Select startup-config #1 and restart.
Yamaha#startup-config description 1 TEST ... (Assign the description “TEST” to startup-config #1) Yamaha#startup-config select 1 ... (Select startup-config #1) reboot system? (y/n): y ... (Restart)
5.2 Save running config
Save running-config.
Yamaha#copy running-config startup-config Suceeded to write configuration Yamaha#
5.3 Copy startup config
Copy startup-config #1 to the SD card.
Yamaha#copy startup-config 1 sd ... (Copy startup-config #1 to SD card) Suceeded to copy configuration Yamaha#show startup-config sd ... (Show startup-config of SD card) ! ! Last Modified: Tue Mar 13 17:34:02 JST 2018 ! dns-client enable ! interface port1.1 switchport switchport mode access no shutdown ! ...
5.4 Erase startup config
Erase startup-config from the SD card.
Yamaha#erase startup-config sd ... (Erase startup-config of SD card) Suceeded to erase configuration Yamaha#
6 Points of Caution
None
7 Related Documentation
- SWR2310 Series Technical Data (Basic Functions)
- Maintenance and operation functions
- Remote access control
Remote access control
1 Function Overview
This product lets you restrict access to the following applications that implement network services.
- Telnet server
- SSH server
- HTTP server / secure HTTP server
- TFTP server
2 Definition of Terms Used
None
3 Function Details
The following four functions are provided to limit access to network services.
- Control whether to leave the service in question running in the background on the system (start/stop control)
- Change reception port number
- Limit access destinations for services currently running
- Limit the source IP addresses that can access services currently running
The following functions that correspond to each network service are shown in the table below.
Network service access control
| Network service | Start/stop control | Change reception port number | Limit access destinations | Limit access sources |
|---|---|---|---|---|
| Telnet server | ✓ | ✓ | ✓ | ✓ |
| SSH server | ✓ | ✓ | ✓ | ✓ |
| HTTP server Secure HTTP server | ✓ | ✓ | ✓ | ✓ |
| TFTP server | ✓ | ✓ | ✓ | - |
- Multiple instances of a network service cannot be started.
If the start control is applied to the same service that is currently running, the service will restart. Any connected sessions will be disconnected as a result.
- Limiting access destinations for network services is done for the VLAN interface.
- Limiting access sources for network services is done by specifying access source IP addresses and whether to permit or deny access.
- The default settings for the network services are shown in the table below.
Network service Start/stop status Reception port number Access destination restriction Access source restriction Telnet server run 23 Only default management VLAN (VLAN #1) permitted Allow all SSH server stop 22 Only default management VLAN (VLAN #1) permitted Allow all HTTP server run 80 Only default management VLAN (VLAN #1) permitted Allow all Secure HTTP server stop 443 TFTP server stop 69 Only default management VLAN (VLAN #1) permitted Allow all
4 Related Commands
Related commands are shown below.
For details, refer to the Command Reference.
List of related commands
| Network service | Operations | Operating commands |
|---|---|---|
| Common | Management VLAN | management interface |
| Telnet server | Start/stop | telnet-server |
| Change reception port number | telnet-server enable (use argument to specify port number) | |
| Access control | telnet-server interface | |
| IP address access control | telnet-server access | |
| Show settings | show telnet-server | |
| SSH server | Start/stop | ssh-server |
| Change reception port number | ssh-server enable (use argument to specify port number) | |
| Access control | ssh-server interface | |
| IP address access control | ssh-server access | |
| Check whether client is alive | ssh-server client alive | |
| Show settings | show ssh-server | |
| Generate host key | ssh-server host key generate | |
| Clear host key | clear ssh-server host key | |
| Show public key | show ssh-server host key | |
| HTTP server | Start/stop HTTP server | http-server |
| Change HTTP server reception port number | http-server enable (use argument to specify port number) | |
| Start/stop secure HTTP server | http-server secure | |
| Change secure HTTP server reception port number | http-server secure enable (use argument to specify port number) | |
| Access control | http-server interface | |
| IP address access control | http-server access | |
| Show settings | show http-server | |
| TFTP server | Start/stop | tftp-server |
| Access control | tftp-server interface |
5 Examples of Command Execution
5.1 Telnet server access control
This example restricts access to the Telnet server.
Change the Telnet server’s reception port to 1024.
Change the management VLAN to VLAN #1000 and allow access. Access from other than the management VLAN is denied.
Access to the Telnet server is allowed only for a client from 192.168.100.1.
If you specify telnet-server access, access from IP addresses that do not meet the conditions is denied.
Yamaha(config)#telnet-server enable 1024 ... (Change reception port to 1024, and restart Telnet server)
Yamaha(config)#management interface vlan1000 ... (Permit access for VLAN #1000 as the management VLAN)
Yamaha(config)#telnet-server access permit 192.168.100.1 ... (Permit access only from 192.168.100.1)
Yamaha(config)#end
Yamaha#show telnet-server ... (Check state of settings)
Service:Enable
Port:1024
Management interface(vlan):1000
Interface(vlan):None
Access:
permit 192.168.100.15.2 SSH server access control
This example restricts access to the SSH server.
Generate the SSH server host key.
Register a user name and password.
Login from an SSH client is possible only for a registered user and password.
Change the SSH server’s reception port to 1024.
Change the management VLAN to VLAN #1000 and allow access for VLAN #2.
This allows access only from the management VLAN VLAN #1000 and from VLAN #2.
If you specify ssh-server access, access from IP addresses that do not meet the conditions is denied.
Yamaha#ssh-server host key generate ... (Create host key) Yamaha#show ssh-server host key ... (Check contents of key) ssh-dss (Omitted) ssh-rsa (Omitted) Yamaha# Yamaha#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Yamaha(config)#username user1 password pw1 ... (Register a user name and password.) Yamaha(config)#ssh-server enable 1024 ... (Change reception port to 1024, and restart SSH server) Yamaha(config)#management interface vlan1000 ... (Permit access for #1000 as the management VLAN) Yamaha(config)#ssh-server interface vlan2 ... (Permit access for VLAN #2) Yamaha(config)#end Yamaha#show ssh-serverr ... (Check state of settings) Service:Enable Port:1024 Hostkey:Generated Client alive :Disable Management interface(vlan):1000 Interface(vlan):2 Access:None Yamaha#
5.3 HTTP server access restriction
This example makes it possible to restrict HTTP server access.
The HTTP server reception port is changed to 8000, and access is permitted from VLAN #2.
This allows access only from the default management VLAN VLAN #1 and from VLAN #2.
Access to the HTTP server is allowed only for a client from 192.168.100.1.
If you specify http-server access, access from IP addresses that do not meet the conditions is denied.
Yamaha(config)#http-server enable 8000 ... (Change reception port to 8000, and restart HTTP server)
Yamaha(config)#http-server interface vlan2 ... (Permit access for VLAN #2)
Yamaha(config)#http-server access permit 192.168.100.1 ... (Permit access only from 192.168.100.1)
Yamaha(config)#end
Yamaha#show http-server ... (Check state of settings)
HTTP :Enable(8000)
HTTPS:Disable
Management interface(vlan):1
Interface(vlan):2
Access:
permit 192.168.100.15.4 TFTP server access restriction
This example restricts TFTP server access.
The TFTP server reception port is changed to 2048, and access is permitted from VLAN #10.
Allow access only from the default management VLAN VLAN #1 and from VLAN #10.
Yamaha(config)#tftp-server enable 2048 ... (Change reception port to 2048, and restart TFTP server) Yamaha(config)#tftp-server interface vlan10 ... (Permit access for VLAN #10)
6 Points of Caution
None
7 Related Documentation
Time management
1 Function Overview
This product provides the functions shown below for managing the date and time.
- Manual (user-configured) date/time information setting function
- Automatic date/time setting information function via network
- Time zone setting function
Note that a function to set summertime (DST: Daylight Saving Time) is not provided.
2 Definition of Terms Used
- UTC (Coordinated Universal Time)
This is an official time used when recording worldwide times.
UTC is used as a basis to determine standard time in all countries around the world.
For instance, Japan (JST, or Japan standard time) is nine hours ahead of Coordinated Universal Time, and is thus shown as “+0900 (JST)”.
- SNTP (Simple Network Time Protocol)
This is a simple protocol to correct clocks by using SNTP packets.
This protocol is defined in RFC4330.
3 Function Details
3.1 Manually setting the date and time
Use the clock set command to directly input the time.
3.2 Automatically setting the date and time
Date and time information is collected from a specified time server, and set in this product.
Defined in RFC4330, SNTP (Simple Network Time Protocol) is used as a communication protocol.
Up to two time servers can be specified, which can be either an IPv4 address, an IPv6 address, or an FQDN (Fully Qualified Domain Name).
Port number 123 is used for the SNTP client. (This setting cannot be changed by the user.)
Use the ntpdate command to choose from the following two methods of automatically setting the date/time.
- One-shot update (a function to update when a command is inputted)
- Interval update (a function to update in a 1–24-hour cycle from command input)
If time synchronization is performed when two time servers have been specified, queries are performed in the order of NTP server 1 and then NTP server 2 shown by the show ntpdate command.
The query to NTP server 2 is performed only if synchronization with NTP server 1 fails.
By default, one hour is specified as the update interval cycle.
However, when the default time cannot be set right after booting up the system, the time server will be queried in a one-minute cycle, regardless of the interval cycle time.
Synchronization with the time server operates with one sampling (the frequency of replies from the server) and with a timeout of 1 second.
Synchronization is blocked during command execution, and an error message is outputted if a timeout occurs.
3.3 Time zone settings
In order to manage the time for the region considered as the “base of daily life”, the “clock timezone” command is used to manage the time zone of the users, and reflect this into the time.
The time zone can be set in ±1 hour increments for Coordinated Universal Time (UTC), from -12 hours to +13 hours.
The default time zone value for this product is +9.0.
4 Related Commands
Related commands are shown below.
For details, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Set clock manually | clock set |
| Set time zone | clock timezone |
| Show current time | show clock |
| Set NTP server | ntpdate server |
| Synchronize time from NTP server (one-shot update) | ntpdate oneshot |
| Synchronize time from NTP server (update interval) | ntpdate interval |
| Show NTP server time synchronization settings | show ntpdate |
5 Examples of Command Execution
5.1 Manually setting the time
In this example, the time zone is set to JST, and the current time is set to 2014.01.21 15:50:59.
Yamaha#configure terminal Yamaha(config)#clock timezone JST … (Set time zone) Yamaha(config)#exit Yamaha#clock set 15:50:59 Jan 21 2014 … (Set time) Yamaha#show clock … (Show current time) 15:50:59 JST Tue Jan 21 2014
5.2 Automatically setting the time
In this example, the time zone is set to +9.00, and the local 192.168.1.1 and ntp.nict.jp are specified as the NTP servers.
Also, the update cycle with the NTP server is changed to once per 24 hours.
Yamaha#configure terminal Yamaha(config)#clock timezone +9:00 … (Set time zone) Yamaha(config)#ntpdate server ipv4 192.168.1.1 … (Set NTP server) Yamaha(config)#ntpdate server name ntp.nict.jp … (Set NTP server) Yamaha(config)#ntpdate interval 24 … (Set 24 hours as the update interval for synchronizing with NTP server) Yamaha(config)#exit Yamaha#show clock … (Show current time) 10:03:20 +9:00 Mon Dec 12 2016 Yamaha#show ntpdate … (Show NTP time synchronization settings) NTP server 1 : 192.168.100.1 NTP server 2 : ntp.nict.jp adjust time : Mon Dec 12 10:03:15 2016 + interval 24 hours sync server : 192.168.1.1
6 Points of Caution
None
7 Related Documentation
SNMP
1 Function Overview
Setting SNMP (Simple Network Management Protocol) makes it possible to monitor and change network management information for SNMP management software.
In this instance, this product will operate as an SNMP agent.
This product supports communication using SNMPv1, SNMPv2c, and SNMPv3. As an MIB (Management Information Base), it is also compatible with RFC1213 (MIB-II) and with a private MIB (yamahaSW).
SNMPv1 and SNMPv2 notifies the recipient of the group name (called a “community”), and communicates only with hosts that belong to that community. In this instance, different community names can be given for the two access modes, read-only and read-write.
In this sense, community names function as a kind of password; but since community names are sent over a network using plain text, they carry inherent security risks. The use of SNMPv3 is recommended when more secure communications are required.
SNMPv3 offers communication content authentication and encryption. SNMPv3 does away with the concept of community and instead uses security models called “USM” (User-based Security Model) and “VACM” (View-based Access Control Model). These models provide a higher level of security.
SNMP messages that notify the status of this product are called “traps.” This product transmits standard SNMP traps. In SNMPv1, trap requests that do not ask for an answer with the confirmation of receipt from the recipient are specified as the notification message format. However, with SNMPv2c and SNMPv3, either an “inform” request asking for an answer from the recipient, or a trap request can be selected.
Since this product does not specifically determine a default value for the read-only and community trap names used in SNMPv1 and SNMPv2c, you can specify a community name as appropriate. However, as described above, the community name is sent over the network in plaintext, so be careful to never use a login password or administrator password as the community name.
By default, no access is possible in each SNMP version. The transmission host for the trap is not set, so traps will not be sent anywhere.
2 Definition of Terms Used
None
3 Function Details
The main characteristics of each SNMP version and the router setting policies are explained below.
See “5 Examples of Command Execution” later in this text for specific examples of settings.
3.1 SNMPv1
This is authentication between the SNMP manager and agent by using community names.
The controlling device (this product) is divided and managed by zones called “communities”.
- Accessing the MIB objects
Use the snmp-server community command to permit access using the community name that was set.
Access is possible from a VLAN interface whose IP address has been specified.
- SNMP traps
SNMP traps allow for the status of this product to be sent to the hosts that are configured with the snmp-server host command.
The snmp-server enable trap command sets what kind of trap is transmitted.
3.2 SNMPv2c
As with SNMPv1, this performs authentication between the SNMP manager and agent by using community names.
The snmp-server community command sets the community name used when accessing via SNMPv2c.
The “GetBulk” and “Inform” requests are also now supported from this version.
These requests are used to efficiently retrieve multiple MIB objects, and to confirm replies to notification packets sent from this product.
- Accessing the MIB objects
Use the snmp-server community command to permit access using the community name that was set.
Access is possible from a VLAN interface whose IP address has been specified.
- SNMP traps
SNMP traps allow for the status of this product to be sent to the hosts that are configured with the snmp-server host command.
Also, the settings of this command can be used to select whether the transmitted message format is a trap or inform request.
Inform requests are used to request confirmation of reply to the recipient.
3.3 SNMPv3
In addition to all of the functions offered in SNMPv2, SNMPv3 offers more robust security functions.
SNMP packets transmitted across the network are authenticated and encrypted, protecting the SNMP packets from eavesdropping, spoofing, falsification, replay attacks and so on, by offering security-related functionality that could not be realized in SNMPv1 and v2C in regard to community names and IP addresses of SNMP managers.
Security
SNMPv3 offers the following security functions.
- USM (User-based Security Model)
USM is a model for maintaining security at the message level. It offers authentication and encryption based on shared key cryptography, and prevents falsification of the message stream.
- Security level
The security level can be specified using the parameter settings for the group to which the user belongs.
The security level combines authentication and encryption, and is classified as shown below.
- noAuthNoPriv: no authentication and encryption
- AuthNoPriv: authentication only
- AuthPriv: authentication and encryption
- User authentication
For authentication, HMAC is used in the procedure to authenticate the integrity (whether data has been falsified or not) and the source.
A hash is used in the authentication key to confirm whether the message has been falsified, and whether the sender is the user themselves.
Both HMAC-MD5-96 and HMAC-SHA-96 are supported as hash algorithms.
- Encryption
With SNMPv3, SNMP messages are encrypted for the purpose of preventing leakage of managed information.
Both the DES-CBC and AES128-CFB encryption schemes are supported.
The user and membership group name, user authentication method and encryption scheme, as well as the password can be set with the snmp-server user command.
The necessary authentication and encryption settings can be made according to the security level specified in the group settings.
- Security level
- VACM (View-based Access Control Model)
VACM is a model for controlling access to SNMP messages.
- Group
With VACM, the access policies mentioned below are defined per group, not per user.
Use the group option of the snmp-server user command to set the group(s) that the user will belong to. The MIB views set here that are accessible to the specified groups can be configured.
- MIB view
With SNMPv3, a collection of accessible MIB objects can be defined for each group. When defined, the collection of MIB objects is called the “MIB view”. The “MIB view” is expressed as a collected view sub-tree that shows the object ID tree.
Use the snmp-server view command to configure the MIB view. Whether the MIB view should be included or excluded in each view sub-tree can be selected.
- Access policies
With VACM, set the MIB view that will permit reading and writing for each group.
Use the snmp-server group command to set the group name, security level, and MIB view.
The MIB view will be the view that was configured using the snmp-server view command.
- Group
SNMP traps
SNMP traps allow for the status of this product to be sent to the hosts that are configured with the snmp-server host command.
In order to transmit a trap, the snmp-server user command must first be used to configure the user.
Also, the settings of this command can be used to select whether the transmitted message format is a trap or inform request.
Inform requests are used to request confirmation of reply to the recipient.
3.4 Private MIB
This product supports yamahaSW, which is a proprietary private MIB for switch management.
This private MIB allows the obtaining of information for Yamaha’s proprietary functions, and for more detailed information about the switch.
Refer to the following SNMP MIB Reference for information on private MIBs that are supported, and on how to get them.
4 Related Commands
Related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Set host that receives SNMP notifications | snmp-server host |
| Set notification type to transmit | snmp-server enable trap |
| Set system contact | snmp-server contact |
| Set system location | snmp-server location |
| Set SNMP community | snmp-server community |
| Set SNMP view | snmp-server view |
| Set SNMP group | snmp-server group |
| Set SNMP user | snmp-server user |
| Show SNMP community information | show snmp community |
| Show SNMP view settings | show snmp view |
| Show SNMP group settings | show snmp group |
| Show SNMP user settings | show snmp user |
5 Examples of Command Execution
5.1 SNMPv1 setting example
This example makes SNMPv1-based network monitoring possible under the following conditions.
- Set the read-only community name “public.”
- Set the trap destination as “192.168.100.11”, and set “snmptrapname” as the trap community name.
Yamaha(config)# snmp-server community public ro ... 1 Yamaha(config)# snmp-server host 192.168.100.11 traps version 1 snmptrapname ... 2
5.2 SNMPv2c setting example
This example makes SNMPv2c-based network monitoring possible under the following conditions.
- Set the readable/writable community name as “private.”
- Specify the notification message destination as “192.168.100.12”, the notification type as “inform” request format, and the notification destination community name as “snmpinformsname”.
Yamaha(config)# snmp-server community private rw ...1 Yamaha(config)# snmp-server host 192.168.100.12 informs version 2c snmpinformsname ...2
5.3 SNMPv3 setting example
This example makes SNMPv3-based network monitoring possible under the following conditions.
- Specify the view that shows the internet node (1.3.6.1) and below as “most”.
- Specify the view that shows the mib-2 node (1.3.6.1.2.1) and below as “standard”.
- Create the user group “admins”, and grant users belonging to the “admins” group full access rights to the “most” view.
- Create the user group “users”, and grant users belonging to the “users” group read access rights to the “standard” view.
- Create an “admin1” user that belongs to the “admins” group.
Set the password to “passwd1234”, using the “HMAC-SHA-96” authentication algorithm.
Set the encryption password to “passwd1234”, using the “AES128-CFB” encryption algorithm.
- Create an “user1” user that belongs to the “users” group.
Set the password to “passwd5678”, using the “HMAC-SHA-96” authentication algorithm.
- Send notifications in trap format (without response confirmation) to 192.168.10.3.
- Send notifications in inform request format to 192.168.20.3.
Yamaha(config)# snmp-server view most 1.3.6.1 include ... 1 Yamaha(config)# snmp-server view standard 1.3.6.1.2.1 include ... 2 Yamaha(config)# snmp-server group admins priv read most write most ... 3 Yamaha(config)# snmp-server group users auth read standard ... 4 Yamaha(config)# snmp-server user admin1 admins auth sha passwd1234 priv aes passwd1234 ... 5 Yamaha(config)# snmp-server user user1 users auth sha passwd5678 ... 6 Yamaha(config)# snmp-server host 192.168.10.13 traps version 3 priv admin1 ... 7 Yamaha(config)# snmp-server host 192.168.20.13 informs version 3 priv admin1 ... 8
6 Points of Caution
- Check the SNMP version that can be used with the SNMP manager beforehand. It is necessary to configure this product in accordance with the SNMP version that will be used.
- This product is not compatible with the following functions related to SNMPv3.
- Proxy function
- Access to MIB objects after the SNMPv2 subtree (1.3.6.1.6). Changing SNMPv3-related settings via SNMP is also not supported.
7 Related Documentation
RMON
1 Function Overview
By making settings for the RMON (Remote network MONitering) function, you can monitor and record the traffic volume and error occurrences for each interface.
Since the settings for the RMON function and the data obtained by the RMON function are held as an MIB, they can be retrieved and edited from the SNMP manager.
The RMON function of this product supports the following groups defined in RFC2819.
- Ethernet statistics group
- History group
- Alarm group
- Event group
2 Definition of Terms Used
- RMON MIB
- MIB for the RMON function, defined in RFC2819
- Ethernet statistics group
MIB group defined as group 1 of the RMON MIB.
This holds a table for monitoring Ethernet statistical information.
The information in the table includes counters for the number of packets, the number of errors, etc.
The etherStatsTable is the applicable MIB for this product.
- History group
MIB group defined as group 2 of the RMON MIB.
At a specified interval, it measures the same information as the Ethernet statistical information group, and has a table for saving the history of this information.
The MIBs relevant for this product are the historyControlTable and the etherHistoryTable.
- Alarm group
MIB group defined as group 3 of the RMON MIB.
At the specified interval, the statistical information of the Ethernet statistical information group is compared with the threshold values.
If the sampled values exceed the threshold values, the event defined for the event group is generated.
The alarmTable is the applicable MIB for this product.
- Event group
MIB group defined as group 9 of the RMON MIB.
This is the action taken in response when the alarm group conditions are met.
The eventTable is the applicable MIB for this product.
3 Function Details
The operating specifications for operation of the RMON function are shown below.
3.1 Common between groups
The specifications common between groups are given below.
- In order to enable the RMON function on this product, the system-wide RMON function must be enabled.
- Use the rmon command to make settings.
- This is enabled by default.
- You can also set this by using the private MIB ysrmonSetting(1.3.6.1.4.1.1182.3.7.1).
3.2 Ethernet statistics group
The operating specifications for the Ethernet statistics group are given below.
- Make settings by using the rmon statistics command on an interface.
- Starting at the point at which you specified the rmon statistics command, statistical information is collected, and the etherStatsTable of the RMON MIB will be available for retrieval.
- This can be specified for a physical interface.
- A maximum of eight rmon statistics commands can be specified for the same interface.
- If an rmon statistics command is deleted, the collected statistical information is also deleted.
- If an rmon statistics command is overwritten, the previously collected statistical information is deleted, and collection is started once again.
- If the RMON function is disabled system-wide, collection of statistical information is halted.
If the RMON function is subsequently enabled system-wide, the previously collected statistical information is deleted, and collection is started once again.
- The supported OIDs in the Ethernet statistical information group are as follows.
rmon(1.3.6.1.2.1.16)
+- statistics(1.3.6.1.2.1.16.1)
+- etherStatsTable(1.3.6.1.2.1.16.1.1)
+ etherStatsEntry(1.3.6.1.2.1.16.1.1.1) { etherStatsIndex }
+- etherStatsIndex(1.3.6.1.2.1.16.1.1.1.1) (read-only)
+- etherStatsDataSource(1.3.6.1.2.1.16.1.1.1.2) (read-create)
| Interface being monitored
+- etherStatsDropEvents(1.3.6.1.2.1.16.1.1.1.3) (read-only)
| Number of packets dropped
+- etherStatsOctets(1.3.6.1.2.1.16.1.1.1.4) (read-only)
| Number of octets received
+- etherStatsPkts(1.3.6.1.2.1.16.1.1.1.5) (read-only)
| Number of packets received
+- etherStatsBroadcastPkts(1.3.6.1.2.1.16.1.1.1.6) (read-only)
| Number of broadcast packets received
+- etherStatsMulticastPkts(1.3.6.1.2.1.16.1.1.1.7) (read-only)
| Number of multicast packets received
+- etherStatsCRCAlignErrors(1.3.6.1.2.1.16.1.1.1.8)(read-only)
| Number of FCS error packets received
+- etherStatsUndersizePkts(1.3.6.1.2.1.16.1.1.1.9) (read-only)
| Number of undersize packets received (packets smaller than 64 octets)
+- etherStatsOversizePkts(1.3.6.1.2.1.16.1.1.1.10) (read-only)
| Number of oversize packets received (packets larger than 1518 octets)
+- etherStatsFragments(1.3.6.1.2.1.16.1.1.1.11) (read-only)
| Number of fragment packets received (packets smaller than 64 octets with abnormal FCS)
+- etherStatsJabbers(1.3.6.1.2.1.16.1.1.1.12) (read-only)
| Number of jabber packets received (packets larger than 1518 octets with abnormal FCS)
+- etherStatsCollisions(1.3.6.1.2.1.16.1.1.1.13) (read-only)
| Number of collisions
+- etherStatsOwner(1.3.6.1.2.1.16.1.1.1.20) (read-create)
| Name of owner
+- etherStatsStatus(1.3.6.1.2.1.16.1.1.1.21) (read-create)
Status of statistical group3.3 History group
The operating specifications for the history group are shown below.
- Make settings by using the rmon history command on an interface.
- Starting at the point at which you specified the rmon history command, historical information is collected, and the etherHistoryTable of the RMON MIB will be available for retrieval.
- This can be specified for a physical interface.
- A maximum of eight rmon history commands can be specified for the same interface.
- If an rmon history command is deleted, the collected historical information is also deleted.
- If an rmon history command is overwritten, the previously collected historical information is deleted, and collection is started once again.
- If the RMON function is disabled system-wide, collection of historical information is halted.
If the RMON function is subsequently enabled system-wide, the previously collected historical information is deleted, and collection is started once again.
- The supported OIDs in the Ethernet history group are as follows.
rmon(1.3.6.1.2.1.16)
+- history(1.3.6.1.2.1.16.2)
+- historyControlTable(1.3.6.1.2.1.16.2.1)
| + historyControlEntry(1.3.6.1.2.1.16.2.1.1) { historyControlIndex }
| +- historyControlIndex(1.3.6.1.2.1.16.2.1.1.1) (read-only)
| +- historyControlDataSource(1.3.6.1.2.1.16.2.1.1.2) (read-create)
| | Interface being monitored
| +- historyControlBucketsRequested(1.3.6.1.2.1.16.2.1.1.3)(read-create)
| | Number of history group history saves requested
| +- historyControlBucketsGranted(1.3.6.1.2.1.16.2.1.1.4) (read-only)
| | Number of history group histories saved
| +- historyControlInterval(1.3.6.1.2.1.16.2.1.1.5) (read-create)
| | Interval at which history group histories are saved
| +- historyControlOwner(1.3.6.1.2.1.16.2.1.1.6) (read-create)
| | Name of owner
| +- historyControlStatus(1.3.6.1.2.1.16.2.1.1.7) (read-create)
| History group status
|
+- etherHistoryTable(1.3.6.1.2.1.16.2.2)
+ etherHistoryEntry(1.3.6.1.2.1.16.2.2.1) { etherHistoryIndex, etherHistorySampleIndex }
+- etherHistoryIndex(1.3.6.1.2.1.16.2.2.1.1) (read-only)
+- etherHistorySampleIndex(1.3.6.1.2.1.16.2.2.1.2) (read-only)
+- etherHistoryIntervalStart(1.3.6.1.2.1.16.2.2.1.3) (read-only)
| Interval at which history group histories are saved
+- etherHistoryDropEvents(1.3.6.1.2.1.16.2.2.1.4) (read-only)
| Number of packets dropped
+- etherHistoryOctets(1.3.6.1.2.1.16.2.2.1.5) (read-only)
| Number of octets received
+- etherHistoryPkts(1.3.6.1.2.1.16.2.2.1.6) (read-only)
| Number of packets received
+- etherHistoryBroadcastPkts(1.3.6.1.2.1.16.2.2.1.7) (read-only)
| Number of broadcast packets received
+- etherHistoryMulticastPkts(1.3.6.1.2.1.16.2.2.1.8) (read-only)
| Number of multicast packets received
+- etherHistoryCRCAlignErrors(1.3.6.1.2.1.16.2.2.1.9)(read-only)
| Number of FCS error packets received
+- etherHistoryUndersizePkts(1.3.6.1.2.1.16.2.2.1.10)(read-only)
| Number of undersize packets received (packets smaller than 64 octets)
+- etherHistoryOversizePkts(1.3.6.1.2.1.16.2.2.1.11) (read-only)
| Number of oversize packets received (packets larger than 1518 octets)
+- etherHistoryFragments(1.3.6.1.2.1.16.2.2.1.12) (read-only)
| Number of fragment packets received (packets smaller than 64 octets with abnormal FCS)
+- etherHistoryJabbers(1.3.6.1.2.1.16.2.2.1.13) (read-only)
| Number of jabber packets received (packets larger than 1518 octets with abnormal FCS)
+- etherHistoryCollisions(1.3.6.1.2.1.16.2.2.1.14) (read-only)
| Number of collisions
+- etherHistoryUtilization(1.3.6.1.2.1.16.2.2.1.15) (read-only)
Estimated value of network usage ratio3.4 Alarm group
The operating specifications for the alarm group are shown below.
- Use the rmon alarm command to make settings.
- From the point that the rmon alarm command is specified, sampling occurs at the specified interval.
- If an rmon alarm command is overwritten, the previous sampling data is deleted, and sampling is started once again.
- If the RMON function is disabled system-wide, sampling is halted.
If the RMON function is subsequently enabled system-wide, the previous sampling data is deleted, and sampling is started once again.
- Only etherStatsEntry(.1.3.6.1.2.1.16.1.1.1) MIB objects that have a counter type can be specified as the object of alarm group monitoring.
- If the Ethernet statistical information group used by the rmon alarm command is deleted, the rmon alarm command is also deleted.
- If the event group used by the rmon alarm command is deleted, the rmon alarm command is also deleted.
- The supported OIDs in the alarm group are as follows.
rmon(1.3.6.1.2.1.16)
+- alarm(1.3.6.1.2.1.16.3)
+- alarmTable(1.3.6.1.2.1.16.3.1)
+ alarmEntry(1.3.6.1.2.1.16.3.1.1) { alarmIndex }
+- alarmIndex(1.3.6.1.2.1.16.3.1.1.1) (read-only)
+- alarmInterval(1.3.6.1.2.1.16.3.1.1.2) (read-create)
| Sampling interval
+- alarmVariable(1.3.6.1.2.1.16.3.1.1.3) (read-create)
| MIB object to be monitored
+- alarmSampleType(1.3.6.1.2.1.16.3.1.1.4) (read-create)
| Sampling type
+- alarmValue(1.3.6.1.2.1.16.3.1.1.5) (read-only)
| Estimated value
+- alarmStartupAlarm(1.3.6.1.2.1.16.3.1.1.6) (read-create)
| Threshold value used for first alarm determination
+- alarmRisingThreshold(1.3.6.1.2.1.16.3.1.1.7) (read-create)
| Upper threshold value
+- alarmFallingThreshold(1.3.6.1.2.1.16.3.1.1.8) (read-create)
| Lower threshold value
+- alarmRisingEventIndex(1.3.6.1.2.1.16.3.1.1.9) (read-create)
| Event index when crossing upper limit
+- alarmFallingEventIndex(1.3.6.1.2.1.16.3.1.1.10) (read-create)
| Event index when crossing lower limit
+- alarmOwner(1.3.6.1.2.1.16.3.1.1.11) (read-create)
| Name of owner
+- alarmStatus(1.3.6.1.2.1.16.3.1.1.12) (read-create)
Alarm group statusAlarm detection is determined by an upper threshold value and a lower threshold value. If the threshold value is crossed, the specified event is executed.
If an alarm is detected, the alarm will not be detected again until the value crosses the opposite threshold.
The following cases are explained as examples.
- At point 1, the upper threshold value is crossed, so an alarm is detected.
The threshold value that is used for the very first decision can be specified by STARTUP.
In the example above, we will assume that the STARTUP value is “1” (using only the upper threshold value (risingAlarm)) or “3” (using both the upper threshold value and the lower threshold value (risingOrFallingAlarm)).
- At point 2, an alarm is not detected.
- At point 3, the upper threshold value is crossed, but since the opposite threshold was not previously crossed, an alarm is not detected.
- At point 4, the lower threshold value is crossed, and since the upper threshold was previously crossed, an alarm is detected.
- At point 5, the lower threshold value is exceeded, but since the opposite upper threshold was not previously crossed, an alarm is not detected.
- At point 6, the upper threshold value is crossed, and since the lower threshold was previously crossed, an alarm is detected.
3.5 Event group
The operating specifications for the event group are shown below.
- Use the rmon event command to make settings.
- The following operations can be specified for the event group.
- Record to log
- Send SNMP trap
- Record to log and send SNMP trap
- If trap transmission is specified, the following SNMP commands must be set in order to transmit the SNMP trap.
- snmp-server host
- snmp-server enable trap rmon
- The following operations will be carried out when specifying trap transmission.
- SNMPv1, SNMPv2c
- Only the traps for which the community name specified using the rmon event command, and for which the community name specified by the snmp-server host host command are matching will be transmitted.
- SNMPv3
- Only the traps for which the community name specified using the rmon event command, and for which the user name specified by the snmp-server host host command are matching will be transmitted.
- Only the traps for which the community name specified using the rmon event command, and for which the user name specified by the snmp-server host host command are matching will be transmitted.
- SNMPv1, SNMPv2c
- The supported OIDs in the event group are as follows.
rmon(1.3.6.1.2.1.16) +- event(1.3.6.1.2.1.16.9) +- eventTable(1.3.6.1.2.1.16.9.1) + eventEntry(1.3.6.1.2.1.16.9.1.1) { eventIndex } +- eventIndex(1.3.6.1.2.1.16.9.1.1.1) (read-only) +- eventDescription(1.3.6.1.2.1.16.9.1.1.2) (read-create) | Event description +- eventType(1.3.6.1.2.1.16.9.1.1.3) (read-create) | Event type +- eventCommunity(1.3.6.1.2.1.16.9.1.1.4) (read-create) | Community name +- eventLastTimeSent(1.3.6.1.2.1.16.9.1.1.5) (read-only) | Event execution time +- eventOwner(1.3.6.1.2.1.16.9.1.1.6) (read-create) | Name of owner +- eventStatus(1.3.6.1.2.1.16.9.1.1.7) (read-create) Event group status
3.6 Setting by SetRequest from an SNMP manager
The same content as the commands of each group can be specified by using SetRequest from an SNMP manager.
The procedure for making settings from an SNMP manager is as follows.
As an example, we explain how to make new settings for the Ethernet statistics information (etherStatsTable) group to port1.1 using index number 1.
Similar operations can be used to make settings for a supported MIB on other groups.
- Make SNMP settings to allow the MIB to be written.
For details, refer to the SNMP technical reference.
- For etherStatsStatus.1, specify “2” (createRequest).
The “.1” of etherStatsStatus.1 is the etherStatsTable index.
- For etherStatsDataSource.1, specify iFindex.5001 as the interface to be monitored.
ifIndex.5001 indicates port1.1.
- Specifying “owner” is optional, but if you do, specify the text string in etherStatsOwner.1.
- For etherStatsStatus, specify “1” (valid).
When you perform the above steps, the following commands are specified for port1.1.
We assume that “RMON” was set as the “owner” setting.
rmon statistics 1 owner RMON
Below we show how to disable the RMON function system-wide from the SNMP manager.
- Make SNMP settings to allow the MIB to be written.
For details, refer to the SNMP technical reference.
- For ysrmonSetting(1.3.6.1.4.1.1182.3.7.1), specify “2” (disabled).
When you perform the above steps, the following commands are specified.
rmon disable
To specify enable, set ysrmonSetting(1.3.6.1.4.1.1182.3.7.1) to “1” (enabled).
4 Related Commands
Related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| RMON function settings | rmon |
| Set RMON Ethernet statistical information group | rmon statistics |
| Set RMON history group | rmon history |
| Set RMON event group | rmon event |
| Set RMON alarm group | rmon alarm |
| Show RMON function status | show rmon |
| Show RMON Ethernet statistical information group status | show rmon statistics |
| Show RMON history group status | show rmon history |
| Show RMON event group status | show rmon event |
| Show RMON alarm group status | show rmon alarm |
| Clear RMON Ethernet statistical information group counters | rmon clear counters |
5 Examples of Command Execution
5.1 Set Ethernet statistical information group
Make Ethernet statistical information group settings for port 1.1, and from the SNMP manager, retrieve the MIB of the Ethernet statistical information group.
- Enable the Ethernet statistical information group setting for port1.1.
The index of the Ethernet statistical information group is “1.”
Yamaha(config)#interface port1.1 Yamaha(config-if)#rmon statistics 1 ... (Enable the Ethernet statistical information group setting)
- From the SNMP manager, make SNMP settings that the MIB of the Ethernet statistical information group can be retrieved.
In this example, we use “private” access on SNMPv1 or SNMPv2c.
Yamaha(config)#snmp-server community private rw ... (Set the readable/writable community name as “private”)
- From the SNMP manger, it will be possible to retrieve the etherStatsTable(.1.3.6.1.2.1.16.1.1) with the community name “private.”
5.2 Set history group
Make settings for the history group of port1.1 and retrieve the MIB of the history group from the SNMP manager.
- Enable the port1.1 history group setting.
The index of the history group is “1.”
Yamaha(config)#interface port1.1 Yamaha(config-if)#rmon history 1 ... (Enable the history group setting)
- From the SNMP manager, make SNMP settings that the MIB of the history group can be retrieved.
In this example, we use “private” access on SNMPv1 or SNMPv2c.
Yamaha(config)#snmp-server community private rw ... (Set the readable/writable community name as “private”)
- From the SNMP manger, it will be possible to retrieve the etherHistoryTable(.1.3.6.1.2.1.16.2.2) with the community name “private.”
5.3 Set alarm event group
Use the alarm group to monitor the statistical information values of the Ethernet statistical information group.
The conditions for monitoring are as follows.
- The MIB to be monitored is port1.1’s etherStatsPkts(.1.3.6.1.2.1.16.1.1.1.5).
- The sampling interval is 180 seconds.
- The sampling type is delta.
- The upper threshold value is 2000.
- The lower threshold value is 1000.
When the above monitoring conditions are matched, the following event group is executed.
- Record to log and send SNMP trap
- Community name is “RMON”
- Make the required settings for SNMP trap transmission.
Yamaha(config)#snmp-server host 192.168.100.3 traps version 2c RMON ... (Set trap transmission destination) Yamaha(config)#snmp-server enable trap rmon ... (Enable trap transmission for the RMON function)
- Make event group settings.
The index of the event group is “1.”
Yamaha(config)#rmon event 1 log-trap RMON ... (Enable the event group setting)
- In order to set the alarm group’s monitoring target MIB object, enable the port1.1 Ethernet statistical information group setting.
The index of the Ethernet statistical information group is “1.”
Yamaha(config)#interface port1.1 Yamaha(config-if)#rmon statistics 1 ... (Enable the Ethernet statistical information group setting)
- Set the alarm group with the listed conditions.
The index of the alarm group is “1.”
Yamaha(config)#rmon alarm 1 etherStatsPkts.1 interval 180 delta rising-threshold 3000 event 1 falling-threshold 2000 event 1 ... (Enable the alarm group)
6 Points of Caution
None
7 Related Documentation
SYSLOG
1 Function Overview
This product provides the SYSLOG functions shown below as a means to ascertain the operating state.
- Functions to collect, reference, and delete the log that is accumulated inside this product
- Functions for output to the console simultaneously with logging
- Functions for transmitting to a previously-registered notification destination (SYSLOG server) simultaneously with logging
Logging, output to console, and notifications to the SYSLOG server are performed according to the output level specified by the user. Processing occurs only for the permitted messages.
Logging occurs in RAM, and is automatically backed up to flash ROM or can be backed up manually.
When backing up manually, you can also back up to an SD card at the same time.
Notifications to the SYSLOG server are done simultaneously with logging, but only if a SYSLOG server has been registered.
2 Definition of Terms Used
None
3 Function Details
The SYSLOG function is described below.
- Logging occurs in RAM, and can accumulate up to 10,000 items.
Backup to Flash ROM can be performed by the following means.
- Automatic backup performed every hour since system boot
- Manual backup performed by the save logging command
- Backup performed when the write command is executed successfully
- The accumulated log can be viewed by the show logging command.
It can also be deleted by the clear logging command.
The show logging command shows the information in RAM.
For the log information of this product, it is assumed that the information in RAM always matches the information in flash ROM.
(When the system starts, the log information in flash ROM is applied to RAM, and the service is started. The log information in RAM is not deleted following execution of a backup.)
- Log transmission occurs only if the notification destination (SYSLOG server) has been registered.
You can use the logging host command to register up to two notification destinations.
Specify the notification destination either by IP address or FQDN.
As the port number of the notification destination, the default port number 514 is used. (This setting cannot be freely set by the user.)
- The level of log that is transmitted (SYSLOG priority) can be set using the logging trap command.
This product allows you to enable or disable output for each level of log.
With the factory settings, the output level enables only Information and Error.
- The logging backup sd command enables SYSLOG backup to the SD card.
If SYSLOG backup to the SD card is enabled, executing the save logging command will save the dated log file to the SD card.
4. List of related commands
Related commands are shown below.
For details, refer to the Command Reference.
List of related commands
| Function name | Command name |
|---|---|
| Set log output level | logging trap |
| Set log console output | logging stdout |
| Set log notification destination (SYSLOG server) | logging host |
| Back up log | save logging |
| Clear log | clear logging |
| Show log | show logging |
| Set SD card backup of log | logging backup sd |
5 Examples of Command Settings
- Enable debug-level log output, and start log output to the SYSLOG server (192.168.1.100).
Also output informational-level log to the console.
Yamaha(config)# logging trap debug … (Enable debug level log output) Yamaha(config)# logging host 192.168.1.100 … (Register SYSLOG server) Yamaha(config)# logging stdout info … (Output informational-level log to the console)
- Stop notifications to the SYSLOG server.
Yamaha(config)# no logging host
- Save and show the accumulated log information.
Yamaha# save logging … (Save log from RAM to ROM) Yamaha# show logging … (Show accumulated log) 2018/03/08 20:42:46: [ SESSION]:inf: Login succeeded as (noname) for HTTP: 192.168.1.40 2018/03/09 10:06:42: [ NSM]:inf: Interface port1.11 changed state to down 2018/03/09 10:09:48: [ SESSION]:inf: Logout timer expired as (noname) from HTTP: 192.168.1.40 2018/03/09 16:19:36: [ NSM]:inf: Interface port1.17 changed state to up :
- Clear the accumulated log information.
Yamaha# clear logging … (Clear all accumulated logs) Yamaha# show logging … (Show log) (Since they were cleared, nothing is shown)
6 Points of Caution
If creation of the system information storage area at startup fails, all logs saved inside this product will be deleted.
The following log is output after re-creating the system information storage area.
Syslog messages are cleared by partition re-creation.
7 Related Documentation
None
Firmware update
1 Function Overview
This product offers the following three firmware update functions, in order to correct problems in the program and to add new functionality.
- Firmware updates can be transmitted and applied to this product from a remote terminal such as a PC.
- This product’s built-in HTTP client can access an HTTP server, to download and apply the latest firmware.
- A firmware update placed on the SD card can be applied to this product.
These update functions can be used to upgrade or downgrade the version of firmware used on this product.
While firmware is being updated, all port LEDs flash green regardless of the LED display mode.
During stack configuration, the updated firmware is written simultaneously to the stack master and stack slave.
When the firmware update has been correctly written, the system will reboot in order to apply the new firmware.
For details on how to specify reboot, refer to 3.4 Reboot following writing.
2 Definition of Terms Used
None
3 Function Details
3.1 Update by transmitting the firmware update
This function transmits firmware updates to this product from a remote terminal, such as a PC, and applies it as boot firmware.
The update process is executed using a TFTP client or the Web GUI.
3.1.1 Using a TFTP client to update the firmware
A TFTP client installed on a PC or other remote terminal can be used to transmit the firmware update to this product and apply it.
In order to operate this product’s TFTP server, use the steps shown below to set up a network environment that allows remote access.
- Decide on the VLAN that will be used for maintenance.
- Set the IPv4 address on the maintenance VLAN. Use the ip address command for this setting.
- Permit access from the maintenance VLAN to the TFTP server. To make this setting, use the tftp-server interface command or the management interface command.
- Enable the TFTP server. Use the tftp-server enable command for this setting.
Follow the rules below when sending the firmware update using the TFTP client.
- Set the transmission mode to “binary mode”.
- As shown in the table below, specify the remote path to which the firmware update is sent.
- If an administrative password has been specified for this product, use the form “/PASSWORD” to specify the administrative password following the remote path.
For a firmware update using a TFTP client, the following three types of update can be performed.
Updated firmware
| Type | Remote path |
|---|---|
| Internal firmware | exec |
| Boot loader | boot |
| Boot loader + internal firmware | rom |
If there is no problem with the firmware update that was sent, the firmware update will be saved.
3.1.2. Firmware update by specifying the Web GUI local file
Specify the firmware update located on the terminal accessing the Web GUI, and applies it to this product.
This function does not do a version comparison with the existing firmware, and will overwrite the specified firmware regardless of version.
Firmware updates by specifying a local file are done by updating the firmware via Update firmware from PC located in [Maintenance] - [Firmware update] of the Web GUI. (Refer to the part shown in a red frame on the screenshot below.)
Refer to the help contents within the GUI for the specific operation method.
Initial screen on the Web GUI for updating firmware using a PC
3.2 Using an HTTP client to update the firmware
This method of firmware update uses an HTTP client to obtain the firmware update from a specified URL, and then apply it to this product.
This function assumes that the firmware version will be upgraded. Downgrading to a previous version will only be permitted if “revision-down” is allowed.
The firmware cannot be rewritten with the same version of firmware.
This function cannot be used when the stack is enabled.
An HTTP client can be used to update the firmware using the methods below.
- Use the firmware-update command from the CLI (Command-line interface)
- Execute the firmware update over the network using the Web GUI
Updating the firmware with an HTTP client is done by using the settings value shown in the table below.
Firmware update using an HTTP client: setting parameters
| Setting parameter | Explanation |
|---|---|
| Download source URL | Sets the source URL from which the firmware is downloaded. A URL of up to 255 characters in length can be set. The initial value is set as follows for each model. http://www.rtpro.yamaha.co.jp/firmware/revision-up/swr2310.bin |
| Permit downward revision | Sets whether the current version of firmware can be downgraded to a previous version. The default value is “Don’t allow”. Overwriting the firmware with the same version of firmware is not permitted. |
| Timeout | Specifies the timer for monitoring the completion of the processes shown below. - Version check of old and new firmware - The download monitoring timer from the specified URL can be specified from 100 seconds to 86,400 seconds, and the initial setting is set to 300 seconds. |
Refer to “5 Examples of Command Execution” or to the “Command Reference” for more information on how to use the firmware-update command.
To update firmware over the network using the Web GUI, execute the [Maintenance] - [Firmware update] command from the Web GUI. (Refer to the part shown in a red frame on the screenshot below.)
Refer to the help contents within the GUI for the specific operation method.
Initial screen for updating the firmware over the network using the Web GUI
3.3 Using an SD card to update the firmware
This function takes a firmware update from the SD card and applies it as boot firmware.
Perform the update from the CLI (Command-line interface) by using the firmware-update sd execute command.
In the case of stack configuration, only commands from the stack master can be used.
After entering the firmware update confirmation, the update will continue even if the SD card is removed. To unmount the SD card when executing the command, enter “N” in the confirmation of continued SD card mounting status, or specify the “sd-unmount” option with the command.
When rebooting with the SD card inserted in the main unit, the system will be booted from the firmware in the SD card as specified by the boot prioritize sd command.
- File path in the SD card
/swr2310/firmware/swr2310.bin
3.4 Reboot after writing
When the firmware update has been successfully written, the unit will reboot in accordance with the reboot time specified by the firmware-update reload-time command.
If the reboot time was not specified, the unit reboots immediately. If the reboot time was specified, the unit reboots at the specified time.
When configuring a stack, the firmware update method can be selected using the firmware-update reload-method command.
- Method to update member switches during configuration simultaneously
- Method to update without stopping network services
See Firmware Update in Stack function for an overview of how to update the firmware.
4 Related Commands
Related commands are shown below.
For details, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Set firmware update site | firmware-update url |
| Execute firmware update | firmware-update execute |
| Set firmware download timeout duration | firmware-update timeout |
| Permit downward revision | firmware-update revision-down |
| Show firmware update function settings | show firmware-update |
| Execute firmware update from SD card | firmware-update sd execute |
| Set firmware update reboot time | firmware-update reload-time |
| Setting the firmware update restart method during stack configuration | firmware-update reload-method |
5 Examples of Command Execution
5.1 Using an HTTP client to update the firmware
In this example, the firmware update is stored on the local HTTP server, and this product is set to manage the firmware in order to perform the update.
- Change the firmware download URL to http://192.168.100.1/swr2310.bin.
- The revision-down option is left in disabled mode.
- The timeout value is left at 300 sec.
- We will not specify a reboot time, but will reboot immediately after update.
- The download URL is changed, and the firmware update settings are confirmed.
Yamaha(config)#firmware-update url http://192.168.100.1/swr2310.bin … (Set download destination URL) Yamaha(config)#exit Yamaha#show firmware-update … (Show firmware update function setting) url:http://192.168.100.1/swr2310.bin timeout:300 (seconds) revision-down:Disable - The firmware update is executed.
Yamaha#firmware-update execute … (Execute firmware update) Found the new revision firmware Current Revision: Rev.2.04.01 New Revision: Rev.2.04.02 Downloading... Update to this firmware? (Y/N)y … (Enter “y”) Updating... Finish (Reboots automatically) - Pressing “CTRL+C” during the firmware update process will interrupt the update.
Yamaha#firmware-update execute Found the new revision firmware Current Revision: Rev.2.04.01 New Revision: Rev.2.04.02 Downloading... … (Enter Ctrl-C) ^CCanceled the firmware download
5.2 Using an SD card to update the firmware
In this example, the firmware update is placed on an SD card inserted in the unit, and this product is set to manage the firmware in order to perform the update.
This is an example of a two-stack configuration.
- Change the reboot time to 23:30.
- Change the reboot method to stack master/slave sequential reboot.
- Change the reboot time and reboot method.
Yamaha(config)#firmware-update reload-time 23 30 … (Reboot time setting) Yamaha(config)#firmware-update reload-method sequential … (Reboot method setting) Yamaha(config)#exit - Insert the SD card into the stack master and execute the firmware update.
Yamaha#firmware-update sd execute … (Execute firmware update) Update the firmware. Current Revision: Rev.2.04.01 New Revision: Rev.2.04.01 Update to this firmware? (Y/N)y … (enter “y”) Continue without unmounting the SD card? (Y/N)n … (enter “n”) Unmounted the SD card. Pull out the SD card. Updating... Finish Yamaha# (Reboots at specified reboot time) - The stack slave reboots after updating the firmware at the same time as the stack master and restarting the stack master.
The following log is displayed on the console of the stack slave.
(Press ENTER on the stack master. The firmware is received and the update starts.) Receiving exec file... Testing received file... Writing to Nonvolatile memory... Done. (Wait for restart of stack master then reboot) - After checking the version of the update firmware, you can enter “n” to cancel.
Yamaha#firmware-update sd execute … (Execute firmware update) Update the firmware. Current Revision: Rev.2.04.01 New Revision: Rev.2.04.02 Update to this firmware? (Y/N)n … (Enter “n”) Yamaha#
6 Points of Caution
If the system is rebooted or the power is turned off during firmware update, the update will be interrupted and the system will start with the firmware before the update operation.
7 Related Documentation
- Maintenance and operation functions: LED control
L2MS control
1 Function Overview
L2MS (Layer2 Management Service) is a function that manages Yamaha network devices at the layer 2 level.
L2MS consists of one L2MS master which performs centralized management and multiple L2MS slave units (subsequently called slaves) which are controlled from the L2MS master (subsequently called the master).
The SWR2310/SWR2311P-10G/SWP2 can be either a master or a slave.
Connections for the PC, master, and slaves are described below.
L2MS connections
From the PC, log in to the master via serial connection, Telnet, or HTTP/HTTPS.
The master provides commands for administering the slaves, and a Web GUI for making settings or acquiring the state, and these are used to operate the slaves.
The master and slaves are connected via Ethernet cables, and use a proprietary protocol for communication.
This function has the following features.
- Initial settings are not required
Although it is necessary to specify the IP address if using Telnet or SSH, this function communicates using its own protocol, so initial settings for the slaves are not required.
When an Ethernet cable is connected, the master automatically detects the slaves that are under it.
- Simultaneously control multiple supported units
The master can simultaneously recognize and control multiple slaves.
2 Definition of Terms Used
- Master
The device that manages Yamaha switches that are operating as L2MS and switch control function slaves.
It manages the Yamaha switches in the network.
- Slave
A Yamaha switch that is managed by the L2MS and switch control function master.
Its settings can be viewed or changed from the master.
3 Function Details
3.1 Supported models
The SWP2/SWR2310/SWR2311P-10G can be either an L2MS master or slave.
If operating as a master, one master can control a maximum of 64 slave units.
The following models can be managed as slaves.
As described earlier, devices that support switch control functionality (slaves) can also be controlled.
- SWR2100P series (SWR2100P-5G, SWR2100P-10G)
- SWR2310 series (SWR2310-10G, SWR2310-18GT, SWR2310-28GT)
- SWR2311P-10G
- SWP1 series (SWP1-8, SWP1-8MMF, SWP1-16MMF)
- SWP2 series (SWP2-10MMF, SWP2-SMF)
When operating as a slave, the unit is managed from the master of the Yamaha switch.
3.2 Usage
L2MS operation and role is set by the l2ms command.
- For the L2MS master
This unit manages the SWR2310 series, SWR2311P-10G, or SWP2 series units that are operating as slaves.
By specifying the terminal-watch enable command, information for terminals such as PCs on the network can be acquired and monitored at regular intervals.
Yamaha(config)#l2ms configuration Yamaha(config-l2ms)#l2ms enable Yamaha(config-l2ms)#l2ms role master Yamaha(config-l2ms)#terminal-watch enable
- For an L2MS slave
This unit is managed from the Yamaha switch that is operating as the master.
Yamaha(config)#l2ms configuration Yamaha(config-l2ms)#l2ms enable Yamaha(config-l2ms)#l2ms role slave
By specifying the show l2ms command, you can check current operation and role.
3.3 L2MS protocol
L2MS control is performed using the L2 frames of the proprietary protocol described below.
Contents of the L2MS protocol’s L2 frames
| Item | Value |
|---|---|
| Destination MAC | 01:a0:de:00:e8:12 – 01:a0:de:00:e8:15 |
| Ethertype | 0xe812 |
If there is a firewall between the master and slave, the firewall must be set to pass these L2 frames.
3.4 Slave monitoring
The master monitors the slaves under it by transmitting a query frame at regular intervals.
In response to the query frame, the slave sends a response frame, notifying the master of their own existence.
The interval at which the query frame is transmitted is set by the slave-watch interval command.
Higher settings of the value will reduce the frequency of transmission, but will lengthen the time from when a slave is connected to when the master recognizes it.
Lower settings of the value will have the opposite result, increasing the frequency of transmission but shortening the time from when a slave is connected to when the master recognizes it.
If a response frame from the slave is not received even though the master has sent the query frame for a specified number of times, the corresponding slave is determined to be down.
The number of times is specified by the slave-watch down-count command.
If the Ethernet cable connecting the slave is unplugged, there may be cases in which the slave is determined to be down even earlier than the setting of this command.
Set the slave-watch interval and slave-watch down-count commands to values that are appropriate for your network environment.
3.5 Slave ownership
One slave cannot be simultaneously controlled by multiple masters.
For this reason, you must make settings such that there is one master in a network.
If a slave receives a query frame after boot, that slave will be managed by the master that transmitted that query frame.
This state is canceled by any of the following conditions.
- If a query frame was not received for 30 seconds.
- If the master was restarted.
- If the l2ms reset command was executed on the master.
3.6 Slave control
When the master makes settings on an L2MS-compliant slave, or acquires its operating status, these actions are referred to as “controlling the slave.”
The LAN map of the Web GUI is used to control a slave.
After logging in to the Web GUI of the master, select the applicable slave in the LAN map and control it.
For details on operations in the LAN map, refer to the Web GUI help page.
Note that you cannot control a slave using commands from the SWP2/SWR2310/SWR2311P-10G (master).
Here we explain the operations that can be performed on slaves from the LAN map.
3.6.1 Operations for the SWR2100P series
The following operations can be performed for SWR2100P series (SWR2100P-5G, SWR2100P-10G) units.
- Display the status of the device and ports
- Update the firmware
- Show and control the power supply status of the ports (PoE-equipped models only)
3.6.2 Operations for the SWP1/SWP2/SWR2311P/SWR2310 series
The following operations can be performed for slaves.
- Display the status of the device and ports
- Show and control the power supply status of the ports (PoE-equipped models only)
- IP address setting
- Save and restore config
* Saving and restoring the SWP1’s config is supported by Rev.2.00.14 and later firmware.
- Use the HTTP Proxy function to log in to the slave’s GUI
If the HTTP Proxy function is enabled, you can log in to the slave’s GUI from the master’s LAN map.
When logging in to the slave, it will not be necessary to enter a user name and password.
If the IP address of a slave in the network conflicts with another device, it will not be possible to log in to the slave GUI via the HTTP Proxy function.
In this case, make settings in the master LAN map to change the IP address setting of the slave.
For details, refer to “3.6.3. HTTP Proxy function and IP Address Settings.”
3.6.3 About the HTTP Proxy function and IP address settings
The following operations can be performed for the SWP1/SWP2/SWR2310/SWR2311P series.
With the factory settings, or immediately after the cold start command is executed, a fixed IP address is specified. (The L2MS operates as a slave.)
At this time if the unit is managed by the master, DHCP client settings are made automatically.
This is to avoid conflicting IP addresses in the case that multiple slaves exist.
Since the IP address is allocated by the DHCP sever in the network, you can access the slave’s Web GUI via HTTP Proxy without making slave settings.
If a DHCP server does not exist in the network, it will not be possible to obtain an IP address, so you must specify the slave’s IP address in the master’s LAN map.
If settings are made and a startup config has been saved, they will not subsequently be automatically set by the DHCP client.
3.7 Information notified from the slave
A slave that is managed by the master informs the master when its own state changes or if a fault is detected.
Information from the slave is output to the master’s SYSLOG or LAN map.
For details on the messages that are output to SYSLOG, refer to “7. SYSLOG message list.”
The notifications sent by each slave are as follows.
Notifications sent by each slave to the master
| Slave | Information sent |
|---|---|
| SWR2100P series (SWR2100P-10G, SWR2100P-5G) | Port link up/down Loop detection Power supply function status for each port Power supply function error for each device |
| SWP1 series (SWP1-16MMF, SWP1-8MMF, SWP1-8) | Port link up/down Loop detection using the unique loop detection function SFP optical reception level fault Egress queue usage ratio fault |
| SWR2310 series SWR2311P-10G | Port link up/down Loop Loop detection using the unique loop detection function SFP optical reception level fault Egress queue usage ratio fault Status of power supply function for each port (SWR2311P-10G) Power supply function error for each device (SWR2311P-10G) Temperature fault Fan fault (SWR2311P-10G) Terminal monitoring notification |
3.8 Monitoring of connected terminals
By specifying the terminal-watch enable command for the master, you can enable the monitoring function for connected terminals, and manage information for the terminals that are connected to the master and to the slaves.
The following information for connected terminals is managed by the master.
- If the master and slave are Yamaha switches
- MAC address of the terminal
- Port number of the master or slave to which the terminal is connected
- Date and time at which the terminal was detected
This information can be referenced by the show l2ms detail command.
The recommended number of terminals managed by this function is a maximum of 200 units regardless of the network configuration.
Note that if more terminals than the recommended number of units exist in the network, the LAN map of the Web GUI might become sluggish or unresponsive.
According to changes in the network, the master will search for connected terminals or delete terminal information that it is managing.
The timing at which the master searches for connected terminals and the object of the search are as follows.
If new terminal information is found as a result of the search, it is determined that a terminal was detected.
Timing and object of terminal search
| Timing | Object |
|---|---|
| A port of the master linked-up | The master’s corresponding port |
| A new slave was detected | All ports of the detected slave |
| Port link-up notification received from a managed slave | The slave’s corresponding port |
| The time specified by the terminal-watch interval command elapsed | Master and all slaves |
The timing at which the master determines that a terminal has disappeared from the network and deletes the managed terminal information, and the object of the deletion, are as follows.
Timing and object of terminal information deletion
| Timing | Object |
|---|---|
| A port of the master linked-down | The terminal that was connected to the corresponding port of the master |
| A slave down was detected | All terminals that were connected to that slave |
| Port link-down notification received from a managed slave | The terminal that was connected to the corresponding port of the slave |
| As a result of searching for connected terminals, a previously-detected terminal was not found | Terminals that were not found |
4 Related Commands
Related commands are shown below.
For details, refer to the Command Reference.
List of L2MS-related commands
| Operations | Operating commands |
|---|---|
| Move to L2MS mode | l2ms configuration |
| Set L2MS function | l2ms enable |
| Set L2MS function role | l2ms role |
| Set slave monitoring time interval | slave-watch interval |
| Set number of times after which slave is determined to be down | slave-watch down-count |
| Set terminal management function | terminal-watch enable |
| Set time interval at which terminal information is acquired | terminal-watch interval |
| Set event monitoring function | event-watch disable |
| Event information monitoring time interval | event-watch interval |
| Set L2MS control frame transmission/reception | l2ms filter enable |
| Set whether the slave’s zero-config function is used | config-auto-set enable |
| Reset slave management | l2ms reset |
| Show L2MS information | show l2ms |
| Show L2MS slave config information | show l2ms slave-config |
| Set LAN map log output | logging event lan-map |
5 Examples of Command Execution
5.1 Set slave monitoring
Set the slave monitoring time interval.
L2SW(config)#l2ms configuration L2SW(config-l2ms)#slave-watch interval 8
Set the number of times after which the slave is determined to be down.
L2SW(config)#l2ms configuration L2SW(config-l2ms)#slave-watch down-count 7
5.2 Set terminal management function
Enable the terminal monitoring function.
L2SW(config)#l2ms configuration L2SW(config-l2ms)#terminal-watch enable
Set the time interval at which terminal information is acquired.
L2SW(config)#l2ms configuration L2SW(config-l2ms)#terminal-watch interval 3600
Show the terminal information acquired by the master.
Yamaha>show l2ms detail
Role : Master
[Master]
Number of Terminals : 0
[Slave]
Number of Slaves : 2
[ac44.f230.00a5]
Model name : SWR2310-10G
Device name : SWR2310-10G_Z5301050WX
Route : port2.1
LinkUp : 1, 3, 9
Uplink : 1
Downlink : 3
Config : None
Appear time : Tue Mar 13 18:43:18 2018
Number of Terminals : 1
[bcae.c5a4.7fb3]
Port : 9
Appear time : Wed Mar 14 14:01:18 2018
[00a0.deae.b8bf]
Model name : SWR2311P-10G
Device name : SWR2311P-10G_S4L000401
Route : port2.1-3
LinkUp : 1
Uplink : 1
Downlink : None
Config : None
Appear time : Tue Mar 13 18:43:18 2018
Number of Terminals : 0
5.3 Set L2MS control frame transmission/reception
Make settings so that L2MS control frames are not transmitted and received on port 1.5.
L2SW(config)#interface port1.5 L2SW(config-if)#l2ms filter enable
5.4 Set event monitoring function
Disable the event monitoring function.
L2SW(config)#l2ms configuration L2SW(config-l2ms)#event-watch disable
Set the time interval at which event information is acquired.
L2SW(config)#l2ms configuration L2SW(config-l2ms)#event-watch interval 60
5.5 Enable/disable use of the zero-config function
Specify whether the master uses the zero-config function for slaves.
This setting must be made for the master.
Disable the zero config function.
L2SW(config)#l2ms configuration L2SW(config-l2ms)#l2ms enable L2SW(config-l2ms)#l2ms role master L2SW(config-l2ms)#config-auto-set disable
6 Points of Caution
6.1 Regarding device configuration
Up to 64 slaves can be managed.
If slaves are used in a series connection, the maximum number of slave units that can be connected is eight units counting from the master.
Counting slaves from the master, a ninth or subsequent slave unit cannot be connected in series.
If the number of slave units connected in series is no more than eight units counting from the master, the number of units specified by the maximum number of administered units can be controlled.
If nine or more slave units are connected in series, counting from the master, L2MS communication will be delayed, preventing slaves from being correctly detected or controlled, and possibly causing problems such as the following.
- Synchronization processing might not work correctly.
- When slave settings are modified from the GUI, correct execution might not be possible.
If a switch made by a different manufacturer exists in the L2MS communication route, such as if a switch made by a different manufacturer is inserted between the master and a slave, it might not be possible to correctly control the slave.
If you are configuring a network that includes a switch made by a different manufacturer, verify operation beforehand.
6.2 Regarding terminal monitoring
The recommended number of managed units in the network is a maximum of 200 units.
If more terminals than the recommended number of managed units exist, the LAN map of the Web GUI might become sluggish or unresponsive.
If necessary, disable the terminal management function (terminal-watch disable command).
Terminal monitoring is performed using the information that is registered in the FDB (MAC address table) of the applicable device.
For this reason, depending on the timing at which search is performed, a terminal might not be detected even though it is connected, or a terminal might be detected even though it is no longer present on the network.
If link-down is detected for a master port or for a port of a Yamaha switch, all information for terminals connected to that port is deleted even if the terminals are registered in the FDB (MAC address table).
After a slave is connected to a port, it may take several seconds until L2MS detects the slave.
During this time, the corresponding slave is handled as a terminal.
Yamaha network devices that are not managed by the master as a slave are treated as terminals.
Since terminal search at the interval specified by the terminal-watch interval command is performed for the master and for all slaves, it might take twenty to thirty minutes for terminal search to be completed, depending on the configuration of the network.
It is not the case that other processing cannot be executed until terminal search has completed.
If an L2 switch made by another manufacturer is connected to an L2MS-compliant device, the terminals that are connected to the other manufacturer’s L2 switch are detected as terminals connected to the L2MS-compliant device.
However, if a terminal and a Yamaha switch are connected in parallel to the other manufacturer’s L2 switch, it will not be possible to detect terminals that are connected to the other manufacturer’s L2 switch.
6.3 Regarding use in conjunction with other functions
6.3.1 Use in conjunction with VLAN
If using a VLAN, you must specify the port used for L2MS communication as the access port or as the trunk port assigned to the native VLAN.
It is not possible to perform L2MS communication on a trunk port that is not assigned to the native VLAN.
6.3.2 Use in conjunction with mirroring
When the mirroring function is used, L2MS communication sent and received at the monitor port is also copied.
For this reason, connecting a master or slave to the mirror port might cause L2MS to not operate correctly; do not make such a connection.
6.3.3 Use with ACL
L2MS communication is not subject to ACL control.
Although the ACL discards frames that are not specified in the permission list (tacit rejection), L2MS communication is not subject to control, and therefore will be forwarded without being discarded.
6.3.4 Use with STP and the loop detection function
L2MS communication cannot be performed on a port that is in a blocked state because of STP or the loop detection function.
If link switching is performed by STP, the master is unable to correctly recognize the topology, possibly making it impossible to find a slave, or causing a mistake in the route when a slave is found.
In such cases, reset slave management by executing the l2ms reset command after STP has finished switching the link.
If multiple MST instances are operating, L2MS control frames are sent and received on the logical route (tree) formed by CIST (instance #0).
6.3.5 Use with link aggregation
If link aggregation is used, L2MS communication is considered to be occurring on “the lowest-numbered of the linked-up ports associated with the logical interface.”
If link aggregation is used in conjunction with the monitoring function for connected terminals, and a terminal is discovered at the end of a logical interface connection, the terminal is considered to be connected to “the lowest-numbered of the linked-up ports associated with the logical interface,” and the corresponding port number is shown.
In the following situation, L2MS communication is considered to be occurring between port1.1 and port1.1.
In the following situation, L2MS communication is considered to be occurring between port1.4 of the master and port1.5 of the slave.
6.3.6 Use with the stack function
In the case of one-unit stack configuration, L2MS will not function.
- For a one-unit configuration (standalone state)
In the case of an L2MS slave, it cannot be detected from the L2MS master.
In the case of the L2MS master, an L2MS slave in the network cannot be detected.
- For a two-unit configuration (active status)
In the case of the L2MS master, the L2MS slave cannot be detected.
In the case of an L2MS slave, it will be detected from the L2MS master.
Devices connected below either stack ID#1 or stack ID#2 will also be detected.
7. SYSLOG message list
The SYSLOG messages output by L2MS are shown below.
The messages that are output are given the prefix “[ L2MS].”
The prefix “route(ADDR):” is further added to SYSLOG messages that are shown when operating as the master.
ADDR is the MAC address of the slave.
SYSLOG messages shown when the unit starts up
| Output level | Message | Meaning |
|---|---|---|
| informational | Start L2MS(Master) | L2MS started as master. |
| Start L2MS(Slave) | L2MS started as slave. | |
| L2MS is disabled | L2MS was set to disable, and therefore did not start. |
SYSLOG messages shown when operating as master
| Type | Output level | Message | Meaning |
|---|---|---|---|
| Slave management | informational | Find slave | Slave was found. |
| Detect down | Slave went down. | ||
| Synchronization processing | informational | Sync start | Slave synchronization processing was started. |
| Sync done | Slave synchronization processing was completed. | ||
| Sync failed | Slave synchronization processing failed. | ||
| debug | Can’t get param of sync | Failed to obtain the slave information needed to perform synchronization processing. | |
| Terminal management | informational | Fail to update device info | Failed to update terminal information connected to slave. |
| debug | Update device info | Updated terminal information connected to slave. | |
| Device master management | debug | path: Format Version: Not found. | The format version is not listed in the device master file path. |
| path: Format Version: Illegal value. | An illegal value is listed for the format version in the device master file path. | ||
| path: Device Information: Illegal value. (line) | An illegal value is listed in the device information of the device master file path. (line) | ||
| path: Device Information: Duplicate device. (line) | A conflicting device is listed in the device information in (line) of the device master file path. (line) | ||
| path: Character Code: Not Shift_JIS. | The character code of the device master file path is not expressed in Shift JIS. | ||
| Config management | informational | Received config (file) | The master received a config file (file) from the slave and saved it. |
| Sent config (file) | The master sent a config file (file) to the slave. | ||
| Removed config (file) | Config file (file) was deleted. |
- SYSLOG
messages that are shown if operating as the master and the logging event lan-map command is set are prefixed with “[LANMAP].”Type Output level Message Meaning Snapshot function informational SnapShot: Not found. [Device_Name: “device_name”, MAC_Address: addr] There is a Yamaha switch that cannot be found. SnapShot: Not found. [MAC_Address: addr] There is a terminal that cannot be found. SnapShot: Unknown. [Device_Name: “device_name”, MAC_Address: addr] There is a Yamaha switch that is not registered. SnapShot: Unknown. [MAC_Address: addr] There is a terminal that is not registered. SnapShot: Route difference. [Device_Name: “device_name”, Route: route(UpLink:uplink_port), Route(SnapShot): route_snapshot(UpLink:uplink_port_snapshot), MAC_Address: addr] There is a Yamaha switch of a different connection port. The correct route is route_snapshot, and the uplink port is uplink_port_snapshot. SnapShot: Route difference. [Route: route, Route(SnapShot): route_snapshot, MAC_Address: addr] There is a terminal of a different connection port. The correct route is route_snapshot. SnapShot: Status recovered. [Device_Name: “device_name”, MAC_Address: addr] The state of the Yamaha switch matched the snapshot file. SnapShot: Status recovered. [MAC_Address: addr] The state of the terminal matched the snapshot file.
- Notifications received by the master from the slave include the following information.
Type Output level Message Meaning Link status informational Port n link up(SPEED) Port n of the slave linked-up. The communication speed is SPEED. Port n link down Port n of the slave went link-down. Loop detection informational Port n loop detect A loop occurred at port n of the slave. PoE informational Port n PoE state(supply-classX) Power supply to a classX device started on slave port n. classX is shown as class0–4. Port n PoE state(terminate) Power supply stopped at slave port n. Port n PoE state(overcurrent) Power supply stopped at slave port n because of overcurrent. Port n PoE state(forced-terminate) Power supply stopped at slave port n which had been supplying Class3 (15.4 W) by Class4 (30 W) power supply. Port n PoE state(over-supply) Power supply stopped because the supplied power at slave port n exceeded the maximum supply capability. Port n PoE state(over-temperature) Power supply stopped at slave port n because of an internal temperature error. Port n PoE state(power-failure) Power supply stopped at slave port n because the power supply malfunctioned. Port n PoE state(class-failure) Power supply stopped at slave port n because a class higher than the power class setting was detected. Port n PoE state(pd-failure) Power supply stopped at slave port n because a malfunction was detected on the PD. Port n PoE state(over-guardband) The supplied power reached the guard band on slave port n. PoE state error(over-supply) The power supplied by the slave exceeded the maximum supply capacity. PoE state error(over-temperature) Power supply stopped because of a slave internal temperature error. PoE state error(fanlock) Power supply stopped due to slave fan stop. PoE state error(power-failure) The slave’s power supply has malfunctioned. SFP optical reception level informational Port n SFP RX power(normal) The SFP optical reception level at slave port n returned to normal. Port n SFP RX power(low) The SFP optical reception level at slave port n fell below the lower threshold value. Port n SFP RX power(high) The SFP optical reception level at slave port n rose above the upper threshold value. Transmit queue usage informational Port n queue m usage rate(recovered) The transmission load at slave port n returned to normal. (QoS transmission queue: m) Port n queue m usage rate(busy) The transmission load at slave port n increased. (QoS transmission queue: m) Port n queue m usage rate(full) The transmission load at slave port n reached the upper limit. (QoS transmission queue: m) Terminal monitoring informational ping: ip-address(description) state(IDLE) ip-address(description) is not performing ping monitoring. ping: ip-address(description) state(DOWN) According to ping monitoring, ip-address(description) has gone down. ping: ip-address(description) state(UP) According to ping monitoring, ip-address(description) is now operating. Frame Counter: port(description) state(IDLE) port(description) is not performing frame reception volume monitoring. Frame Counter: port(description) state(DOWN) According to frame reception volume monitoring, port(description) has gone down. Frame Counter: port(description) state(UP) According to frame reception volume monitoring, port(description) is now operating. LLDP: port(description) state(IDLE) port(description) is not performing LLDP frame monitoring. LLDP: port(description) state(DOWN) According to LLDP frame monitoring, port(description) has gone down. LLDP: port(description) state(UP) According to LLDP frame monitoring, port(description) is now operating. Power supply informational Power voltage(high) The slave’s power supply voltage exceeded the upper threshold value. Power current(high) Overcurrent occurred at the slave’s power supply. Temperature informational CPU temperature(normal) The slave’s CPU temperature returned to normal. CPU temperature(high) The slave’s CPU temperature exceeded the threshold value. CPU temperature(alarm) A temperature fault occurred at the slave’s CPU. PHY temperature(normal) The slave’s PHY temperature returned to normal. PHY temperature(high) The slave’s PHY temperature exceeded the threshold value. PHY temperature(alarm) A temperature fault occurred at the slave’s PHY. SFP temperature(normal) The slave’s SFP temperature returned to normal. SFP temperature(high) The slave’s SFP temperature exceeded the threshold value. SFP temperature(alarm) A temperature fault occurred at the slave’s SFP. Thermal sensor temperature(normal) The slave’s thermal sensor monitoring temperature returned to normal. Thermal sensor temperature(high) The slave’s thermal sensor monitoring temperature exceeded the threshold value. Thermal sensor temperature(alarm) A temperature fault occurred at the slave’s thermal sensor. PSE temperature(normal) The slave’s PSE temperature returned to normal. PSE temperature(high) The slave’s PSE temperature exceeded the threshold value. Config management informational Executing a config ... progress% (file) Config file (file) settings are being recovered on the slave. progress indicates the ratio of completion. Finished executing a config (file) Recovery of config file (file) settings on the slave has finished. line: errmsg (file) While recovering a config file (file) on the slave, line line produced the error errmsg. errmsg is the content of the error, and line is the line within the config file of the command that produced the error.
SYSLOG messages shown when operating as slave
| Type | Output level | Message | Meaning |
|---|---|---|---|
| Slave management | infromational | Start management by controller(ADDR) | MAC address was managed by the ADDR master. |
| Release from controller(ADDR) | MAC address was released from management of the ADDR master. | ||
| Config management | infromational | Sent config to master (ADDR) | Config file was sent to the master. |
| Received config from master (ADDR) | Config file was received from the master. | ||
| Restart for update settings. | The unit will restart in order to update the received config file. |
8 Related Documentation
None
Mail notification
1 Function Overview
Mail notification is a function in which information detected by the L2MS function or the terminal monitoring function is conveyed via email.
By making the following settings, you can be notified of the information detected by various functions.
- Specify the mail server used when sending the mail.
- Specify the mail template.
For models that do not support the stack function, functions related to the stack function cannot be used.
2 Definition of Terms Used
- Mail template
- A definition that collects the following information needed when sending mail.
- Mail server to use
- Sender’s mail address
- Recipient’s mail address
- Subject of mail
- Content of notification
- Transmission wait time
3 Function Details
3.1 Operation
With the mail server settings and mail template settings having been made correctly, when a notification event occurs for a function that supports mail notification, the mail notification function will enter the send-standby state.
The mail notification function that is now in the send-standby state will wait until the mail transmission wait time specified for each mail template has elapsed.
When the mail transmission wait time has elapsed, the mail notification function combines the notification events that have occurred during the wait time into a single mail, and sends it to the recipient.
3.2. Mail server setting
This can be set in List of registered mail servers in the Web GUI’s [Advanced settings]-[Mail notification].
Press the [New] button or the [Setting] button of an existing setting to move to Mail server settings.
In Mail server settings, make the following settings.
- Account identification name
A name that distinguishes the mail server settings. This may be omitted.
- SMTP server address
- Port number of the SMPT server

3.3 Mail template settings
This can be set in List of mail notification settings in the Web GUI’s [Advanced settings]-[Mail notification].
Press the [New] button or the [Setting] button of an existing setting to move to Mail notification settings.
In Mail notification settings, make the following settings.
- Sender (From)
- Recipient (To)
- Subject
If Use prescribed subject has a check mark, the subject line of the mail will be Notification from (device name).
- Content of notification
- Mail transmission wait time

For models that do not support the stack function, the stack function error notification is not displayed in item notification contents
3.4 Functions that support mail notification
The following functions support mail notification.
LAN map
The following notification events will be the subject of mail notification.
For the correspondence between Yamaha network products managed by L2MS and notification events, refer to the technical data on L2MS control.
| Category | Type | Description |
|---|---|---|
| Fault in a Yamaha switch | ||
| Power supply fault | Power supply voltage exceeded the upper threshold value | |
| Overcurrent occurred in power supply | ||
| Temperature fault | CPU temperature exceeded the threshold value | |
| PHY temperature exceeded the threshold value | ||
| SFP module temperature exceeded the threshold value | ||
| Unit temperature exceeded the threshold value | ||
| PSE temperature exceeded the threshold value | ||
| CPU temperature fault occurred | ||
| PHY temperature fault occurred | ||
| SFP module temperature fault occurred | ||
| Unit temperature fault occurred | ||
| Loop occurred | Loop occurred at port | |
| SFP optical reception level fault | SFP optical reception level exceeded the threshold value | |
| Egress queue usage ratio fault | Egress queue usage ratio increased | |
| Fault in a Yamaha PoE switch | Maximum power supply capacity was exceeded | The power supply exceeded the maximum supply capacity |
| Temperature fault | Internal temperature fault occurred | |
| Power supply stopped due to a power supply class fault | Power supply was stopped because a class greater than the power supply class setting was detected at the power supply port | |
| Power supply stopped due to power supply Class 4 | Power supply stopped because Class 4 (30 W) power was supplied at the power supply port which had been supplying Class 3 (15.4 W) | |
| Power supply fault | The power supply has malfunctioned | |
| Power supply stopped due to overcurrent | Power supply stopped because overcurrent occurred at the power supply port | |
| Power supply stopped due to temperature fault | Power supply stopped due to temperature fault | |
| Power supply stopped due to stoppage of fan | Power supply stopped because the fan stopped | |
| Power supply stopped due to power fault | Power supply stopped due to a PoE power supply fault | |
| Discrepancy with snapshot | Invalid device connected | A device not registered in the snapshot was detected |
| Connection port mismatch | A device whose connection ports differ from the snapshot was detected | |
| Device lost | A device registered in the snapshot is not connected |
Terminal monitoring function
The following notification events will be the subject of mail notification.
| Category | Type | Description |
|---|---|---|
| Ping monitoring | Up detection | Terminal up was detected |
| Down detection | Terminal down was detected | |
| Frame reception amount monitoring | Up detection | Terminal up was detected |
| Down detection | Terminal down was detected | |
| LLDP monitoring | Up detection | Terminal up was detected |
| Down detection | Terminal down was detected |
Stack function
The following notification events will be the subject of mail notification.
| Type | Description |
|---|---|
| Stack port link down | The stack port connected to the member switch went link-down |
| Heartbeat error detection | A member switch heartbeat error was detected |
| Slave promotion | Slave switch was promoted to master |
3.5 Mail body example
The body of a notification mail includes content such as the following.
For details, refer to the technical reference for each function.
Up to 100 items can be shown in one notification mail.
Model: SRX2310-28GT * Model name Revision: Rev.2.04.01 * Firmware version SystemName: SRX2310-28GT_XXXXXXXX * Host name Time: 2017/06/13 11:42:56 * Mail transmission time Template ID: 1 * Mail template ID <<<<<<<<<<<<<<<<<<<<<<<< Lan Map Information >>>>>>>>>>>>>>>>>>>>>>>>> [SFP RX Power] Type Device_Name MAC_Address Err_Port Route State ============================================================================ (Detected: 2017/06/13 10:09:40 Recovered: 2017/06/13 10:10:10) SWR2311P-10G SWR2311P-10G_S4K000398 00a0.deae.b89c 1.9 port1.7(UpLink:1.5) Low ---------------------------------------------------------------------------- [Queue Usage Rate] Type Device_Name MAC_Address Err_Port Route State ============================================================================ (Detected: 2017/06/13 10:15:42 Recovered: 2017/06/13 10:17:24) SWR2311P-10G SWR2311P-10G_S4K000398 00a0.deae.b89c 1.6 port1.7(UpLink:1.5) Full(Queue:2) ---------------------------------------------------------------------------- [Fan Lock] Type Device_Name MAC_Address Route ============================================================================ (Detected: 2017/06/13 10:28:43 Recovered: ----/--/-- --:--:--) SWR2311P-10G SWR2311P-10G 00a0.de83.4146 port1.5(UpLink:2) ---------------------------------------------------------------------------- (Detected: 2017/06/13 10:42:13 Recovered: 2017/06/13 10:42:22) SWR2311P-10G SWR2311P-10G 00a0.de2a.dbbb port1.1(UpLink:23) ---------------------------------------------------------------------------- <<<<<<<<<<<<<<<<<< Terminal Monitoring Information >>>>>>>>>>>>>>>>>>> [via Ping] Date Status IP Address Description ---------------------------------------------------------------------------- 2017/06/13 Thu 10:42:56 UP 192.168.100.155 IP_Camera_1 2017/06/13 Thu 10:51:00 DOWN 192.168.100.155 IP_Camera_1 2017/06/13 Thu 10:54:02 UP 192.168.100.10 IP_Camera_2 2017/06/13 Thu 11:29:27 UP 192.168.100.155 IP_Camera_1 2017/06/13 Thu 11:30:31 DOWN 192.168.100.10 IP_Camera_2 [via Bandwidth Usage] Date Status Interface Description ---------------------------------------------------------------------------- 2017/06/13 Thu 10:45:43 UP port1.4 IP_Camera_2 2017/06/13 Thu 10:45:56 UP port1.6 Note_PC_1 2017/06/13 Thu 10:50:00 DOWN port1.6 Note_PC_1 2017/06/13 Thu 10:53:27 DOWN port1.4 IP_Camera_2 [via LLDP] Date Status Interface Description ---------------------------------------------------------------------------- 2017/06/13 Thu 10:53:56 UP port1.3 Note_PC_2 2017/06/13 Thu 11:11:54 DOWN port1.3 Note_PC_2 2017/06/13 Thu 11:14:24 UP port1.3 Note_PC_2 <<<<<<<<<<<<<<<<<<<<<<<<<< Stack Information >>>>>>>>>>>>>>>>>>>>>>>>> Date Information ---------------------------------------------------------------------------- 2017/06/13 Thu 10:53:44 The stack port changed state to down. (port1.28) 2017/06/13 Thu 10:53:46 Promoted from a slave to a master. (Old master ID : 1) 2017/06/13 Thu 10:59:10 Occurred the heartbeat error. (ID : 1)
LAN map
The device information included in the notification is shown below.
The device information that is shown will differ depending on the type of fault. The device information shown for each type of fault is as follows.
| Category | Type | Content of notification | Type | Device_Name | MAC_Address | Comment | Err_Port | Fan_number | Route | Route(SnapShot) | State | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Fault in a Yamaha switch | Fan fault | [Fan Lock] [Fan speed] | ✓ | - | - | - | ✓ | - | - | |||
| [Fan stop] | - | - | ✓ | ✓ | - | - | Only if a specific fan stopped | |||||
| Power supply fault | [Power voltage] [Power supply] | - | - | - | ✓ | - | - | |||||
| Temperature fault | [CPU temperature] [CPU temperature error] [PHY temperature] [PHY temperature error] [SFP temperature] [SFP module temperature error] [Unit temperature] [Unit temperature error] [PSE temperature] | - | - | - | ✓ | - | - | |||||
| Loop occurred | [Loop Detect] | - | ✓ | - | ✓ | - | - | |||||
| SFP optical reception level fault | [SFP RX Power] | - | - | - | ✓ | - | ✓ | |||||
| Egress queue usage ratio fault | [Queue Usage Rate] | - | - | - | ✓ | - | ✓ | |||||
| Fault in a Yamaha PoE switch | Temperature fault | [Over Temperature] | - | - | - | ✓ | - | - | ||||
| Maximum power supply capacity was exceeded | [Over Supply] | - | - | - | ✓ | - | - | |||||
| Power supply stopped due to a power supply class fault | [Class Failure] | - | ✓ | - | ✓ | - | - | |||||
| Power supply stopped due to power supply Class 4 | [Forced Terminate] | - | ✓ | - | ✓ | - | - | |||||
| Power supply fault | [Power Failure] | - | - | - | ✓ | - | - | |||||
| Power supply stopped due to overcurrent | [Over Current] | - | ✓ | - | ✓ | - | - | |||||
| Power supply stopped due to temperature fault | [PoE state error(over-temperature)] | - | - | - | ✓ | - | - | |||||
| Power supply stopped due to stoppage of fan | [PoE state error(fanlock)] | - | - | - | ✓ | - | - | |||||
| Power supply stopped due to power fault | [PoE state error(power-failure)] | - | - | - | ✓ | - | - | |||||
| Discrepancy with snapshot | Invalid device connected | [Illegal Equipment(SnapShot)] | ✓ | - | - | ✓ | - | - | ||||
| Connection port mismatch | [Port Mismatch(SnapShot)] | ✓ | - | - | ✓ | ✓ | - | |||||
| Device lost | [Disappearance Equipment(SnapShot)] | ✓ | - | - | - | ✓ | - | |||||
4 Related Commands
This function does not support settings via commands.
5 Points of Caution
None
6 Related Documentation
LLDP
1 Function Overview
LLDP is a protocol for passing device management information between a device and its neighboring devices.
This is a simple protocol in which a device unidirectionally advertises its own information and neighbor devices receive this information. However, since LLDP-compliant devices maintain the information received from neighbor devices as MIB objects, the user can access this information via SNMP and ascertain what type of devices are connected to which interfaces are.
This is also used for negotiation between devices that support PoE (Power Over Ethernet).
2 Definition of Terms Used
- LLDP
- Link Layer Discovery Protocol.
This is defined in IEEE 802.1AB.
- LLDP-MED
- LLDP for Media Endpoint Devices.
This is defined in ANSI/TIA-1057.
3 Function Details
3.1 Operating Specifications
3.1.1 Basic Specifications
This product supports the following operations.
- LLDP frames are transmitted from any LAN/SFP port to convey information about the device itself.
- LLDP frames are received at any LAN/SFP port to obtain information about neighboring devices.
- Information transmitted via LLDP about the device itself, and information obtained via LLDP about neighbor devices, etc., can be referenced via SNMP.
LLDP sends and receives information using Type, Length, and Value (TLV) attributes.
For details on the TLV information sent by this product, refer to 3.2 TLV list.
This product’s LLDP supports the following MIBs of SNMP. For details, refer to 3.3 Supported MIBs.
- LLDP-V2-MIB
The following settings are required in order to use the LLDP function.
- Use the lldp run command to enable the system-wide LLDP function.
- Use the lldp-agent command to create an LLDP agent for the applicable interface.
- Use the set lldp command to specify the LLDP frame transmit/receive mode.
With the default settings of this product, the LLDP function is enabled.
LLDP frames are always transmitted without tags, regardless of the VLAN settings of the transmitting switch port.
They are also transmitted without tags from a trunk port without a native VLAN.
3.1.2 Transmitted information settings
Use the following commands to specify the LLDP frames that are transmitted from the device itself. There are also some TLVs (required TLVs) that are transmitted regardless of the settings of the following commands.
- tlv-select basic-mgmt command (basic management TLV)
- tlv-select ieee-8021-org-specific command (IEEE 802.1 TLV)
- tlv-select ieee-8023-org-specific command (IEEE 802.3 TLV)
- tlv-select med command (LLDP-MED TLV)
The system name and description that are transmitted in the basic management TLVs are specified by the lldp system-name command and the lldp system-description command.
The type of management address is set by the set management-address-tlv command.
3.1.3 Transmission timer setting
The interval at which LLDP frames are sent is specified by the set timer msg-tx-interval command.
The multiplier for calculating the hold time (TTL) for device information is set by the set msg-tx-hold command.
The TTL for LLDP transmission is the result of the following calculation. The default is 121 seconds.
- TTL = ( value set by the “set timer msg-tx-interval” command ) × ( value set by the “set msg-tx-hold” command ) + 1 (second)
When a neighbor device is connected to a LAN/SFP port for which LLDP frame transmission is enabled, LLDP frames are transmitted rapidly at a fixed interval according to the high-speed transmission interval setting.
The transmission interval and the number of transmissions for high speed transmission are set by the set timer msg-fast-tx command and the set tx-fast-init.
If from a state in which LLDP frame transmission is enabled, the set lldp command is used to disable it, this product transmits a shut-down frame, notifying the neighbor device that LLDP frame transmission has stopped.
Subsequently, even if LLDP frame transmission is once again enabled, LLDP frame transmission to the neighbor device is stopped for a time.
The stopped duration until the next transmission occurs after transmitting the shutdown frame is set by the set timer reinit-delay command.
3.1.4 Maximum connected devices setting
The maximum number of connected devices that can be managed by the corresponding port is set by the set too-many-neighbors limit command.
The default value for the maximum number of connected devices is 5 devices.
3.1.5 Checking LLDP information
LLDP interface settings and received information about neighbor devices can be checked by using the show lldp interface command or the show lldp neighbors command.
To clear the LLDP frame counter, use the clear lldp counters command.
3.1.6 Other functions using LLDP
This product provides a function that uses LLDP to automatically make optimal settings for the Dante digital audio network. The Dante optimization settings function is set by the lldp auto-setting command. For details, refer to Dante optimization setting function.
This product also provides a function that uses LLDP to monitor the live/dead state of a specific connected terminal. For details, refer to Terminal monitoring.
For the voice VLAN function, you can use LLDP-MED to make voice traffic settings for IP telephony. For details, refer to VLAN.
3.2 TLV list
The TLVs supported by this product are listed below.
- Required TLVs
- Basic management TLVs
- IEEE 802.1 TLV
- IEEE 802.3 TLV
- LLDP-MED TLV
For the detailed specification of each TLV, refer to IEEE 802.1AB (LLDP) and ANSI/TIA-1057 (LLDP-MED).
The TLVs that are transmitted by this product are explained below.
3.2.1 Required TLVs
If LLDP frame transmission is enabled, these TLVs are always transmitted.
Three TLVs are transmitted: chassis ID, port ID, and TTL.
The required TLVs are shown below.
Required TLVs
| Type | Description | Length | Value (only fixed values are listed) |
|---|---|---|---|
| Chassis ID | Chassis ID | 6 bytes | MAC address of the device |
| Port ID | Port ID | 7–8 bytes | Port name (portX.X) |
| Time To Live (TTL) | Time to keep device information (seconds) | 2 bytes |
3.2.2 Basic management TLVs
These TLVs are transmitted if LLDP frame transmission is enabled and the tlv-select basic-mgmt command is specified.
System-related management information is transmitted, such as name, system capabilities, and address.
The basic management TLVs are as follows.
Basic management TLVs
| Type | Description | Length | Value (only fixed values are listed) |
|---|---|---|---|
| Port Description | Port description text string | 0–255 bytes | |
| System Name | System name text string Default: Host name | 0–255 bytes | |
| System Description | System description text string Default: device name + firmware revision | 0–255 bytes | |
| System Capabilities | The functions supported by the system | 2 bytes | 0x0004 (bridge) |
| The system’s functions that are in an enabled state | 2 bytes | 0x0004 (bridge) | |
| Management Address | The management address IP address (4 bytes) or MAC address (6 bytes) | 4 or 6 bytes | |
| Interface sub-type | 1 byte | 0x02 (ifIndex) | |
| Interface number | 4 bytes | ifIndex value |
3.2.3 IEEE 802.1 TLV
These TLVs are transmitted if LLDP frame transmission is enabled and the tlv-select ieee-8021-org-specific command is specified.
These transmit information such as VLAN and link aggregation for the corresponding port.
The IEEE 802.1 TLVs are shown below.
IEEE 802.1 TLV
| Type | Description | Length | Value (only fixed values are listed) |
|---|---|---|---|
| Port VLAN ID | Port VLAN number | 2 bytes | |
| Port and Protocol VLAN ID | Support for protocol VLAN, and whether enabled or disabled | 1 byte | 0x00 (no support) |
| Protocol VLAN number | 2 bytes | 0x0000 | |
| Protocol Identity | bytes string that identifies the protocol | 0–255 bytes | |
| Link Aggregation | Link aggregation capability and status | 1 byte | |
| ifIndex number of aggregation logical interface | 4 bytes | ||
| VLAN Name | Name of VLAN to which the port is associated | 0–32 bytes |
3.2.4 IEEE 802.3 TLV
These TLVs are transmitted if LLDP frame transmission is enabled and the tlv-select ieee-8023-org-specific command is specified.
Auto negotiation support information and PoE information etc. for the corresponding port is transmitted.
The IEEE 802.3 TLVs are shown below.
IEEE 802.3 TLV
| Type | Description | Length | Value (only fixed values are listed) |
|---|---|---|---|
| MAC/PHY Configuration/Status | Auto negotiation support, and whether enabled or disabled | 1 byte | |
| Communication methods for which auto negotiation is possible | 2 bytes | LAN ports: 0x6C01 (10/100/1000M) SFP ports: 0x0001 (1000M) | |
| Operational MAU Type Communication speed and duplex mode (IETF RFC 4836) | 2 bytes | ||
| Maximum Frame Size | Maximum frame size | 2 bytes |
3.2.5 LLDP-MED TLV
These TLVs are transmitted if LLDP frame transmission is enabled and the tlv-select med command is specified.
These transmit information such as network policy and extended PoE information.
The LLDP-MED TLVs are shown below.
LLDP-MED TLV
| Type | Description | Length | Value (only fixed values are listed) |
|---|---|---|---|
| LLDP-MED Capabilities | LLDP-MED TLVs that can be transmitted | 2 bytes | 0x000F (LLDP-MED Capabilities, Network Policy, Location Identification, Extended Power-via-MDI TLV ) |
| Device type | 1 byte | 0x04 (Network Connectivity) | |
| Location Identification | Format of location data | 1 byte | 0x03 (ECS ELIN) |
| Location data | 8 bytes | “Location” |
3.3 Supported MIBs
Refer to the following SNMP MIB Reference for information on the MIBs that are supported.
4 Related Commands
Related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Enable LLDP function | lldp run |
| Set system description text string | lldp system-description |
| Set system name | lldp system-name |
| Create LLDP agent | lldp-agent |
| Set LLDP transmission/reception mode | set lldp |
| Set management address type | set management-address-tlv |
| Set basic management TLV | tlv-select basic-mgmt |
| Set IEEE-802.1 TLV | tlv-select ieee-8021-org-specific |
| Set IEEE-802.3 TLV | tlv-select ieee-8023-org-specific |
| Set LLDP-MED TLV | tlv-select med |
| Set LLDP frame transmission interval | set timer msg-tx-interval |
| Set duration to stop transmission following LLDP transmission stop until transmission is once again possible | set timer reinit-delay |
| Set multiplier for calculating the time to maintain device information (TTL) | set msg-tx-hold |
| Set LLDP frame transmission interval for high-speed transmission term | set timer msg-fast-tx |
| Set number of LLDP frames transmitted for high-speed transmission term | set tx-fast-init |
| Set maximum number of devices that can be managed by an individual port | set too-many-neighbors limit |
| Show interface status | show lldp interface |
| Show connected device information for all interfaces | show lldp neighbors |
| Clear LLDP frame counters | clear lldp counters |
| Set Dante optimization function using LLDP | lldp auto-setting |
5 Examples of Command Execution
5.1 Set LLDP frame transmission/reception
For port1.1, enable LLDP frame transmission/reception.
Basic management TLVs, IEEE 802.1 TLVs, IEEE 802.3 TLVs, and LLDP-MED TLVs are transmitted.
Set the LLDP frame transmission interval to 60 seconds. Set the LLDP frame TTL to 181 seconds.
Set “SWITCH1” as the name of the transmitting system.
Specify 10 as the maximum number of connected devices managed by the port.
Yamaha#configure terminal Yamaha(confif)#lldp system-name SWITCH1 ... (Set system name) Yamaha(config)#interface port1.1 Yamaha(config-if)#lldp-agent ... (Create LLDP agent and transition modes) Yamaha(lldp-agent)#tlv-select basic-mgmt ... (Set basic management TLV) Yamaha(lldp-agent)#tlv-select ieee-8021-org-specific ... (Set IEEE 802.1 TLV) Yamaha(lldp-agent)#tlv-select ieee-8023-org-specific ... (Set IEEE 802.3 TLV) Yamaha(lldp-agent)#tlv-select med ... (Set LLDP-MED TLV) Yamaha(lldp-agent)#set timer msg-tx-interval 60 ... (Set transmission interval) Yamaha(lldp-agent)#set msg-tx-hold 3 ... (Set multiplier for TTL calculation: TTL = 60 × 3 + 1 = 181 seconds) Yamaha(lldp-agent)#set too-many-neighbors limit 10 ... (Set maximum number of connected devices) Yamaha(lldp-agent)#set lldp enable txrx ... (Set LLDP transmission/reception mode) Yamaha(lldp-agent)#exit Yamaha(config-if)#exit Yamaha(config)#lldp run ... (Enable LLDP function) Yamaha(config)#exit
5.2 Show LLDP interface status
Show the port1.1 LLDP interface status.
Yamaha#show lldp interface port1.1 ... (Show interface information) Agent Mode : Nearest bridge Enable (tx/rx) : Y/Y Message fast transmit time : 1 Message transmission interval : 30 Reinitialisation delay : 2 MED Enabled : Y Device Type : NETWORK_CONNECTIVITY LLDP Agent traffic statistics Total frames transmitted : 0
5.3 Show LLDP connected device information
Show LLDP connected device information.
Yamaha#show lldp neighbors ... (Show connected device information)
Interface Name : port1.1
System Name : SWR2310-10G
System Description : SWR2310 Rev.2.04.01 (Mon Dec 4 12:33:18 2019)
Port Description : port1.3
System Capabilities : L2 Switching
Interface Numbering : 2
Interface Number : 5003
OID Number :
Management MAC Address : ac44.f230.0000
Mandatory TLVs
CHASSIS ID TYPE
IP ADDRESS : 0.0.0.0
PORT ID TYPE
INTERFACE NAME : port1.3
TTL (Time To Live) : 41
8021 ORIGIN SPECIFIC TLVs
Port Vlan id : 1
PP Vlan id : 0
Remote VLANs Configured
VLAN ID : 1
VLAN Name : default
Remote Protocols Advertised :
Multiple Spanning Tree Protocol
Remote VID Usage Digestt : 0
Remote Management Vlan : 0
Link Aggregation Status : Disabled
Link Aggregation Port ID : 0
8023 ORIGIN SPECIFIC TLVs
AutoNego Support : Supported Enabled
AutoNego Capability : 27649
Operational MAU Type : 30
Power via MDI Capability (raw data)
MDI power support : 0x0
PSE power pair : 0x0
Power class : 0x0
Type/source/priority : 0x0
PD requested power value : 0x0
PSE allocated power value : 0x0
Max Frame Size : 1522
LLDP-MED TLVs
MED Capabilities :
Capabilities
Network Policy
MED Capabilities Dev Type : End Point Class-3
MED Application Type : Reserved
MED Vlan id : 0
MED Tag/Untag : Untagged
MED L2 Priority : 0
MED DSCP Val : 0
MED Location Data Format : ECS ELIN
Latitude Res : 0
Latitude : 0
Longitude Res : 0
Longitude : 0
AT : 0
Altitude Res : 0
Altitude : 0
Datum : 0
LCI length : 0
What : 0
Country Code : 0
CA type : 0
MED Inventory6 Points of Caution
None
7 Related Documentation
- SWR2310 Series Technical Data (Basic Functions)
- Maintenance and operation functions
- Terminal monitoring
Terminal monitoring
1 Function Overview
The terminal monitoring function checks the dead-or-alive state of specific terminals connected to the network switch.
The operating specifications for the terminal monitoring function are shown below.
Terminal monitoring function overview
This is an example with an L2 switch as the L2MS master and an intelligent L2 PoE switch as the L2MS slave.

As dead/alive monitoring methods, the following three types are provided.
- Monitoring by ping
Ping (ICMP Echo request/reply) is issued at regular intervals to a terminal that has an IP address, and the terminal is determined to be down if there is no longer a response.
The user can specify the interval at which ping is transmitted, the time to wait for ping response, and the number of failures until the terminal is determined to be down.
- Frame reception amount monitoring
The frame reception amount is monitored at regular intervals for an individual port, and the terminal is determined to be down if the traffic falls below a specified amount.
The user can specify the monitoring start threshold value and the threshold value at which a down condition is determined.
Monitoring starts when the traffic exceeds the monitoring start threshold value, and a down condition is determined when the traffic falls below the down decision threshold.
- LLDP reception interval monitoring
The LLDP received at regular intervals by an individual port is monitored.
Using the TTL which is a required item in the data portion of an LLDP packet, a down condition is determined if LLDP is not received within the TTL interval.
If monitoring detects a terminal fault (down), the following processing is automatically performed.
- Alert shown in dashboard screen
An indication that a fault (down) occurred for the monitored terminal is displayed in the alert screen of the dashboard.
- Alert shown in LAN map screen
If the switch performing the monitoring is the L2MS master
An indication that a fault (down) occurred for the monitored terminal is shown in the LAN map notification and history information.
If the switch performing the monitoring is an L2MS slave
The L2MS trap function is used to notify the L2MS master.
The L2MS master that receives the notification indicates in the LAN map screen that the monitored terminal has experienced a fault (down).
By the user’s choice, the following operations can be applied in parallel.
- Fault detection notification by mail
Notification that a monitored terminal has experienced a fault is sent to the desired recipient.
- Notification to the SNMP manager
A trap is sent to the SNMP manager specified by a command.
- Restart terminal by temporarily stopping the PoE power supply
If a down condition is detected on a port to which PoE power is being supplied, PoE power supply is temporarily turned off in an attempt to recover the monitored terminal.
2 Definition of Terms Used
None
3 Function Details
3.1 Monitoring by ping (ICMP Echo request/reply)
Specifications for terminal monitoring by ping are given below.
- The interval of ICMP Echo request transmission from the network switch is fixed at 5 seconds.
- The ICMP Echo request that is transmitted has the following format.
- As the ID field of the ICMP header, the unique ID assigned to each monitored terminal is specified.
- As the sequence field of the ICMP header, a number that is sequentially incremented from 0 is specified.
- The validity of the ICMP Echo reply is checked as follows.
- Whether the ID field of the ICMP header contains the ID that was specified when sending the request
- Whether the sequence field of the ICMP header contains the sequence number that was specified when sending the request
- The wait time for ICMP Echo reply can be changed in the range of 1–60 sec, and the default is 2 sec.
- The number of failures to receive the ICMP Echo reply from the monitored terminal after which a fault is determined can be set in the range of 1–100, and the default is twice.
- Monitoring via ping can be done for a maximum of 64 units.
3.2 Monitoring by frame reception amount
The way in which this device monitors by frame reception amount is described below.
Overview of frame reception amount monitoring

- At one-second intervals, the number of octets received at the port is referenced, and the number of octets received during one second is calculated.
- All ports are the object of observation.
- Using the number of octets received during one second and the link speed, the reception throughput (bps) and reception ratio (%) are calculated.
- Monitoring by frame reception amount starts when the monitoring start threshold value (bps) specified by the user is exceeded.
- After monitoring has started, a fault (down) is detected if the amount falls below the down detection threshold value (bps) specified by the user.
3.3 Monitoring by LLDP
Using the TTL which is a required item in the data portion of an LLDP frame, a down condition is determined if LLDP is not received within the TTL time.
Monitoring starts when an LLDP frame is first received.
This monitoring can be specified individually by port.
4 Related Commands
This function does not support settings via commands.
5. Settings via the Web GUI
Terminal monitoring settings can be done from [Advanced settings]-[Terminal monitoring] of the Web GUI.
Details on the settings in each screen can be referenced via the Web GUI help.
5.1 Terminal monitoring top page
The top page of terminal monitoring is shown below.
Terminal monitoring top page

- If you want to newly add a terminal for monitoring, press the New icon.
- If you want to change a currently-specified monitored terminal, press the [Setting] button in the list.
If you want to delete a currently-specified monitored terminal, select the check box of that terminal, and press the [Delete] button.
- If you want to ascertain the current state of the monitored terminal for which you are making settings, press the [Update] button to acquire the latest state.
5.2 Adding or modifying a monitored terminal
The method for adding a new monitored terminal, or for making changes, is shown below for each method of monitoring.
- Monitoring by ping
- Monitoring by frame reception amount
- Monitoring by LLDP
- Restart terminal by controlling PoE power supply can be specified only for models that support PoE power supply.
- When specifying the monitoring start threshold value and the down detection threshold value for frame reception amount monitoring, it is useful to use the traffic observation function.
- If you want mail notification to be sent in the event of a fault, you must separately make mail notification settings.
For details, refer to Technical reference: [Maintenance and operation functions] - [Mail notification] and to Web GUI help: [Advanced settings] - [Mail notification].
5.3. Checking the state of a monitored terminal
The state of a specified monitored terminal can be checked in the terminal monitoring gadget of the dashboard.
Dashboard terminal monitoring gadget

- For each monitored terminal, this shows the monitoring target, model name, monitoring type, and status.
- The following three states are shown as the state of the monitored terminal.
- Idle: Monitoring is not yet being performed:
- Up: The monitored terminal is operating correctly:
- Down: The monitored terminal is not operating correctly:
- Idle: Monitoring is not yet being performed:
- When you place the mouse cursor on the status field, the status of the monitored terminal is shown.
- If you click the [Idle] , [Up], or [Down] button in the upper part of the dashboard, only the monitored terminals that are in the corresponding state are shown. (The [All] button shows terminals of all states.)
- If not even one monitor terminal is registered, the display indicates “No monitored terminals are registered.”
6 Points of Caution
None
7 Related Documentation
- SWR2310 Series Technical Data (Basic Functions)
- Maintenance and operation functions
- Performance observation
Performance observation
1 Function Overview
This product provides a mechanism for constantly observing the system’s performance.
An overview of the function is given below.
Performance observation

This product constantly observes the following two types of data.
- Resource usage: CPU and memory usage
- Traffic amount: The amount of communication port bandwidth used (transmission/reception)
Based on the results of observation, one year’s worth of the following change data is accumulated inside this product.
- Hourly change: Change for each hour (e.g. 0:00, 1:00, ...)
- Daily change: Change for each day of each month (e.g. 1/1, 1/2, ...)
- Weekly change: Change for each day of the week (e.g. SUN, MON, ...)
- Monthly change: Change for each month (e.g. Jan, Feb, ...)
The accumulated data can be backed up to an SD card. By accessing this product via the Web GUI, the maintainer can view the various types of change data including live data in the dashboard, and can also acquire the accumulated result in a PC.
Since the acquired data is in CSV format, it can also be manipulated using spreadsheet software on a PC.
By using this function, the maintainer can accomplish the following:
- Ascertain the short-term communication status
- Predict long-term future demand for network facilities
2 Definition of Terms Used
None
3 Function Details
3.1 Resource and traffic usage observation
Starting immediately after boot, this device automatically observes the CPU and memory and the transmit/receive throughput of each port every second.
The observed data is normalized using a moving average, and one year of data is saved in RAM.
3.3 Observation data backup
Backup of observation data can be specified only in the Web GUI.
Backup of observation data assumes that an SD card is inserted in this device.
If backup is enabled, the most recent hour of observation data every hour starting at the point it was enabled (e.g., 1:00, 2:00 ...) is saved on the SD card.
The saved data is dedicated binary data of this device.
The save-destination on the SD card and the file name of the backup data file are as follows.
Resource information
- Hourly change data
/[model name]/data/resource/YYYYMM_smsys_res_monitor_hour.bin
- Daily change data (data for each day)
/[model name]/data/resource/YYYYMM_smsys_res_monitor_day.bin
- Weekly change data
/[model name]/data/resource/YYYYMM_smsys_res_monitor_week.bin
- Monthly change data
/[model name]/data/resource/YYYY_smsys_res_monitor_month.bin
- Hourly change data
Traffic information
- Hourly change data
/[model name]/data/trf/YYYYMM_trf_bandwidth_hour.bin
- Daily change data
/[model name]/data/trf/YYYYMM_trf_bandwidth_day.bin
- Weekly change data
/[model name]/data/trf/YYYYMM_trf_bandwidth_week.bin
- Monthly change data
/[model name]/data/trf/YYYY_trf_bandwidth_month.bin
- Hourly change data
- [Model name] is the following.
- For the SWR2310-10G/18GT/28GT: swr2310
- For the SWR2311P-10G: swr2311p
- For the SWP2-10SMF/MMF: swp2
- YYYY: year, MM: month are specified.
- Since this is a proprietary Yamaha format, it cannot be referenced.
3.4. Observation data export
Export of observation data to a PC can be executed only in the Web GUI.
As with backup data, export of observation data to a PC assumes that an SD card is inserted in this device.
The exported data is multiple CSV files compressed in zip format. The structure of the compressed files are given below.
- When resource observation data is exported
- zip file name: YYYYMMDDhhmmss_resource_csv.zip
- Folder structure
YYYYMMDDhhmmss_resource_csv +- 20170922_resource_hour.csv ... (CPU and memory data for each hour of 2017/9/22) +- : +- 20170925_resource_hour.csv ... (CPU and memory data for each hour of 2017/9/25) +- 201709_resource_day.csv ... (CPU and memory data for each day of 2017/9) - When transmission traffic observation data is exported
- zip file name: YYYYMMDDhhmmss_trf_tx_csv.zip
- Folder structure
YYYYMMDDhhmmss_trf_tx_csv +- 20170922_trf_tx_hour.csv ... (Transmission traffic data for each hour of 2017/9/22) +- : +- 20170925_trf_tx_hour.csv ... (Transmission traffic data for each hour of 2017/9/25) +- 201709_trf_tx_day.csv ... (Transmission traffic data for each day of 2017/9) - When reception traffic observation data is exported
- zip file name: YYYYMMDDhhmmss_trf_rx_csv.zip
- Folder structure
YYYYMMDDhhmmss_trf_rx_csv +- 20170922_trf_rx_hour.csv ... (Reception traffic data for each hour of 2017/9/22) +- : +- 20170925_trf_rx_hour.csv ... (Reception traffic data for each hour of 2017/9/25) +- 201709_trf_rx_day.csv ... (Reception traffic data for each day of 2017/9)
- YYYYMMDDhhmmss specifies the date and time at which export was executed (the date and time that the file was generated).
4 Related Commands
This function does not support settings via commands.
5. Settings via the Web GUI
Performance observation can be controlled from the following pages of the Web GUI.
- Viewing the resource usage amount
- This can be viewed in the [Dashboard] item [Resource information (graph)].
- Viewing the traffic usage amount
- This can be viewed in the [Dashboard] item [Traffic information (graph)].
- Backing up, clearing, or exporting observation data
- Select [Management], and then use [Maintenance] - [Summary data management] to make these settings.
Details on how to view and make settings in each screen can be referenced via the Web GUI help.
5.1 Viewing the resource usage amount
The resource information (graph) screen is shown below.
Example when Live is selected for resource information (graph)

- The graph rendering can be changed using the following buttons.
Current status: [Live]
The various current usage ratios are obtained at one-second intervals and shown on the graph.
Hourly change: [Day]
The various usage ratios for the specified day are shown at one-hour intervals on the graph.
To specify the day, use the day-specifying box in the upper right of the gadget.
Daily change: [Month]
The various usage ratios for the specified month are shown at one-day intervals.
To specify the month, use the month-specifying box in the upper right of the gadget.
Monthly change: [Year]
The various usage ratios for the specified year are shown at one-month intervals.
To specify the year, use the select box in the upper right of the gadget.
- It is not currently possible to reference changes in the day of the week.
- If the CPU and memory usage ratios exceed 80%, then a warning message is shown on the dashboard.
If the ratio falls below 80% after having exceeded 80%, the warning is automatically cleared.
5.2 Viewing the traffic usage amount
The traffic usage amount (graph) screen is shown below.
Example of when traffic usage amount (graph) Day is selected / Example of transmission traffic
- The traffic usage amount of each port can be shown separately for transmission and reception.
- The graph rendering can be changed using the following buttons.
Current status: [Live]
The various current usage ratios are obtained at one-second intervals and shown on the graph.
The most recent two minutesof the obtained data is held and rendered on the graph.
Hourly change: [Day]
The various usage ratios for the specified day are shown at one-hour intervals on the graph.
To specify the day, use the day-specifying box in the upper right of the gadget.
Daily change: [Month]
The various usage ratios for the specified month are shown at one-day intervals.
To specify the month, use the month-specifying box in the upper right of the gadget.
Monthly change: [Year]
The various usage ratios for the specified year are shown at one-month intervals.
To specify the year, use the select box in the upper right of the gadget.
- It is not currently possible to reference changes in the day of the week.
To select the interface to be shown, click the interface select button (
), and then make a selection in the following screen.
- If the traffic usage ratio exceeds 60%, a warning message is shown on the dashboard. If the ratio falls below 50% after having exceeded 60%, the warning is automatically cleared.
5.3 Backing up, clearing, or exporting observation data
Backup, clearing, and exporting of observation data is performed from [Management] - [Maintenance] - [Summary data management].
The Summary data management screen is shown below.
Summary data management screen (top page)

5.3.1 Observation data backup settings
Backup settings for observation data are performed from [Top page] - [Backup settings for summary data].
The screen that appears when you press the [Settings] button is shown below.
- Observation data backup settings screen
- Place a check mark in the check box of the summary data for which you want to enable backup, and then press the [Confirm] button.
After you press the button, the following screen appears.
- If you decide to cancel this setting, press the [Back] button in each screen.
5.3.2 Clearing observation data
Clearing the observation data is performed from [Top page] - [Clearing summary data].
The screen that appears when you press the [Next] button is shown below.
- Clear observation data screen
- In the select box, choose the statistical data that will be cleared, and press the [Confirm] button. After you press the button, the following screen appears.
- If you decide to cancel this operation, press the [Back] button in each screen.
5.3.3 Exporting observation data
Exporting observation data is performed from [Top screen] - [Export summary data].
The screen that appears when you press the [Next] button is shown below.
- Observation data export screen
- From the select box, choose the observation data that you want to export to the PC that is accessing the Web GUI, and then specify the term of observation data that you want to export.
After making the selection, press the [OK] button, and the following screen will appear.
- If you decide to cancel this operation, press the [Back] button in each screen.
6 Points of Caution
None
7 Related Documentation
None
- SWR2310 Series Technical Data (Basic Functions)
- Maintenance and operation functions
- Dante optimization setting function
Dante optimization setting function
1 Function Overview
Dante optimization settings is a function that makes it easy to specify the optimal environment for the Dante digital audio network.
This allows the user to easily make settings such as QoS settings, IGMP snooping settings, flow control disable settings, and EEE disable settings.
The following items can be set using the Dante optimization setting function.
| Object of setting | Function | Command |
|---|---|---|
| Entire system | Disable flow control | flowcontrol disable |
| Enable QoS | qos enable | |
| Optimize transmission queue by DSCP value | qos dscp-queue | |
| VLAN interface | Enable IGMP snooping | ip igmp snooping enable |
| Enable IGMP query transmission function | ip igmp snooping querier | |
| Set IGMP query transmission interval | ip igmp snooping query-interval | |
| Disable IGMP packet TTL value checking function | ip igmp snooping check ttl disable | |
| LAN/SFP port | Set QoS trust mode to DSCP | qos trust dscp |
| Disable flow control | flowcontrol disable | |
| Disable EEE | eee disable |
Use the Dante optimization setting function after you have made all of the basic switch settings (such as VLAN and IP).
If you make new changes to the settings, the Dante optimization settings will not follow.
2 Definition of Terms Used
- Dante
- A digital audio network specification developed by the Audinate Corporation.
3 Function Details
This function provides the following operations.
- Automatic optimization settings using LLDP
- Manual optimization settings via the Web GUI
3.1 Automatic optimization settings using LLDP
By receiving special LLDP frames from certain Dante-enabled devices made by Yamaha, optimal settings for using Dante can be automatically applied.
Automatic optimization settings via LLDP are set by the lldp auto-setting command.
By default, this product is set to enable automatic optimization settings via LLDP.
Certain Dante-enabled devices made by Yamaha transmit Yamaha-proprietary LLDP frames that include the following content.
- EEE (Energy-Efficient Ethernet) disable setting
- Flow control disable setting
- Diffserve base QoS setting
- IGMP snooping setting
If this function is enabled and the corresponding LLDP frame is received, the following settings are automatically applied to running-config.
[System-wide]
flowcontrol disable ... (Disable flow control) qos enable ... (Enable QoS) qos dscp-queue 0 0 ... (Set the DSCP-transmission queue ID conversion table; same for the following) qos dscp-queue 1 0 qos dscp-queue 2 0 qos dscp-queue 3 0 qos dscp-queue 4 0 qos dscp-queue 5 0 qos dscp-queue 6 0 qos dscp-queue 7 0 qos dscp-queue 8 2 qos dscp-queue 9 0 qos dscp-queue 10 0 qos dscp-queue 11 0 qos dscp-queue 12 0 qos dscp-queue 13 0 qos dscp-queue 14 0 qos dscp-queue 15 0 qos dscp-queue 16 0 qos dscp-queue 17 0 qos dscp-queue 18 0 qos dscp-queue 19 0 qos dscp-queue 20 0 qos dscp-queue 21 0 qos dscp-queue 22 0 qos dscp-queue 23 0 qos dscp-queue 24 0 qos dscp-queue 25 0 qos dscp-queue 26 0 qos dscp-queue 27 0 qos dscp-queue 28 0 qos dscp-queue 29 0 qos dscp-queue 30 0 qos dscp-queue 31 0 qos dscp-queue 32 0 qos dscp-queue 33 0 qos dscp-queue 34 0 qos dscp-queue 35 0 qos dscp-queue 36 0 qos dscp-queue 37 0 qos dscp-queue 38 0 qos dscp-queue 39 0 qos dscp-queue 40 0 qos dscp-queue 41 0 qos dscp-queue 42 0 qos dscp-queue 43 0 qos dscp-queue 44 0 qos dscp-queue 45 0 qos dscp-queue 46 5 qos dscp-queue 47 0 qos dscp-queue 48 0 qos dscp-queue 49 0 qos dscp-queue 50 0 qos dscp-queue 51 0 qos dscp-queue 52 0 qos dscp-queue 53 0 qos dscp-queue 54 0 qos dscp-queue 55 0 qos dscp-queue 56 7 qos dscp-queue 57 0 qos dscp-queue 58 0 qos dscp-queue 59 0 qos dscp-queue 60 0 qos dscp-queue 61 0 qos dscp-queue 62 0 qos dscp-queue 63 0
[VLAN interface that received LLDP]
interface vlanX *Applies to the VLAN ip igmp snooping enable ... (Enable IGMP snooping) ip igmp snooping query-interval 30 ... (Set query transmission interval) ip igmp snooping querier ... (Set query) ip igmp snooping check ttl disable ... (Disable IGMP packet TTL value checking function)
[LAN/SFP port that received LLDP]
interface portX.X qos trust dscp ... (Set DSCP trust mode) flowcontrol disable ... (Disable flow control) eee disable ... (Disable EEE)
If you save using the copy running-config startup-config command or the write command, the settings are also applied to the startup-config that is used for the next and subsequent startups.
Even if the port to which the device is connected experiences a link-down state after automatic optimization settings, the automatically added settings are maintained.
This function can be used only for a physical interface (LAN/SFP port). It cannot be used with a link aggregated logical interface.
This does not apply to the trunk port.
In order to use this function, reception of LLDP frames must be enabled.
For this reason, check in advance that the following settings have been made.
- Use the lldp run command to enable the system-wide LLDP function.
- Use the lldp-agent command to create an LLDP agent for the applicable interface.
- Use the set lldp command to specify the LLDP frame transmit/receive mode.
With the default settings of this product, LLDP frame transmission and reception is enabled.
3.2 Manual optimization settings via the Web GUI
The Web GUI of this product allows you to manually specify Dante optimization settings and to enable/disable automatic settings using LLDP.
If manual settings are executed, the settings shown in 3.1 Automatic optimization settings via LLDP are specified for all LAN/SFP ports and VLAN interfaces.
In addition, the no shutdown command is set for the VLAN interface.
Dante optimization settings are performed from [Management] - [Dante optimization].
The Dante optimization screen is shown below.
Dante optimization screen (top page)

To execute manual settings, press the [Next] button for Manual settings.
To enable/disable automatic settings, press the [Setting] button for Automatic settings using LLDP.
3.2.1 Manual settings
The screen that appears when you press the [Next] button for Manual settings is shown below.
Manual settings - execution screen

To execute manual settings, press the [OK] button.
3.2.2 Auto-configure via LLDP
The screen that appears when you press the [Setting] button for Auto-configure via LLDP is shown below.
Auto-configure via LLDP - execution screen

To enable/disable the automatic setting function using LLDP, select the [Enable] or [Disable] radio button, and then press the [Confirm] button.
The screen that appears when you press the [Confirm] button is shown below.
Auto-configure via LLDP - confirmation screen

To enable/disable automatic settings using LLDP, press the [OK] button.
4 Related Commands
Related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Set Dante automatic optimization settings function using LLDP | lldp auto-setting |
| Enable LLDP function | lldp run |
| Create LLDP agent | lldp-agent |
| Set LLDP transmission/reception mode | set lldp |
| Set flow control (system) | flowcontrol |
| Enable QoS | qos |
| Set DSCP - transmission queue ID conversion table | qos dscp-queue |
| Enable/disable IGMP snooping | ip igmp snooping |
| Set IGMP query transmission function | ip igmp snooping querier |
| Set IGMP query transmission interval | ip igmp snooping query-interval |
| Set IGMP packet TTL value checking function | ip igmp snooping check ttl disable |
| Set flow control (interface) | flowcontrol |
| Set QoS trust mode | qos trust |
| Set EEE | eee disable |
5 Examples of Command Execution
5.1 Automatic optimization settings using LLDP
Enable automatic optimization settings using LLDP.
Enable LLDP transmission and reception on port1.1.
Yamaha#configure terminal Yamaha(config)#interface port1.1 Yamaha(config-if)#lldp-agent ... (Create LLDP agent and transition modes) Yamaha(lldp-agent)#set lldp enable txrx ... (Set LLDP transmission/reception mode) Yamaha(lldp-agent)#exit Yamaha(config-if)#exit Yamaha(config)#lldp run ... (Enable LLDP function) Yamaha(config)#lldp auto-setting enable ... (Enable automatic optimization settings using LLDP)
6 Points of Caution
- Note that if you use this function when settings such as QoS settings, flow control settings, EEE settings, and IGMP snooping have already been made, those settings are overwritten by Dante-optimized settings.
- It is assumed that you will use the Dante optimization setting function after you have made all of the basic switch settings (such as VLAN and IP).
If you make new changes to the settings (such as adding a VLAN), the Dante optimization settings will not follow. - The setting values requested from Dante-enabled devices must be consistent between all devices. If the values are different, operation cannot be guaranteed.
- In general, IGMP snooping operates as version “3”.
7 Related Documentation
Stack function
1 Function Overview
A stack is a function that connects multiple switches and operates as a single virtual switch.
The features of the stack are shown below.
Realization of highly efficient redundancy
There are two methods for removing single points of failure (SPOF) in the network configuration: the method composed of VRRP and STP, and the method composed of stack and link aggregation.
By using the stack, unlike VRRP, there is no standby switch, so you can increase the usage efficiency of the switch while ensuring redundancy.
Easy port expansion
You can easily increase the number of available ports by adding switches.
Stack overview
The stack function is disabled when shipped from the factory.
2 Definition of Terms Used
- Member switch
Network switches that make up the stack.
Each switch is identified by a stack ID.
- Stack ID
An ID that identifies the member switches that make up the stack.
The stack ID can be set from 1 to the maximum number of stacks that can be configured (currently 2).
- Master switch
A switch that manages the network switches that make up the stack.
By default, the switch with stack ID 1 operates as the master switch.
- Slave switch
A network switch managed by the master switch.
By default, a switch with a stack ID other than 1 operates as a slave switch.
- Virtual switch
A single logical switch consisting of multiple member switches using the stack function.
- Stack port
SFP+ slot used to connect the network switches that make up the stack.
- Stack link
A connection between member switches that make up a stack.
3 Function Details
3.1 Stack configuration
The configurations that can be stacked for each model are shown below.
Only two units of the same model are supported.
Note that the stack must be configured with two stack links in order to reduce the impact of failure.
SWR2310-28GT stack configuration
3.2 Connection between member switches
When the stack function is enabled, the following SFP+ slots are switched to stack ports as connecting ports between members.
- SWR2310-28GT: ports 27, 28
Unlike normal communication ports, stack ports are used only for communication between member switches.
Connection between member switches is only possible with the direct attach cable (DAC-SWRT-1M/3M) or SFP+ module (SFP-SWRT-SR/LR) provided by Yamaha.
When connecting with another company’s product, the stack link will be forced down.
The stack port to be connected connects the lower number port and the higher number port of the member switch.
3.3 Master switch selection and MAC address assignment
The master switch selection and MAC address assignment rules are shown below.
Note that the MAC address used in the stack configuration is applied according to the following rules in order to eliminate the impact on communication.
- In the initial stack configuration, the MAC address of the master switch (switch with ID 1) is used as the virtual switch MAC address.
- If a slave switch is disconnected (due to an error) during stack configuration, the virtual switch continues to use the configured MAC address.
- If a master switch is disconnected (due to an error) during stack configuration, the virtual switch continues to use the configured MAC address.
In other words, the MAC address of the switch that is not included in the stack configuration is used.
- Even when a switch other than the failed switch (a switch with a different MAC address) is installed as a member switch, the virtual switch continues to use the configured MAC address.
If you want to reconfigure the stack with the current configuration status, restart the virtual switch at the same time to perform reconstruction.
(ID 1 is the master switch, and the virtual switch uses the MAC address of the master switch.)
Master switch selection and MAC address assignment
| No | Stack configuration | Master selection rules | |
|---|---|---|---|
| 1 | Initial composition |  | The switch with stack ID 1 is elected as the master switch. At this time, the MAC address of stack ID 1 is used as the virtual switch MAC address. |
| 2 | Fault occurrence |  | If an error occurs in the master switch, the switch with the smallest stack ID among the member switches is elected as the master switch. At this time, the virtual switch MAC address retains the MAC address of stack ID 1. |
| 3 | Abnormal state recovery |  | When the failed switch is re-installed in the stack, the currently elected master switch retains its function as the master switch. At this time, the virtual switch MAC address retains the MAC address of the faulty stack ID 1. |
3.4 Operations on virtual switches
Operations on virtual switches in a stack configuration are basically controlled from the master switch.
The specifications related to operation are shown below.
- When you log in to the virtual switch, you are always logged in to the master switch.
If necessary, use the remote-login command to log in to the slave switch.- Prompt when logging in to master switch
Yamaha>
- Prompt when logging in to slave switch
Yamaha-2> ... (Stack ID is displayed after the host name)
- Prompt when logging in to master switch
- The configuration (running-config, startup-config) for the virtual switch is always synchronized between member switches.
After completing the configuration, be sure to save running-config with the write command.
The write command can only be executed from the master switch side.
- When operating a virtual switch, the information stored in the L2 network switch (e.g. FDB learning information, ARP cache, etc.) is automatically synchronized.
There is no need for the user to be aware of this.
- Use the show logging command to show logging for the virtual switch after logging in.
The logging shown in this state is the master switch logging. If you want to show the slave switch logging, log in to the relevant switch using the remote-login command and show the logging.
3.5 Switch status when stacking
The member switch manages the status in the stack configuration as follows.
This state can be shown using the show stack command.
Setting
- A state in which one or more stack port links are up, and the settings necessary for stacking between member switches are performed.
Specifically, the configuration is automatically ascertained between member switches.
- A state in which one or more stack port links are up, and the settings necessary for stacking between member switches are performed.
Active
- A state in which automatic recognition of the configuration between member switches is completed, various settings are synchronized, and virtualization is performed by multiple member switches.
Virtualization is performed by two or more switches.
- A state in which automatic recognition of the configuration between member switches is completed, various settings are synchronized, and virtualization is performed by multiple member switches.
Inactive
- A state in which a failure has occurred and the virtual switch has been removed.
All communication ports including the stack port are forcibly shut down and communication cannot be established. (Closed state)
- A state in which a failure has occurred and the virtual switch has been removed.
Standalone
- The stack function is enabled, but since negotiation cannot be performed with the member switch, it is operating on one unit.
Transition to this state occurs when there is no opposing switch temporarily, such as during initial installation.
In this state, the stack ID that has been set must be enabled, so it is operated with the set ID.
- The stack function is enabled, but since negotiation cannot be performed with the member switch, it is operating on one unit.
Disable
- The stack function is disabled.
In this state, the stack ID is forcibly operated at 1. (Even if the stack ID is set to other than 1)
- The stack function is disabled.
3.6 Detection and measures for abnormal conditions
When a member switch in the stack configuration detects an error, it tries to resolve it autonomously within the virtual switch so that the network service is not affected.
This switch monitors the following abnormal conditions.
Abnormality detection on the local node
- Does not meet stack configuration conditions (stack ID error, firmware version error)
- Stack link error (down detection)
- Voltage value error
- Current value error
Connection node error detection
- Heartbeat frame reception timeout
Heartbeat is a function to check whether member switches are operating normally.
If the heartbeat frame is not received for a certain period (currently 4 seconds), it is determined that an error has occurred in the member switch.
The operation when an error is detected is shown below.
Operation when fault is detected
| Detected node | Detected content | Operation after detection | State after detection | Remarks | |
|---|---|---|---|---|---|
| Master | Setting error | Abnormal stack ID or firmware version | As a virtual switch, it is determined that processing cannot be continued, and the network port and stack link are forcibly taken down and disconnected from the stack configuration. | Inactive | |
| Stack link down | One of the two links down | Maintain the master and realize two-way communication with one. | Active | ||
| Both links down | Maintain the master. | Standalone | Possible double master status | ||
| HW error | Voltage/current value error | As a master, it is determined that processing cannot be continued, and the network port and stack link are forcibly taken down and disconnected from the stack configuration. | Inactive | ||
| Heartbeat error | Notification from the slave disappeared | Continue to operate as a master. | Standalone or Active | If there is only one remaining configuration, Standalone | |
| Slave | Setting error | Abnormal stack ID or firmware version | As a virtual switch, it is determined that processing cannot be continued, and the network port and stack link are forcibly taken down and disconnected from the stack configuration. | Inactive | |
| Stack link down | One of the two links down | Maintain the slave and realize two-way communication with one. | Active | ||
| Both links down | Promote to master to continue service. | Standalone | Possible double master status | ||
| HW error | Voltage/current value error | As a slave, it is determined that processing cannot be continued, and the network port and stack link are forcibly taken down and disconnected from the stack configuration. | Inactive | ||
| Heartbeat error | Notification from the master disappeared | Promote to master to continue service. | Standalone or Active | If there is only one remaining configuration, Standalone | |
4 Related Commands
Related commands are shown below.
For details, refer to the Command Reference.
List of stack related commands
| Operations | Operating commands |
|---|---|
| Stack function enable/disable setting | stack |
| Change stack member ID | stack renumber |
| Stack port IP address range setting | stack subnet |
| Show stack information | show stack |
5 stack initial settings
The initial setting flow for stack configuration is shown below.
- Preparation of necessary equipment
- Member switch settings
- Connecting member switches
5.1 Preparation of necessary equipment
Prepare the equipment necessary to configure the stack.
Member switch
Prepare member switches for stack configuration.
For the stackable configuration, refer to 3.1 Stack configuration.
Stack port connection cable
Determine and prepare the interface to which the member switches are connected.
Use direct attach cables when configuring the stack in a rack, and SFP+ modules when a certain distance is required such as between floors or buildings.
For details, refer to 3.2 Connection between member switches.
External memory (SD card)
It is recommended to use external memory to save backup data such as configs and logs during stack operation.
By using external memory, you can use it to recover the config if a failure occurs.
5.2 Member switch settings
Set the member switches that constitute the stack.
Consider the following before you begin configuration.
Determine the stack IDs assigned to the member switches
The stack IDs assigned to the member switches must be determined statically.
During initial settings, stack ID: 1 is the master switch, and other IDs are slave switches.
Determine the IP address range of the stack port
The IP address range used for the stack port is 192.168.250.0/24 as the initial setting.
If the corresponding address is used on the operation network, it is necessary to change the IP address range of the stack port.
Determine the startup config save destination
Determine the save destination for the startup config during stack configuration.
Select the config ID in the flash ROM as the save destination and make it clear that it is to be used for saving the stack in the description.
After reviewing, configure member switches individually as follows.
Activate member switches
Start the member switches individually and access them from the serial console.
Check and update firmware version
Check the current firmware version with the show environment command.
Yamaha> show environment SWR2310-28GT BootROM Ver.1.00 SWR2310-28GT Rev.2.04.01 (Thu Sep 26 17:35:20 2019) ... (Check firmware version) main=SWR2310-28GT ver=00 serial=Z0000000XX MAC-Address=ac44.f200.0000 ...
Check the latest public firmware on Rt pro.
If the public firmware version of the relevant switch is newer than the firmware that is running, update it.- It is recommended that member switches be updated to the latest firmware with improvements made to known issues.
- By default, firmware update using an SD card is enabled.
Refer to Firmware update for how to update using an SD card.
Set the save destination for startup config
Use the startup-config select command to select the config to be used during stack operation.
At this time, it is recommended to set the description to use for the config during stack operation.
Yamaha> enable Yamaha# startup-config description 1 Stack ... (Set “Stack” and the description in startupconfig#1) Yamaha# startup-config select 1 ... (Select startup-config#1) reboot system? (y/n): y ... (Reboot)
Stack ID settings
Check the switch status with show stack and confirm that the stack function is disabled.
Also check the stack ID. The initial value of the stack ID is set to 1.
Yamaha> enable Yamaha# Yamaha# show stack Stack: Disable Configured ID: 1 Subnet on stack port : Auto-ip ID Model Status Role ------------------------------------- Yamaha#
If necessary, change the stack ID using the stack renumber command.Yamaha(config)# stack 1 renumber 2 ... (Change the stack ID from #1 to #2) Yamaha(config)# do show stack Stack: Disable Configured ID: 2 Subnet on stack port : 192.168.250.0 ID Model Status Role ------------------------------------- Yamaha#
Set the stack port IP address range
The IP address range used for the stack port is 192.168.250.0/24 as the initial setting.
If necessary, change the stack port IP address range using the stack subnet command.
Be sure to make the same setting on all member switches.
Yamaha(config)# stack subnet 192.168.255.0 ... (Change the IP address range to 192.168.255.0/24) Yamaha(config)# do show stack Stack: Disable Configured ID: 1 Subnet on stack port : 192.168.255.0 ID Model Status Role -------------------------------------
Enabling the stack function
Use the stack enable command to enable the stack function.
After entering the command, reboot the device.
After the reboot is complete, default-config is applied.
Yamaha(config)# stack enable ... (enable stack function) reset configuration and reboot system? (y/n): y ... (execute reboot)
After rebooting, check the switch status with show stack and confirm that the stack function is enabled.
Also check the save destination of the startup config.Yamaha> enable Yamaha# Yamaha# show stack Stack: Enable ... (Stack function is enabled) Configured ID: 1 Running ID : 1 Status : Standalone Subnet on stack port : 192.168.255.0 ID Model Status Role ------------------------------------- 1 SWR2310-28GT Standalone Master ... (Because it is operating with one unit, it is Standalone Master) Yamaha>show environment SWR2310-28GT BootROM Ver.1.00 SWR2310-28GT Rev.2.04.01 (Thu Sep 26 17:35:20 2019) main=SWR2310-28GT ver=00 serial=Z0000000XX MAC-Address=ac44.f200.0000 CPU: 12%(5sec) 5%(1min) 6%(5min) Memory: 11% used Startup firmware: exec0 Startup Configuration file: config1 ... (Confirm that the set startup config is applied) selected file: config1 Serial Baudrate: 9600 Boot time: 2019/10/10 22:52:22 +09:00 Current time: 2019/10/10 22:57:38 +09:00 Elapsed time from boot: 0days 00:05:21
5.3 Connecting member switches
Connect the enabled switches to the stack using a direct attach cable or SFP+ module.
Refer to 3.2 Connection between member switches for the connection method.
The member switches can be connected with the power turned off or the power turned on.
After connecting the member switches, check the system status using the show stack command.
Yamaha# show stack Stack: Enable Configured ID: 1 Running ID : 1 Status : Active Subnet on stack port : 192.168.255.0 ID Model Status Role ------------------------------------- 1 SWR2310-28GT Active Master ... (Switch with stack ID 1 is master) 2 SWR2310-28GT Active Slave ... (Switch with stack ID 2 is slave)
Use the backup system command to back up the initial setting status of the member switch to the SD card.
By saving swr2310.bin (firmware file) in the /swr2310/firmware folder in the SD card, both settings and firmware can be backed up during backup execution.
Yamaha> enable Yamaha# backup system ... (Copy all master switch settings to the SD card) Succeeded to backup system files and firmware file. Yamaha# remote-login 2 ... (Remote login to slave switch (stack ID: 2)) Entering character mode Escape character is '^]'. SWR2310-28GT Rev.2.04.01 (Thu Sep 26 17:35:20 2019) Copyright (c) 2018-2019 Yamaha Corporation. All Rights Reserved. Yamaha-2> enable Yamaha-2# backup system ... (Copy all slave switch settings to SD card) Succeeded to backup system files and firmware file.
This completes the initial stack settings.
Install the virtual switch in the network to be used and perform the settings required for operation.
After completing the settings required for operation, backup should be performed in case of an abnormality, just as with the initial settings.
6 Exchanging member switches
This section describes the exchange procedure when an error occurs in a member switch in a configuration that uses two SWR2310-28GTs.
The following shows each case of using and not using an SD card.
6.1 Exchange procedure using an SD card
Member switches are exchanged by backup/restore using an SD card.
Exchange procedure
During normal operation
After completing the setting to the member switches, back up the system information to the SD card in consideration of failure.
To back up system information, execute the backup system command.
Before performing backup, save swr2310.bin (firmware file) in the /swr2310/firmware folder on the SD card to back up the firmware.
Fault occurrence
Stack ID: Assume that an error occurred in the second slave device.
Fault recovery
Prepare the member switches to be exchanged and connect the SD card that contains the backup of the failed switches.
Apply the firmware and system information by executing the restore system command.
After application, turn off the power, connect to the active master switch, and turn on the power to restore the stack configuration.
6.2 Exchange procedure without using an SD card
Exchange the member switches without using an SD card.
At the start of operation
After installation of the member switches is completed, store the same revision firmware as the firmware written in the member switches on a PC, etc.
Record the serial number, config ID being used, and stack ID of each member switch.
Yamaha> show environment SWR2310-28GT BootROM Ver.1.00 SWR2310-28GT Rev.2.04.01 (Thu Sep 26 17:35:20 2019) main=SWR2310-28GT ver=00 serial=Z0000000XX MAC-Address=ac44.f200.0000 ... (Serial number) CPU: 12%(5sec) 5%(1min) 6%(5min) Memory: 11% used Startup firmware: exec0 Startup Configuration file: config1 ... (config ID) selected file: config1 Serial Baudrate: 9600 Boot time: 2019/10/10 22:52:22 +09:00 Current time: 2019/10/10 22:57:38 +09:00 Elapsed time from boot: 0days 00:05:21 Yamaha> show stack Stack: Enable Configured ID: 1 ... (Stack ID) Running ID : 1 Status : Active Subnet on stack port : 192.168.250.0 ID Model Status Role ------------------------------------- 1 SWR2310-28GT Active Master 2 SWR2310-28GT Active SlaveFault occurrence
Stack ID: Assume that an error occurred in the second slave device.
Fault recovery
Prepare the member switches to be exchanged and write the saved firmware.
Start the member switches and change the config ID used at startup.
* If the config ID used at the start of operation is 0, there is no need to change it.
Yamaha> enable Yamaha# startup-config select 1 reboot system? (y/n): y
After rebooting, enable the stack function.
For the stack ID to be set, refer to the member switch serial number and stack ID recorded at the start of operation.Yamaha> enable Yamaha# configure terminal Yamaha(config)# stack 1 renumber 2 ... (Set stack ID 2) Yamaha(config)# stack enable ... (Enable stack function) reset configuration and reboot system? (y/n): y
After enabling the stack function, turn off the power, connect to the active master switch, and turn on the power to restore the stack configuration.
7 Firmware update
The following two methods are provided for updating the firmware during stack configuration.
- Method to update member switches during configuration simultaneously (parallel update)
- Method to update without stopping network services (sequential update)
Parallel update is an effective method if you have enough time to allow a service outage.
However, during stack configuration, it is recommended to perform a sequential update without service interruption.
Note that firmware updates during stack configuration are supported only for the following.
- Update by sending update firmware using tftp client or Web GUI
- Using an SD card to update the firmware
If the firmware is updated while the SD card is inserted, SD card boot may be performed when restarting.
You can disable SD card boot with the boot prioritize sd command.
Yamaha> enable Yamaha# boot prioritize sd disable ... (Disable SD card boot) reboot system? (y/n): y
For details, refer to Firmware update.
7.1 Firmware parallel update
Firmware parallel update updates the firmware of the member switches in the stack configuration at the same time.
The service will be stopped because the entire virtual switch is restarted for the update.
Note the following points when performing parallel update.
- Confirm that the firmware update method is set to normal (firmware-update reload-method command)
- Confirm that the firmware update application time is set to the set time (firmware-update reload-time command)
An overview of parallel update is shown below.
Parallel update process flow
7.2 Firmware sequential update
Firmware serial update updates the firmware of the member switches in the stack configuration sequentially.
The service will not be stopped because the entire virtual switch is not restarted for the update. (* See Points of Caution 6)
Note the following points when performing sequential update.
- Confirm that the firmware update method is set to sequential (firmware-update reload-method command)
- Confirm that the firmware update application time is set to the set time (firmware-update reload-time command)
An overview of sequential update is shown below.
Sequential update process flow
8 Points of Caution
- When the stack function is enabled, the following functions cannot be used.
- RMON
- MLD snooping
- When the stack function is enabled, it can be used as a function, but some restrictions occur.
- Mirroring function
- Mirroring between member switches is not possible.
- Flow control
- Pause frame cannot be transmitted.
- Back pressure function
- When communicating via the stack port, jam signals are not transmitted.
- SFP optical reception level monitoring
- The optical reception level of the stack port is not monitored.
- Link aggregation
- Dynamic link aggregation (LACP) cannot be used.
- The maximum number of logical groups is reduced by one.
- Command line input
- The users who can transition to global configuration mode are limited.
When the console side is in global configuration mode and the telnet side transitions to global configuration mode, the console side automatically transitions to privileged EXEC mode.
Console, telnet, ssh, remote login, and GUI settings are exclusively controlled.
- It is not possible to log in from the master switch and slave switch consoles at the same time.
- The users who can transition to global configuration mode are limited.
- DHCP client
- If the stack function is enabled and the Auto IP function is used on the stack port, the DHCP client cannot be used.
- startup-config select command
- Do not use the startup-config select command while the stack is configured. It may become impossible to configure correctly.
To switch the config using the startup-config select command, disconnect the direct attach cable and cancel the stack configuration before executing.
- Do not use the startup-config select command while the stack is configured. It may become impossible to configure correctly.
- Mirroring function
- When the stack function is enabled, make sure that the stack configuration is configured before setting functions with commands or the GUI.
If the stack is not configured correctly, the settings may not be reflected correctly.
The write command and copy running-config startup-config command can be executed only on the master switch side (Active state).
They cannot be executed on the slave switch side or when the stack is not configured correctly.
- When the stack function is enabled, the stack control packets use transmission queues #7 and #6, so do not assign other packets to transmission queues #7 and #6.
When QoS is enabled, transmission queues #7 and #6 are assigned by default in the CoS-transmission queue ID conversion table, so change the assignment.
- When the stack function is enabled, the initial setting for the transmission queue specification for frames transmitted from the switch itself is transmission queue #6.
Do not change the transmission queue specification setting for frames transmitted from the switch itself from the default setting.
- If the member switches are reconnected due to device exchange or connection failure, etc., all communication will be temporarily stopped because it is in stack configuration.
The communication stop state is canceled after stack configuration is completed.
Even during firmware update (sequential update), the startup-config reflection period is temporarily stopped.
- If there is a difference in the settings (startup-config) on the master/slave switch during stack configuration, update the slave switch settings and reboot.
- If there is a difference in the IP address range settings of the stack port between the master switch/slave switch during stack configuration, communication between stacks cannot be performed normally.
9 Related Documentation
- SWR2310 Series Technical Data (Basic Functions)
- Maintenance and operation functions
- List of default settings
List of default settings
List of default settings
The default settings of the SWR2310 Series is shown below.
System-wide default settings
| Category | Setting item | Setting value |
|---|---|---|
| Terminal settings | Console timeout | 600 sec |
| Number of VTYs | 8 | |
| Number of lines displayed | 24 | |
| Password | Login password for unnamed user | None |
| Administrator password | None | |
| Password encryption | Don’t encrypt | |
| Time management | Time zone | JST (UTC+9.0) |
| NTP server | None | |
| NTP update cycle | Once per hour | |
| RMON | Operation | Enabled |
| Firmware update | Download URL | firmware-update url http://www.rtpro.yamaha.co.jp/firmware/revisionup/swr2310.bin |
| Permit downward revision | Don’t allow | |
| Timeout | 300 sec | |
| LLDP | Operation | Enabled |
| Automatic setting function | Enabled | |
| L2MS | Operation | Enabled |
| Role | Slave | |
| SYSLOG | Debug level log output | OFF |
| Information level log output | ON | |
| Error level log output | ON | |
| SYSLOG server | None | |
| Access control | Telnet server status | Start |
| Telnet server access | Allow only VLAN #1 | |
| SSH server status | Don’t start | |
| TFTP server status | Don’t start | |
| HTTP server status | Start | |
| HTTP server access | Allow only VLAN #1 | |
| Secure HTTP server status | Don’t start | |
| Management VLAN | VLAN interface | VLAN #1 |
| L2 switching | Automatic MAC address acquisition | Enabled |
| Automatic MAC address acquisition ageing time | 300 sec | |
| Spanning tree | Enabled | |
| Proprietary loop detection | Disabled | |
| DNS client | Operation | Enabled |
| Traffic control | QoS | Disabled |
| Flow control (IEEE 802.3x) | Disabled | |
| L3 routing | Inter-VLAN routing | Disabled |
| WebGUI | Language setting | English |
Default settings for each LAN/SFP port
| Category | Setting item | Setting value |
|---|---|---|
| Basic settings | Speed/communication mode setting | Auto |
| Cross/straight automatic detection | Enabled | |
| MRU | 1,522 bytes | |
| Port description | None | |
| EEE | Disabled | |
| Port Mode | Access | |
| Associated VLAN ID | 1 (default VLAN) | |
| L2MS | L2MS filter | Disabled |
| L2 switching | Spanning tree | Enabled |
| Proprietary loop detection | Enabled | |
| Traffic control | QoS trust mode | CoS |
| Flow control (IEEE 802.3x) | Disabled | |
| Storm control | Disabled | |
| LLDP agent | Transmission/reception mode | Transmission and reception |
Settings for default VLAN (vlan1)
- IPv4 Address: DHCP client
- IGMP Snooping: Enable
- Querier : Disable
- Fast-Leave : Disable
- Check TTL : Enable
- SWR2310 Series Technical Data (Basic Functions)
- Interface control functions
Interface control functions
- SWR2310 Series Technical Data (Basic Functions)
- Interface control functions
- Interface basic functions
Interface basic functions
1 Function Overview
Here we explain the basic interface functions of this product.
2 Definition of Terms Used
None
3 Function Details
3.1 Interface types
This product can handle the five interface types shown in the table below.
Interface list
| Interface types | Interface ID | Explanation |
|---|---|---|
| LAN port | port | A physical port of this product. There are two types: a fixed LAN port and a removable SFP+ port. This interface is expressed as port followed by “stack ID” + “.” + “port number printed on the chassis.” Specifying LAN port #1: port1.1 |
| SFP port | ||
| SFP+ port | ||
| VLAN interface | vlan | A user-defined VLAN. This interface is expressed as vlan followed by “VLAN ID.” Specifying VLAN1: vlan1 |
| Static logical interface | sa | This is the user-defined link aggregation. Multiple LAN/SFP ports can be grouped together and used as one interface. This interface is expressed as “sa” or “po,” followed by “logical link ID.” Specifying the LACP logical interface for logical link ID #1: po1 |
| LACP logical interface | po |
3.2 Interface control
The interface on this product can be controlled as shown in the table below.
Interface control items
| Control items | Commands | Explanation |
|---|---|---|
| Set description | description | Sets the description text for the applicable interface. |
| Enable/disable | shutdown | Enables/disables the interface. |
| Communication speed/communication mode | speed-duplex | Sets the communication speed and communication mode for the interface. (Select from the following values.)
|
| MRU | mru | Sets the maximum frame size that can be received by the interface, within a range of 64–10,240 bytes. |
| Cross/straight automatic detection (Auto MDI/MDI-X function) | mdix | This function automatically detects the connection port type (MDI or MDI-X), allowing for interconnection without relying on the cable type (cross or straight). |
| Speed downshift | - | This function automatically drops the speed and tries to link, when a LAN cable is connected for which 1000BASE-T cannot be used. This function is always enabled for LAN ports. (Cannot be disabled.) |
| EEE | eee | Specifies whether EEE (Energy-Efficient Ethernet) is used. This is standard for IEEE 802.3az. |
Command control of the interface is performed as shown on the table below.
Interface control functionality chart
| Interface name | Set description | Enable/disable | Communication speed/communication mode | MRU | Cross/straight automatic detection | EEE |
|---|---|---|---|---|---|---|
| LAN port | ✓ | ✓ | ✓ (*1) | ✓ | ✓ | ✓ |
| SFP port | ✓ | ✓ | ✓ (*2) | ✓ | - | - |
| SFP+ port | ✓ | ✓ | ✓ (*3) | ✓ | - | - |
| VLAN interface | ✓ | - | - | - | - | - |
| Static logical interface | ✓ | ✓ | - | - | - | - |
| LACP logical interface | ✓ | ✓ | - | - | - | - |
*1: As the communication speed / communication mode setting for a LAN port, it is not possible to select 10 Gbps / full-duplex.
*2: The communication speed / communication mode setting for an SFP port will be either auto negotiation or 1 Gbps / full-duplex.
*3: The communication speed / communication mode setting for an SFP+ port will be either auto negotiation or 10 Gbps / full-duplex.
When 10 Gbps / full duplex is set and an SFP module is connected, it operates as 1 Gbps / full-duplex.
3.3 LAN/SFP port defaults
Initially, this product’s LAN/SFP ports will be in the following state.
- All LAN/SFP ports function as access ports (ports that handle untagged frames), and belong to the default VLAN (VLAN #1).
- The following functions are enabled for the default VLAN (VLAN #1) to which all LAN/SFP ports belong.
- MSTP: Multiple Spanning Tree Protocol
- IGMP Snooping
- IPv4 address (192.168.100.240/24)
- Access from a Telnet client
- Access from a web client
3.4 Port mirroring
This product provides a port mirroring function, which copies the data traffic from a selected LAN/SFP port to another specified port.
The communication status can be analyzed by collecting the copied packets.
This product allows you to specify one mirror port, making all other LAN/SFP port allocable as “monitor ports”.
The monitoring direction (transmit/receive, transmit only, receive only) can be selected for the monitor ports.
The mirror command can be used to set the port mirroring.
The mirror port setting is disabled by default.
3.5 Frame counter
This product counts the number of frames transmitted/received for each LAN/SFP port. (This is called a “frame counter”.)
To reference the frame counter, use the show frame counter command.
The table below shows the display items for the frame counter and their maximum values.
Received frame counter display items
| Display item | Explanation | Maximum value |
|---|---|---|
| Octets | Number of octets received | 18,446,744,073,709,551,615 |
| Packets (*1) | Number of packets received | 34,359,738,360 |
| Broadcast packets (*2) | Number of broadcast packets received | 4,294,967,295 |
| Multicast packets (*2) | Number of multicast packets received | 4,294,967,295 |
| Unicast packets (*2) | Number of unicast packets received | 4,294,967,295 |
| Undersize packets (*2) | Number of undersize packets received (packets smaller than 64 octets) | 4,294,967,295 |
| Oversize packets (*2) | Number of oversize packets received (packets larger than 1,523 octets (*3)) | 4,294,967,295 |
| Fragments (*2) | Number of fragment packets received (packets smaller than 64 octets whose CRC is incorrect) | 4,294,967,295 |
| Jabbers (*2) | Number of jabber packets received (packets larger than 1,523 octets whose CRC is incorrect (*3)) | 4,294,967,295 |
| FCS errors (*2) | Number of FCS error packets received | 4,294,967,295 |
| RX errors | Number of reception errors | 4,294,967,295 |
| Drop packets (*4) | Number of packets dropped from the reception buffer | 4,294,967,295 |
(*1): Packets is the total value of the (*2) packets.
(*3): This will change, depending on the MRU that is set for the LAN/SFP port.
(4): This is shown only if tail drop is disabled.
Transmitted frame counter display items
| Display item | Explanation | Maximum value |
|---|---|---|
| Octets | Number of octets transmitted | 18,446,744,073,709,551,615 |
| Packets (*1) | Number of packets transmitted | 12,884,901,885 |
| Broadcast packets (*2) | Number of broadcast packets transmitted | 4,294,967,295 |
| Multicast packets (*2) | Number of multicast packets transmitted | 4,294,967,295 |
| Unicast packets (*2) | Number of unicast packets received | 4,294,967,295 |
| TX errors | Number of transmission errors | 4,294,967,295 |
| Collisions | Number of collision occurrences | 4,294,967,295 |
| Drop Packets(*3) | Number of tail-dropped transmission packets | 536,870,911 |
(*1): The packet value is the total of the (*2) packets.
(3): This is shown only if tail drop is enabled.
Transmitted/received frame counter display items
| Display item | Explanation | Maximum value |
|---|---|---|
| 64 octet packets | Number of packets with 64 octet length transmitted/received | 4,294,967,295 |
| 65–127 octet packets | Number of packets with 65–127 octet length transmitted/received | 4,294,967,295 |
| 128–255 octet packets | Number of packets with 128–255 octet length transmitted/received | 4,294,967,295 |
| 256–511 octet packets | Number of packets with 256–511 octet length transmitted/received | 4,294,967,295 |
| 512–1,023 octet packets | Number of packets with 512–1,023 octet length transmitted/received | 4,294,967,295 |
| 1,024–MAX octet packets | Number of packets with 1,024–maximum octet length (*1) transmitted/received | 4,294,967,295 |
(*1): This will change, depending on the MRU that is set for the LAN/SFP port.
The frame counter can also be cleared by using the clear counters command.
When you execute the show interface command which shows the status of the LAN/SFP ports, information on the number of transmitted and received frames is shown, but this information is shown based on the frame counter information.
The number of frames transmitted/received that is displayed using the show interface command and how the frame counter is handled are shown below.
- Number of frames transmitted/received that is displayed by the show interface command, and how the frame counter is handled
Display item Information on the frame counter referred to input packets Received frame counter packets bytes Received frame counter octets multicast packets Received frame counter multicast packets drop packets(*1) Received frame counter drop packets output packets Transmitted frame counter packets bytes Transmitted frame counter octets multicast packets Transmitted frame counter multicast packets broadcast packets Transmitted frame counter broadcast packets drop packets(*1) Transmitted frame counter drop packets (*1) If tail drop is enabled this shows only the transmission information; if it is disabled this shows only the reception information.
3.6 SFP module optical receive level monitoring
This product provides functionality for monitoring the optical receive level of an SFP/SFP+ module connected to the SFP/SFP+ port.
If a fault occurs in an SFP/SFP+ module’s optical receive level, this product’s port lamp indications change to a dedicated state, and a SYSLOG message is output.
When the optical receive level returns to the normal range, this product’s port lamp indications will recover, and a SYSLOG message is output.
The SYSLOG message is not output when the corresponding port is linked down.
The SFP/SFP+ module’s optical receive level monitoring settings can be made using the sfp-monitor command.
By default, SFP module optical receive level monitoring is enabled.
3.7 Transmit queue usage monitoring
If the transmit queue’s usage ratio becomes high (above 60%, above 100%), a SYSLOG message is output.
A SYSLOG message is also output when the transmit queue’s usage ratio returns to the normal range (below 50%).
Transmit queue usage monitoring is always enabled.
4 Related Commands
The related commands are shown below.
For details on the commands, refer to the Command Reference.
Basic interface functions: list of related commands
| Operations | Operating commands |
|---|---|
| Set description | description |
| Shutdown | shutdown |
| Set communication speed and communication mode | speed-duplex |
| Set MRU | mru |
| Set cross/straight automatic detection | mdix auto |
| Set EEE | eee |
| Show EEE capabilities | show eee capabilities |
| Show EEE status | show eee status |
| Set port mirroring | mirror |
| Show mirroring port status | show mirror |
| Show interface status | show interface |
| Show frame counter | show frame-counter |
| Clear frame counters | clear counters |
| Show SFP/SFP+ status | show ddm status |
| Set SFP module optical receive level monitoring | sfp-monitor rx-power |
5 Examples of Command Execution
5.1 Basic LAN port settings
Some examples of basic LAN port settings are shown below.
For details on how to make the settings, refer to the Command Reference.
- Set the description text for LAN port #1 (port1.1).
Yamaha(config)#interface port1.1 Yamaha(config-if)#description Connected to rtx1200-router
- Disable LAN port #1 (port1.1).
Yamaha(config)#interface port1.1 Yamaha(config-if)#shutdown
- Enable LAN port #1 (port1.1).
Yamaha(config)#interface port1.1 Yamaha(config-if)#no shutdown
- Set the communication speed and communication mode for LAN port #1 (port1.1) to 100Mbps/Full.
Yamaha(config)#interface port1.1 Yamaha(config-if)#speed-duplex 100-full
5.2 Mirroring settings
In this example, we will set LAN port #1 to monitor the frames transmitted/received by LAN port #4 and the frames transmitted by LAN port #5.
The roles of the ports are shown below.
- Mirror port: LAN port #1 (port1.1)
- Monitor port: LAN port #4 (port1.4), LAN port #5 (port1.5)
- Set the monitor port for mirror port LAN port #1 (port1.1).
Yamaha(config)#interface port1.1 Yamaha(config-if)#mirror interface port1.4 direction both ... (Monitor transmission/reception frames) Yamaha(config-if)#mirror interface port1.5 direction transmit ... (Monitor transmission frames)
- Confirm the mirroring settings.
Yamaha#show mirror Monitor Port Mirror Port Mirror Option Direction ============= ============ ============== ========== port1.1 port1.4 enable both port1.5 enable transmit
5.3 Show LAN/SFP port information
- Confirm the status of LAN port #1 (port1.1).
Yamaha#show interface port 1.1 Interface port1.1 Link is UP Hardware is Ethernet HW addr: 00a0.deae.b89f Description: Connected to router ifIndex 5001, MRU 1522 Speed-Duplex: auto(configured), 1000-full(current) Auto MDI/MDIX: on Vlan info : Switchport mode : access Ingress filter : enable Acceptable frame types : all Default Vlan : 1 Configured Vlans : 1 Interface counter: input packets : 0 bytes : 0 multicast packets: 0 output packets : 0 bytes : 0 multicast packets: 0 broadcast packets: 0 drop packets : 0
6 Points of Caution
None
7 Related Documentation
None
Link aggregation
1 Function Overview
Link aggregation is a function used to combine multiple LAN/SFP ports that connect network devices, and handle them as a single logical interface.
Link aggregation is a technology that is useful when multiple communications occur. Communications can be distributed by using a load balance function within the combined lines.
If one LAN/SFP port fails within the lines that were combined using link aggregation, and communications cannot be made, the other ports will continue communicating.
Link aggregation function overview
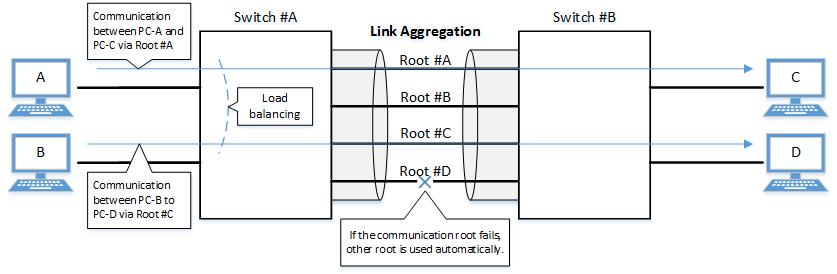
The link aggregation functions in this L2 switch are shown below.
Link aggregation functions
| Functions provided | Contents |
|---|---|
| Static link aggregation | Link aggregation for manually setting the LAN/SFP ports to combine. This begins to operate as a logical interface when the LAN/SFP ports link up. |
| LACP link aggregation | Link aggregation that uses LACP to combine the LAN/SFP ports. This begins to operate as a logical interface when the negotiation via LACP between the connected devices is successful. |
2 Definition of Terms Used
- LACP
Abbreviation for “Link Aggregation Control Protocol”. This is a technology standardized in IEEE802.3ad,
and is also called EtherChannel.
- Load balance
This is a function to distribute forwarded frames between the LAN/SFP ports that are associated with the logical interface.
As a distribution rule, the L2/L3/L4 information within frames is used.
3 Function Details
3.1 Static/LACP link aggregation: common specifications
The common specifications for the static/LACP link aggregation functions of this L2 switch are shown below.
- The link aggregation on this L2 switch can be defined for 127 interfaces, including both static and LACP.
A single logical interface can be associated with up to eight LAN/SFP ports.
- The settings shown below must be the same for each of the LAN/SFP ports contained within.
- Communication speed/communication mode
If auto negotiation is enabled, only the same port that was used in the contained ports for the initial negotiation results will be contained.
- Port mode (access/trunk [including native VLAN settings])
- Associated VLAN
- QoS trust mode (including port priority and default CoS settings)
- Communication speed/communication mode
- The following operations are performed when a LAN/SFP port is associated with a logical interface.
- LAN/SFP ports that are linked up will be linked down.
The logical interface’s default value will be set to shutdown, in order to safely integrate the logical interface into the system.
- MSTP settings will be discarded and will revert to their defaults.
When dissociating a LAN/SFP port from the logical link, the MSTP settings for the relevant port will revert to their defaults as well.
- LAN/SFP ports that are linked up will be linked down.
- The following operations can be performed for the logical interface.
- Add description text (description command)
- Enable/disable the interface (shutdown command)
- Another LAN/SFP port cannot be associated with a logical interface in operation.
To associate a LAN/SFP port, make sure to shut down the logical interface before associating.
- LAN/SFP ports that are associated with a logical interface that is in operation cannot be removed.
When dissociating a LAN/SFP port, make sure to shut down the logical interface before dissociating.
LAN/SFP ports that have been dissociated from a logical interface will be in shutdown mode. Enable the ports as necessary (using “no shutdown”).
- Load balance settings can be made on the logical interface. The rules that can be set for this are shown below.
The default value when defining a logical interface is the destination/source MAC address.
- Destination MAC address
- Source MAC address
- Destination/source MAC address
- Destination IP address
- Source IP address
- Destination/source IP address
- Destination port number
- Source port number
- Destination/source port number
3.2 Static link aggregation
The operating specifications for static link aggregation are shown below.
- An interface number from 1–96 can be assigned to the static logical interface.
- Use the static-channel-group command to associate a LAN/SFP port with a static logical link interface.
- When associating a LAN/SFP port with an interface number for which there is no static logical interface, a new logical interface will be generated.
- When the associated port no longer exists as a result of removing a LAN/SFP port from a static logical interface, the relevant logical interface will be deleted.
- Use the show static-channel-group command to show the static logical link interface’s status.
3.3 LACP link aggregation
The operating specifications for LACP link aggregation are shown below.
Refer to “3.1 Static/LACP link aggregation: common specifications” for the common specifications of static link aggregation.
- An interface number from 1–127 can be assigned to the LACP logical interface.
- Use the channel-group command to associate a LAN/SFP port with an LACP logical link interface.
- When associating an LAN/SFP, specify the following operating modes. (It is recommended to specify “active mode”.)
- Active mode
The LACP frame will be voluntarily transmitted, and negotiation with the opposing device’s port will begin.
- Passive mode
The LACP frame will not be voluntarily transmitted, but will instead be transmitted when a frame is received from the opposing device.
- Active mode
- When associating a LAN/SFP port with an interface number for which there is no LACP logical interface, a new logical interface will be generated.
- When the associated port no longer exists as a result of removing a LAN/SFP port from an LACP logical interface, the relevant logical interface will be deleted.
- When associating an LAN/SFP, specify the following operating modes. (It is recommended to specify “active mode”.)
- The parameters that influence the operations of the LACP logical interface are shown below.
- LACP timeout
LACP timeout indicates the down time that was determined, when an LACP frame has not been received from the opposing device.
Specify either “Long” (90 sec.) or “Short” (3 sec.) using the lacp timeout command.
The LACP timeout value is stored in the LACP frame and transmitted to the opposing device.
The opposing device that received the frame will transmit the LACP frames it has stored at intervals equaling 1/3 of the LACP timeout value.
The default value when the logical interface is generated is “Long (90 sec.)”.
- LACP system priority
The LACP system priority is used when deciding which device will control the logical interface, when communicating with the opposing device.
The device with the highest combined system priority exchanged with the opposing device and MAC address (together called the “system ID”) is selected.
The LAN/SFP port associated with the logical interface that is to be enabled (active) is determined for the selected device.
The LACP system priority can be specified from a range of 1–65,535 by the lacp system-priority command. (Lower numbers have higher priority.)
The default value when the logical interface is generated is set to 32,768 (0x8000).
- LACP port priority
LACP port priority is used to control active/standby for the LAN/SFP ports that are associated with the logical interface.
When there are more LAN/SFP ports associated to the logical interface than the 8-port maximum, the port status is controlled based on a combination of the LACP port priority and the port number (which is called “port ID”).
As the maximum number of LAN/SFP ports associated to a logical interface is currently eight, this function is disabled.
The LACP system priority for opposing devices is transmitted at a fixed value (32,768 (0x8000)).
- LACP timeout
- Use the show etherchannel command to show the LACP logical interface status.
4 Related Commands
The related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Set the static logical interface | static-channel-group |
| Show the static logical interface status | show static-channel-group |
| Set the LACP logical interface | channel-group |
| Set LACP system priority | lacp system-priority |
| Show LACP system priority | show lacp sys-id |
| Set LACP timeout | lacp timeout |
| Clear LACP packet counter | clear lacp |
| Show LACP packet counter | show lacp counters |
| Show the status of the LACP logical interface | show etherchannel |
| Set load balance function rules | port-channel load-balance |
5 Examples of Command Execution
5.1 Setting the static logical interface
In this example, we will set link aggregation to use four LAN ports, in order to communicate between L2 switches.
- Static logical interface setting example
- Static link aggregation is set to static.
The logical interface numbers are set to switch A: #2 and switch B: #5.
- The LAN ports associated with the logical interface are all access ports, and are associated with the VLAN #1000.
- Define [switch A] VLAN #1000, and associate it with LAN ports (#15, #17, #19, #21, #23).
Together with this, associate LAN ports (#17, #19, #21, #23) with the logical interface #2.
Yamaha(config)#vlan database ... (VLAN-ID #1000 definition) Yamaha(config-vlan)#vlan 1000 Yamaha(config-vlan)#exit Yamaha(config)#interface port1.15 ... (Set LAN port #15) Yamaha(config-if)#switchport access vlan 1000 ... (Set as access port, and associate with VLAN #1000) Yamaha(config-if)#interface port1.17 ... (Set LAN port #17) Yamaha(config-if)#switchport access vlan 1000 ... (Set as access port, and associate with VLAN #1000) Yamaha(config-if)#static-channel-group 2 ... (Associate with logical interface #2) Yamaha(config-if)#interface port1.19 Yamaha(config-if)#switchport access vlan 1000 Yamaha(config-if)#static-channel-group 2 Yamaha(config-if)#interface port1.21 Yamaha(config-if)#switchport access vlan 1000 Yamaha(config-if)#static-channel-group 2 Yamaha(config-if)#interface port1.23 Yamaha(config-if)#switchport access vlan 1000 Yamaha(config-if)#static-channel-group 2
- Confirm the setting status of [switch A] logical interface #2.
Yamaha#show static-channel-group % Static Aggregator: sa2 % Member: port1.17 port1.19 port1.21 port1.23
- Define [switch B] VLAN #1000, and associate it with LAN ports (#07, #09, #11, #13, #15).
Together with this, associate LAN ports (#09, #11, #13, #15) with the logical interface #5.
Yamaha(config)#vlan database Yamaha(config-vlan)#vlan 1000 Yamaha(config-vlan)#exit Yamaha(config)#interface port1.7 Yamaha(config-if)#switchport access vlan 1000 Yamaha(config-if)#interface port1.9 Yamaha(config-if)#switchport access vlan 1000 Yamaha(config-if)#static-channel-group 5 Yamaha(config-if)#interface port1.11 Yamaha(config-if)#switchport access vlan 1000 Yamaha(config-if)#static-channel-group 5 Yamaha(config-if)#interface port1.13 Yamaha(config-if)#switchport access vlan 1000 Yamaha(config-if)#static-channel-group 5 Yamaha(config-if)#interface port1.15 Yamaha(config-if)#switchport access vlan 1000 Yamaha(config-if)#static-channel-group 5
- Confirm the setting status of [switch B] logical interface #5.
Yamaha#show static-channel-group % Static Aggregator: sa5 % Member: port1.9 port1.11 port1.13 port1.15
- Enable [switch A] logical interface.
Yamaha(config)#interface sa2 ... (Set logical interface #2) Yamaha(config-if)#no shutdown ... (Enable logical interface)
- Enable [switch B] logical interface.
Yamaha(config)#interface sa5 ... (Set logical interface #5) Yamaha(config-if)#no shutdown ... (Enable logical interface)
- Confirm the setting status of [switch A] logical interface.
Yamaha#show interface sa2 Interface sa2 Link is UP ... (is enabled) Hardware is AGGREGATE ifIndex 4502, MRU 1522 Vlan info : Switchport mode : access Ingress filter : enable Acceptable frame types : all Default Vlan : 1000 Configured Vlans : 1000 Interface counter: input packets : 1020 bytes : 102432 multicast packets: 1020 output packets : 15 bytes : 1845 multicast packets: 15 broadcast packets: 0 - Confirm the setting status of [switch B] logical interface.
Yamaha#show interface sa5 Interface sa5 Link is UP Hardware is AGGREGATE ifIndex 4505, MRU 1522 Vlan info : Switchport mode : access Ingress filter : enable Acceptable frame types : all Default Vlan : 1000 Configured Vlans : 1000 Interface counter: input packets : 24 bytes : 2952 multicast packets: 24 output packets : 2109 bytes : 211698 multicast packets: 2109 broadcast packets: 0
5.2 Setting the LACP logical interface
In this example, we will set link aggregation to use four LAN ports, in order to communicate between L2 switches.
- Set the LACP logical interface
- Use LACP for link aggregation.
The logical interface numbers are set to switch A: #10 and switch B: #20.
Set the switch A logical interface to active status, and the switch B logical interface to passive status.
- The LAN ports associated with the logical interface are all access ports, and are associated with the VLAN #1000.
- For load balance, set the destination/source IP address.
- Define [switch A] VLAN #1000, and associate it with LAN ports (#15, #17, #19, #21, #23).
Together with this, associate LAN ports (#17, #19, #21, #23) in active status with the logical interface #10.
The logical interface at this point in time will be in shutdown mode.
Yamaha(config)#vlan database Yamaha(config-vlan)#vlan 1000 ... (VLAN #1000 definition) Yamaha(config-vlan)#exit Yamaha(config)#interface port1.15 Yamaha(config-if)#switchport access vlan 1000 ... (Set as access port, and associate with VLAN #1000) Yamaha(config-if)#interface port1.17 Yamaha(config-if)#switchport access vlan 1000 ... (Set as access port, and associate with VLAN #1000) Yamaha(config-if)#channel-group 10 mode active ... (Associate with logical interface #10 in an active status) Yamaha(config-if)#interface port1.19 Yamaha(config-if)#switchport access vlan 1000 Yamaha(config-if)# channel-group 10 mode active Yamaha(config-if)#interface port1.21 Yamaha(config-if)#switchport access vlan 1000 Yamaha(config-if)# channel-group 10 mode active Yamaha(config-if)#interface port1.23 Yamaha(config-if)#switchport access vlan 1000 Yamaha(config-if)# channel-group 10 mode active
- Confirm the setting status of [switch A] logical interface #10.
Yamaha#show etherchannel % Lacp Aggregator: po10 % Member: port1.17 port1.19 port1.21 port1.23 Yamaha#show lacp sys-id ... (Check LACP system ID: set to the default value (0x8000)) % System 8000,00-a0-de-ae-b9-1f Yamaha#show interface po10 Interface po10 Link is DOWN ... (Link is down) Hardware is AGGREGATE ifIndex 4610, MRU 1522 Vlan info : Switchport mode : access Ingress filter : enable Acceptable frame types : all Default Vlan : 1000 Configured Vlans : 1000 Interface counter: input packets : 0 bytes : 0 multicast packets: 0 output packets : 0 bytes : 0 multicast packets: 0 broadcast packets: 0 - Define [switch A] VLAN #1000, and associate it with LAN ports (#07, #09, #11, #13, #15).
Together with this, associate LAN ports (#09, #11, #13, #15) in passive status with the logical interface #20.
The logical interface at this point in time will be in shutdown mode.
Yamaha(config)#vlan database Yamaha(config-vlan)#vlan 1000 ... (VLAN #1000 definition) Yamaha(config-vlan)#exit Yamaha(config)#interface port1.7 Yamaha(config-if)#switchport access vlan 1000 ... (Set as access port, and associate with VLAN #1000) Yamaha(config-if)#interface port1.9 Yamaha(config-if)#switchport access vlan 1000 ... (Set as access port, and associate with VLAN #1000) Yamaha(config-if)#channel-group 20 mode passive ... (Associate with logical interface #20 in a passive status) Yamaha(config-if)#interface port1.11 Yamaha(config-if)#switchport access vlan 1000 Yamaha(config-if)# channel-group 20 mode passive Yamaha(config-if)#interface port1.13 Yamaha(config-if)#switchport access vlan 1000 Yamaha(config-if)# channel-group 20 mode passive Yamaha(config-if)#interface port1.15 Yamaha(config-if)#switchport access vlan 1000 Yamaha(config-if)# channel-group 20 mode passive
- Confirm the setting status of [switch B] logical interface #20.
Yamaha#show etherchannel % Lacp Aggregator: po20 % Member: port1.9 port1.11 port1.13 port1.15 Yamaha#show lacp sys-id ... (Check LACP system ID: set to the default value (0x8000)) % System 8000,00-a0-de-ae-b8-7e Yamaha#show interface po20 Interface po20 Link is DOWN ... (Link is down) Hardware is AGGREGATE ifIndex 4620, MRU 1522 Vlan info : Switchport mode : access Ingress filter : enable Acceptable frame types : all Default Vlan : 1000 Configured Vlans : 1000 Interface counter: input packets : 0 bytes : 0 multicast packets: 0 output packets : 0 bytes : 0 multicast packets: 0 broadcast packets: 0 - Set the load balance of [switch A] to the destination/source IP address, and enable.
Yamaha(config)#port-channel load-labance src-dst-ip ... (Set load balancing) Yamaha(config)#interface po10 ... (Set logical interface #10) Yamaha(config-if)#no shutdown ... (Enable logical interface)
- Set the load balance of [switch B] to the destination/source IP address, and enable.
Yamaha(config)#port-channel load-labance src-dst-ip ... (Set load balancing) Yamaha(config)#interface po20 ... (Set logical interface #20) Yamaha(config-if)#no shutdown ... (Enable logical interface)
- Confirm the setting status of [switch A] logical interface.
Link up and confirm whether frames are being sent and received.
Yamaha#show interface po10 Interface po10 Link is UP Hardware is AGGREGATE ifIndex 4610, MRU 1522 Vlan info : Switchport mode : access Ingress filter : enable Acceptable frame types : all Default Vlan : 1000 Configured Vlans : 1000 Interface counter: input packets : 560 bytes : 58239 multicast packets: 560 output packets : 98 bytes : 12474 multicast packets: 98 broadcast packets: 0 Yamaha# Yamaha#show lacp-counter % Traffic statistics Port LACPDUs Marker Pckt err Sent Recv Sent Recv Sent Recv % Aggregator po10 , ID 4610 port1.17 50 47 0 0 0 0 port1.19 49 46 0 0 0 0 port1.21 49 46 0 0 0 0 port1.23 49 46 0 0 0 0 - Confirm the setting status of [switch B] logical interface.
Link up and confirm whether frames are being sent and received.
Yamaha#show interface po20 Interface po20 Link is UP Hardware is AGGREGATE ifIndex 4620, MRU 1522 Vlan info : Switchport mode : access Ingress filter : enable Acceptable frame types : all Default Vlan : 1000 Configured Vlans : 1000 Interface counter: input packets : 78 bytes : 9914 multicast packets: 78 output packets : 438 bytes : 45604 multicast packets: 438 broadcast packets: 0 Yamaha# Yamaha#show lacp-counter % Traffic statistics Port LACPDUs Marker Pckt err Sent Recv Sent Recv Sent Recv % Aggregator po20 , ID 4620 port1.9 55 57 0 0 0 0 port1.11 54 56 0 0 0 0 port1.13 54 56 0 0 0 0 port1.15 54 56 0 0 0 0
6 Points of Caution
- A host port that is associated with a private VLAN cannot be aggregated as a link aggregation logical interface.
- If access list settings exist for the received frame of a LAN/SFP port, the ports cannot be aggregated as a link aggregation logical interface.
7 Related Documentation
- LAN/SFP port control: Interface basic functions
- SWR2310 Series Technical Data (Basic Functions)
- Interface control functions
- Port authentication functions
Port authentication functions
1 Function Overview
Port authentication is a function that authenticates devices or users.
This authenticates a device connected to the LAN/SFP port, and permits LAN access only for devices that succeeded in authenticating.
Devices that are not yet authenticated or that failed to authenticate can be denied access to the LAN, or permitted to access only a specific VLAN.

2 Definition of Terms Used
- IEEE 802.1X
- The authentication standard used when connecting to the LAN.
- Authenticator
A device or software that authenticates a supplicant connected to a LAN/SFP port.
It mediates between the supplicant and the authentication server, controlling access to the LAN according to the success or failure of authentication.
- Supplicant
- A device or software that connects to an authenticator and receives authentication.
- Authentication server
A device or software that authenticates a supplicant that is connected via the authenticator.
This manages authentication information such as user names, passwords, MAC addresses, and associated VLANs.
- EAP (Extended authentication protocol)
This is an authentication protocol that extends PPP, allowing various authentication methods to be used.
This is defined in RFC3748.
- EAP over LAN (EAPOL)
- This is a protocol for conveying EAP packets between the supplicant and the authenticator.
- EAP over Radius
- This is a protocol for conveying EAP packets between the authenticator and the authentication server (RADIUS server).
- EAP-MD5 (Message digest algorithm 5)
Client authentication using user name and password.
This uses an MD5 hash value to authenticate.
- EAP-TLS (Transport Layer Security)
This uses the digital certificates of the server and the client to authenticate.
With the transport layer encrypted, the digital certificates are exchanged and authenticated.
This is defined in RFC2716 and RFC5216.
- EAP-TTLS (Tunneled TLS)
This is an extended version of EAP-TLS.
This uses the digital signature of the server to establish a TLS communication route, and within this encrypted communication route uses a password to authenticate the client.
This is defined in RFC5281.
- EAP-PEAP (Protected EAP)
The principle of operation is equivalent to EAP-TTLS (the only difference is the protocol inside the encrypted tunnel).
This uses the digital signature of the server to establish a TLS communication route, and within this encrypted communication route uses a password to authenticate the client.
3 Function Details
The operating specifications for port authentication are shown below.
As port authentication functions, this product supports IEEE 802.1X authentication, MAC authentication, and Web authentication.
The following table shows the distinctive features of each authentication method.
Port authentication method features
| MAC authentication | IEEE 802.1X authentication | Web authentication | |
|---|---|---|---|
| Authenticated element | MAC address | User name and password (EAP-MD5, EAP-TTLS, EAP-PEAP) | User name and password |
| Authenticated object (supplicant) | Device | Device or user | Device or user |
| Functionality needed by supplicant | None | IEEE 802.1X authentication | Web browser |
| Operation when authenticating | None | User name and password entry (EAP-MD5, EAP-TTLS, EAP-PEAP) | User name and password entry |
This screen assumes a RADIUS server as the authentication server.
Note that the port authentication functionality of this product has the following limitations.
- It cannot be used on a private VLAN port.
- It cannot be used on a voice VLAN port.
- If port authentication is enabled, a spanning tree topology change will occur according to the authentication result.
If you want to avoid this, specify “spanning-tree edgeport” for the authentication port to which the supplicant will be connected.
- The number of supplicants that can be authenticated is one for each port in single host mode or multi-supplicant mode; for multi-supplicant mode, the maximum is 512 for the entire system.
- Web authentication can be used only in multi-supplicant mode.
- Web authentication cannot be used together with a guest VLAN.
- The L2MS functions cannot be used if settings are made with the trunk port without a native VLAN.
- When using the stack function, the file stored in the master switch is referenced for the Web authentication screen customization file.
- When using the stack function, if a member switch is added, the authentication information of the supplicant connected to the logical interface is cleared.
- The L2MS functions cannot be used if settings are made with the trunk port without a native VLAN.
- Guest VLAN cannot be used on trunk ports.
- If the following supplicant VLAN is changed by the authentication VLAN, the authentication function may not work properly.
- DHCP server
- L2MS compatible device
3.1 IEEE 802.1X authentication
IEEE 802.1X authentication uses EAP to authenticate in units of devices or users.
The supplicant receiving authentication must support IEEE 802.1X authentication.
This product operates as an authenticator that communicates with the supplicant via EAP over LAN and communicates with the RADIUS server via EAP over RADIUS.
The authentication process itself occurs directly between the supplicant and the RADIUS server.
As authentication methods, this product supports EAP-MD5, EAP-TLS, EAP-TTLS, and EAP-PEAP.
The features of each authentication method are shown in the following table.
Features of each authentication method
| Client authentication method | Server authentication method | Ease of implementation | Degree of safety | |
|---|---|---|---|---|
| EAP-MD5 | User name and password entry | No authentication | Easy | Low |
| EAP-TLS | Client certificate | Server certificate | Complex | High |
| EAP-TTLS | User name and password entry | Server certificate | Medium | Medium |
| EAP-PEAP | User name and password entry | Server certificate | Medium | Medium |
Make settings for the supplicant and the RADIUS server as appropriate for the authentication method you use.
The basic procedure for IEEE 802.1X authentication is shown in the following diagram.
Basic procedure for IEEE 802.1X authentication

The supplicant is connected to the LAN, and transmits a communication start message (EAPOL-Start) message to start authentication.
When authentication succeeds, authentication success (Success) notification is sent to the supplicant, and the supplicant’s MAC address is registered in the FDB, allowing the supplicant to access the network.
If authentication fails, an authentication failure (Failure) notification is sent to the supplicant, and network access is denied for the supplicant.
(Even without authentication, it is possible to allow access to a specific VLAN if a guest VLAN has been specified.)
3.2 MAC authentication
MAC authentication uses the MAC address of a device to authenticate an individual device.
Since the supplicant does not need special functionality to be authenticated, authentication is possible even for devices that do not support IEEE 802.1X.
The basic procedure for MAC authentication is shown in the following diagram.

When this product receives any Ethernet frame from the supplicant, it queries the RADIUS server with the supplicant’s MAC address as the user name and password.
EAP-MD5 is used as the authentication mode between this product and the RADIUS server.
When authentication succeeds, the supplicant’s MAC address is registered in the FDB, allowing the supplicant to access the network.
If authentication fails, the supplicant is denied network access.
(Even without authentication, it is possible to allow access to a specific VLAN if a guest VLAN has been specified.)
The supplicant’s MAC address must be registered as the user name and password in the RADIUS server, in one of the following formats.
- XX-XX-XX-XX-XX-XX (hyphen delimited)
- XX:XX:XX:XX:XX:XX (colon delimited)
- XXXXXXXXXXXX (not delimited)
This product lets you use the auth-mac auth-user command to change the format of the MAC address query that is made to the RADIUS server.
Specify the appropriate command according to the format of the MAC addresses that are registered in the RADIUS server.
3.3 Web authentication
Web authentication is a function that authenticates a user when a user name and password are entered from the supplicant’s web browser.
HTTP is supported as the communication method between the web browser and the switch.
Because web authentication performs authentication by communicating via HTTP, it is necessary for IP communication between this product and the supplicant to be possible even before authentication.
Either the DHCP server must assign an IP address to the supplicant, or the supplicant must specify an IP address statically.
Web authentication operates only in multi-supplicant mode.
Also, this cannot be used together with a guest VLAN.
The basic procedure for web authentication is shown in the following diagram.

This product queries the RADIUS server using the user name and password that were entered in the supplicant’s web browser.
EAP-MD5 is used as the authentication mode between this product and the RADIUS server.
When authentication succeeds, the supplicant’s MAC address is registered in the FDB, allowing the supplicant to access the network.
If authentication fails, the supplicant is denied network access.
3.3.1 Operations on the supplicant
When the supplicant’s web browser accesses IPv4 TCP port 80, the following authentication screen appears.

To be authenticated, enter a user name and password, and click the [Login] button.
The supplicant’s MAC address is registered in the FDB, allowing the supplicant to access the network.
If authentication fails three times in succession, authentication is temporarily restricted.
3.3.2 Customizing the authentication screen
The displayed content on the Web authentication screen (the edited HTML, CSS and image files) can be copied to this product, and the following parts can be customized.
Note that we cannot provide support for how to code in HTML/CSS or what formatting to use, or for any troubles that may occur due to modifications to the code.

- Header
The header section includes the “header.html” and “style.css” files. Edit these files and copy them to this product in order to customize them. - Image file
Copy the image provided to this product in order to modify it. - Input form
The display style used for the input form is defined in the “style.css” file. Although the text cannot be changed, you can edit the “style.css” file and copy it to this product in order to change the input form’s design. - Footer
The footer section includes the “footer.html” and “style.css” files. Edit these files and copy them to this product in order to customize them.
The following explains how to modify the Web authentication screen.
3.3.2.1 Preparing the authentication screen customization files
The following files are used to customize the Web authentication screen.
- header.html
- footer.html
- logo.png
- style.css
Use the Web browser to access the “header.html”, “footer.html” and “style.css” files from the switch.
For example if the IP address of the switch is 192.168.100.240, you can use the following URL to access the file from a PC connected to a port on which Web authentication is enabled, and then use the browser’s “Save as” command to save the file on the PC.
- http://192.168.100.240/web-auth/header.html
- http://192.168.100.240/web-auth/footer.html
- http://192.168.100.240/web-auth/style.css
When saving, specify the extension as “.css” and specify the character encoding as “UTF-8.”
For the image file logo.png, prepare a desired image file on the PC, and save it with the file name logo.png.
The maximum file size is 1 MB.
3.3.2.2 Editing the authentication screen customization files
Edit the above-mentioned HTML and CSS files as appropriate on your PC.
You are free to edit each file in accordance with HTML and CSS specifications, but please note the following points.
- The only image file that can be referenced from the “header.html” and “footer.html” files is “logo.png”.
- The extension of the CSS file must be “.html” or “.css” and the character encoding must be consistent with UTF-8.
3.3.2.3 Placing the authentication screen customization files
When you have prepared the files, place them in /model name/startup-config/web-auth/ on the SD card.
After placing the files, use the copy auth-web custom-file command or the copy startup-config command to copy the authentication screen customization files to the switch.
If the following files exist in the folder hierarchy in which the currently-running CONFIG is saved, they are used to generate the Web authentication screen.
You can determine the currently-running CONFIG number by using the show environment command. Even if the switch started up using the CONFIG on the SD card, you can customize the Web authentication screen by placing these files in /model name/startup-config/web-auth/ on the SD card.
- header.html
This is used as the header section referenced from the authentication screen. If this file does not exist, the original “header.html” is used.
- footer.html
This is used as the footer section referenced from the authentication screen. If this file does not exist, the original “footer.html” is used.
- logo.png
This is used as the logo in the upper left of the authentication screen. If this file does not exist, the original Yamaha logo is shown.
- style.css
This is used as the “style.css” referenced from the authentication screen. If this file does not exist, the original style.css is used.
When you have finished placing the edited files, check the display by using your browser to access the Web authentication screen.
If you need to make additional changes, edit the files on your PC, and transfer them again.
3.3.2.4 Canceling customization
If you decide to cancel customization of the authentication screen, delete the customization files from the folder in which the currently-running CONFIG is saved. You will revert to the original authentication screen.
To delete the files, you can use the erase auth-web custom-file command or the erase startup-config command.
However, since the erase startup-config command also deletes files such as config.txt, you should first copy files such as config.txt to an SD card etc. as a backup.
3.4 Using multiple authentication functions
This screen lets you use IEEE802.1X authentication, MAC authentication, and Web authentication together on the same port.
When multiple methods are used together, IEEE 802.1X authentication takes priority.
Web authentication can be attempted at any time as long as another of the multiple authentication methods is not currently communicating with the RADIUS server.
If multiple authentication methods are being used simultaneously, operation is as follows.
- Procedure if the supplicant supports IEEE 802.1X authentication
- Procedure if the supplicant does not support IEEE 802.1X authentication
note
- If authentication succeeds with any one of the methods, authentication has succeeded.
- If the reauthentication setting is enabled, then reauthentication is performed using the method with which authentication succeeded.
- If multiple authentication methods are being used simultaneously, the forwarding control setting of an unauthenticated port will be to discard reception.
- If EAPOL start is received from an unauthenticated supplicant, operation will transition to IEEE 802.1X authentication even if authentication operation is already in progress using MAC authentication or Web authentication.
- If 802.1X authentication and MAC authentication are being used simultaneously, the authentication restriction interval does not start even if 802.1X authentication fails.
- If 802.1X authentication and MAC authentication are being used simultaneously, and any Ethernet frame is received from the supplicant, this product transmits an EAP Request.
- If Web authentication is also being used, unauthenticated supplicants are registered in FDB as static/discard.
3.5 Host mode
This product lets you select the host mode for the port authentication function.
Host mode indicates how an applicable supplicant’s communication will be permitted on the authentication port.
This product lets you choose from the following host modes.
- Single host mode
This mode permits communication for only one supplicant for each LAN/SFP port.
Communication is permitted only for the first supplicant that successfully authenticates.
- Multi-host mode
This mode permits communication for multiple supplicants for each LAN/SFP port.
When a supplicant successfully authenticates and communication is permitted, another supplicant that is connected to the same LAN/SFP port and that successfully authenticates is also permitted to communicate on the same VLAN.
- Multi-supplicant
This mode permits communication for multiple supplicants for each LAN/SFP port.
Each supplicant is distinguished by its MAC address, permitting communication in units of supplicants.
When using dynamic VLAN functions, you can specify the VLAN for each supplicant.
3.5 Authentication VLAN
This product supports authentication VLAN with IEEE802.1X, MAC and Web authentication.
An authentication VLAN is a function that changes the authentication port’s associated VLAN according to the VLAN attributes of authentication data received from the RADIUS server.
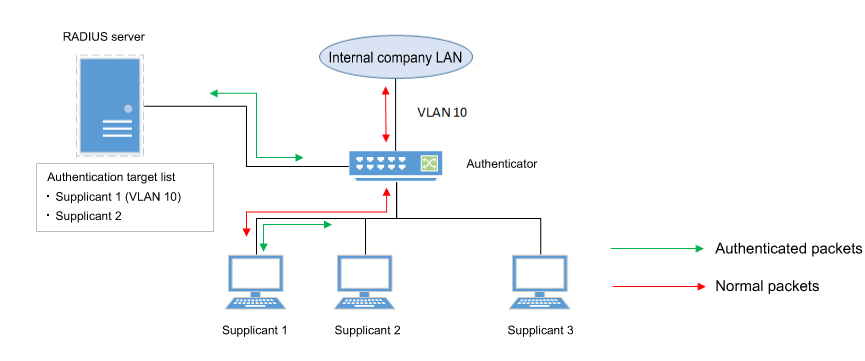
As shown in the illustration above, if a port’s associated VLAN is 1, and the received authentication data has a VLAN attribute of 10, then following successful authentication, the authentication port’s associated VLAN is 10, and communication on VLAN 10 is permitted.
For the RADIUS server, make settings so that the authentication information sent from the server includes the following attribute values.
- Tunnel-Type = VLAN (13)
- Tunnel-Medium-Type = IEEE-802 (6)
- Tunnel-Private-Group-ID = VLAN ID
If an authentication VLAN is used, operation in the various host modes will be as follows.
- Single host mode
The authentication port’s associated VLAN is changed according to the VLAN attribute value of the supplicant that successfully authenticates.
- Multi-host mode
The authentication port’s associated VLAN is changed according to the VLAN attribute value of the supplicant that successfully authenticates.
Other supplicants that are connected to the same port are also permitted to communicate on the same VLAN.
- Multi-supplicant mode
The authentication port’s associated VLAN is changed according to the VLAN attribute value of the supplicant that successfully authenticates.
You can specify the VLAN for each supplicant.
3.6 VLAN for unauthenticated or failed-authentication ports
This product’s IEEE 802.1X authentication and MAC authentication allows you to specify a guest VLAN so that unauthenticated ports or ports that failed authentication will be assigned to a specific VLAN.
In multi-supplicant mode, you can specify this for each supplicant.
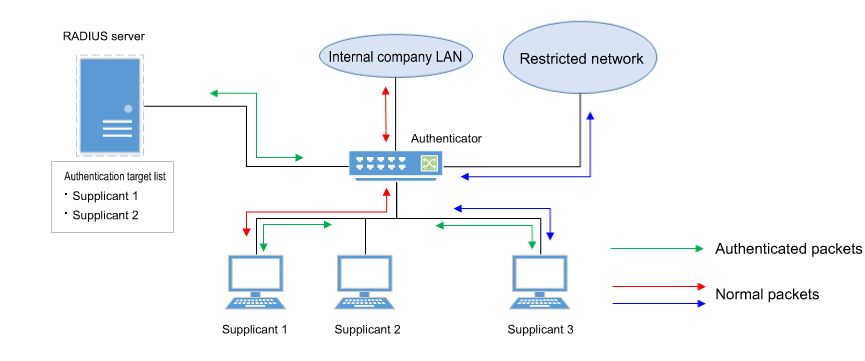
This is useful when you want to provide partial functionality on a limited network even to a supplicant that has not succeeded in authenticating, as shown in the illustration above.
3.7 EAP pass-through function
You can switch between enable and disable for EAP pass-through and configure whether EAPOL frames are to be forwarded.
The authentication function will be prioritized for interfaces on which the 802.1X authentication function is enabled, and EAP pass-through will not be applied.
3.8 Attribute values sent to the RADIUS server
The NAS-Identifier attribute value can be notified to the RADIUS server.
The character string set with the auth radius attribute nas-identifier command is sent to the RADIUS server as the NAS-Identifier attribute value.
4 Related Commands
The related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Set IEEE 802.1X authentication function for the entire system | aaa authentication dot1x |
| Set MAC authentication function for the entire system | aaa authentication auth-mac |
| Set Web authentication function for the entire system | aaa authentication auth-web |
| Set IEEE 802.1X authentication function operating mode | dot1x port-control |
| Set unauthenticated port forwarding control for IEEE 802.1X authentication | dot1x control-direction |
| Set number of retransmitted EAPOL packets | dot1x max-auth-req |
| Set MAC authentication function | auth-mac enable |
| Set MAC address format setting for MAC authentication | auth-mac auth-user |
| Set Web authentication function | auth-web enable |
| Set redirect-destination URL following successful Web authentication | auth-web redirect-url |
| Copy Web authentication screen customization files | copy auth-web custom-file |
| Delete Web authentication screen customization files | erase auth-web custom-file |
| Set host mode | auth host-mode |
| Set reauthentication | auth reauthentication |
| Set dynamic VLAN | auth dynamic-vlan-creation |
| Set guest VLAN | auth guest-vlan |
| Set restriction period following failed authentication | auth timeout quiet-period |
| Set reauthentication interval | auth timeout reauth-period |
| Set response wait time for the entire RADIUS server | auth timeout server-timeout |
| Set response wait time for the supplicant | auth timeout supp-timeout |
| Set RADIUS server host | radius-server host |
| Set response wait time for a single RADIUS server | radius-server timeout |
| Set number of times to retransmit request to RADIUS server | radius-server retransmit |
| Set shared password for RADIUS server | radius-server key |
| Set availability time restriction for RADIUS server | radius-server deadtime |
| Setting the NAS-Identifier attribute to notify the RADIUS server | auth radius attribute nas-identifier |
| Show port authentication status | show auth status |
| Show RADIUS server setting status | show radius-server |
| Show supplicant status | show auth supplicant |
| Show statistical information | show auth statistics |
| Clear statistical information | clear auth statistics |
| Clear authentication state | clear auth state |
| Set time at which authentication state is cleared (system) | auth clear-state time |
| Set time at which authentication state is cleared (interface) | auth clear-state time |
| EAP pass-through settings | pass-through eap |
5 Examples of Command Execution
5.1 Set IEEE 802.1X authentication
Make settings so that IEEE 802.1X authentication can be used.

- We will use LAN port #1 as the authentication port to which the supplicant is connected.
- We will set the host mode to multi-supplicant mode.
- We will use VLAN #10 as the guest LAN.
- We will use 192.168.100.101 as the IP address of the RADIUS server that is connected.
- Define VLAN #10 as the guest VLAN.
Yamaha(config)#vlan database Yamaha(config-vlan)#vlan 10 ... (VLAN #10 definition) Yamaha(config-vlan)#exit
- Enable the IEEE 802.1X authentication function for the entire system.
Yamaha(config)#aaa authentication dot1x
- Set IEEE 802.1X authentication for LAN port #1.
Yamaha(config)#interface port1.1 Yamaha(config-if)#dot1x port-control auto ... (Set IEEE 802.1X authentication operating mode to auto) Yamaha(config-if)#auth host-mode multi-supplicant ... (Set host mode to multi-supplicant mode) Yamaha(config-if)#auth guest-vlan 10 ... (Set guest VLAN as VLAN #10) Yamaha(config-if)#exit
- Set RADIUS server settings.
Yamaha(config)#radius-server host 192.168.100.101 key test1 (Set host as 192.168.100.101 and shared password as “test1”) - Check RADIUS server settings.
Yamaha#show radius-server Server Host : 192.168.100.101 Authentication Port : 1812 Secret Key : test1 Timeout : 5 sec Retransmit Count : 3 Deadtime : 0 min
- Check port authentication settings.
Yamaha#show auth status [System information] 802.1X Port-Based Authentication : Enabled MAC-Based Authentication : Disabled WEB-Based Authentication : Disabled Clear-state time : Not configured Redirect URL : Not configured RADIUS server address : 192.168.100.101 (port:1812) [Interface information] Interface port1.1 (up) 802.1X Authentication : Force Authorized (configured:auto) MAC Authentication : Disabled (configured:disable) WEB Authentication : Enabled (configured:disable) Host mode : Multi-supplicant Dynamic VLAN creation : Disabled Guest VLAN : Enabled (VLAN ID:10) Reauthentication : Disabled Reauthentication period : 3600 sec MAX request : 2 times Supplicant timeout : 30 sec Server timeout : 30 sec Quiet period : 60 sec Controlled directions : In (configured:both) Protocol version : 2 Clear-state time : Not configured
5.2 Set MAC authentication
Make settings so that MAC authentication can be used.

- We will use LAN port #1 as the authentication port to which the supplicant is connected.
- We will set the host mode to multi-supplicant mode.
- We will use 192.168.100.101 as the IP address of the RADIUS server that is connected.
- Enable the MAC authentication function for the entire system.
Yamaha(config)#aaa authentication auth-mac
- Set MAC authentication for LAN port #1.
Yamaha(config)#interface port1.1 Yamaha(config-if)#auth-mac enable ... (Enable MAC authentication) Yamaha(config-if)#auth host-mode multi-supplicant ... (Set host mode to multi-supplicant mode) Yamaha(config-if)#exit
- Set RADIUS server settings.
Yamaha(config)#radius-server host 192.168.100.101 key test1 (Set host as 192.168.100.101 and shared password as “test1”) - Check RADIUS server settings.
Yamaha#show radius-server Server Host : 192.168.100.101 Authentication Port : 1812 Secret Key : test1 Timeout : 5 sec Retransmit Count : 3 Deadtime : 0 min
- Check port authentication settings.
Yamaha#show auth status [System information] 802.1X Port-Based Authentication : Disabled MAC-Based Authentication : Enabled WEB-Based Authentication : Disabled Clear-state time : Not configured Redirect URL : Not configured RADIUS server address : 192.168.100.101 (port:1812) [Interface information] Interface port1.1 (up) 802.1X Authentication : Force Authorized (configured:-) MAC Authentication : Enabled (configured:enable) WEB Authentication : Disabled (configured:disable) Host mode : Multi-supplicant Dynamic VLAN creation : Disabled Guest VLAN : Disabled Reauthentication : Disabled Reauthentication period : 3600 sec MAX request : 2 times Supplicant timeout : 30 sec Server timeout : 30 sec Quiet period : 60 sec Controlled directions : In (configured:both) Protocol version : 2 Clear-state time : Not configured Authentication status : Unauthorized
5.3 Set Web authentication
Make settings so that Web authentication can be used.

- We will use LAN port #1 as the authentication port to which the supplicant is connected.
- We will assume that 192.168.100.10 the IP address of the supplicant.
- We will use 192.168.100.101 as the IP address of the RADIUS server that is connected.
- Assign an IP address to the authenticator for IP communication.
Yamaha(config)#interface valn1 Yamaha(config-if)#ip address 192.168.100.240/24 Yamaha(config-if)#exit
- Enable the Web authentication function for the entire system.
Yamaha(config)#aaa authentication auth-web
- Set Web authentication for LAN port #1.
Yamaha(config)#interface port1.1 Yamaha(config-if)#auth host-mode multi-supplicant ... (Set host mode to multi-supplicant mode) Yamaha(config-if)#auth-web enable ... (Enable web authentication) Yamaha(config-if)#exit
- Set RADIUS server settings.
Yamaha(config)#radius-server host 192.168.100.101 key test1 (Set host as 192.168.100.101 and shared password as “test1”) - Check RADIUS server settings.
Yamaha#show radius-server Server Host : 192.168.100.101 Authentication Port : 1812 Secret Key : test1 Timeout : 5 sec Retransmit Count : 3 Deadtime : 0 min
- Check port authentication settings.
Yamaha#show auth status [System information] 802.1X Port-Based Authentication : Disabled MAC-Based Authentication : Disabled WEB-Based Authentication : Enabled Clear-state time : Not configured Redirect URL : Not configured RADIUS server address : 192.168.100.101 (port:1812) [Interface information] Interface port1.1 (up) 802.1X Authentication : Force Authorized (configured:-) MAC Authentication : Disabled (configured:disable) WEB Authentication : Enabled (configured:enable) Host mode : Multi-supplicant Dynamic VLAN creation : Disabled Guest VLAN : Disabled Reauthentication : Disabled Reauthentication period : 3600 sec MAX request : 2 times Supplicant timeout : 30 sec Server timeout : 30 sec Quiet period : 60 sec Controlled directions : In (configured:both) Protocol version : 2 Clear-state time : Not configured
6 Points of Caution
Using dynamic VLAN in multi-supplicant mode will consume internal resources.
These resources are also used by the ACL and QoS functions. There may not be enough resources according to the settings.
Use caution, since communications may not be possible if there are not enough resources, even though authentication might succeed.
7 Related Documentation
None
- SWR2310 Series Technical Data (Basic Functions)
- Interface control functions
- Port security functions
Port security functions
1 Function Overview
Port security is a function that limits communication to only permitted terminals, preventing access from illegal terminals.

2 Definition of Terms Used
None
3 Function Details
For ports on which the port security function is enabled, you can pre-register the MAC address of a terminal for which you want to permit communication, thereby allowing communication only for permitted terminals.
Conversely, if there is access from a terminal that is not registered (an illegal terminal), this is considered illegal access, and the packets are discarded.
Depending on the settings, the corresponding port can also be shut down.
The port security function cannot be used simultaneously with the port authentication function.
3.1 Limiting the terminals that can access
By enabling the port security function, and using the port-security mac-address command to register the MAC addresses of only the terminals for which you want to allow communication, you can limit the terminals that are allowed access.
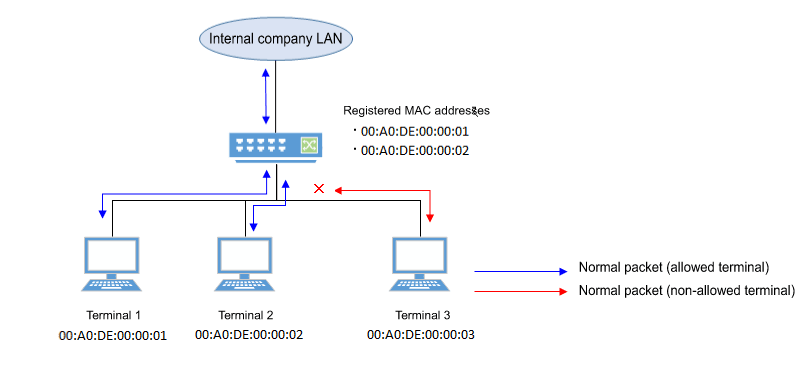
4 Related Commands
The related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Set port security function | port-security enable |
| Register allowed MAC addresses | port-security mac-address |
| Set operation for when security violation occurs | port-security violation |
| Show port security status | show port-security status |
5 Examples of Command Execution
5.1 Limiting the terminals that can access
Manually specify the MAC address so that only the permitted terminal can communicate.
- Enable port security on LAN port #1.
Yamaha(config)#interface port1.1 Yamaha(config-if)#port-security enable
- Register the MAC address that you want to permit.
Yamaha(config)#port-security mac-address 00A0.DE00.0001 forward port1.1 vlan 1 Yamaha(config)#port-security mac-address 00A0.DE00.0002 forward port1.1 vlan 1
- Check the port security status.
Yamaha#show port-security status Port Security Action Status Last violation --------- --------- ---------- --------- --------------------- port1.1 Enabled Discard Normal 00A0.DE00.0003 port1.2 Disabled Discard Normal port1.3 Disabled Discard Normal port1.4 Disabled Discard Normal port1.5 Disabled Discard Normal port1.6 Disabled Discard Normal port1.7 Disabled Discard Normal port1.8 Disabled Discard Normal port1.9 Disabled Discard Normal port1.10 Disabled Discard Normal
6 Points of Caution
- Use the no shutdown command to recover the port that has shut down due to illegal access.
The status of the show port-security status command will not return to normal until the port links up. (The status will remain in shutdown state.)
- If the wrong port is specified with the port-security mac-address command, traffic and violation frames will not be correctly detected.
7 Related Documentation
None
- SWR2310 Series Technical Data (Basic Functions)
- Layer 2 functions
- SWR2310 Series Technical Data (Basic Functions)
- Layer 2 functions
- Forwarding database
Forwarding database
1 Function Overview
The Forwarding Database (subsequently referred to as the FDB) manages the combination of destination MAC addresses, transmission ports, and VLANs.
This product uses the FDB to determine the forwarding destination port for the received frames.
- Enable/disable acquisition function
- Timeout adjustment for FDB entries acquired
- Timeout clear for FDB entries acquired
- Manual registration of FDB entries (static entries)
2 Definition of Terms Used
- FDB
Abbreviation of “Forwarding Database.”
This database manages the combination of destination MAC address, transmission port, and VLAN.
- FDB entry
- This is data registered in the FDB, and consists of multiple elements.
3 Function Details
3.1 FDB entry
On this product, the contents listed in the table below are registered as a single entry in the FDB.
| Element managed | Description |
|---|---|
| MAC address | A device’s MAC address can be unicast or multicast. |
| VLAN-ID (FID) | The VLAN ID to which a device is associated. This is a value from 1–4094. |
| Forwarding destination interface ID | The interface on which the device exists*. (*: LAN/SFP port or Static/LACP logical interface) |
| Action | The method of processing the frame addressed to the device. There are two processing methods, “discard” and “forward”. |
| Registration classification | The registration type for the entry. There are three types, as shown below. * dynamic ... Entries registered through automatic acquisition * static ... Entries registered manually via commands * multicast ... Entries acquired by IGMP/MLD Snooping |
3.1.1 MAC address
This is one of the FDB key items; the VLAN-ID and MAC address are combined to become the record key.
Operation differs depending on whether the MAC address is unicast or multicast.
- Unicast
Since the forwarding destination interface ID must be uniquely determined for a given record key, duplication is not allowed.
(Multiple combinations of the same VLAN-ID and MAC address do not exist.)
- Multicast
Multiple forwarding destination interface IDs may exist for a given key record.
In this case, frames are sent to multiple forwarding destination interface IDs.
Up to 16,384 addresses (described later*) can be registered on this product, including entries registered via automatic acquisition and manual registration.
The MAC addresses of all received frames can be acquired, and the source MAC address is acquired and registered in the FDB.
(However, if the transmission source MAC address is multicast, this is considered an invalid frame and is discarded without being registered.)
Automatically acquired MAC address information is maintained until the ageing timeout.
If multiple multicast MAC addresses are specified, all are considered as one in this case.
VLAN port mac fwd type timeout 1 port1.1 0100.0000.1000 forward static 0 1 port1.2 0100.0000.1000 forward static 0 1 port1.3 0100.0000.1000 forward static 0 1 port1.4 0100.0000.1000 forward static 0 1 port1.5 0100.0000.1000 forward static 0 1 port1.6 0100.0000.1000 forward static 0
3.1.2 VLAN-ID
MAC address acquisition is done per VLAN, and the MAC address and VLAN are managed in the FBD as a pair.
For different VLANs, identical MAC addresses are also acquired.
3.1.3 Forwarding destination interface ID
The following IDs are registered.
- LAN/SFP port (port)
- Static/LACP logical interface (sa,po)
3.1.4 Action
This defines the action for a received frame that matches a key record.
If the MAC address is unicast, the actions are as follows.
- forward ... Forward to the forwarding destination interface ID.
- discard ... Discard without forwarding.
If the MAC address is multicast, the actions are as follows.
- forward ... Forward to the forwarding destination interface ID.
- discard ... Cannot be specified.
(The discard setting cannot be made if the MAC address is multicast.)
3.1.5 Registration types
- dynamic ... Registered and deleted automatically. The registration result does not remain in the config settings file.
- static ... Registered and deleted manually, and therefore remains in the config settings file.
- multicast ... Automatically registered and deleted by the IGMP/MLD snooping function. The registration result does not remain in the config settings file.
3.2 Automatic MAC address acquisition
Automatic MAC address acquisition refers to the active creation of FBD entries based on the information for the source MAC address of the received frame, and the reception port.
Entries registered through automatic acquisition are called “dynamic entries”.
A timer (ageing time) is used to monitor individual entries.
Entries for MAC addresses that have not received frames within a certain amount of time will be deleted from the FDB (see below*).
This prevents invalid device entries from being left over in the FDB due to power shutoff, being moved and so on.
If a frame is received within the specified amount of time, the monitoring timer will be reset.
The control specifications for automatic acquisition are shown below.
- Automatic MAC address acquisition can be enabled or disabled using the mac-address-table learning command. The setting is enabled by default.
- If automatic acquisition is changed from enabled to disabled, all dynamic entries that have been learned will be deleted. The acquisition function “disable” setting is useful when you want to flood all ports with all received frames.
- The ageing time for dynamic entries can be adjusted by specifying a value from 10–400 seconds, using the mac-address-table ageing-time command. This value is set to 300 seconds by default.
- Clear the dynamic entries that have been acquired by using the clear mac-address-table dynamic command. The entire contents of the FDB can be cleared at once; or a VLAN number can be specified and all MAC addresses acquired by that VLAN can be cleared from the FDB. Specifying the port number will clear all MAC addresses from the FDB that were acquired from that port.
- Use the show mac-address-table command to check the automatic acquisition status.
* The time after which an FDB entry is actually deleted from the FDB by the timer (ageing time) is as follows.
- With the ageing time as “T,” it is the time from “T” seconds that does not exceed 2*T seconds.
3.3 Setting MAC addresses manually
In addition to automatic acquisition using received frames, MAC addresses can be set on this product by using user commands.
Entries that have been registered by using commands are called “static entries”.
The specifications for manual settings are shown below.
- Use the mac-address-table static command to register static entries.
- When registering static entries, dynamic acquisition will not be performed on the corresponding MAC addresses.
Entries that have already been acquired will be deleted from the FDB, and will be registered as static entries.
- Use the no mac-address-table static command to delete static entries.
- Either “forward” or “discard” can be specified for the destination MAC address of a received frame.
- When forwarding is specified, either the LAN/SFP port forwarding destination or the static/LACP logical interface can be specified.
- When discarding is specified, frames received by the MAC address will not be forwarded to any port, and will be discarded.
- If registering a multicast MAC address, you cannot specify “discard.”
Also, MAC addresses in the following ranges cannot be registered.
- 0000.0000.0000
- 0100.5e00.0000–0100.5eff.ffff
- 0180.c200.0000–0180.c200.000f
- 0180.c200.0020–0180.c200.002f
- 3333.0000.0000–3333.ffff.ffff
- ffff.ffff.ffff
4 Related Commands
4.1 List of related commands
| Operations | Operating commands |
|---|---|
| Enable/disable MAC address acquisition function | mac-address-table learning |
| Set dynamic entry ageing time | mac-address-table ageing-time |
| Clear dynamic entry | clear mac-address-table dynamic |
| Register static entry | mac-address-table static |
| Delete static entry | no mac-address-table static |
| Refer to MAC address table | show mac-address-table |
5 Examples of Command Execution
5.1 Referring to the FDB
Yamaha#show mac-address-table VLAN port mac fwd type timeout 1 port1.2 00a0.de11.2233 forward static 0 1 port1.1 1803.731e.8c2b forward dynamic 300 1 port1.1 782b.cbcb.218d forward dynamic 300
5.2 Deleting a dynamic entry
Deleting an FDB entry registered in the FBD (MAC address 00:a0:de:11:22:33)
Yamaha#clear mac-address-table dynamic address 00a0.de11.2233
5.3 Changing the dynamic entry ageing time
This example shows how to change the dynamic entry ageing time to 400 seconds.
Yamaha(config)#mac-address-table ageing-time 400
5.4 Registering a static entry
This example shows how frames addressed to a device associated with VLAN #10 (MAC address 00:a0:de:11:22:33) can be forwarded to LAN port 2 (port1.2).
Yamaha(config)#mac-address-table static 00a0.de11.2233 forward port1.2 vlan 10
This example shows how to discard the frames sent to a device associated with VLAN #10 (MAC address 00:a0:de:11:22:33).
Specifying the interface name (“port1.2” in the example) will have no effect on operations. Since this cannot be omitted, specify the LAN/SFP port.
Yamaha(config)#mac-address-table static 00a0.de11.2233 discard port1.2 vlan 10
5.5 Deleting a static entry
This example shows how to delete the forwarding settings sent to a device associated with VLAN #10 (MAC address 00:a0:de:11:22:33).
Yamaha(config)#no mac-address-table static 00a0.de11.2233 forward port1.2 vlan 10
6 Points of Caution
If the l2-unknown-mcast command is configured to discard unknown multicast frames, using the mac-address-table static command to passively forward a multicast MAC address will have no effect when registered.
7 Related Documentation
None
VLAN
1 Function Overview
VLAN (Virtual LAN) is technology that allows a LAN to be constructed virtually, without regard to the physical structure of connections.
This product lets you use VLANs to divide the LAN into multiple broadcast domains.
The VLANs that are supported by this product are shown below.
Supported VLAN types
| VLAN types | Summary |
|---|---|
| Port-based VLAN | Groups that can communicate are configured for each LAN/SFP port. |
| Tagged VLAN | Groups that can communicate are identified, based on the fixed-length tag information appended to the Ethernet frame. Multiple and different VLANs can be made to communicate by means of one LAN/SFP port. |
| Private VLAN | Groups that can communicate within the same VLAN can be divided up. This includes the following three VLAN types.
|
| Multiple VLAN | Each LAN/SFP port can be divided into multiple groups that can communicate. Refer to this information for multiple VLANs. |
| Voice VLAN | This allows audio and data to be handled separately on an access port. |
2 Definition of Terms Used
- Broadcast domain
This is a range in which broadcast frames can be delivered in a network, such as an Ethernet.
Devices that are connected by relaying a data link layer (MAC layer), such as switching hubs, can belong to the same broadcast domain.
A broadcast domain generally refers to the network in an Ethernet.
3 Function Details
3.1 Defining a VLAN ID
On product, a maximum of 255 VLANs can be defined, with VLAN IDs ranging from 2–4094. (ID #1 is used as the default VLAN ID.)
VLAN IDs are defined using the vlancommand, after the vlan database command is used to enter VLAN mode.
For details, refer to the Command Reference.
3.2 VLAN settings for the LAN/SFP ports
The following settings must be configured after defining the VLANs to use, in order to make use of VLAN on this product.
- LAN/SFP port mode settings
- VLAN associations for LAN/SFP ports
- The LAN/SFP ports on this product are set to one of the following modes.
- Access port
This is a port that handles untagged frames. It can be associated with one VLAN.
- Trunk port
This is a port that handles both tagged and untagged frames.
It can be associated with multiple VLANs, and is mainly used to connect switches to one another.
This product only supports IEEE 802.1Q. (Cisco ISL is not supported.)
- Access port
- Use the switchport mode command to set the LAN/SFP port mode.
When setting the trunk port, use the input filter (“ingress-filter”) to control whether frames not belonging to the specified VLAN ID will be handled.
- Input filter enabled: only frames set to the specified VLAN ID will be handled.
- Input filter disabled: all VLAN IDs will be handled.
- Use the show interface switchport command to check the LAN/SFP port setting mode.
- Use the switchport access vlan command to set which VLANs belong to the access port.
- Use the switchport trunk allowed vlan command to set which VLANs belong to the trunk port.
As the trunk port can be associated with multiple VLANs, use the “all”, “none”, “except”, “add” and “remove” settings as shown below.
- add
Adds the specified VLAN ID.
VLAN IDs that can be added are limited by the IDs that are defined by the VLAN mode.
- remove
Deletes the specified VLAN ID.
- all
Adds all VLAN IDs specified by the VLAN mode.
The VLAN IDs added by the VLAN mode can also be added after this command is executed.
- none
The trunk port will not be associated with any VLAN.
- except
Adds all other VLAN IDs except for the ones specified.
The VLAN IDs added by the VLAN mode can also be added after this command is executed.
- add
- A VLAN that uses untagged frames (native VLAN) can be specified for the trunk port.
- Tagged audio frames can be transferred by specifying a voice VLAN for an access port.
- Use the show vlan command to check which VLANs belong to a LAN/SFP port.
3.3 VLAN access control
This product provides an VLAN access map function, to control access to the VLAN.
The VLAN access map can be associated with a standard/extended IP access control list and a MAC address control list as VLAN ID filtering parameters.
The VLAN access map is operated using the commands shown below.
- Create VLAN access map: vlan access-map command
- Set VLAN access map parameters: match access-list command
- Assign VLAN access map: vlan filter command
- Show VLAN access map: show vlan access-map command
3.4 Default VLAN
The default VLAN is VLAN #1 (vlan1), which exists in this switch by default.
As the default VLAN is a special VLAN, it always exists and cannot be deleted.
The following operations can be used to automatically delete the relevant port from the default VLAN.
- Setting the VLAN for an access port
- Setting any VLAN other than the default as the native VLAN for the trunk port
- Setting the native VLAN for the trunk port to “none”
3.5 Native VLAN
A native VLAN is a VLAN that associates untagged frames received by the LAN/SFP port that was set as a trunk port.
Defining an LAN/SFP port as a trunk port will set the default VLAN (VLAN #1) as the native VLAN.
Use the switchport trunk native vlan command when specifying a certain VLAN as the native VLAN.
The native LAN can be set to none, when setting the relevant LAN/SFP port to not handle untagged frames. (Specify “none” in the switchport trunk native vlan command.)
3.6 Private VLAN
This product can configure a private VLAN for further dividing up groups that can communicate within the same subnet. The operating specifications are shown below.
- A private VLAN contains the following three VLAN types.
- Primary VLAN
This is the parent VLAN of the secondary VLAN.
Only one primary VLAN can be set per private VLAN.
- Isolated VLAN
This is a kind of secondary VLAN, which only sends traffic to a primary VLAN.
Only one primary VLAN can be set per private VLAN.
- Community VLAN
This is a kind of secondary VLAN, which only sends traffic to VLANs in the same community and to a primary VLAN.
Multiple community VLANs can be set for each private VLAN.
- Primary VLAN
- A primary VLAN may contain multiple promiscuous ports.
Access ports, trunk ports, or static/LACP logical interfaces are the ports that can be used as promiscuous ports.
- Only access ports can be used as host ports for a secondary VLAN (isolated VLAN, community VLAN).
- A secondary VLAN (isolated VLAN, community VLAN) can be associated with one primary VLAN.
Use the switchport private-vlan mapping command to create the association.
- An isolated VLAN can be associated with multiple promiscuous ports contained within a private VLAN.
- A community VLAN can be associated with multiple promiscuous ports contained within a private VLAN.
3.7 Voice VLAN
Voice VLAN is a function that can prevent audio from being adversely affected even when IP phone voice traffic is mixed with PC data traffic.

Some IP phones have two ports: a port for connection to the switch and a port for connection to the PC.
By connecting the switch to the IP phone, and the IP phone to the PC, it is possible to use one port of the switch to handle the IP phone audio traffic and the PC’s data traffic.
Using the voice VLAN function in this type of configuration allows the audio data and the PC data to be separated so that noise is less likely to occur on the IP phone, or to handle the audio data with a higher priority.
Voice VLAN settings are made by the switchport voice vlan command.
Set one of the following to be handled as voice traffic.
- Frames with the 802.1p tag
- Priority tag frames (802.1p tags with a VLAN ID of 0 and only the CoS value specified)
- Untagged frames
When tagged frames are handled as voice traffic, untagged frames are handled as data traffic.
By using LLDP, this product can automatically apply settings to a connected IP telephone.
The conditions for making automatic settings are as follows.
- LLDP-MED TLV transmission is enabled on the port for which voice VLAN is enabled.
- The connected IP phone supports settings via LLDP-MED.
If the above conditions are satisfied, and when an IP phone is connected to the corresponding port, voice VLAN information (tagged/untagged, VLAN ID, the CoS value to be used, DSCP value) are notified according to the Network Policy TLV of LLDP-MED when an IP phone is connected to the corresponding port.
The IP phone will transmit voice data according to the information that was provided to it from this unit.
The CoS value specified for the IP phone is set by the switchport voice cos command, and the DSCP value is set by the switchport voice dscp command.
In order to give priority to handling voice traffic, QoS settings (enable QoS, set trust mode) are also required.
The limitations of voice VLAN are as follows.
- It can be used only on a physical interface port that is assigned as an access port.
It cannot be used on a link aggregation logical interface or on a VLAN logical interface.
- The voice VLAN function and the port authentication function cannot be used together.
4 Related Commands
4.1 List of related commands
- The related commands are shown below.
Operations Operating commands Enter VLAN mode vlan database Define VLAN interface, or change a predefined VLAN vlan Define a private VLAN private-vlan Set the secondary VLAN for a private VLAN private-vlan association Create VLAN access map vlan access-map Set VLAN access map parameters match Assign VLAN access map to VLAN vlan filter Set access port (untagged port) switchport mode access Set associated VLAN of an access port (untagged port) switchport access vlan Set trunk port (tagged port) switchport mode trunk Set associated VLAN for trunk port (tagged port) switchport trunk allowed vlan Set native VLAN for trunk port (tagged port) switchport trunk native vlan Set ports for private VLAN (promiscuous port, host port) switchport mode private-vlan Configure VLAN for private VLAN port and host port switchport private-vlan host-association Configure VLAN for private VLAN port and promiscuous port switchport private-vlan mapping Configure voice VLAN switchport voice vlan Set CoS value for voice VLAN switchport voice cos Set DSCP value for voice VLAN switchport voice dscp Show VLAN information show vlan Show private VLAN information show vlan private-vlan Show VLAN access map show vlan access-map Show VLAN access map filter show vlan filter
5 Examples of Command Execution
5.1 Port-based VLAN settings
In this example, a port-based VLAN is configured for this product in order to allow communication between hosts A–B and hosts C–D.
Port VLAN setting example
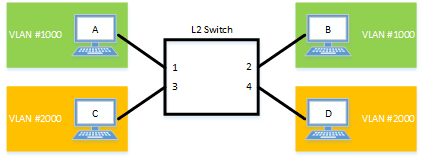
The LAN port settings for this product are as follows.
- Set LAN ports #1/#2 as access ports, and associate them with VLAN #1000.
- Set LAN ports #3/#4 as access ports, and associate them with VLAN #2000.
- Switch to VLAN mode using the vlan database command, and define two VLANs using the vlan command.
Yamaha(config)# vlan database … (Transition to VLAN mode) Yamaha(config-vlan)# vlan 1000 … (Create VLAN #1000) Yamaha(config-vlan)# vlan 2000 … (Create VLAN #2000) Yamaha(config-if)# exit
- Set LAN ports #1–2 as access ports, and associate them with VLAN #1000.
Yamaha(config)# interface port1.1-2 … (Transition to interface mode) Yamaha(config-if)# switchport mode access … (Set as access port) Yamaha(config-if)# switchport access vlan 1000 … (Specify VLAN ID) Yamaha(config-if)# exit
- Set LAN ports #3–4 as access ports, and associate them with VLAN #2000.
Yamaha(config)# interface port1.3-4 Yamaha(config-if)# switchport mode access Yamaha(config-if)# switchport access vlan 2000 Yamaha(config-if)# exit
- Confirm the VLAN settings.
Yamaha#show vlan brief (u)-Untagged, (t)-Tagged VLAN ID Name State Member ports ======= ================ ======= =============================== 1 default ACTIVE port1.5(u) port1.6(u) port1.7(u) port1.8(u) 1000 VLAN1000 ACTIVE port1.1(u) port1.2(u) 2000 VLAN2000 ACTIVE port1.3(u) port1.4(u)
5.2 Tagged VLAN settings
In this example, a tagged VLAN is configured between #A and #B of this product, in order to communicate between hosts A–B and hosts C–D.
Tagged VLAN setting example

The LAN port settings for #A and #B of this product are as follows.
- Set LAN port #1 as an access port, and associate it with VLAN #1000
- Set LAN port #2 as an access port, and associate it with VLAN #2000
- Set LAN port #3 as a trunk port, and associate it with LAN #1000 and VLAN #2000
- [Switch #A/#B] Define VLAN.
Yamaha(config)#vlan database … (Transition to VLAN mode) Yamaha(config-vlan)#vlan 1000 … (Define VLAN 1000) Yamaha(config-vlan)#vlan 2000 … (Define VLAN 2000)
- [Switch #A/#B] Set LAN port #1 as the access port, and associate it with VLAN #1000.
Yamaha(config)#interface port1.1 … (Transition to interface mode) Yamaha(config-if)#switchport mode access … (Set as access port) Yamaha(config-if)#switchport access vlan 1000 … (Associate to VLAN 1000) Yamaha(config-if)#exit
- [Switch #A/#B] Set LAN port #2 as the access port, and associate it with VLAN #2000.
Yamaha(config)#interface port1.2 … (Transition to interface mode) Yamaha(config-if)#switchport mode access … (Set as access port) Yamaha(config-if)#switchport access vlan 2000 … (Associate to VLAN 2000) Yamaha(config-if)#exit
- [Switch #B] Set LAN port #3 as a trunk port, and associate it with VLAN #1000/#2000.
Yamaha(config)#interface port1.3 … (Transition to interface mode) Yamaha(config-if)#switchport mode trunk … (Set as trunk port) Yamaha(config-if)#switchport trunk allowed vlan add 1000 … (Add VLAN 1000) Yamaha(config-if)#switchport trunk allowed vlan add 2000 … (Add VLAN 2000) Yamaha(config-if)#exit
- Confirm the VLAN settings.
Yamaha#show vlan brief (u)-Untagged, (t)-Tagged VLAN ID Name State Member ports ======= ================================ ======= ====================== 1 default ACTIVE port1.3(u) 1000 VLAN1000 ACTIVE port1.1(u) port1.3(t) 2000 VLAN2000 ACTIVE port1.2(u) port1.3(t)
5.3 Private VLAN settings
This example makes private VLAN settings for this product, to achieve the following.
Hosts connected to ports 1–7 will connect to the Internet and other external lines, through the line to which port 8 is connected
Communications between hosts connected to ports 1–4 are blocked (isolated VLAN: VLAN #21)
Communications between hosts connected to ports 5–7 are permitted (community VLAN: VLAN #22)
Communications between hosts connected to ports 1–4 and ports 5–7 are blocked
Private VLAN setting example
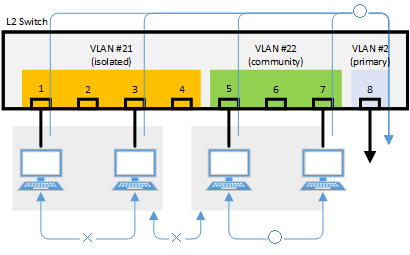
- Define the VLAN ID to be used for the private VLAN.
Yamaha(config)# vlan database … (Transition to VLAN mode) Yamaha(config-vlan)# vlan 2 … (Create VLAN) Yamaha(config-vlan)# vlan 21 Yamaha(config-vlan)# vlan 22 Yamaha(config-vlan)# private-vlan 2 primary … (Set Primary VLAN) Yamaha(config-vlan)# private-vlan 21 isolated … (Set Isolated VLAN) Yamaha(config-vlan)# private-vlan 22 community … (Set Community VLAN) Yamaha(config-vlan)# private-vlan 2 association add 21 … (Associate with Primary VLAN) Yamaha(config-vlan)# private-vlan 2 association add 22 Yamaha(config-vlan)# exit
- Configure the isolated VLAN (VLAN #21) for LAN ports 1–4.
Yamaha(config)#interface port1.1-4 … (Transition to interface mode) Yamaha(config-if)#switchport mode access … (Set as access port) Yamaha(config-if)#switchport access vlan 21 .. (Associate to VLAN #21) Yamaha(config-if)#switchport mode private-vlan host … (Set as private VLAN’s host port) Yamaha(config-if)#switchport private-vlan host-association 2 add 21 Yamaha(config-if)#exit
- Configure the community VLAN (VLAN #22) for LAN ports 5–7.
Yamaha(config)#interface port1.5-7 … (Transition to interface mode) Yamaha(config-if)#switchport mode access … (Set as access port) Yamaha(config-if)#switchport access vlan 22 … (Associate to VLAN #22) Yamaha(config-if)#switchport mode private-vlan host … (Set as private VLAN’s host port) Yamaha(config-if)#switchport private-vlan host-association 2 add 22 Yamaha(config-if)#exit
- Configure the primary VLAN (VLAN #2) for LAN port 8. (Promiscuous port)
Yamaha(config)#interface port1.8 … (Transition to interface mode) Yamaha(config-if)#switchport mode access … (Set as access port) Yamaha(config-if)#switchport access vlan 2 … (Associate to VLAN #2) Yamaha(config-if)#switchport mode private-vlan promiscuous … (Set as private VLAN’s promiscuous port) Yamaha(config-if)#switchport private-vlan mapping 2 add 21 Yamaha(config-if)#switchport private-vlan mapping 2 add 22 Yamaha(config-if)#exit
- Confirm the VLAN settings.
Yamaha#show vlan brief (u)-Untagged, (t)-Tagged VLAN ID Name State Member ports ======= ================================ ======= ====================== 1 default ACTIVE 2 VLAN0002 ACTIVE port1.8(u) 21 VLAN0021 ACTIVE port1.1(u) port1.2(u) port1.3(u) port1.4(u) 22 VLAN0022 ACTIVE port1.5(u) port1.6(u) port1.7(u) Yamaha#show vlan private-vlan PRIMARY SECONDARY TYPE INTERFACES ------- --------- ---------- ---------- 2 21 isolated port1.1 port1.2 port1.3 port1.4 2 22 community port1.5 port1.6 port1.7
5.4 Voice VLAN settings
Make voice VLAN settings for this product, and implement the following.
Connect an IP phone to port 1. Connect a PC to the other LAN port of the IP phone.
Using LLDP-MED, make the following settings from this product for the IP phone.
- As voice traffic for the IP phone, transmit and receive 802.1q tagged frames of VLAN #2.
- Untagged frames are transmitted and received as PC data traffic.
- Use a CoS value of 6 when transmitting and receiving voice traffic.
- Define the VLAN ID used by the voice VLAN.
Yamaha(config)# vlan database … (transition to vlan mode) Yamaha(config-vlan)# vlan 2 … (create a VLAN) Yamaha(config-vlan)# exit
- Set voice VLAN for LAN port #1.
Yamaha(config)#interface port1.1 … (transition to interface mode) Yamaha(config-if)#switchport mode access … (assign as access port) Yamaha(config-if)#switchport voice vlan 2 … (set voice traffic as tagged frames of VLAN #2) Yamaha(config-if)#switchport voice cos 6 … (set CoS value to 6 for voice traffic) Yamaha(config-if)#exit
- Set QoS for LAN port #1.
Yamaha(config)#qos enable … (enable QoS) Yamaha(config)#interface port1.1 … (transition to interface mode) Yamaha(config-if)#qos trust cos ... (set trust mode to CoS) Yamaha(config-if)#exit
- Set LLDP-MED transmission and reception for LAN port #1.
Yamaha(config)#interface port1.1 … (transition to interface mode) Yamaha(config-if)#lldp-agent ... (create LLDP agent, transition modes) Yamaha(lldp-agent)#tlv-select med ... (set LLDP-MED TLV) Yamaha(lldp-agent)#set lldp enable txrx ... (set LLDP transmission and reception mode) Yamaha(lldp-agent)#exit Yamaha(config-if)#exit Yamaha(config)#lldp run … (enable LLDP function) Yamaha(config)#exit
6 Points of Caution
A host port that is associated with a private VLAN cannot be aggregated as a link aggregation logical interface; this limitation is specific to host ports.
7 Related Documentation
Multiple VLAN
1 Function Overview
On a multiple VLAN, by associating a port with a multiple VLAN group, you can block traffic from ports that do not belong to the same multiple VLAN group.
You can also join a single port to multiple VLAN groups.
By using this function, it is easy to handle requests to block only traffic between terminals, such as the example below.
Example of using multiple VLANs
2 Definition of Terms Used
None
3 Function Details
3.1 Operating Specifications
Use the switchport multiple-vlan group command to configure a multiple VLAN group.
Multiple VLANs can be configured as LAN/SFP ports and link aggregation logical interfaces.
If you wish to configure a multiple VLAN group for a trunk port, this will be applied to all relevant VLANs that belong to the port in question.
The VLAN group settings will also be applied to a multicast frame.
This can be used together with the following functions. Control of traffic enable/disable for these functions is set according to the multiple VLAN settings.
- Port-based VLAN/tagged VLAN/voice VLAN
- Port authentication
A multiple VLAN can contain up to 256 groups.
Use the show vlan multiple-vlan group command to confirm the setting status for the interface of each multiple VLAN group.
3.2 Examples of traffic between multiple VLAN groups
Example of traffic for a multiple VLAN group
When using multiple VLAN group settings (Group #1 through #4) as shown in the diagram above, enabling/disabling traffic between specific ports A/B and the reasons for such as shown in the table below.
Traffic enabled/disabled between specific ports A/B
| Port number A (group) | Port number B (group) | Traffic enable/disable | Reason |
|---|---|---|---|
| port1.1 (Group 1) | port1.2 (Group 2) | Disabled | The multiple VLAN group is different |
| port1.1 (Group 1) | port1.3 (Group 1) | Enabled | Associated with multiple VLAN group #1 |
| port1.2 (Group 2) | port1.4 (Group 2) | Enabled | Associated with multiple VLAN group #2 |
| port1.5 (Group 3) | port1.7 (Group 3,4) | Enabled | Associated with multiple VLAN group #3 |
| port1.6 (no group) | port1.8 (Group 4) | Disabled | The multiple VLAN group is different |
| port1.7 (Group 3,4) | port1.8 (Group 4) | Enabled | Associated with multiple VLAN group #4 |
Also, traffic can be established between ports that are not associated with a multiple VLAN group, so long as it is within the same VLAN.
3.3 Communication example when inter-VLAN routing is possible
Example of inter-VLAN routing communication
Inter-VLAN routing is possible with L2 switches with routing enabled. In inter-VLAN routing, packets that are routed by hardware can be controlled by multiple VLAN groups.
When using multiple VLAN group settings (Group #1 through #2) as shown in the diagram above, enabling/disabling traffic between specific ports A/B and the reasons for such as shown in the table below.
Communication enable/disable between specific ports A/B when routing between VLANs is possible
| Port number A (group) | Port number B (group) | Traffic enable/disable | Reason |
|---|---|---|---|
| port1.3 (Group 1) | port1.5 (Group 1) | Enabled | Associated with multiple VLAN group #1 |
| port1.4 (Group 1) | port1.8 (Group 2) | Disabled | The multiple VLAN group is different |
4 Related Commands
Related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Multiple VLAN group settings | switchport multiple-vlan group |
| Settings for the name of multiple VLAN group | multiple-vlan group name |
| Show multiple VLANs | show vlan multiple-vlan |
5 Examples of Command Execution
5.1 Multiple VLAN settings example 1
This configures multiple VLAN settings to achieve the following.
Hosts connected to ports 1–7 will connect to the Internet and other external lines, through the line to which port 8 is connected
Communications between hosts connected to ports 1–4 are blocked
Communications between hosts connected to ports 5–7 are permitted
Communications between hosts connected to ports 1–4 and ports 5–7 are blocked
Examples of multiple VLAN settings
The multiple VLAN group settings are as follows.
- port1.1: Associated with multiple VLAN group #1
- port1.2: Associated with multiple VLAN group #2
- port1.3: Associated with multiple VLAN group #3
- port1.4: Associated with multiple VLAN group #4
- port1.5: Associated with multiple VLAN group #5
- port1.6: Associated with multiple VLAN group #5
- port1.7: Associated with multiple VLAN group #5
- port1.8: Associated with multiple VLAN groups #1, #2, #3, #4, #5
- This sets the name of multiple VLAN group #1 to “Network1”.
Yamaha(config)# multiple-vlan group 1 name Network1 …(settings for the name of multiple VLAN group #1)
- This sets the name of multiple VLAN group #5 to “Network5”.
Yamaha(config)# multiple-vlan group 1 name Network5 …(settings for the name of multiple VLAN group #5)
- Associates port1.1 through port1.4 with multiple VLAN groups #1 through #4 respectively.
Yamaha(config)# interface port1.1 … (Transition to interface mode) Yamaha(config-if)# switchport multiple-vlan group 1 … (Multiple VLAN group setting) Yamaha(config-if)# exit Yamaha(config)# interface port1.2 … (Transition to interface mode) Yamaha(config-if)# switchport multiple-vlan group 2 … (Multiple VLAN group setting) Yamaha(config-if)# exit Yamaha(config)# interface port1.3 … (Transition to interface mode) Yamaha(config-if)# switchport multiple-vlan group 3 … (Multiple VLAN group setting) Yamaha(config-if)# exit Yamaha(config)# interface port1.4 … (Transition to interface mode) Yamaha(config-if)# switchport multiple-vlan group 4 … (Multiple VLAN group setting) Yamaha(config-if)# exit
- This associates port1.5 through port1.7 with multiple VLAN group #5.
Yamaha(config)# interface port1.5-7 … (Transition to interface mode) Yamaha(config-if)# switchport multiple-vlan group 5 … (Multiple VLAN group setting) Yamaha(config-if)# exit
- This associates port1.8 with multiple VLAN groups #1, #2, #3, #4, #5.
Yamaha(config)# interface port1.8 … (Transition to interface mode) Yamaha(config-if)# switchport multiple-vlan group 1-5 … (Multiple VLAN group setting) Yamaha(config-if)# exit
- This checks the multiple VLAN group settings.
Yamaha>show vlan multiple-vlan GROUP ID Name Member ports ======== ================================ ====================== 1 Network1 port1.1 port1.8 2 GROUP0002 port1.2 port1.8 3 GROUP0003 port1.3 port1.8 4 GROUP0004 port1.4 port1.8 5 Network5 port1.5 port1.6 port1.7 port1.8
6 Points of Caution
The points of caution regarding this function are as follows.
- The function cannot be used in conjunction with a private VLAN.
- The multiple VLAN group to associate with a link aggregation logical interface must be the same.
- A multiple VLAN group is only applicable to forwarding between ports. Voluntary packets will not be affected by the settings of a multiple VLAN group.
- Even if a multiple VLAN is configured, communication may not work correctly due to the following influences.
- Block status of spanning tree
- IGMP snooping/MLD snooping status
- Blocked status of loop detection
- In inter-VLAN routing, multiple VLAN communication restrictions are applied only to packets routed by hardware processing.
Restrictions do not apply to inter-VLAN routing through the CPU.
7 Related Documentation
Spanning tree
1 Function Overview
The spanning tree is a function that maintains redundancies in the network routes while preventing loops.
Normally, the L2 switch floods the adjacent switch with the broadcast packets.
If the network is constructed as a loop, the switches will flood each other, causing the loop to occur.
This results in a major degradation of bandwidth and CPU resources in the switches.
The spanning tree determines the roles of each port and establishes a network construction where the broadcast packets do not keep traveling around, for networks that contain physical loops as well.
When there are problems linking, the problem is detected and the tree is reconstructed in order to restore the system.
This product supports STP, RSTP, and MSTP.
Spanning tree function overview

2 Definition of Terms Used
- STP: Spanning Tree Protocol (802.1d)
The spanning tree protocol (STP) exchanges BPDU (bridge protocol data unit) messages, in order to avoid loops.
This product supports IEEE802.1d and RFC4188.
- RSTP: Rapid Spanning Tree Protocol (802.1w)
The rapid spanning tree protocol (RSTP) is an extension of STP. It can recover the spanning tree more quickly than STP, when the network architecture has changed or when there is a problem linking.
This product supports IEEE802.1w and RFC4318.
- MSTP: Multiple Spanning Tree Protocol (802.1s)
Multiple spanning tree protocol (MSTP) is a further extension of STP and RSTP. It groups the VLAN into instances, and constructs a spanning tree for each group.
This can be used to distribute load within the network routes.
This product supports IEEE802.1s.
3 Function Details
This product supports the following functions in order to flexibly handle the construction of routes based on MSTP.
- Set priority
- Set bridge priority
- Set port priority
- Set path cost
- Set timeout
- Set forward delay time
- Set maximum aging time
- Specify edge port (Port Fast settings)
- BPDU guard
- BPDU filtering
- Route guard
4 Related Commands
The related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Set spanning tree for the system | spanning-tree shutdown |
| Set forward delay time | spanning-tree forward-time |
| Set maximum aging time | spanning-tree max-age |
| Set bridge priority | spanning-tree priority |
| Set spanning tree for an interface | spanning-tree |
| Set spanning tree link type | spanning-tree link-type |
| Set interface BPDU filtering | spanning-tree bpdu-filter |
| Set interface BPDU guard | spanning-tree bpdu-guard |
| Set interface path cost | spanning-tree path-cost |
| Set interface priority | spanning-tree priority |
| Set edge port for interface | spanning-tree edgeport |
| Show spanning tree status | show spanning-tree |
| Show spanning tree BPDU statistics | show spanning-tree statistics |
| Clear protocol compatibility mode | clear spanning-tree detected protocols |
| Move to MST mode | spanning-tree mst configuration |
| Generate MST instance | instance |
| Set VLAN for MST instance | instance vlan |
| Set priority of MST instance | instance priority |
| Set MST region name | region |
| Set revision number of MST region | revision |
| Set MST instance for interface | spanning-tree instance |
| Set interface priority for MST instance | spanning-tree instance priority |
| Set interface path cost for MST instance | spanning-tree instance path-cost |
| Show MST region information | show spanning-tree mst config |
| Show MSTP information | show spanning-tree mst |
| Show MST instance information | show spanning-tree mst instance |
5 Examples of Command Execution
5.1 MSTP setting example
Use this product to realize the architecture shown in the diagram below.
MSTP architecture diagram

- In this example, MST instances are used to construct the spanning tree.
- A different route is set for each MST instance (VLAN), in order to distribute network load.
- The LAN port that is connected to the PC is set as the edge port.
- [Switch #A] Define VLAN #2 and VLAN #3.
Yamaha(config)#vlan database Yamaha(config-vlan)#vlan 2 ... (VLAN #2 definition) Yamaha(config-vlan)#vlan 3 ... (VLAN #3 definition) Yamaha(config-vlan)#exit
- [Switch #A] Set the CIST priority.
Yamaha(config)#spanning-tree priority 8192 ... (Set CIST priority to 8192)
- [Switch #A] Set the MST.
Yamaha(config)#spanning-tree mst configuration Yamaha(config-mst)#region Sample ... (Set MST region name to “Sample”) Yamaha(config-mst)#revision 1 ... (Set MST revision number to 1) Yamaha(config-mst)#instance 2 vlan 2 ... (Define MST interface #2, and associate with VLAN #2) Yamaha(config-mst)#instance 3 vlan 3 ... (Define MST interface #3, and associate with VLAN #3) Yamaha(config-mst)#exit
- [Switch #A] Set LAN ports #1–#2 as trunk ports, and associate them with VLAN #2–#3.
Also, set the MST instances #2–#3.
Yamaha(config)#interface port1.1 Yamaha(config-if)#switchport mode trunk ... (Set as trunk port) Yamaha(config-if)#switchport trunk allowed vlan add 2,3 ... (Associate to VLAN #2–#3) Yamaha(config-if)#spanning-tree instance 2 ... (Set MST instance #2) Yamaha(config-if)#spanning-tree instance 3 ... (Set MST instance #3) Yamaha(config-if)#exit (Also perform the above settings for LAN port #2.)
- [Switch #A] Set LAN port #3 as the access port, and associate it with VLAN #2.
Also, set the MST instance #2, and make it an edge port.
Yamaha(config)#interface port1.3 Yamaha(config-if)#switchport mode access ... (Set as access port) Yamaha(config-if)#switchport access vlan 2 ... (Associate to VLAN #2) Yamaha(config-if)#spanning-tree instance 2 ... (Set MST instance #2) Yamaha(config-if)#spanning-tree edgeport ... (Set as edge port) Yamaha(config-if)#exit
- [Switch #A] Set LAN port #4 as the access port, and associate it with VLAN #3.
Also, set the MST instance #3, and make it an edge port.
Yamaha(config)#interface port1.4 Yamaha(config-if)#switchport mode access ... (Set as access port) Yamaha(config-if)#switchport access vlan 3 ... (Associate to VLAN #3) Yamaha(config-if)#spanning-tree instance 3 ... (Set MST instance #3) Yamaha(config-if)#spanning-tree edgeport ... (Set as edge port) Yamaha(config-if)#exit
- [Switch #B] Define VLAN #2 and VLAN #3.
Yamaha(config)#vlan database Yamaha(config-vlan)#vlan 2 ... (VLAN #2 definition) Yamaha(config-vlan)#vlan 3 ... (VLAN #3 definition) Yamaha(config-vlan)#exit
- [Switch #B] Set the CIST priority.
Yamaha(config)#spanning-tree priority 16384 ... (Set CIST priority to 16384)
- [Switch #B] Set the MST.
Yamaha(config)#spanning-tree mst configuration Yamaha(config-mst)#region Sample ... (Set MST region name to “Sample”) Yamaha(config-mst)#revision 1 ... (Set MST revision number to 1) Yamaha(config-mst)#instance 2 vlan 2 ... (Define MST interface #2, and associate with VLAN #2) Yamaha(config-mst)#instance 2 priority 8192 ... (Set priority of MST instance #2 to 8192) Yamaha(config-mst)#instance 3 vlan 3 ... (Define MST interface #3, and associate with VLAN #3) Yamaha(config-mst)#instance 3 priority 16384 ... (Set priority of MST instance #3 to 16384) Yamaha(config-mst)#exit
- [Switch #B] Set LAN ports #1–#2 as trunk ports, and associate them with VLAN #2–#3.
Also, set the MST instances #2–#3.
Yamaha(config)#interface port1.1 Yamaha(config-if)#switchport mode trunk ... (Set as trunk port) Yamaha(config-if)#switchport trunk allowed vlan add 2,3 ... (Associate to VLAN #2–#3) Yamaha(config-if)#spanning-tree instance 2 ... (Set MST instance #2) Yamaha(config-if)#spanning-tree instance 3 ... (Set MST instance #3) Yamaha(config-if)#exit (Also perform the above settings for LAN port #2.)
- [Switch #B] Set LAN port #3 as the access port, and associate it with VLAN #2.
Also, set the MST instance #2, and make it an edge port.
Yamaha(config)#interface port1.3 Yamaha(config-if)#switchport mode access ... (Set as access port) Yamaha(config-if)#switchport access vlan 2 ... (Associate to VLAN #2) Yamaha(config-if)#spanning-tree instance 2 ... (Set MST instance #2) Yamaha(config-if)#spanning-tree edgeport ... (Set as edge port) Yamaha(config-if)#exit (Also perform the above settings for LAN port #4.)
- [Switch #C] Define VLAN #2 and VLAN #3.
Yamaha(config)#vlan database Yamaha(config-vlan)#vlan 2 ... (VLAN #2 definition) Yamaha(config-vlan)#vlan 3 ... (VLAN #3 definition) Yamaha(config-vlan)#exit
- [Switch #C] Set the MST.
Yamaha(config)#spanning-tree mst configuration Yamaha(config-mst)#region Sample ... (Set MST region name to “Sample”) Yamaha(config-mst)#revision 1 ... (Set MST revision number to 1) Yamaha(config-mst)#instance 2 vlan 2 ... (Define MST interface #2, and associate with VLAN #2) Yamaha(config-mst)#instance 2 priority 16384 ... (Set priority of MST instance #2 to 16384) Yamaha(config-mst)#instance 3 vlan 3 ... (Define MST interface #3, and associate with VLAN #3) Yamaha(config-mst)#instance 3 priority 8192 ... (Set priority of MST instance #3 to 8192) Yamaha(config-mst)#exit
- [Switch #C] Set LAN ports #1–#2 as trunk ports, and associate them with VLAN #2–#3.
Also, set the MST instances #2–#3.
Yamaha(config)#interface port1.1 Yamaha(config-if)#switchport mode trunk ... (Set as trunk port) Yamaha(config-if)#switchport trunk allowed vlan add 2,3 ... (Associate to VLAN #2–#3) Yamaha(config-if)#spanning-tree instance 2 ... (Set MST instance #2) Yamaha(config-if)#spanning-tree instance 3 ... (Set MST instance #3) Yamaha(config-if)#exit (Also perform the above settings for LAN port #2.)
- [Switch #C] Set LAN port #3 as the access port, and associate it with VLAN #3.
Also, set the MST instance #3, and make it an edge port.
Yamaha(config)#interface port1.3 Yamaha(config-if)#switchport mode access ... (Set as access port) Yamaha(config-if)#switchport access vlan 3 ... (Associate to VLAN #3) Yamaha(config-if)#spanning-tree instance 3 ... (Set MST instance #3) Yamaha(config-if)#spanning-tree edgeport ... (Set as edge port) Yamaha(config-if)#exit (Also perform the above settings for LAN port #4.)
- Connect the LAN cable.
- [Switch #A] Check the CIST architecture.
Yamaha>show spanning-tree | include Root Id % Default: CIST Root Id 200100a0deaeb920 ... (The higher-priority switch #A is the CIST root bridge) % Default: CIST Reg Root Id 200100a0deaeb920 Yamaha>show spanning-tree | include Role % port1.1: Port Number 905 - Ifindex 5001 - Port Id 0x8389 - Role Designated - State Forwarding % port1.2: Port Number 906 - Ifindex 5002 - Port Id 0x838a - Role Designated - State Forwarding % port1.3: Port Number 907 - Ifindex 5003 - Port Id 0x838b - Role Designated - State Forwarding % port1.4: Port Number 908 - Ifindex 5004 - Port Id 0x838c - Role Designated - State Forwarding % port1.5: Port Number 909 - Ifindex 5005 - Port Id 0x838d - Role Disabled - State Discarding % port1.6: Port Number 910 - Ifindex 5006 - Port Id 0x838e - Role Disabled - State Discarding % port1.7: Port Number 911 - Ifindex 5007 - Port Id 0x838f - Role Disabled - State Discarding % port1.8: Port Number 912 - Ifindex 5008 - Port Id 0x8390 - Role Disabled - State Discarding % port1.9: Port Number 913 - Ifindex 5009 - Port Id 0x8391 - Role Disabled - State Discarding % port1.10: Port Number 914 - Ifindex 5010 - Port Id 0x8392 - Role Disabled - State Discarding
- [Switch #B] Check the CIST architecture.
Yamaha>show spanning-tree | include Root Id % Default: CIST Root Id 200100a0deaeb920 ... (The higher-priority switch #A is the CIST root bridge) % Default: CIST Reg Root Id 200100a0deaeb920 Yamaha>show spanning-tree | include Role % port1.1: Port Number 905 - Ifindex 5001 - Port Id 0x8389 - Role Rootport - State Forwarding % port1.2: Port Number 906 - Ifindex 5002 - Port Id 0x838a - Role Designated - State Forwarding % port1.3: Port Number 907 - Ifindex 5003 - Port Id 0x838b - Role Designated - State Forwarding % port1.4: Port Number 908 - Ifindex 5004 - Port Id 0x838c - Role Designated - State Forwarding % port1.5: Port Number 909 - Ifindex 5005 - Port Id 0x838d - Role Disabled - State Discarding % port1.6: Port Number 910 - Ifindex 5006 - Port Id 0x838e - Role Disabled - State Discarding % port1.7: Port Number 911 - Ifindex 5007 - Port Id 0x838f - Role Disabled - State Discarding % port1.8: Port Number 912 - Ifindex 5008 - Port Id 0x8390 - Role Disabled - State Discarding % port1.9: Port Number 913 - Ifindex 5009 - Port Id 0x8391 - Role Disabled - State Discarding % port1.10: Port Number 914 - Ifindex 5010 - Port Id 0x8392 - Role Disabled - State Discarding
- [Switch #C] Check the CIST architecture.
Yamaha>show spanning-tree | include Root Id % Default: CIST Root Id 200100a0deaeb920 ... (The higher-priority switch #A is the CIST root bridge) % Default: CIST Reg Root Id 200100a0deaeb920 Yamaha>show spanning-tree | include Role % port1.1: Port Number 905 - Ifindex 5001 - Port Id 0x8389 - Role Alternate - State Discarding ... (LAN #1 port of lower-priority switch #C is the CIST alternate port) % port1.2: Port Number 906 - Ifindex 5002 - Port Id 0x838a - Role Rootport - State Forwarding % port1.3: Port Number 907 - Ifindex 5003 - Port Id 0x838b - Role Designated - State Forwarding % port1.4: Port Number 908 - Ifindex 5004 - Port Id 0x838c - Role Designated - State Forwarding % port1.5: Port Number 909 - Ifindex 5005 - Port Id 0x838d - Role Disabled - State Discarding % port1.6: Port Number 910 - Ifindex 5006 - Port Id 0x838e - Role Disabled - State Discarding % port1.7: Port Number 911 - Ifindex 5007 - Port Id 0x838f - Role Disabled - State Discarding % port1.8: Port Number 912 - Ifindex 5008 - Port Id 0x8390 - Role Disabled - State Discarding % port1.9: Port Number 913 - Ifindex 5009 - Port Id 0x8391 - Role Disabled - State Discarding % port1.10: Port Number 914 - Ifindex 5010 - Port Id 0x8392 - Role Disabled - State Discarding
- [Switch #A] Check the architecture of MST instance #2.
Yamaha>show spanning-tree mst instance 2 | include Root Id % Default: MSTI Root Id 200200a0deaeb879 ... (The higher-priority switch #B is the root bridge for MST instance #2) Yamaha>show spanning-tree mst instance 2 | include Role % port1.1: Port Number 905 - Ifindex 5001 - Port Id 0x8389 - Role Rootport - State Forwarding % port1.2: Port Number 906 - Ifindex 5002 - Port Id 0x838a - Role Alternate - State Discarding ... (LAN #2 port of lower-priority switch #A is the alternate port for MST instance #2) % port1.3: Port Number 907 - Ifindex 5003 - Port Id 0x838b - Role Designated - State Forwarding
- [Switch #B] Check the architecture of MST instance #2.
Yamaha>show spanning-tree mst instance 2 | include Root Id % Default: MSTI Root Id 200200a0deaeb879 ... (The higher-priority switch #B is the root bridge for MST instance #2) Yamaha>show spanning-tree mst instance 2 | include Role % port1.1: Port Number 905 - Ifindex 5001 - Port Id 0x8389 - Role Designated - State Forwarding % port1.2: Port Number 906 - Ifindex 5002 - Port Id 0x838a - Role Designated - State Forwarding % port1.3: Port Number 907 - Ifindex 5003 - Port Id 0x838b - Role Designated - State Forwarding % port1.4: Port Number 908 - Ifindex 5004 - Port Id 0x838c - Role Designated - State Forwarding
- [Switch #C] Check the architecture of MST instance #2.
Yamaha>show spanning-tree mst instance 2 | include Root Id % Default: MSTI Root Id 200200a0deaeb879 ... (The higher-priority switch #B is the root bridge for MST instance #2) Yamaha>show spanning-tree mst instance 2 | include Role % port1.1: Port Number 905 - Ifindex 5001 - Port Id 0x8389 - Role Rootport - State Forwarding % port1.2: Port Number 906 - Ifindex 5002 - Port Id 0x838a - Role Designated - State Forwarding
- [Switch #A] Check the architecture of MST instance #3.
Yamaha>show spanning-tree mst instance 3 | include Root Id % Default: MSTI Root Id 200300a0deaeb83d ... (The higher-priority switch #C is the root bridge for MST instance #3) Yamaha>show spanning-tree mst instance 3 | include Role % port1.1: Port Number 905 - Ifindex 5001 - Port Id 0x8389 - Role Alternate - State Discarding ... (LAN #1 port of lower-priority switch #A is the alternate port for MST instance #3) % port1.2: Port Number 906 - Ifindex 5002 - Port Id 0x838a - Role Rootport - State Forwarding % port1.4: Port Number 908 - Ifindex 5004 - Port Id 0x838c - Role Designated - State Forwarding
- [Switch #B] Check the architecture of MST instance #3.
Yamaha>show spanning-tree mst instance 3 | include Root Id % Default: MSTI Root Id 200300a0deaeb83d ... (The higher-priority switch #C is the root bridge for MST instance #3) Yamaha>show spanning-tree mst instance 3 | include Role % port1.1: Port Number 905 - Ifindex 5001 - Port Id 0x8389 - Role Designated - State Forwarding % port1.2: Port Number 906 - Ifindex 5002 - Port Id 0x838a - Role Rootport - State Forwarding
- [Switch #C] Check the architecture of MST instance #3.
Yamaha>show spanning-tree mst instance 3 | include Root Id % Default: MSTI Root Id 200300a0deaeb83d ... (The higher-priority switch #C is the root bridge for MST instance #3) Yamaha>show spanning-tree mst instance 3 | include Role % port1.1: Port Number 905 - Ifindex 5001 - Port Id 0x8389 - Role Designated - State Forwarding % port1.2: Port Number 906 - Ifindex 5002 - Port Id 0x838a - Role Designated - State Forwarding % port1.3: Port Number 907 - Ifindex 5003 - Port Id 0x838b - Role Designated - State Forwarding % port1.4: Port Number 908 - Ifindex 5004 - Port Id 0x838c - Role Designated - State Forwarding
6 Points of Caution
- STP and RSTP on this product are supported by backward-compatibility provided by MSTP.
7 Related Documentation
- L2 switching functions: VLAN
- STP
- IEEE802.1d
- RFC4188
- RSTP
- IEEE802.1w
- RFC4318
- MSTP
- IEEE802.1s
- SWR2310 Series Technical Data (Basic Functions)
- Layer 2 functions
- Proprietary loop detection
Proprietary loop detection
1 Function Overview
This product offers a proprietary system to detect whether there is a loop in the network environment that was configured.
A proprietary loop detection frame is sent from the LAN/SFP port, and the unit monitors whether the frame returns or not.
If the transmitted frame returns, the system determines that there is a loop in the port in question.
2 Definition of Terms Used
- LDF (Loop Detection Frame)
- This is a Yamaha proprietary Ethernet frame that is used to detect loops.
3 Function Details
3.1 Loop detection operating specifications
The loop detection specifications for this product are shown below.
- In addition to enabling/disabling the entire system, the loop detection on this product can enable/disable individual ports.
When detecting loops in LAN/SFP ports, the system-wide setting must be set to enable.
- Use the loop-detect command in global configuration mode for system-wide settings.
- Use the loop-detect command in the interface mode of the relevant port for individual LAN/SFP port settings.
- The default settings for the loop detection function are as shown below. (In the initial state, this function is not operating.)
- System-wide settings: disabled
- LAN/SFP port settings: enabled
- When the system-wide settings for both loop detection and spanning tree protocol are set to enabled, the spanning tree protocol is given priority for LAN/SFP port settings.
- If the loop detection function is enabled for this product, the following operations are performed.
- Loop detection frames (hereafter “LDF”) are sent every two seconds from the linked-up LAN/SFP port.
The loop detection function cannot be used on static/LACP logical interfaces, and ports on which mirror settings have been made (mirror ports).
- When the transmitted loop detection frame receives itself, it determines that a loop has occurred, and the following operations are performed.
- Port Shutdown
When both the transmitting and the receiving LAN/SFP port is the same, the relevant port is shut down.
The linkup will be made five minutes after shutdown, and LDF transmission will resume. (If a loop has occurred, this operation will repeat.)
When a linkup to the relevant port is desired within five minutes of monitored time, the no shutdown command is used.
- Port Blocking
When the port number of the transmitting LAN/SFP port is smaller than the receiving port number, all frames except for LDF are blocked.
The LDF will be transmitted periodically, but LDF will not be forwarded from other devices.
For the LAN/SFP ports that were blocked, if the LDF that was transmitted does not return within five seconds, it is determined that the loop has been resolved, and normal communications are resumed.
- Port Detected
When the port number of the LAN/SFP port that was transmitted is larger than the port number during reception, another port is doing the blocking, so communication continues as normal.
- Port Shutdown
- When a loop is detected, the port lamp display on this product changes to a dedicated status, and the following SYSLOG message is output.
- [LOOP]: inf: Detected Loop!: port1.1, 1.3 … (displayed in a five-second cycle, starting from the detection of the loop)
- The port lamp display on this product is restored as communications are resumed after the loop is resolved, and the following SYSLOG message is output.
- [LOOP]: inf: Recovered Loop! : port1.1, 1.3
- Loop detection frames (hereafter “LDF”) are sent every two seconds from the linked-up LAN/SFP port.
- The “detected” operation can be forcibly performed without performing shutdown/blocking of the LAN/SFP port on which the loop was detected.
- Use the loop-detect blocking-disable command for this setting.
- If this setting is “enabled”, port blocking will be implemented on the next largest port number. (Shutdown operations will not occur.)
- A force-clear can be performed on the loop detection status (detected, blocking) by using the loop-detect reset command. (On models equipped with a [MODE] button, this can be also done by holding down the [MODE] button for three seconds.)
If a linkdown has occurred on the port where a loop has been detected, the detection status will be cleared. (The port lamp display is restored, and the following syslog message is outputted.)
- The status of the loop detection function can be checked using the show loop-detect command. The following is displayed.
- System Enable/disable status
- Loop detection status (status for each LAN/SFP port)
- When an LDF is received by a LAN/SFP port when the loop detection function is disabled, the received frames from all other ports will be forwarded as-is.
However, frames will not be forwarded for static/LACP logical interfaces and ports on which mirror settings have been made (mirror ports).
- In the following kinds of situations, loops in hubs that are connected to this product might not be detected.
- Loops are being detected in a connected hub
- Loop detection frames are not being forwarded by a connected hub
3.2 Loop detection example
The following shows examples of loop detection in this product.
Loop detection example
| Loop detection case | Configuration example | Loop detection status |
|---|---|---|
| 1 |  | A loop is detected when the device receives the LDF that it has transmitted.
|
| 2 |  | When loops are detected in multiple ports on the same terminal, the port with the largest number is blocked.
|
| 3 |  | The loop is avoided by blocking multiple ports. The blocking port is selected using the same rules as case 2.
|
| 4 |  | When loops are detected in multiple groups, the port with the largest number in each group is blocked.
|
| 5 |  | When a loop occurs between two switches, one of the switches detects the loop. ○When detected in port1.3 of switch #A
○When detected in port1.7 of switch #B
|
| 6 |  | Out of the six ports that are connected by cable, the port for which the loop is most quickly detected is the one that is blocked. ○When detected in port1.2 of switch #A
○When detected in port1.4 of switch #B
○When detected in port1.6 of switch #C
|
| 7 |  | Because the LDF transmitted from each port returns to these ports, port1.5 and port1.6 will both shut down.
|
| 8 |  | Port1.6 of switch #B is blocked. Depending on the timing, port1.1 of switch #A will shut down; but the loop in port1.1 of switch #A is resolved by blocking port1.6 of switch #B.
|
4 Related Commands
The related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Enable/disable loop detection function (system) | loop-detect enable/disable |
| Enable/disable loop detection function (LAN/SFP port) | loop-detect enable/disable |
| Set port blocking for loop detection | loop-detect blocking enable/disable |
| Reset loop detection status | loop-detect reset |
| Refer to the setting status of loop detection | show loop-detect |
5 Examples of Command Execution
This example detects any loops occurring on this product using the following configuration, when the loop detection function is enabled.
- [Example 1] Loop occurring within this product
- [Example 2] Loop occurring in a third-party hub connected to this product
- This sets LAN ports #1 and #2 to detect loops.
- Enable the loop detection function for the entire system.
Yamaha(config)#loop-detect enable ... (Enable the system-wide loop detection function)
- Enable the loop detection function for LAN ports #1 and #2.
Yamaha(config)#interface port1.1 Yamaha(config-if)#spanning-tree disable ... (Disable the spanning tree function for each LAN port) Yamaha(config-if)#loop-detect enable ... (Enable the loop detection function for each LAN port) Yamaha(config-if)#loop-detect blocking ... (Enable blocking) (Also perform the above settings for LAN port #2.)
- The loop detection function for each LAN port and blocking are both enabled by default, so there is no need to set them.
- Confirm that the loop detection function has been set.
Confirm whether the loop detection function is enabled(*) for LAN ports #1 and #2.
Yamaha>show loop-detect loop-detect: Enable port loop-detect port-blocking status ------------------------------------------------------- port1.1 enable(*) enable Normal port1.2 enable(*) enable Normal port1.3 enable enable Normal port1.4 enable enable Normal port1.5 enable enable Normal port1.6 enable enable Normal port1.7 enable enable Normal port1.8 enable enable Normal port1.9 enable enable Normal : : : : ------------------------------------------------------- (*): Indicates that the feature is enabled.
- If a loop has been detected, the loop detection status can be checked.
- In the case of example 1:
Yamaha>show loop-detect loop-detect: Enable port loop-detect port-blocking status ------------------------------------------------------- port1.1 enable(*) enable Detected ... (LAN port #1 changes to the Detected state) port1.2 enable(*) enable Blocking ... (LAN port #2 changes to the Blocking state) port1.3 enable enable Normal port1.4 enable enable Normal port1.5 enable enable Normal port1.6 enable enable Normal port1.7 enable enable Normal port1.8 enable enable Normal port1.9 enable enable Normal : : : : ------------------------------------------------------- (*): Indicates that the feature is enabled.
- In the case of example 2:
Yamaha>show loop-detect loop-detect: Enable port loop-detect port-blocking status ------------------------------------------------------- port1.1 enable(*) enable Shutdown ... (LAN port #1 changes to the Shutdown state) port1.2 enable(*) enable Normal port1.3 enable enable Normal port1.4 enable enable Normal port1.5 enable enable Normal port1.6 enable enable Normal port1.7 enable enable Normal port1.8 enable enable Normal port1.9 enable enable Normal : : : : ------------------------------------------------------- (*): Indicates that the feature is enabled.
- In the case of example 1:
6 Points of Caution
None
7 Related Documentation
- SWR2310 Series Technical Data (Basic Functions)
- Layer 3 functions
- SWR2310 Series Technical Data (Basic Functions)
- Layer 3 functions
- IPv4/IPv6 common settings
IPv4/IPv6 common settings
1 Function Overview
This product is compatible with the following network environment settings that are common to IPv4 and IPv6, mainly for the purpose of maintenance (configuring the settings of the switch).
- DNS client settings
- Equal cost multipath settings
2 Definition of Terms Used
None
3 Function Details
3.1 DNS client settings
This product supports DNS (Domain Name System) clients.
If a FQDN (Fully Qualified Domain Name) has been set for an NTP server or a syslog server, an inquiry is made to the DNS server to retrieve the IPv4/IPv6 address.
This product provides the following DNS client control functions.
- Set IP address of the DNS server
- Set default domain name
- Set query domain list
Inquiries to the DNS server are enabled by default, and the setting can be changed by using the dns-client enable/disable command.
3.1.1 Set IP address of the DNS server
Up to three IP addresses can be set for the DNS server, using the methods shown below.
- Manual setting using the dns-client name-server command
- This lets you specify the IPv4/IPv6 address.
- Automatic setting via DHCP
- The highest default gateway value takes priority if there is more than one.
This product always gives priority to the information that was set via commands.
Check the configured DNS servers by using the show dns-client command.
3.1.2 Set default domain
Only one default domain can be set using the methods shown below. The domain can be specified using up to 256 characters.
- Manual setting using the dns-client domain-name command
- Automatic setting via DHCP
- The highest default gateway value takes priority if there is more than one.
As with the IP addresses of the DNS server, this product gives priority to the information that was set via commands.
Check the default domain that was set by using the show dns-client command.
The use of a default domain is only allowed if there are no listings in the search domain list.
3.1.3 Set query domain list
This product uses a query domain list to manage the domain names used when inquiring with the DNS.
Up to six domain names can be set on the query domain list using the method below.
- Manual setting using the dns-client domain-list command
The query domain list that has been set can be checked using the show dns-client command.
The query domain list must be within 256 characters total for all domain names registered.
3.2 Equal-cost multi-path settings
This product supports equal-cost multi-path settings using the following functions.
- IPv4 static routing
- IPv6 static routing
- RIPv1, RIPv2, RIPng (only on supporting devices)
- OSPFv2, OSPFv3 (only on supporting devices)
If multiple routes to the same destination are registered in the RIB, these multiple routes will be reflected in the FIB.
Up to eight routes leading to the same destination can be registered in the FIB. The default setting is four routes.
The number of equal-cost multi-paths that can be registered may be changed using the maximum-paths command.
The changes to the settings will not be reflected in actual operations until rebooting.
Use the port-channel load-balance command to configure the load balance rules for equal-cost multi-path destinations.
Caution must be used when changing the load balance rule settings using the port-channel load-balance command, as this has an impact on how link aggregation works.
4 Related Commands
The related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Function types | Operations | Operating commands |
|---|---|---|
| DNS client settings | DNS client settings | dns-client enable/disable |
| Set DNS server address | dns-client name-server | |
| Set default domain name | dns-client domain-name | |
| Set query domain list | dns-client domain-list | |
| Show DNS client settings | show dns-client | |
| Equal-cost multi-path settings | Settings for the number of equal-cost multi-paths that can be registered | maximum-paths |
| Display the number of equal-cost multi-paths that can be registered | show ip route summary | |
| show ipv6 route summary | ||
| Set load balance function rules | port-channel load-balance |
5 Examples of Command Execution
5.1 DNS client settings
Set DNS client settings for this product to prepare an environment for DNS queries.
- Specify 192.168.100.1 and 192.168.100.2 as the IP addresses of the servers for DNS queries.
- Specify example.com as the default domain used for DNS queries.
- Enable the DNS query functionality.
Yamaha(config)#dns-client enable
- Since this is specified as the default value, we do not need to do set this specifically.
- Specify the DNS servers.
Yamaha(config)#dns-client name-server 192.168.100.1 Yamaha(config)#dns-client name-server 192.168.100.2
- Set the default domain.
Yamaha(config)#dns-client domain-name example.com
- Check the DNS client information that was set.
Yamaha#show dns-client DNS client is enabled Default domain : example.com Domain list : Name Servers : 192.168.100.1 192.168.100.2 * - Values assigned by DHCP Client.
5.2 Equal-cost multi-paths
This changes the number of equal-cost multi-paths that can be registered to “5”.
Also, the source and destination IP addresses are used as load balance rules.
- Set the number of equal-cost multi-paths that can be registered
Yamaha(config)#maximum-paths 5 % System Reboot is required for new Maximum-Path value to take effect.
- A reboot is required to apply the settings.
- Set the source and destination IP addresses as load balance rules.
Yamaha(config)#port-channel load-balance src-dst-ip
- Check the current number of equal-cost multi-paths that can be registered.
Yamaha(config)#show ip route summary IP routing table name is Default-IP-Routing-Table(0) IP routing table maximum-paths : 5 Route Source Networks connected 3 rip 2 Total 5
6 Points of Caution
None
7 Related Documentation
None
- SWR2310 Series Technical Data (Basic Functions)
- Layer 3 functions
- IPv4 basic settings
IPv4 basic settings
1 Function Overview
This product is compatible with the following IPv4 network environment settings , mainly for the purpose of maintenance (configuring the settings of the switch).
- IPv4 address settings
- Route information settings
- ARP table settings
2 Definition of Terms Used
- IPv4 link local address
- This is an address that is only valid within the same segment, within the range of 169.254.0.0/16 to 169.254.255.255/16.
3 Function Details
3.1 IPv4 address settings
This product lets you specify the IPv4 address and subnet mask for a VLAN interface.
As the setting method, both fixed settings and automatic settings via DHCP are supported.
- To set the fixed/automatic IPv4 address, use the ip address command.
- The actions when specifying automatic settings via DHCP are shown below.
- The HostName option (option code 12) can be added to the Discover/Request message.
- The lease time requested from the DHCP server is fixed at 72 hours. (The actual lease time will depend on the setting of the DHCP server.)
- If the no ip addresscommand is executed with automatic settings, a release message for the IPv4 address obtained is sent to the DHCP server.
- The information obtained from the DHCP server can be checked using the show dhcp lease.
- An IPv4 address can be set for up to eight VLAN interfaces.
The IPv4 address that is allocated to a VLAN interface can be checked using the show ip interface command.
- In the initial state, 192.168.100.240/24 is fixed for the default VLAN (VLAN #1).
3.2 Auto IP function
As part of the IPv4 address setting functionality, this product provides an auto IP function which automatically generates IPv4 link local addresses based on the MAC address.
The auto IP function only works when an IPv4 address has not been allocated from the DHCP server. (The IPv4 address must be set to “DHCP” as a prerequisite.)
This function confirms whether the automatically-generated IPv4 link local address does not already exist on the network via ARP.
If it has been confirmed that the address does not already exist, the generated address will start to be used.
If the IPv4 address was allocated from the DHCP server after the IPv4 link local address was determined via auto IP, the IPv4 link local address is discarded, and the IP address obtained from the DHCP server is used.
- To enable the Auto IP function, use the auto-ip enable command.
- The Auto IP function can be enabled for only one VLAN interface. In the initial state, the default VLAN (VLAN #1) is enabled.
3.3 Route information settings
This product refers to a routing table when sending syslog messages and when sending out voluntary IPv4 packets as a IPv4 host for NTP-based time adjustments and so on.
This product uses the following functions to perform the routing table operations.
- Set VLAN interface route information
- Set default gateway
- Set static route information
- Show route information
3.3.1 VLAN interface route information
When setting an IPv4 address on this product for a VLAN interface, the correspondence between the network address and VLAN ID is automatically set as route information.
When releasing IPv4 addresses set for the VLAN interface, the above settings will be deleted.
3.3.2 Set default gateway
The destination for IPv4 packets sent to network addresses that are not set in the routing table can be set as the default gateway on this product.
- To set the default gateway, use the ip route command.
- To show the default gateway, use the show ip route command.
3.3.3 Set static route information
A static route to the destination network address (the gateway address to which packets will be sent) can be set on this product.
- Static route information is set using the ip route command.
- Static route information is displayed using the show ip route command.
3.3.4 Routing table and route selection
You will use the following two types of table to specify routing information.
- RIB (Routing Information Base: IP routing table)
- FIB (Forwarding Information Base: IP forwarding table)
The roles of each are explained below.
- RIB
RIB (Routing Information Base: IP routing table) is a database that stores various routing information.
- A route is registered in the RIB in the following cases.
- When an IPv4 address is assigned to a VLAN interface
- When a static route or a default gateway are specified manually
- When a default gateway is learned via a DHCP message
- To check the RIB, use the show ip route database command.
- A route is registered in the RIB in the following cases.
- FIB
FIB (Forwarding Information Base: IP forwarding table) is a database that is referenced when deciding how to forward IP packets.
Of the routes that are registered in the RIB, the FIB registers only the route that is determined to be “optimal” and is actually used for forwarding packets.
- The conditions by which a route is determined to be optimal are as follows.
- The corresponding VLAN interface is in the link up state
- If multiple routes to the same destination are registered in the RIB, only one is decided in the following order of priority
- A manually specified route takes priority over a route learned via a DHCP message.
- A route whose gateway has a higher IP address value takes priority
- To check the FIB, use the show ip route command.
- The conditions by which a route is determined to be optimal are as follows.
3.4 ARP table settings
When sending IPv4 packets, this product uses ARP (Address Resolution Protocol) to obtain the MAC addresses from the IPv4 addresses.
The correspondence between IPv4 address and MAC address is saved in the ARP table with the following specifications.
- The ARP entries saved in the ARP table manage the following information.
- IPv4 address
- MAC address
- VLAN interface
- Up to 508 entries are stored in the ARP table, including dynamic and static entries.
- With the default settings, dynamic entries saved in the ARP table are maintained for 1,200 sec.
The entry timeout value can be changed using the arp-ageing-timeout command.
- Dynamic entries saved in the ARP table can be cleared regardless of the timeout value, by using the clear arp-cache command.
- Settings for the static entries in the ARP table are made using the arp command. Up to 255 items can be registered.
- Use the show arp command to check the ARP table.
4 Related Commands
The related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Function types | Operations | Operating commands |
|---|---|---|
| IPv4 address settings | Set IPv4 address | ip address |
| Show IPv4 address | show ip interface | |
| Set dynamic IPv4 address by DHCP client | ip address dhcp | |
| Show DHCP client status | show dhcp lease | |
| Enable/disable Auto IP function | auto-ip enable/disable | |
| Route information settings | Set default gateway | ip route |
| Show default gateway | show ip route | |
| Set static route information | ip route | |
| Show static route information | show ip route | |
| Show route information | show ip route | |
| ARP table settings | Show ARP table | show arp |
| Set timeout for dynamic entries | arp-ageing-timeout | |
| Clear dynamic entries | clear arp-cache | |
| Set static entry | arp |
5 Examples of Command Execution
5.1 Set IPv4 network environment (DHCP)
In this example, the IPv4 addresses are set on this product, and an environment is set up for accessing the unit from a remote terminal.
- Maintenance for this product is done using the default VLAN (VLAN #1).
- The IPv4 address is set automatically by DHCP for the default VLAN (VLAN #1).
- Permit Web/TFTP access from hosts connected to VLAN #1.
- Check the IPv4 address that is currently set.
If the default settings are still in effect, the fixed IPv4 address (192.168.100.240/24) is set.
Yamaha#show ip interface brief Interface IP-Address Status Protocol vlan1 192.168.100.240/24 up up
- Specify DHCP for the default VLAN (VLAN #1).
Yamaha#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Yamaha(config)#interface vlan1 Yamaha(config-if)#ip address dhcp
- Check the information that was provided by the DHCP server.
Yamaha(config-if)#end Yamaha#show dhcp lease Interface vlan1 -------------------------------------------------------------------------------- IP Address: 192.168.1.3 Expires: YYYY/MM/DD 05:08:41 Renew: YYYY/MM/DD 19:08:41 Rebind: YYYY/MM/DD 02:38:41 Server: Options: subnet-mask 255.255.255.0 default-gateway 192.168.1.1 dhcp-lease-time 72000 domain-name-servers 192.168.1.1 dhcp-server-identifier 192.168.1.1 domain-name xxx.xxxxx.xx.xx
- Set the default VLAN (VLAN #1) to permit access from HTTP servers and TFTP servers.
Access using a remote host over the Web after settings are made.
Yamaha(config)#http-server interface vlan1 ... (Permit HTTP server access) Yamaha(config)#tftp-server interface vlan1 ... (Permit TFTP server access)
6 Points of Caution
None
7 Related Documentation
- L2 switching functions: VLAN
- Remote access functions:Remote access control
- SWR2310 Series Technical Data (Basic Functions)
- Layer 3 functions
- IPv6 basic settings
IPv6 basic settings
1 Function Overview
This product is compatible with the following IPv6 network environment settings, mainly for the purpose of maintenance (configuring the settings of the switch).
- IPv6 address settings
- Route information settings
- Neighbor cache table settings
2 Definition of Terms Used
- RA (Router Advertisement)
- This is a system that automatically sets address information and network settings for devices of the network that is associated with a router.
- IPv6 address
- The IPv6 address is 128 bits expressed as hexadecimal. The address is divided into eight fields delimited by “:” with 16 bits in each field.
- 2001:02f8:0000:0000:1111:2222:0000:4444
The expression can be abbreviated according to the following rules.
- If the beginning of a field is a zero, the zero can be omitted.
- A field that consists of four zeros can be abbreviated as a single zero.
- Multiple fields consisting only of consecutive zeros can be abbreviated as “::” in only one location for the entire address.
Applying these rules to the above address, we get the following.
- 2001:2f8::1111:2222:0:4444
- IPv6 link local address
- This is an address that is only valid within the same segment, and is in the following range.
- [Start]FE80:0000:0000:0000:0000:0000:0000:0000
- [End]FE80:0000:0000:0000:FFFF:FFFF:FFFF:FFFF
3 Function Details
3.1 IPv6 address settings
This product lets you specify the IPv6 address and prefix length for a VLAN interface.
As the setting method, both fixed settings and automatic settings via RA (router advertisement) are supported.
- In order to specify an IPv6 address, IPv6 functionality must be enabled for the corresponding VLAN interface.
- To enable IPv6 functionality, use the ipv6 enable command.
- When IPv6 functionality is enabled, an IPv6 link local address is automatically assigned.
- To set a fixed/automatic IPv6 address, use the ip address command.
- An IPv6 address can be set for up to eight VLAN interfaces.
The IPv6 address that can be set for one VLAN interface will be either a fixed setting or an automatic setting.
The IPv6 address that is allocated to a VLAN interface can be checked using the show ipv6 interface command.
3.2 Route information settings
This product refers to a routing table when sending syslog messages and when sending out voluntary IPv6 packets as a IPv6 host for NTP-based time adjustments and so on.This product uses the following functions to perform the routing table operations.
- Set VLAN interface route information
- Set default gateway
- Set static route information
- Show route information
3.2.1 VLAN interface route information
When an IPv6 address is specified for a VLAN interface, the correspondence between the network address and the VLAN ID is automatically specified by this product as route information.
When IPv6 addresses set for the VLAN interface are released, the above settings are deleted.
3.2.2 Set default gateway
The destination for IPv6 packets sent to network addresses that are not set in the routing table can be set as the default gateway on this product.
- To set the default gateway, use the ipv6 route command.
- To show the default gateway, use the show ipv6 route command.
3.2.3 Set static route information
A static route to the destination network address (the gateway address to which packets will be sent) can be set on this product.
- Static route information is set using the ipv6 route command.
- Static route information is displayed using the show ipv6 route command.
3.2.4 Routing table and route selection
You will use the following two types of table to specify routing information.
- RIB (Routing Information Base: IP routing table)
- FIB (Forwarding Information Base: IP forwarding table)
The roles of each are explained below.
- RIB
RIB (Routing Information Base: IP routing table) is a database that stores various routing information.
- A route is registered in the RIB in the following cases.
- When an IPv6 address is assigned to a VLAN interface
- When a static route or a default gateway are specified manually
- To check the RIB, use the show ipv6 route database command.
- A route is registered in the RIB in the following cases.
- FIB
FIB (Forwarding Information Base: IP forwarding table) is a database that is referenced when deciding how to forward IP packets.
Of the routes that are registered in the RIB, the FIB registers only the route that is determined to be “optimal” and is actually used for forwarding packets.
- The conditions by which a route is determined to be optimal are as follows.
- The corresponding VLAN interface is in the link up state
- If multiple routes to the same destination are registered in the RIB, only one is decided in the following order of priority
- A route whose gateway has a higher IP address value takes priority
- To check the FIB, use the show ipv6 route command.
- The conditions by which a route is determined to be optimal are as follows.
3.3 Neighbor cache table settings
When sending IPv6 packets, this product uses Neighbor Discovery Protocol to obtain the MAC addresses from the IPv6 addresses.
The correspondence between IPv6 address and MAC address is saved in the neighbor cache table with the following specifications.
- The neighbor cache entries saved in the neighbor cache table manage the following information.
- IPv6 address
- MAC address
- VLAN interface
- Up to 127 entries are stored in the neighbor cache table, including dynamic and static entries.
- Dynamic entries saved in the neighbor cache table can be cleared by using the clear ivp6 neighbors command.
- Settings for the static entries in the neighbor cache table are made using the ipv6 neighbor command. Up to 63 items can be registered.
- Use the show ipv6 neighbor command to check the neighbor cache table.
4 Related Commands
The related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Function types | Operations | Operating commands |
|---|---|---|
| IPv6 address settings | Enable/disable IPv6 addresses | ipv6 enable/disable |
| Set IPv6 address | ipv6 address | |
| Show IPv6 address | show ipv6 interface | |
| Set RA setting for IPv6 address | ipv6 address autoconfig | |
| Route information settings | Set default gateway | ipv6 route |
| Show default gateway | show ipv6 route | |
| Set static route information | ipv6 route | |
| Show static route information | show ipv6 route | |
| Show route information | show ipv6 route | |
| Neighbor cache settings | Set static neighbor cache entry | ipv6 neighbors |
| Show neighbor cache table | show ipv6 neighbors | |
| Clear neighbor cache table | clear ipv6 neighbors |
5 Examples of Command Execution
5.1 Setting up a IPv6 network environment (fixed settings)
In this example, the IPv6 addresses are manually set on this product, and an environment is set up for accessing the unit from a remote terminal.
- Maintenance for this product is done using the default VLAN (VLAN #1).
- The IPv6 address is set manually for the default VLAN (VLAN #1).
- Permit Web/TFTP access from hosts connected to VLAN #1.
- This sets 2001:db8:1::2/64 for the default VLAN (VLAN #1).
Yamaha#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Yamaha(config)#interface vlan1 Yamaha(config-if)#ipv6 enable ... (Enable IPv6) Yamaha(config-if)#ipv6 address 2001:db8:1::2/64 ... (Set IPv6 address)
- Check the IPv6 address that was set.
Yamaha(config-if)#end Yamaha#show ipv6 interface brief Interface IP-Address Status Protocol vlan1 2001:db8:1::2/64 up up fe80::2a0:deff:fe:2/64 - Set the default VLAN (VLAN #1) to permit access from HTTP servers and TFTP servers.
Access using a remote host over the Web after settings are made.
Yamaha(config)#http-server interface vlan1 ... (Permit HTTP server access) Yamaha(config)#tftp-server interface vlan1 ... (Permit TFTP server access)
5.2 Setting up a IPv6 network environment (automatic settings using RA)
In this example, the IPv6 addresses are automatically set on this product, and an environment is set up for accessing the unit from a remote terminal.
- Maintenance for this product is done using the default VLAN (VLAN #1).
- The IPv6 address is set automatically by RA for the default VLAN (VLAN #1).
- Permit Web/TFTP access from hosts connected to VLAN #1.
- Specify RA for the default VLAN (VLAN #1).
Yamaha#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Yamaha(config)#interface vlan1 Yamaha(config-if)#ipv6 enable ... (Enable IPv6) Yamaha(config-if)#ipv6 address autoconfig ... (Set RA)
- Check the IPv6 address that was obtained from RA.
Yamaha(config-if)#end Yamaha#show ipv6 interface brief Interface IP-Address Status Protocol vlan1 2001:db8::2a0:deff:fe:2/64 up up fe80::2a0:deff:fe:2/64 - Set the default VLAN (VLAN #1) to permit access from HTTP servers and TFTP servers.
Access using a remote host over the Web after settings are made.
Yamaha(config)#http-server interface vlan1 ... (Permit HTTP server access) Yamaha(config)#tftp-server interface vlan1 ... (Permit TFTP server access)
6 Points of Caution
None
7 Related Documentation
- L2 switching functions: VLAN
- Remote access functions:Remote access control
Static routing
1 Function Overview
In this product, static routing (static route information) can be used for route control in IP networks.
An administrator can explicitly register route information by entering a command.
You can set both static routes for IPv4 networks and static routes for IPv6 networks.
There are the following two types of static route information.
| Type | Description |
|---|---|
| VLAN interface route information | Route information automatically registered by setting the IP address using the ip/ipv6 address command |
| Static route information | Route information registered by route setting by ip/ipv6 route command |
Use the show ip/ipv6 route command to display the routing table.
2 Definition of Terms Used
None
3 Function Details
3.1 VLAN interface route information
Route information that is automatically registered by setting the IP address using the ip/ipv6 address command.
It is the route information of the network directly connected to this product and is associated with the interface.
Set 192.168.100.1/24 as the IP address for the VLAN1 interface and display the routing table.
Yamaha(config)# interface vlan1
Yamaha(config-if)# ip address 192.168.100.1/24
Yamaha(config-if)# exit
Yamaha(config)# exit
Yamaha#show ip route
Codes: C - connected, S - static
* - candidate default
C 192.168.100.0/24 is directly connected, vlan1
Gateway of last resort is not set
3.2 Static route information
Route information registered by route setting by ip/ipv6 route command.
You can statically set a route to a specific network or set a default gateway.
When setting the default gateway, specify 0.0.0.0/0 as the destination network.
Up to 128 IPv4 static routes with the ip route command can be set.
Up to 32 IPv6 static routes with the ipv6 route command can be set.
Set the gateway for the route addressed to 172.16.0.0/16 to 192.168.100.254 and display the routing table.
Yamaha(config)# ip route 172.16.0.0/24 192.168.100.254
Yamaha(config)# exit
Yamaha# show ip route
Codes: C - connected, S - static
* - candidate default
S 172.16.0.0/24 [1/0] via 192.168.100.254, vlan1
C 192.168.100.0/24 is directly connected, vlan1
Gateway of last resort is not set
Set 192.168.100.200 as the default gateway and display the routing table.
Yamaha(config)# ip route 0.0.0.0/0 192.168.100.200
Yamaha(config)# exit
Yamaha# show ip route
Codes: C - connected, S - static
* - candidate default
Gateway of last resort is 192.168.100.200 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 192.168.100.200, vlan1
S 172.16.0.0/24 [1/0] via 192.168.100.254, vlan1
C 192.168.100.0/24 is directly connected, vlan1
3.3 Display of routing table
There are two routing tables: an IP forwarding table (FIB) in which only route information actually used for packet forwarding is registered, and an IP routing table (RIB) in which all route information is registered.
All VLAN interface route information and static route information are registered in the IP routing table. Within this, only the route information that is actually used in the packet forwarding process is registered in the IP forwarding table.
Use the show ip/ipv6 route command to display the IP forwarding table and the IP routing table.
In the routing table, VLAN interface route information and static route information are displayed as follows.
| Type | Display |
|---|---|
| VLAN interface route information | C - connected |
| Static route information | S - static |
If no option is specified for show ip/ipv6 route, the IP forwarding table is displayed.
You can display the IP routing table by specifying the database option with show ip/ipv6 route.
You can also display summary information and specific route information only by specifying other options.
| Option | Description |
|---|---|
| IP address | Display route information used when forwarding packets to the specified IP address. |
| IP address and prefix | Display route information that matches the specified information. |
| database | Display all configured route information (IP routing table). |
| summary | Display IP routing table summary information |
For details on how to use the show ip route command, see the command reference.
3.4 Route information priority (management distance)
Route information has a priority commonly called Administrative Distance.
This is used to determine which is prioritized when route information to the same destination is registered with VLAN interface route information and static route information.
The priority of route information can be applied not only to static routing but also to dynamic routing.
The priority of static routing route information can be specified in the range of 1 to 255 using the option at the end of the ip route command.
The smaller the value, the higher the priority. In the initial state, the priority is as follows.
| Type | Initial priority | How to change priority |
|---|---|---|
| VLAN interface route information | None (overrides any other route information) | Settings cannot be changed. |
| Static route information | 1 | It can be specified in the range of 1 to 255 by the option at the end of the ip/ipv6 route command. |
3.5 Enabling the routing function
Use the ip/ipv6 forwarding command to enable/disable the routing function.
In the initial state, the routing function is disabled for both IPv4 and IPv6.
4 Related Commands
Related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Function types | Operations | Operating commands |
|---|---|---|
| Route information settings | Set static route information | ip route / ipv6 route |
| Show static route information | show ip route / show ipv6 route | |
| Show route information | show ip route / show ipv6 route | |
| Routing function settings | Routing function settings | ip forwarding / ipv6 forwarding |
| Routing function status display | show ip forwarding / show ipv6 forwarding |
5 Points of Caution
None
6 Related Documentation
None
- SWR2310 Series Technical Data (Basic Functions)
- IP multicast functions
IGMP Snooping
1 Function Overview
IGMP snooping is a function to suppress consumption of network bandwidth in a VLAN environment, by controlling any surplus multicast flooding.
On an L2 switch, since multicast packets are distributed per VLAN, if there is even one device in the VLAN that wants to receive the multicast packet, the packet will be distributed to all ports within the same VLAN.
Operations during multicast distribution (no IGMP snooping)

When using the IGMP snooping function, the IGMP messages exchanged between the receiving device and the multicast router are monitored (snooped), the packet from the relevant group will only be distributed to the port, to which the device that wants to receive the multicast packet is connected.
Operations during multicast distribution (using IGMP snooping)
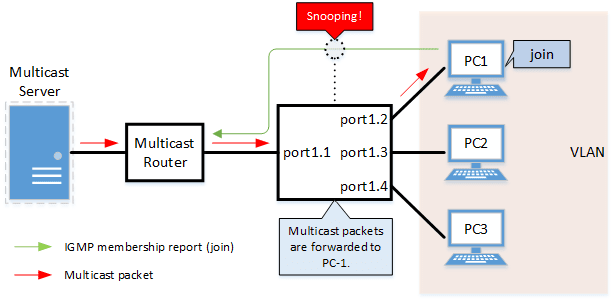
2 Definition of Terms Used
- IGMP (Internet Group Management Protocol)
This is a protocol to control multicast groups.
The multicast router can determine which hosts on the LAN are members of the multicast network, and the hosts can communicate which multicast group they belong to.
There are three protocol versions, respectively defined by IGMPv1 (RFC1112), IGMPv2 (RFC2236), and IGMPv3 (RFC3376).
- Multicast router port
This is the LAN/SFP port to which the multicast router is connected.
The LAN/SFP port that receives the IGMP general query is automatically acquired as the multicast router port.
- IGMP report control function
This is a function where the switch controls the data transmission load between the multicast router and the hosts.
The messages gathered by this product to perform control are shown below.
- IGMP reports replied to IGMP general queries by hosts, sent from the multicast router
- IGMP leave messages notified by the host
The report control function works with IGMPv1/v2/v3.
- IGMPv2 Fast Leave function
This function allows for the LAN/SFP port that received a IGMP leave message to immediately stop receiving multicasts (deleting the necessary FDB entry).
Previously, when an IGMP leave message was received in the course of IGMPv2 leave processing, a group-specific query was sent to that port to check for the existence of a receiver, but if the fast leave function is enabled, this operation is not performed.
For this reason, the fast leave function is effective only when there is a single receiver under the control of the LAN/SFP port.
The fast leave function operates only when an IGMPv2 leave message is received.
- IGMP query transmission function (IGMP Querier)
This is a function to send IGMP general and specific queries.
It is used to make IGMP snooping function in an environment without a multicast router.
3 Function Details
The operating specifications for IGMP snooping are shown below.
- This product offers snooping functions compatible with IGMP v1/v2/v3.
You can use the ip igmp snooping version command to make later versions operate on this product.
Version settings are made for the VLAN interface, and initial settings are for v3.
The difference in operations between the configured version and received frame versions are shown in the table below.
- If an IGMP query whose version is higher than the settings is received, the configured version will be lowered, and the query will be forwarded.
- If an IGMP report whose version is higher than the specified version is received, the relevant report will be discarded without being forwarded.
- If an IGMP query and report of a lower version than the specified version is received, it is forwarded unmodified as the received version.
- The settings to enable/disable IGMP snooping are made for the VLAN interface.
The initial setting for the default VLAN (VLAN #1) and the initial setting after a VLAN is generated are both enabled.
- The IGMP snooping function can handle the following four operations.
- Multicast router port setting
- IGMP report control
- IGMPv2 Fast-leave
- IGMP query transmission
- Although the multicast router port is automatically acquired on VLAN interfaces where IGMP snooping is set to “enable”, the *ip igmp snooping mrouter interface* command can also be used to make static settings.
The show ip igmp snooping mrouter command is used to check multicast router ports that are set for the VLAN interface.
- The IGMP report control function is automatically enabled on VLAN interfaces for which IGMP snooping has been set to “enable”.
The IGMP report control function cannot be disabled.
When transmitting an IGMP report or IGMP leave message using the report control function, the IPv4 address allocated to the VLAN interface will be used for the source IPv4 address.
(The address will be set and transmitted as “0.0.0.0” if it has not been allocated.)
- The IGMPv2 fast-leave function is set for the VLAN interface using the ip igmp snooping fast-leave command.
The initial setting for the default VLAN (VLAN #1) and the initial setting after a VLAN is generated are both disabled.
- The IGMP query transmission function is supported in order to allow use of IGMP snooping in environments that do not have a multicast router.
The IGMP query transmission function controls the following two parameters.
- IGMP query transmission function Enable/disable
- The ip igmp snooping querier command is used for VLAN interfaces.
- The initial setting for the default VLAN (VLAN #1) and the initial setting after a VLAN is generated are both disabled.
- IGMP query transmission interval
- This is executed using the ip igmp snooping query-interval command.
- The transmission interval can be set from 20–18,000 sec., and the default value is 125 sec.
- IGMP query transmission function Enable/disable
- When multiple devices transmit queries within a VLAN, the query is sent by the device with the lowest IPv4 address within the VLAN.
When this product receives a query from a device whose IPv4 address is lower than its own, the query transmission function will be halted.
The source iPv4 address that is set when a query is transmitted uses the IPv4 address allocated to the VLAN interface. If an IPv4 address has not been allocated, an IPv4 address allocated to a different VLAN interface is used instead.
(If no IPv4 addresses have been allocated to any VLAN interfaces, the address will be set and transmitted as “0.0.0.0”.)
- This product features a function that forces the TTL value of a received IGMP packet to change to “1” if the TTL value is invalid (a value other than “1”), instead of discarding the packet.
This is defined as the “TTL check function”, and it can be configured for a VLAN interface by using the ip igmp snooping check ttl command.
The TTL check function is enabled (discard packets with an invalid TTL value) both for the initial setting of the default VLAN (VLAN #1) and for the initial setting after a VLAN is generated.
4 Related Commands
The related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Enable/disable IGMP snooping | ip igmp snooping |
| Set IGMP snooping fast-leave | ip igmp snooping fast-leave |
| Set multicast router port | ip igmp snooping mrouter interface |
| Set query transmission function | ip igmp snooping querier |
| Set IGMP query transmission interval | ip igmp snooping query-interval |
| Set IGMP snooping TTL check | ip igmp snooping check ttl |
| Set IGMP version | ip igmp snooping version |
| Show multicast router port information | show ip igmp snooping mrouter |
| Show IGMP multicast recipient information | show ip igmp snooping groups |
| Show an interface’s IGMP-related information | show ip igmp snooping interface |
| Clear IGMP group membership entries | clear ip igmp snooping |
5 Examples of Command Execution
5.1 IGMP snooping settings (with multicast router)
In an environment with a multicast router, enable the IGMP snooping function and join a multicast group.
Data is distributed only to PC1 and PC3.
IGMP snooping setting example (with multicast router)
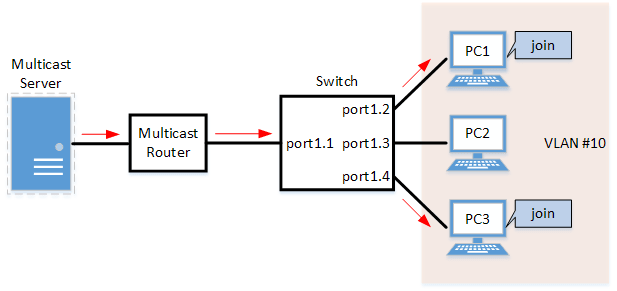
- LAN ports #1–#4 are set as access ports, and associated with VLAN #10.
- Since there is a multicast router, the IGMP query transmission function is left as “disabled”.
- Multicast router port acquisition is set to automatic acquisition only. (A static setting is not used.)
- The IGMPv2 fast-leave function is enabled.
- Define VLAN #10, and set IGMP snooping.
Yamaha(config)# vlan database Yamaha(config-vlan)#vlan 10 ... (VLAN #10 definition) Yamaha(config-vlan)#exit Yamaha(config)#interface vlan10 Yamaha(config-if)#ip igmp snooping ... (Enable IGMP Snooping for VLAN #10) Yamaha(config-if)#no ip igmp snooping querier ... (Disable IGMP query transmission function for VLAN #10) Yamaha(config-if)#ip igmp snooping fast-leave ... (Enable IGMP Fast-leave function for VLAN #10)
- By default, IGMP snooping is enabled and IGMP query transmission is disabled, so there is no need to set them.
- Set LAN ports #1–#4 as access ports, and associate them with VLAN #10.
Yamaha(config)# interface port1.1 Yamaha(config-if)# switchport mode access Yamaha(config-if)# switchport access vlan 10 (Also perform the above settings for LAN ports #2-#4.)
- Confirm the multicast router port information. (It should be connected to LAN port #1.)
Yamaha#show ip igmp snooping mrouter vlan10 VLAN Interface IP-address Expires 10 port1.1(dynamic) 192.168.100.216 00:00:49
- Confirm the information for the multicast recipient.
Yamaha#show ip igmp snooping groups IGMP Snooping Group Membership Group source list: (R - Remote, S - Static) Vlan Group/Source Address Interface Flags Uptime Expires Last Reporter Version 10 239.0.0.1 port1.2 R 00:00:13 00:00:41 192.168.100.2 V3 10 239.0.0.1 port1.4 R 00:00:02 00:00:48 192.168.100.4 V3
5.2 IGMP snooping settings (without multicast router)
In an environment without a multicast router, enable the IGMP snooping function and join a multicast group.
Data is distributed only to PC1 and PC3.
IGMP snooping settings (without multicast router)
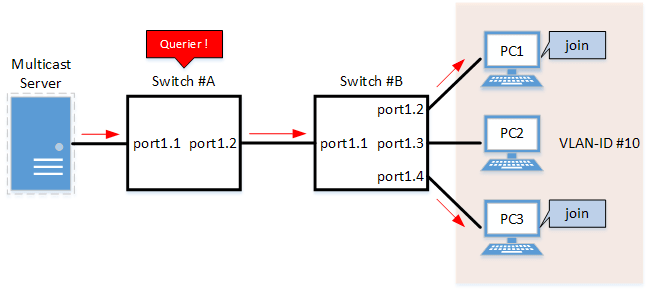
- Switch #A
- LAN ports #1–#2 are set as access ports, and associated with VLAN #10.
- The IGMP query transmission function is enabled.
The IGMP query transmission interval is set to 20 sec.
- Switch #B
- LAN ports #1–#4 are set as access ports, and associated with VLAN #10.
- Multicast router port acquisition is set to automatic acquisition only. (A static setting is not used.)
- The IGMPv2 Fast-Leave function is enabled.
- Since there is a device that sets invalid TTL values in IGMP packets, disable the TTL check function.
- [Switch #A] Define VLAN #10, and set IGMP snooping.
Yamaha(config)# vlan database Yamaha(config-vlan)#vlan 10 ... (VLAN #10 definition) Yamaha(config-vlan)#exit Yamaha(config)#interface vlan10 Yamaha(config-if)#ip igmp snooping ... (Enable IGMP Snooping for VLAN #10) Yamaha(config-if)#ip igmp snooping querier ... (Enable IGMP query transmission function for VLAN #10) Yamaha(config-if)#ip igmp snooping query-interval 20 ... (Set 20 seconds as the IGMP query transmission interval for VLAN #10)
- Since IGMP snooping is enabled by default, we do not need to set this specifically.
- [Switch #A] Set LAN ports #1–#2 as access ports, and associate them with VLAN #10.
Yamaha(config)# interface port1.1 Yamaha(config-if)# switchport mode access Yamaha(config-if)# switchport access vlan 10 (Also perform the above settings for LAN port #2.)
- [Switch #B] Define VLAN #10, and set IGMP snooping.
Yamaha(config)# vlan database Yamaha(config-vlan)#vlan 10 ... (VLAN #10 definition) Yamaha(config-vlan)#exit Yamaha(config)#interface vlan10 Yamaha(config-if)#ip igmp snooping ... (Enable IGMP Snooping for VLAN #10) Yamaha(config-if)#no ip igmp snooping querier ... (Disable IGMP query transmission function for VLAN #10) Yamaha(config-if)#no ip igmp snooping check ttl ... (Disable TTL check function for VLAN #10) Yamaha(config-if)#ip igmp snooping fast-leave ... (Enable IGMP Fast-leave function for VLAN #10)
- By default, IGMP snooping is enabled and IGMP query transmission is disabled, so there is no need to set them.
- [Switch #B] Set LAN ports #1–#4 as access ports, and associate them with VLAN #10.
Yamaha(config)# interface port1.1 Yamaha(config-if)# switchport mode access Yamaha(config-if)# switchport access vlan 10 (Also perform the above settings for LAN ports #2-#4.)
- [Switch #B] Confirm the information for the multicast recipient. (It should be connected to LAN port #1.)
Yamaha#show ip igmp snooping mrouter vlan10 VLAN Interface IP-address Expires 10 port1.1(dynamic) 192.168.100.216 00:00:49
- [Switch #B] Confirm the information for the multicast recipient.
Yamaha#show ip igmp snooping groups IGMP Snooping Group Membership Group source list: (R - Remote, S - Static) Vlan Group/Source Address Interface Flags Uptime Expires Last Reporter Version 10 239.0.0.1 port1.2 R 00:00:13 00:00:41 192.168.100.2 V3 10 239.0.0.1 port1.4 R 00:00:02 00:00:48 192.168.100.4 V3
6 Points of Caution
If you want to change the handling of unknown multicast frames, use the l2-unknown-mcast command.
7 Related Documentation
- L2 switching functions: VLAN
MLD Snooping
1 Function Overview
MLD snooping is a function to suppress consumption of network bandwidth in an IPv6 VLAN environment, by controlling any surplus multicast flooding.
On an L2 switch, since multicast packets are distributed per VLAN, if there is even one device in the VLAN that wants to receive the multicast packet, the packet will be distributed to all ports within the same VLAN.
Operations during multicast distribution (no MLD snooping)

When using the MLD snooping function, the MLD messages exchanged between the receiving device and the multicast router are monitored (snooped), and the packet from the relevant group will only be distributed to the port, to which the device that wants to receive the multicast packet is connected.
Operations during multicast distribution (using MLD snooping)
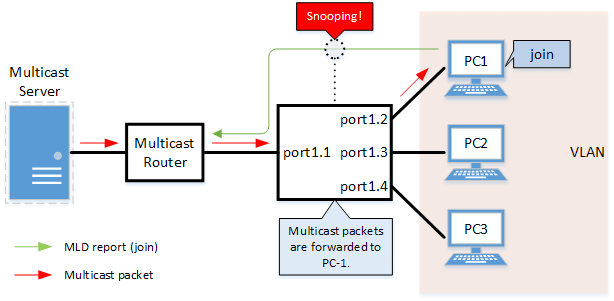
2 Definition of Terms Used
- MLD (Multicast Listener Discovery)
This is a protocol to control multicast groups using IPv6 (a sub-protocol of ICMPv6).
The multicast router can determine which hosts on the LAN are members of the multicast network, and the hosts can communicate which multicast group they belong to.
There are two protocol versions, respectively defined by , MLDv1 (RFC2710), and MLDv2 (RFC3810).
- Multicast router port
This is the LAN/SFP port to which the multicast router is connected.
The LAN/SFP port that receives the MLD general query is automatically acquired as the multicast router port.
- MLD report control function
This is a function where the L2 switch controls the data transmission load between the multicast router and the hosts.
The messages gathered by this product to perform control are shown below.
- MLD reports replied to MLD general queries by hosts, sent from the multicast router
- MLD Done messages notified by the host and MLD reports (Leave)
The report control function works with MLDv1/v2.
- MLD Fast Leave function
This function allows for the LAN/SFP port that received an MLDv1 Done and an MLDv2 report (Leave) to immediately stop receiving multicasts (deleting the necessary FDB entry).
Previously, when an MLDv1 Done message and an MLDv2 report (Leave) was received in the course of MLD leave processing, a group-specific query was sent to check for the existence of a receiver; but if the fast-leave function is enabled, this operation is not performed.
For this reason, the fast leave function is effective only when there is a single receiver under the control of the LAN/SFP port.
- MLD query transmission function (MLD Querier)
This is a function to send MLD general and specific queries.
It is used to make the MLD snooping function in an environment without a multicast router.
3 Function Details
The operating specifications for MLD snooping are shown below.
- This product offers snooping functions compatible with MLDv1/v2.
You can use the mld snooping version command to make later versions work on this product.
Version settings are made for the VLAN interface, and initial settings are for v2.
The difference in operations between the configured version and received frame versions are shown in the table below.- If an MLD query whose version is higher than the settings is received, the version will be lowered to the version that was configured, and the query will be forwarded.
- If an MLD report whose version is higher than the configured version is received, the relevant report will be discarded without being forwarded.
- The settings to enable/disable MLD snooping are made for the VLAN interface.
The initial setting for the default VLAN (VLAN #1) and the initial setting after a VLAN is generated are both enabled.
- The MLD snooping function can handle the following four operations.
- Multicast router port setting
- MLD report control
- MLD fast leave
- MLD query transmission
- Although the multicast router port is automatically acquired on VLAN interfaces where MLD snooping is set to "enable”, the mld snooping mrouter interface command can also be used to make static settings.
The show mld snooping mrouter command is used to check multicast router ports that are set for the VLAN interface.
- The MLD report control function is automatically enabled on VLAN interfaces for which MLD snooping has been set to “enable”.
The MLD report control function cannot be disabled.
When transmitting an MLD report or MLD Done message using the report control function, the IPv6 link local address allocated to the VLAN interface will be used for the source IPv6 address.
(The address will be set and transmitted as “::” if it has not been allocated.)
- The MLD fast-leave function is set for the VLAN interface using the mld snooping fast-leave command.
The initial setting for the default VLAN (VLAN #1) and the initial setting after a VLAN is generated are both disabled.
- The MLD query transmission function is supported in order to allow use of MLD snooping in environments that do not have a multicast router.
The MLD query transmission function controls the following two parameters.- MLD query transmission function enable/disable
- The mld snooping querier command is used for VLAN interfaces.
- The initial setting for the default VLAN (VLAN #1) and the initial setting after a VLAN is generated are both disabled.
- MLD query transmission interval
- This is set using the mld snooping query-interval command.
- The transmission interval can be set from 20–18,000 sec., and the default value is 125 sec.
- MLD query transmission function enable/disable
- When multiple devices transmit queries within a VLAN, the query is sent by the device with the lowest IPv6 address within the VLAN.
When this product receives a query from a device whose IPv6 address is lower than its own, the query transmission function will be halted.
The source iPv6 address that is set when a query is transmitted uses the IPv6 link local address allocated to the VLAN interface. If an IPv6 link local address has not been allocated, an IPv6 link local address allocated to a different VLAN interface is used instead.
(If no IPv6 link local addresses have been allocated to any VLAN interfaces, the query is not transmitted.)
4 Related Commands
Related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Enable/disable MLD snooping | ipv6 mld snooping |
| Set MLD snooping fast-leave | ipv6 mld snooping fast-leave |
| Set the multicast router port | ipv6 mld snooping mrouter interface |
| Set query transmission function | ipv6 mld snooping querier |
| Set the MLD query transmission interval | ipv6 mld snooping query-interval |
| Set the MLD version | ipv6 mld snooping version |
| Show multicast router port information | show ipv6 mld snooping mrouter |
| Show MLD multicast recipient information | show ipv6 mld snooping groups |
| Show an interface’s MLD-related information | show ipv6 mld snooping interface |
| Clear the MLD group membership entries | clear ipv6 mld snooping |
5 Examples of Command Execution
5.1 MLD snooping settings (with multicast router)
In an environment with a multicast router, this enables the MLD snooping function, and data is distributed only to PC1 and PC3 which are joined to a multicast group.
MLD snooping setting example (with multicast router)
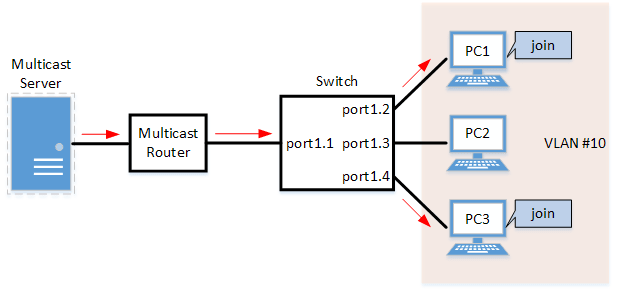
- LAN ports #1–#4 are set as access ports, and associated with VLAN #10.
- Since there is a multicast router, the MLD query transmission function is left as “disabled”.
- Multicast router port acquisition is set to automatic acquisition only. (A static setting is not used.)
- The MLD fast-leave function is enabled.
- Define VLAN #10, and set MLD snooping.
Yamaha(config)# vlan database Yamaha(config-vlan)#vlan 10 ... (definition of VLAN #10) Yamaha(config-vlan)#exit Yamaha(config)#interface vlan10 Yamaha(config-if)#ipv6 enable ... (enables IPv6 functionality on VLAN #10) Yamaha(config-if)#ipv6 mld snooping ... (enables MLD Snooping on VLAN #10) Yamaha(config-if)#no ipv6 mld snooping querier ... (disables the MLD query transmission function on VLAN #10) Yamaha(config-if)#ipv6 mld snooping fast-leave ... (enables the MLD Fast-leave function on VLAN #10)
- By default, MLD snooping is enabled and MLD query transmission is disabled, so there is no need to set them.
- Set LAN ports #1–#4 as access ports, and associate them with VLAN #10.
Yamaha(config)# interface port1.1 Yamaha(config-if)# switchport mode access Yamaha(config-if)# switchport access vlan 10 (the settings above are also applied to LAN ports #2–#4)
- Confirm the multicast router port information. (It should be connected to LAN port #1.)
Yamaha#show ipv6 mld snooping mrouter vlan10 VLAN Interface IP-address Expires 10 port1.1(dynamic) fe80::2a0:deff:feae:b879 00:00:43
- Confirm the information for the multicast recipient.
Yamaha#show ipv6 mld snooping groups MLD Connected Group Membership Vlan Group Address Interface Uptime Expires Last Reporter 10 ff15::1 port1.2 00:00:13 00:00:41 fe80::a00:27ff:fe8b:87e2 10 ff15::1 port1.4 00:00:02 00:00:48 fe80::a00:27ff:fe8b:87e4
5.2 MLD snooping settings (without multicast router)
In an environment without a multicast router, this enables the MLD snooping function, and data is distributed only to PC1 and PC3 which are joined to a multicast group.
MLD snooping settings (without multicast router)
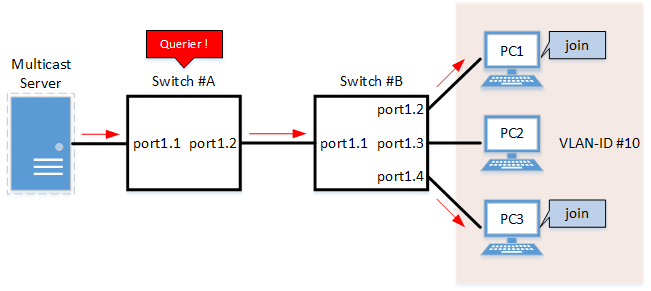
- Switch #A
- LAN ports #1–#2 are set as access ports, and associated with VLAN #10.
- The MLD query transmission function is enabled.
The MLD query transmission interval is set to 20 sec.
- Switch #B
- LAN ports #1–#4 are set as access ports, and associated with VLAN #10.
- Multicast router port acquisition is set to automatic acquisition only. (A static setting is not used.)
- The MLD fast-leave function is enabled.
- [Switch #A] Define VLAN #10, and set MLD snooping.
Yamaha(config)# vlan database Yamaha(config-vlan)#vlan 10 ... (definition of VLAN #10) Yamaha(config-vlan)#exit Yamaha(config)#interface vlan10 Yamaha(config-if)#ipv6 enable ... (enables IPv6 functionality on VLAN #10) Yamaha(config-if)#ipv6 mld snooping ... (enables MLD Snooping on VLAN #10) Yamaha(config-if)#ipv6 mld snooping querier ... (enables the MLD query transmission function on VLAN #10) Yamaha(config-if)#ipv6 mld snooping query-interval 20 ... (sets the MLD query transmission interval to 20 sec. on VLAN #10)
- Since MLD snooping is enabled by default, we do not need to set this specifically.
- [Switch #A] Set LAN ports #1–#2 as access ports, and associate them with VLAN #10.
Yamaha(config)# interface port1.1 Yamaha(config-if)# switchport mode access Yamaha(config-if)# switchport access vlan 10 (the settings above are also applied to LAN port #2)
- [Switch #B] Define VLAN #10, and set MLD snooping.
Yamaha(config)# vlan database Yamaha(config-vlan)#vlan 10 ... (definition of VLAN #10) Yamaha(config-vlan)#exit Yamaha(config)#interface vlan10 Yamaha(config-if)#ipv6 enable ... (enables IPv6 functionality on VLAN #10) Yamaha(config-if)#ipv6 mld snooping ... (enables MLD Snooping on VLAN #10) Yamaha(config-if)#no ipv6 mld snooping querier ... (disables the MLD query transmission function on VLAN #10) Yamaha(config-if)#ipv6 mld snooping fast-leave ... (enables the MLD Fast-leave function on VLAN #10)
- By default, MLD snooping is enabled and MLD query transmission is disabled, so there is no need to set them.
- [Switch #B] Set LAN ports #1–#4 as access ports, and associate them with VLAN #10.
Yamaha(config)# interface port1.1 Yamaha(config-if)# switchport mode access Yamaha(config-if)# switchport access vlan 10 (the settings above are also applied to LAN ports #2–4)
- [Switch #B] Confirm the information for the multicast recipient. (It should be connected to LAN port #1.)
Yamaha#show ipv6 mld snooping mrouter vlan10 VLAN Interface IP-address Expires 10 port1.1(dynamic) fe80::2a0:deff:feae:b879 00:00:43
- [Switch #B] Confirm the information for the multicast recipient.
Yamaha#show ipv6 mld snooping groups MLD Connected Group Membership Vlan Group Address Interface Uptime Expires Last Reporter 10 ff15::1 port1.2 00:00:13 00:00:41 fe80::a00:27ff:fe8b:87e2 10 ff15::1 port1.4 00:00:02 00:00:48 fe80::a00:27ff:fe8b:87e4
6 Points of Caution
If you want to change the handling of unknown multicast frames, use the l2-unknown-mcast command.
If the stack function is enabled, this will be disabled regardless of the MLD snooping settings.
7 Related Documentation
- Layer 2 functions: VLAN
- Layer 3 functions: IPv6 basic settings
- SWR2310 Series Technical Data (Basic Functions)
- Traffic control functions
ACL
1 Function Overview
The access list (ACL) is a conditional statement that determines whether to permit or to deny the frame.
If the access list is applied to the interface, only the permitted frame will be transferred, and the denied frame will be discarded.
As this allows for only specified frames to be selected for transfer, this feature is primarily used for security purposes.
This product supports three access list types, as shown in the table below.
Access list type
| Access list type | Deciding criteria | Access list ID | Purpose of use |
|---|---|---|---|
| IPv4 access list | Source IPv4 address Destination IPv4 address IP protocol type | 1–2000 | Filters access from specific hosts and networks. Filters specific IP protocol types such as TCP/UDP. |
| IPv6 access list | Source IPv6 address | 3001–4000 | Filters access from specific hosts and networks. |
| MAC access list | Source MAC address Destination MAC address | 2001–3000 | Filters access and data transfer from specific devices. |
2 Definition of Terms Used
- ACL
- Abbreviation of “Access Control List”.
- Wildcard mask
Information that specifies which portion of the specified IPv4 address or MAC address is read. This is used when specifying a range of IPv4 addresses or MAC addresses as ACL conditions.
- When the wildcard mask bit is “0”: check the corresponding bit
- When the wildcard mask bit is “1”: do not check the corresponding bit
Examples of settings using wildcard masks are shown below. (The underlined portion is the wildcard mask.)
- To specify conditions for subnet 192.168.1.0/24: 192.168.1.0 0.0.0.255 (specified as decimal)
- To specify conditions for vendor code 00-A0-DE-*-*-*: 00A0.DE00.0000 0000.00FF.FFFF (specified as hexadecimal)
3 Function Details
3.1 Generating an access list
Access lists for the number of IDs in each access list number can be generated. (Refer to the table in "1 Function Overview”.)
A maximum of 256 control parameters can be registered per list for access lists.
If the registered control conditions are not satisfied, forwarding occurs as usual.
3.2 Applying to the interface
The following table shows how access lists are applied to the input/output interfaces of this product.
Note that one access list can be applied to the IN and OUT respectively for an interface.
- Status of access list application to the interface
Access list type LAN/SFP port VLAN interface Static/LACP logical interface in out in out in out IPv4 access list ✓ ✓(*) ✓ - ✓ - IPv6 access list ✓ ✓ ✓ - ✓ - MAC access list ✓ - ✓ - ✓ - (*) As a limitation, an IPv4 access list that specifies a range of port numbers cannot be applied to the output (out) side of an interface.
The number of access lists that can be applied to the interface depends on the number of control parameters that are registered in the access lists.
On this product, a maximum of 512 control parameters can be registered to the interface.
Applying an access list to the interface will use resources “equivalent to the number of control parameters that are registered in the access list”.
However, control parameters may also be used internally within the system in some cases, and use resources accordingly.
3.3 Settings for the LAN/SFP port and logical interface
The steps for applying an access list to a LAN/SFP port and to a logical interface is shown below.
- Decide on the filtering parameters, and generate the access list.
- Add a name if necessary.
- Check the access list.
- Apply the access list to the LAN/SFP port and logical interface.
- Check the applied access list.
A list of operation commands is given below.
Access list operation commands (when applied to the LAN/SFP port and logical interface)
| Access list type | Generate access list | Check access list | Apply access list | Check the applied access list |
|---|---|---|---|---|
| IPv4 access list | access-list | show access-list | access-group | show access-group |
| IPv6 access list | access-list | show access-list | access-group | show access-group |
| MAC access list | access-list | show access-list | access-group | show access-group |
3.4 VLAN interface settings
The steps for applying access lists to the VLAN interface are shown below.
- Decide on the filtering parameters, and generate the access list.
- Add a name if necessary.
- Check the access list.
- Generate the VLAN access map.
- Set the access list for the VLAN access map.
- Check the VLAN access map.
- Apply the VLAN access map to the VLAN.
- Check the VLAN access map that was applied.
The operations in steps 1 and 2 are the same as those shown in 3.3.
The following is a list of operating commands for steps 3. and following.
VLAN access map operating command
| Access list type | VLAN access map generation | Settings for access list used with VLAN access map | VLAN access map confirmation | VLAN access map application | Confirmation of the applied VLAN access map |
|---|---|---|---|---|---|
| IPv4 access list | vlan access-map | match access-list | show vlan access-map | vlan filter | show vlan filter |
| IPv6 access list | vlan access-map | match access-list | show vlan access-map | vlan filter | show vlan filter |
| MAC access list | vlan access-map | match access-list | show vlan access-map | vlan filter | show vlan filter |
4 Related Commands
The related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Apply IPv4 access list | access-group |
| Generate IPv4 access list | access-list |
| Add comment to IPv4 access list | access-list description |
| Apply IPv4 access list | access-group |
| Generate IPv6 access list | access-list |
| Add comment to IPv6 access list | access-list description |
| Apply IPv6 access list | access-group |
| Generate MAC access list | access-list |
| Add comment to MAC access list | access-list description |
| Apply MAC access list | access-group |
| Show generated access list | show access-list |
| Show access list applied to interface | show access-group |
5 Examples of Command Execution
5.1 IPv4 access list settings
5.1.1 Example of application to a LAN port
■ Specify host
In this example, we will set LAN port #1 to permit access from host:192.168.1.1 to host:10.1.1.1.
The access list ID to be used is #123, and the access list name IPV4-ACL-EX is added.
- Generate and confirm access list #123.
Yamaha(config)#access-list 123 permit any host 192.168.1.1 host 10.1.1.1 ... (Generate access list) Yamaha(config)#access-list 123 deny any any any Yamaha(config)#access-list 123 description IPV4-ACL-EX ... (Assign name to access list) Yamaha(config)#end Yamaha# Yamaha#show access-list 123 ... (Check access list) IPv4 access list 123 10 permit any host 192.168.1.1 host 10.1.1.1 20 deny any any any Yamaha# - Apply access list #123 to LAN port #1.
Yamaha(config)#interface port1.1 Yamaha(config-if)#access-group 123 in ... (Apply access list) Yamaha(config-if)#end Yamaha# Yamaha#show access-group ... (Check access list setting) Interface port1.1 : IPv4 access group 123 in
■ Specify network
In this example, we will set LAN port #1 to permit access from network: 192.168.1.0/24 to host: 10.1.1.1.
The access list ID to be used is #123, and the access list name IPV4-ACL-EX is added.
- Generate and confirm access list #123.
Yamaha(config)#access-list 123 permit any 192.168.1.0 0.0.0.255 host 10.1.1.1 ... (Generate access list) Yamaha(config)#access-list 123 deny any any any Yamaha(config)#access-list 123 description IPV4-ACL-EX ... (Assign name to access list) Yamaha(config)#end Yamaha# Yamaha#show ip access-list ... (Check ACL) IPv4 access list 123 10 permit any 192.168.1.0/24 host 10.1.1.1 20 deny any any any Yamaha# - Apply access list #123 to LAN port #1.
Yamaha(config)#interface port1.1 Yamaha(config-if)#access-group 123 in ... (Apply access list) Yamaha(config-if)#end Yamaha# Yamaha#show access-group ... (Check access list setting) Interface port1.1 : IPv4 access group 123 in
5.1.2 Example of application to the VLAN interface
■ Specify host
In this example, we will set VLAN #1000 to permit access from host:192.168.1.1 to host:10.1.1.1.
We will use access list ID #123.
The VLAN access map to be used will be VAM-002, and access list #123 will be set.
- Generate and confirm access list #123.
Yamaha(config)#access-list 123 permit any host 192.168.1.1 host 10.1.1.1 ... (Generate access list) Yamaha(config)#access-list 123 deny any any any Yamaha(config)#end Yamaha# Yamaha#show access-list 123 ... (Check access list) IPv4 access list 123 10 permit any host 192.168.1.1 host 10.1.1.1 20 deny any any any - Generate VLAN access map VAM-002, and set access list #123.
Yamaha(config)#vlan access-map VAM-002 ... (Generate VLAN access map) Yamaha(config-vlan-access-map)#match access-list 123 ... (Register access list) Yamaha(config-vlan-access-map)#end Yamaha# Yamaha#show vlan access-map ... (Check VLAN access map and access list settings) Vlan access-map VAM-002 match ipv4 access-list 123 - Apply VLAN access map VAM-002 to VLAN #1000, and confirm the status.
Yamaha(config)#vlan filter VAM-002 1000 ... (Apply VLAN access map to VLAN) Yamaha(config)#end Yamaha# Yamaha#show vlan filter ... (Check VLAN access map settings) Vlan filter VAM-002 is applied to vlan 1000
■ Specify network
In this example, we will set VLAN port #1000 to permit access from network:192.168.1.0/24 to host:10.1.1.1.
We will use access list ID #123.
The VLAN access map to be used will be VAM-002, and access list #123 will be set.
- Generate and confirm access list #123.
Yamaha(config)#access-list 123 permit any 192.168.1.0 0.0.0.255 host 10.1.1.1 ... (Generate access list) Yamaha(config)#access-list 123 deny any any any Yamaha(config)#end Yamaha# Yamaha#show access-list 123 ... (Check access list) IPv4 access list 123 10 permit any 192.168.1.0/24 host 10.1.1.1 20 deny any any any - Generate VLAN access map VAM-002, and set access list #123.
Yamaha(config)#vlan access-map VAM-002 ... (Generate VLAN access map) Yamaha(config-vlan-access-map)#match access-list 123 ... (Register access list) Yamaha(config-vlan-access-map)#end Yamaha# Yamaha#show vlan access-map ... (Check VLAN access map and access list settings) Vlan access-map VAM-002 match ipv4 access-list 123 - Apply VLAN access map VAM-002 to VLAN #1000, and confirm the status.
Yamaha(config)#vlan filter VAM-002 1000 ... (Apply VLAN access map to VLAN) Yamaha(config)#end Yamaha# Yamaha#show vlan filter ... (Check VLAN access map settings) Vlan filter VAM-002 is applied to vlan 1000
5.2 IPv6 access list settings
5.2.1 Example of application to a LAN port
■ Specify host
In this example, we will set LAN port #1 to receive frames only from host:2001:db8::1.
The access list ID to be used is #3001, and the access list name is IPV6-ACL-EX.
- Generate and confirm access list #3001.
Yamaha(config)#access-list 3001 permit 2001:db8::1/128 ... (Generate access list) Yamaha(config)#access-list 3001 deny any Yamaha(config)#access-list 3001 description IPV6-ACL-EX ... (Assign name to access list) Yamaha(config)#end Yamaha# show access-list 3001 ... (Check access list) IPv6 access list 3001 10 permit 2001:db8::1/128 20 deny any - Apply access list #3001 to LAN port #1.
Yamaha(config)#interface port1.1 Yamaha(config-if)#access-group 3000 in ... (Apply access list) Yamaha(config-if)#end Yamaha# Yamaha#show access-group ... (Check access list setting) Interface port1.1 : IPv6 access group 3001 in
■ Specify network
In this example, we will set LAN port #1 to receive frames only from network:2001:db8::/64.
The access list ID to be used is #3001, and the access list name is IPV6-ACL-EX.
- Generate and confirm access list #3001.
Yamaha(config)#access-list 3001 permit 2001:db8::/64 ... (Generate access list) Yamaha(config)#access-list 3001 deny any Yamaha(config)#access-list 3001 description IPV6-ACL-EX ... (Assign name to access list) Yamaha(config)#end Yamaha# show access-list 3001 ... (Check access list) IPv6 access list 3001 10 permit 2001:db8::/64 20 deny any - Apply access list #3001 to LAN port #1.
Yamaha(config)#interface port1.1 Yamaha(config-if)#access-group 3001 in ... (Apply access list) Yamaha(config-if)#end Yamaha# Yamaha#show access-group ... (Check access list setting) Interface port1.1 : IPv6 access group 3001 in
5.2.2 Example of application to the VLAN interface
■ Specify host
In this example, we will set VLAN #1000 to receive frames only from host:2001:db8::1.
We will use access list ID #3001.
The VLAN access map to be used will be VAM-001, and access list #3001 will be set.
- Generate and confirm access list #3001.
Yamaha(config)#access-list 3001 permit 2001:db8::1/128 ... (Generate access list) Yamaha(config)#access-list 3001 deny any Yamaha(config)#end Yamaha# Yamaha#show access-list 3001 ... (Check access list) IPv6 access list 3001 10 permit 2001:db8::1/128 20 deny any - Generate VLAN access map VAM-001, and set access list #3001.
Yamaha(config)#vlan access-map VAM-001 ... (Generate VLAN access map) Yamaha(config-vlan-access-map)#match access-list 3001 ... (Set access list) Yamaha(config-vlan-access-map)#end Yamaha# Yamaha#show vlan access-map ... (Check VLAN access map and access list settings) Vlan access-map VAM-001 match ipv6 access-list 3001 - Apply VLAN access map VAM-001 to VLAN #1000, and confirm the status.
Yamaha(config)#vlan filter VAM-001 1000 ... (Apply VLAN access map to VLAN) Yamaha(config)#end Yamaha# Yamaha#show vlan filter ... (Check VLAN access map settings) Vlan filter VAM-001 is applied to vlan 1000
■ Specify network
In this example, we will set VLAN port #1000 to receive frames only from network:2001:db8::/64.
We will use access list ID #3001.
The VLAN access map to be used will be VAM-001, and access list #3001 will be set.
- Generate and confirm access list #2.
Yamaha(config)#access-list 3001 permit 2001:db8::/64 ... (Generate access list) Yamaha(config)#access-list 3001 deny any Yamaha(config)#end Yamaha# Yamaha#show access-list 3001 ... (Check access list) IPv6 access list 3001 10 permit 2001:db8::/64 20 deny any - Generate VLAN access map VAM-001, and set access list #3001.
Yamaha(config)#vlan access-map VAM-001 ... (Generate VLAN access map) Yamaha(config-vlan-access-map)#match access-list 3001 ... (Set access list) Yamaha(config-vlan-access-map)#end Yamaha# Yamaha#show vlan access-map ... (Check VLAN access map and access list settings) Vlan access-map VAM-001 match ipv6 access-list 3001 - Apply VLAN access map VAM-001 to VLAN #1000, and confirm the status.
Yamaha(config)#vlan filter VAM-001 1000 ... (Apply VLAN access map to VLAN) Yamaha(config)#end Yamaha# Yamaha#show vlan filter ... (Check VLAN access map settings) Vlan filter VAM-001 is applied to vlan 1000
5.3 MAC access list settings
5.3.1 Example of application to a LAN port
■ Specify host
In this example, we will set LAN port #1 to discard all frames from host:00-A0-DE-12-34-56, and permit all other frames.
The access list ID to be used is #2001, and the access list name MAC-ACL-EX is added.
- Generate and confirm access list #2001.
Yamaha(config)#access-list 2001 deny host 00a0.de12.3456 any ... (Generate access list) Yamaha(config)#access-list 2001 description MAC-ACL-EX ... (Set name for access list) Yamaha(config)#end Yamaha# Yamaha#show access-list 2001 ... (Check access list) MAC access list 2001 10 deny host 00A0.DE12.3456 any - Apply access list #2001 to LAN port #1.
Yamaha(config)#interface port1.1 Yamaha(config-if)#access-group 2001 in ... (Apply access list) Yamaha(config-if)#end Yamaha# Yamaha#show access-group ... (Check access list setting) Interface port1.1 : MAC access group 2001 in
■ Specify vendor
In this example, we will set LAN port #1 to discard all frames from vendor code:00-A0-DE-*-*-* (00-A0-DE-00-00-00 – 00-A0-DE-FF-FF-FF), and permit all other frames.
The access list ID to be used is #2001, and the access list name MAC-ACL-EX is added.
- Generate and confirm access list #2001.
Yamaha(config)#access-list 2001 deny 00a0.de00.0000 0000.00ff.ffff any ... (Generate access list) Yamaha(config)#access-list 2001 description MAC-ACL-EX ... (Set name for access list) Yamaha(config)#end Yamaha# Yamaha#show access-list 2001 ... (Check access list) MAC access list 2001 10 deny 00A0.DE00.0000 0000.00FF.FFFF any - Apply access list #2001 to LAN port #1.
Yamaha(config)#interface port1.1 Yamaha(config-if)#access-group 2001 in ... (Apply access list) Yamaha(config-if)#end Yamaha# Yamaha#show access-group ... (Check access list setting) Interface port1.1 : MAC access group 2001 in
5.3.2 Example of application to the VLAN interface
■ Specify host
In this example, we will set VLAN #1000 to discard all frames from host:00-A0-DE-12-34-56, and permit all other frames.
We will use access list ID #2001. The access list name will be MAC-ACL-EX.
The VLAN access map to be used will be VAM-003, and access list #2001 will be set.
- Generate and confirm access list #2000.
Yamaha(config)#access-list 2001 deny host 00a0.de12.3456 any ... (Generate access list #2001) Yamaha(config)#access-list 2001 description MAC-ACL-EX ... (Set name for access list) Yamaha(config)#end Yamaha# Yamaha#show access-list ... (Check access list) MAC access list 2001 10 deny host 00A0.DE12.3456 any - Generate VLAN access map VAM-003, and set access list #2001.
Yamaha(config)# vlan access-map VAM-003 ... (Generate VLAN access map) Yamaha(config-vlan-access-map)# match access-list 2001 ... (Register access list) Yamaha(config-vlan-access-map)# end Yamaha# Yamaha#show vlan access-map ... (Check VLAN access map and access list settings) Vlan access-map VAM-003 match mac access-list 2001 - Apply VLAN access map VAM-003 to VLAN #1000, and confirm the status.
Yamaha(config)#vlan filter VAM-003 1000 ... (Apply VLAN access map to VLAN) Yamaha(config)#end Yamaha# Yamaha#show vlan filter ... (Check VLAN access map settings) Vlan filter VAM-003 is applied to vlan 1000
■ Specify vendor
In this example, we will set VLAN #1000 to discard all frames from vendor code:00-A0-DE-*-*-* (00-A0-DE-00-00-00 – 00-A0-DE-FF-FF-FF), and permit all other frames.
We will use access list ID #2001. The access list name will be MAC-ACL-EX.
The VLAN access map to be used will be VAM-003, and access list #2001 will be set.
- Generate and confirm access list #2001.
Yamaha(config)#access-list 2001 deny 00a0.de00.0000 0000.00ff.ffff any ... (Generate access list #2001) Yamaha(config)#access-list 2001 description MAC-ACL-EX ... (Set name for access list) Yamaha(config)#end Yamaha# Yamaha#show access-list 2001 ... (Check access list) MAC access list 2001 10 deny 00A0.DE00.0000 0000.00FF.FFFF any - Generate VLAN access map VAM-003, and set access list #2001.
Yamaha(config)# vlan access-map VAM-003 ... (Generate VLAN access map) Yamaha(config-vlan-access-map)# match access-list 2001 ... (Register access list) Yamaha(config-vlan-access-map)# end Yamaha# Yamaha#show vlan access-map ... (Check VLAN access map and access list settings) Vlan access-map VAM-003 match mac access-list 2001 - Apply VLAN access map VAM-003 to VLAN #1000, and confirm the status.
Yamaha(config)#vlan filter VAM-003 1000 ... (Apply VLAN access map to VLAN) Yamaha(config)#end Yamaha# Yamaha#show vlan filter ... (Check VLAN access map settings) Vlan filter VAM-003 is applied to vlan 1000
6 Points of Caution
- LAN/SFP ports for which an access list is configured for received frames cannot belong to a logical interface.
- Access list settings for received frames on an interface cannot be applied to a LAN/SFP port that belongs to a logical interface. If access list settings exist for the received frame of a LAN/SFP port that belongs to a logical interface in startup config, the settings for the most recent port number will be applied to the logical interface.
- Fragment packets may not be judged correctly. Specifically, if layer 4 information (source port number, destination port number, and various TCP flags) is included in the conditions, since the information is not included in the second and subsequent fragment packets, correct judgment cannot be made. If there is a possibility of processing fragmented packets, do not include Layer 4 information in the conditions.
7 Related Documentation
- L2 switching functions: VLAN
QoS
1 Function Overview
QoS (Quality of Service) is a technology for reserving a specified bandwidth for communications over a network, guaranteeing a fixed speed of communication.
Application data is classified and grouped, and then forwarded by group priority level, referring to the DSCP in the IP header or the CoS in the IEEE802.1Q tag.
2 Definition of Terms Used
- CoS (IEEE 802.1p Class of Service)
This expresses priority as a 3-bit field in the VLAN tag header, with a value from 0–7.
Also called 802.1p user priority.
- IP Precedence
This expresses priority as a 3-bit field in the TOS field of the IP header, with a value from 0–7.
Used to indicate the traffic class of the frame in question, for the device that receives the frame.
- DSCP (Diffserv Code Point)
This expresses priority as a 6-bit field in the TOS field of the IP header, with a value from 0–63.
Since DSCP uses the same TOS field as IP precedence, it is compatible with IP-Precedence.
Used to indicate the traffic class of the frame in question, for the device that receives the frame.
- Default CoS
- This is the CoS value that is assigned to an untagged frame for the purpose of internal processing.
- Transmission queue
- This product has eight transmission queues per port. The transmission queues are numbered from ID 0–7, with larger ID numbers being given higher priority.
- Trust mode
This indicates what will be the basis for deciding (trusting) the transmission queue ID.
The CoS value or DSCP value of the incoming frames can be used to differentiate them, or a priority order specified for each reception port can be applied.
Settings can be configured for each LAN/SFP port and logical interface. Note that the settings for LAN/SFP ports that belong to a logical interface cannot be changed.
The default status (when QoS is enabled) is set to “CoS”.
- Transmission queue ID conversion table
This is a conversion table used when deciding on the transmission queue ID from either the CoS value or the DSCP value.
There are two kinds of transmission queue ID conversion tables, the CoS-transmission queue ID conversion table and the DSCP-transmission queue ID conversion table. Each kind is used with its own trust mode.
Mapping can be freely changed by the user.
- Port priority
This is the priority order assigned for each reception port. If the trust mode is “port priority,” frames received at that port are placed in the transmission queue according to the port’s priority setting.
- Class map
This defines the conditions by which packets are classified into traffic classes.
Packets can be associated and used with policy maps, and QoS processing (pre-marking, transmission queue specification, metering/policing/remarking) per traffic class can be defined.
- Policy map
This is an element for performing a QoS processing series on the reception port. This cannot be used by itself, but rather is associated and used with 1–8 class maps.
When a policy map is applied to a LAN/SFP port and logical interface, traffic is classified per class map that is associated with the policy map for the packets received on the relevant port.
Also, QoS processing (pre-marking, transmission queue specification, metering/policing/remarking) set per traffic class can be performed.
- Policer
This is a group series of metering/policing/remarking settings.
There are two types of policers, an individual policer for metering that targets one traffic class, and a group policer that meters multiple traffic classes by putting them together.
3 Function Details
3.1 Enabling or disabling QoS control
When shipped from the factory, the QoS control of this product is set to disable.
To enable QoS control use the qos enable command. To disable this, use the no qos command.
Most QoS control commands cannot be executed if QoS is not enabled.
The QoS function status can be checked using the show qos command.
In order to enable QoS control, the system’s flow control must be disabled.
3.2 QoS processing flow
The QoS processing flow is shown below.
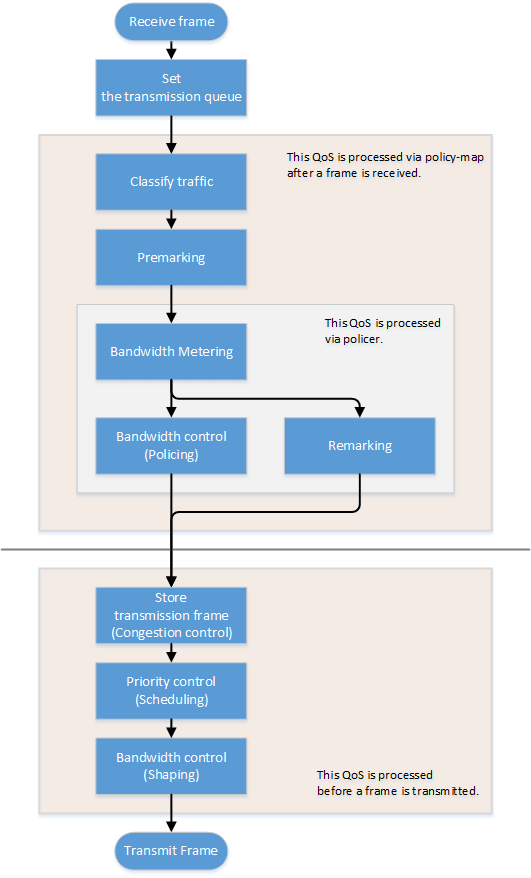
3.3 Transmission queue assignments
When this product receives a frame, it determines the initial value of the transmission queue ID according to the CoS value or DSCP value within the frame and the port priority of the reception port.
Of the factors such as the frame’s CoS value and DSCP value, and the port’s priority order, the port’s trust mode determines which factor will be the basis for determining the transmission queue.
The trust mode can be changed by the qos trust command. The default value (when QoS is enabled) is set to CoS.
The transmission queue is assigned per trust mode, using the following rules.
When trust mode is “CoS”
- When the received frame is a frame with a VLAN tag, the CoS value within the tag is used to determine the transmission queue ID.
- When the received frame is a frame without a VLAN tag, the default CoS that is managed by this product is used to determine the transmission queue ID.
The default setting (when QoS is enabled) and the default CoS are set to “0”. This can be changed using the qos cos command.
- Conversion from the CoS value to the transmission queue ID is performed by the CoS-transmission queue ID conversion table.
One such table is maintained by the system, and with the default settings (when QoS is enabled), the settings are as follows. The setting can be changed using the qos cos-queue command.
CoS value Transmission queue ID Traffic Type 0 2 Best Effort 1 0 Background 2 1 Standard(spare) 3 3 Excellent Effort(Business Critical) 4 4 Controlled Load(Streaming Multimedia) 5 5 Video(Interactive Media) less than 100 msec latency and jitter 6 6 Voice(Interactive Media) less than 10 msec latency and jitter 7 7 Network Control(Reserved Traffic)
When trust mode is “DSCP”
- The DSCP in the IP header is used to determine the transmission queue ID.
- Conversion from the DSCP value to the transmission queue ID is performed by the DSCP-transmission queue ID conversion table.
One such table is maintained by the system, and with the default settings (when QoS is enabled), the settings are as follows. The setting can be changed using the qos dscp-queue command.
DSCP value Transmission queue ID Traffic Type 0 - 7 2 Best Effort 8 -15 0 Background 16 - 23 1 Standard(spare) 24 - 31 3 Excellent Effort(Business Critical) 32 - 39 4 Controlled Load(Streaming Multimedia) 40 - 47 5 Video(Interactive Media) less than 100 msec latency and jitter 48 - 55 6 Voice(Interactive Media) less than 10 msec latency and jitter 56 - 63 7 Network Control(Reserved Traffic)
When trust mode is “port priority”
- The transmission queue ID is determined by the port priority.
- By default (when QoS is enabled), port priority is set to 2. The setting can be changed using the qos port-priority-queue command.
If the trust mode is “CoS” or “DSCP,” the transmission queue ID might be reassigned due to QoS processing (see below) by the policy map.
In this case, the new transmission queue ID is reassigned based on the transmission queue ID conversion table that corresponds to the port’s trust mode.
- Pre-marking
- Refer to “Pre-marking” for details.
- Specify transmission queue
- When the trust mode is “CoS”, specify the CoS value that corresponds to the transmission queue ID, using the set cos-queue command.
- When the trust mode is “DSCP”, specify the DSCP value that corresponds to the transmission queue ID, using the set dscp-queue command.
- Remarking
- Refer to Metering/policing/remarking for details.
If the trust mode is “port priority,” the transmission queue ID cannot be changed by the policy map’s QoS processing. (It is not possible to apply a policy map that includes premarking, transmission queue specification, and remarking settings.)
3.4 Transmission queue assignments (frames sent from the switch itself)
As an exception to the transmission queue assignments, frames sent from the switch itself (CPU) are automatically assigned the transmission queue determined by the system. (They are not given transmission queue assignments based on the trust mode.)
The qos queue sent-from-cpu command can be used to change the transmission queue that is assigned, and by default the transmission queue ID is set to 7.
3.5 Traffic classification
Traffic classification is a function to classify received frames, based on a class map that defines the conditions of the IP header, TCP header, and so on.
The conditions that can be classified and the commands for settings are shown in the table below.
- Conditions that can be classified, and commands for settings
Classification condition Condition-setting command Class map setting mode Number that can be registered per class map Source/destination MAC address access-list
(*Note 3)match access-list 1 Source/destination IP address 1 IP protocol type (*Note 1) 1 Ethernet frame type number match ethertype 1 CoS value for VLAN tag header match cos 8 Precedence value for IP header match ip-precedence 8 DSCP value for IP header match ip-dscp 8 VLAN ID (*Note 2) match vlan, match vlan-range 30 *1: IPv6 is not subject to classification by IP protocol type.
*2: Does not include isolated or community VLANs in a private VLAN.
*3: Up to 39 conditions can be set in the access list for traffic classification.
- Traffic is classified per class map.
- One classification condition type can be set for one class map. Policer-based QoS processing (metering/policing/remarking) and pre-marking, as well as specifying the transmission queue can be done for frames that match the conditions.
- If classification conditions are not specified, all frames are classified into the corresponding traffic class.
- For classification based on CoS, IP precedence, DSCP, and the VLAN ID, multiple classifications can be made for one class map.
- Associating multiple class maps to a policy map will make it possible to classify complex traffic for the receiving port. Up to eight class maps can be associated to one policy map.
- Information for the class map that was set can be confirmed using the show class-map command.
- Information for the policy map that was set can be confirmed using the show policy-map command.
- Use the show qos map-status to check the port to which the policy map is applied, and the policy map to which the class map is associated.
3.6 Pre-marking
Pre-marking is a function to change (assign) the CoS, IP precedence, and DSCP values for received frames classified into traffic classes.
Pre-marking is set using the policy map and class mode settings shown below.
- Pre-marking setting commands
Pre-marking target Command for settings CoS set cos IP Precedence set ip-precedence DSCP set ip-dscp - The DSCP values that can be premarked include the value recommended in the RFC and those not found in the RFC, for a total of four. (This rule also applies to DSCP values that are used in remarking.)
- Only one pre-marking setting can be made for a class map. This cannot be used together when specifying a transmission queue (set cos-queue, set ip-dscp-queue).
- When pre-marking, the transmission queue will be reassigned based on the changed value and the transmission queue ID conversion table that corresponds to the trust mode.
3.7 Metering/policing/remarking
Bandwidth can be controlled by measuring the bandwidth used, and discarding or reprioritizing packets according to the measurement results.
The processing series for metering, policing and remarking is done per “policer”.
- Processing summary for bandwidth control
Process name Summary Metering This measures how much bandwidth is being taken up by the classified traffic based on the traffic rate and burst size, and classifies this into three bandwidth classes (green, yellow and red). Actions such as discarding (policing) and remarking can be specified for each classified bandwidth class.
Policing The bandwidth usage can be kept within a certain amount by discarding frames, using bandwidth class information. Remarking The CoS, IP precedence and DSCP value for a frame can be changed using the bandwidth class information.
Metering, policing, and remarking cannot be performed for the following logical interfaces.
Logical interface grouped across the member switches that make up the stack (green I/F below)
3.7.1 Policer types
There are two types of policers: an individual policer that performs metering/policing/remarking on one traffic class, and an aggregate policer that performs these actions on multiple aggregated traffic classes.
- Individual policer
Metering/policing/remarking is done per traffic class.
To make settings, use the policy map/class mode’s police command and remark-map command.
- Aggregate policer
Metering/policing/remarking is done on multiple traffic classes, which are aggregated.
The aggregate policer can be created using the aggregate-police command, and the content can be specified by the aggregate policer mode’s police command and remark-map command.
To apply a created aggregate policer to a traffic class, use the police-aggregate command.
- The commands used to make settings for an individual policer and an aggregate policer respectively are as follows.
Content of setting Individual policer Aggregate policer Create policer - aggregate-police Set policer (metering/policing/remarking)
police single-rate, police twin-rate (policy map / class mode)
police single-rate, police twin-rate (aggregate policer mode)
Apply policer to traffic class police-aggregate Detailed remarking settings remark-map (policy map / class mode)
remark-map (aggregate policer mode)
3.7.2 Metering settings
There are two types of metering: single rate policy (RFC2697) and twin rate policy (RFC2698).
The type of metering to use and the control parameters are specified using the police command (policy map/class mode or aggregate policer mode).
- Single rate policers (RFC2697)
Single rate policers separate the frames within a traffic class into three bandwidth classes: “green” (conforming), “yellow” (exceeding) or “red” (violating), based on the traffic rate (CIR) and burst size (CBS, EBS).
- Single rate policer control parameters
Parameter Explanation CIR (Committed Information Rate) This is the amount of tokens that is periodically stored in buckets. The amount can be specified in the range of 1–102,300,000 kbps.
CBS (Committed Burst Size) This is the amount of traffic that can be removed at one time from the first token bucket (a conforming token bucket). The amount can be specified in the range of 11–2,097,120 kByte.
EBS (Exceed Burst Size) This is the amount of traffic that can be removed at one time from the second token bucket (an exceeding token bucket). The amount can be specified in the range of 11–2,097,120 kByte.
- Single rate policer control parameters
- Twin rate policer (RFC2698)
Twin rate policers separate the frames within a traffic class into three bandwidth classes: “green” (conforming), “yellow” (exceeding) or “red” (violating), based on the traffic rate (CIR) and burst size (CBS, EBS).
- Twin rate policer control parameters
Parameter Explanation CIR (Committed Information Rate) This is the amount of tokens periodically stored in the second token bucket (confirming token bucket). The amount can be specified in the range of 1–102,300,000 kbps.
PIR (Peak Information Rate) This is the amount of tokens periodically stored in the first token bucket (peak token bucket). The amount can be specified in the range of 1–102,300,000 kbps.
However, a value smaller than the CIR cannot be specified.
CBS (Committed Burst Size) This is the amount of token traffic that can be removed at one time from the conforming token bucket. The amount can be specified in the range of 11–2,097,120 kByte.
PBS (Peak Burst Size) This is the amount of token traffic that can be removed at one time from the peak token bucket. The amount can be specified in the range of 11–2,097,120 kByte.
- Twin rate policer control parameters
3.7.3 Metering action (policing/remarking) settings
To specify the action for a bandwidth class that was categorized by metering, use the police command (in policy map/class mode or aggregate policer mode).
This product lets you define the following actions for each bandwidth class.
- Specifying bandwidth class actions
Bandwidth class Forward Discard Remark Green ✓ - - Yellow ✓ ✓ ✓ (only one or the other)
Red - ✓ - To make detailed settings for remarking, use the remark-map command (policy map/class mode or aggregate policer mode).
As with pre-marking, remarking to DSCP values can use the value recommended by RFC (refer to separate table 1. “Standard PHB (RFC recommended value)” and up to four others in addition.
When remarking, the transmission queue will be reassigned based on the changed value and the transmission queue ID conversion table that corresponds to the trust mode.
- If metering is not done, all frames that have been classified into traffic classes will be handled as the green bandwidth class.
3.8 Storing in the transmission queue
Frames are stored in the transmission queue that is finally determined through a series of QoS processing.
In order to resolve transmission queue congestion, this product provides a system to select and discard frames.
- Tail drop
This product uses the tail drop method to resolve overflow in the transmission queue.
When the threshold values shown below for the bandwidth class that is classified by metering has been exceeded, the frame in question will be discarded.
Frames discarded by tail drop are counted by the frame counter.
Bandwidth class Tail drop threshold value (%) Green + Yellow 100% Red 60% - Tail drop is disabled only if flow control is enabled.
It is not possible to change the threshold value.
- The extent of the transmission queue congestion can be checked using the show qos queue-counters command.
- The number of packets discarded by tail drop can be checked using the show interface, show frame-counter command.
3.9 Scheduling
Scheduling is used to determine what rules are used to send out the frames that are stored in the transmission queue.
Appropriate control of the scheduling along with the system to control congestion will help ensure QoS. (Inappropriate scheduling will result in degradation of QoS.)
This product supports two types of scheduling for the transmission queue, the strict priority system (SP) and the weighted round-robin (WRR) system.
SP and WRR can also be integrated in the interface and used together. (When doing so, SP will be given priority during processing.)
Strict priority system (SP)
The data with the highest priority in the queue will be transmitted first.
When a frame is stored in a high-priority queue, it can never be transmitted from a lower-priority queue.
Weighted round-robin system (WRR)
A weight is set for each queue, and frames are transmitted based on the ratio. A weight of 1–32 can be set.
Frames can also be transmitted from a lower-priority queue, within a specified percentage.
The transmission queue settings are made for the entire system, not for each interface.
Use the qos wrr-weight command to set the weight.
The default setting (when QoS is enabled) and the scheduling setting is “SP” for all queues.
3.10 Shaping
If a frame is forwarded from a broadband network to a narrowband network at the same transmission speed when connecting to a network with different bandwidth, the frame cannot be forwarded, which may result in insufficient bandwidth.
Shaping is a function that monitors the frame transmission speed, and restricts the forwarding rate to a specific amount by temporarily buffering frames with a speed that exceeds the limit, and then transmitting them.
Shaping on this product is realized by using a single token bucket.
- Single token bucket
- Shaping can be specified for individual ports and for individual queues, respectively using the following commands.
Object of shaping Command for settings By port traffic-shape By transmission queue traffic-shape queue - Specify the upper limit of the transmission rate (CIR) and the burst size (BC).
- The upper limit of the transmission rate (CIR) can be specified from 18–1,000,000 kbps.
- The burst size (BC) can be specified from 4–16,000 kbyte. However, this is specified in 4 Kbyte units.
- If shaping is used both by queue and by port, shaping by port is applied after shaping by queue.
- The default setting (when QoS is enabled) and the shaping setting is “disable” for all ports and all queues.
Separate table 1: Standard PHB (RFC recommended value)
Standard PHB (RFC recommended value)
| PHB | DSCP value | RFC | |
|---|---|---|---|
| Default | 0 | RFC2474 | |
| CS (Class Selector) | CS0 | 0 | RFC2474 |
| CS1 | 8 | ||
| CS2 | 16 | ||
| CS3 | 24 | ||
| CS4 | 32 | ||
| CS5 | 40 | ||
| CS6 | 48 | ||
| CS7 | 56 | ||
| AF (Assured Forwarding) | AF11 | 10 | RFC2597 |
| AF12 | 12 | ||
| AF13 | 14 | ||
| AF21 | 18 | ||
| AF22 | 20 | ||
| AF23 | 22 | ||
| AF31 | 26 | ||
| AF32 | 28 | ||
| AF33 | 30 | ||
| AF41 | 34 | ||
| AF42 | 36 | ||
| AF43 | 38 | ||
| EF (Expedited Forwarding) | 46 | RFC2598 | |
4 Related Commands
The related commands are shown below.
For details on the commands, refer to the Command Reference.
QoS-related commands
| Operations | Operating commands |
|---|---|
| Enable/disable QoS | qos enable |
| Set default CoS | qos cos |
| Change trust mode | qos trust |
| Generate policy map for ingress frames | policy-map |
| Apply policy map for ingress frames | service-policy input |
| Show status of QoS function setting | show qos |
| Show QoS information for LAN/SFP port | show qos interface |
| Show egress queue usage ratio | show qos queue-counters |
| Show policy map information | show policy-map |
| Show map status | show qos map-status |
| Set CoS - transmission queue ID conversion table | qos cos-queue |
| Set DSCP - transmission queue ID conversion table | qos dscp-queue |
| Set port priority order | qos port-priority-queue |
| Set priority order of frames sent from the switch itself | qos queue sent-from-cpu |
| Generate class map (traffic category conditions) | class-map |
| Associate class map | class |
| Set traffic classification conditions (access-group) | match access-list |
| Set traffic classification conditions (CoS) | match cos |
| Set traffic classification conditions (TOS precedence) | match ip-precedence |
| Set traffic classification conditions (DSCP) | match ip-dscp |
| Set traffic classification conditions (Ethernet Type) | match ethertype |
| Set traffic classification conditions (VLAN ID) | match vlan |
| Set traffic classification conditions (VLAN ID range) | match vlan-range |
| Show class map information | show class-map |
| Set pre-marking (CoS) | set cos |
| Set pre-marking (TOS precedence) | set ip-precedence |
| Set pre-marking (DSCP) | set ip-dscp |
| Set individual policer / aggregate policer (single rate) | police signle-rate |
| Set individual policer / aggregate policer (twin rate) | police twin-rate |
| Set remarking for individual policer / aggregate policer | remark-map |
| Create aggregate policer | aggregate-police |
| Show aggregate policer | show aggregate-police |
| Apply aggregate policer | police-aggregate |
| Show metering counter | show qos metering-counters |
| Clear metering counter | clear qos metering-counters |
| Set egress queue (CoS-Queue) | set cos-queue |
| Set egress queue (DSCP-Queue) | set ip-dscp-queue |
| Set egress queue scheduling | qos wrr-weight |
| Set traffic shaping (individual port) | traffic-shape rate |
| Set traffic shaping (individual queue) | traffic-shape queue rate |
5 Examples of Command Execution
5.1 Priority control (SP) using DSCP values
This example allocates the transmission queue based on the DSCP value of the frame, for priority control (SP).
When the DSCP = 56, 46, 8, 0 frame is received, large frames for DSCP values from LAN port #3 will be processed with priority.
- DSCP priority control (SP): setting example
- Prioritizing the input frame is done as follows.
- DSCP = 56 frame is set at priority level 7
- DSCP = 46 frame is set at priority level 5
- DSCP = 8 frame is set at priority level 1
- DSCP = 0 frame is set at priority level 0
- This sets the trust mode for the reception ports (LAN ports #1 and #2) on which QoS is enabled.
Yamaha(config)#qos enable … (Enable QoS) Yamaha(config)#interface port1.1 … (Settings for LAN port #1) Yamaha(config-if)#qos trust dscp … (Change trust mode to DSCP) Yamaha(config-if)#exit Yamaha(config)#interface port1.2 … (Settings for LAN port #2) Yamaha(config-if)#qos trust dscp … (Change trust mode to DSCP) Yamaha(config-if)#exit
- This sets the DSCP - transmission queue ID conversion table.
As the transmission queue ID corresponding to DSCP value = 46, 56 is the default, there is no need to make this setting, but it is listed for purposes of clarity.
Yamaha(config)#qos dscp-queue 56 7 … (Place frames of DSCP = 56 in transmission queue #7) Yamaha(config)#qos dscp-queue 46 5 … (Place frames of DSCP = 46 in transmission queue #5) Yamaha(config)#qos dscp-queue 8 1 … (Place frames of DSCP = 8 in transmission queue #1) Yamaha(config)#qos dscp-queue 0 0 … (Place frames of DSCP = 0 in transmission queue #0)
- This sets the scheduling method per transmission queue.
As this is the default, there is no need to make this setting, but it is listed for purposes of clarity.
Yamaha(config)# no qos wrr-weight 7 … (Queue:7 SP method) Yamaha(config)# no qos wrr-weight 5 … (Queue:5 SP method) Yamaha(config)# no qos wrr-weight 1 … (Queue:1 SP method) Yamaha(config)# no qos wrr-weight 0 … (Queue:0 SP method)
5.2 Priority control (SP+WRR) using an access list
This example classifies traffic by using the source IP address, and sets the priority control (WRR).
- Priority control (SP+WRR): setting example
- Classification conditions and priority setting for input frames
- The packet from 192.168.10.2 is classified as traffic A, and is set with a priority level of 7 during packet transmission
- The packet from 192.168.20.2 is classified as traffic B, and is set with a priority level of 6 during packet transmission
- The packet from 192.168.30.2 is classified as traffic C, and is set with a priority level of 5 during packet transmission
- The packet from 192.168.40.2 is classified as traffic D, and is set with a priority level of 4 during packet transmission
- The packet from 192.168.50.2 is classified as traffic E, and is set with a priority level of 3 during packet transmission
- The packet from 192.168.60.2 is classified as traffic F, and is set with a priority level of 2 during packet transmission
- The packet from 192.168.70.2 is classified as traffic G, and is set with a priority level of 1 during packet transmission
- The packet from 192.168.80.2 is classified as traffic H, and is set with a priority level of 0 during packet transmission
- Scheduling method
These are the integrated SP and WRR settings to make.
Queue ID Method Weight (%) 7 SP - 6 SP - 5 SP - 4 WRR 8 (40.0%) 3 WRR 6 (30.0%) 2 WRR 3 (15.0%) 1 WRR 2 (10.0%) 0 WRR 1 (5.0%)
- This enables QoS, defines the access lists for traffic A–H, and defines the traffic classes that will be set in the LAN ports.
Yamaha(config)#qos enable … (Enable QoS) Yamaha(config)#access-list 1 permit any 192.168.10.2 0.0.0.0 any … (Traffic A) Yamaha(config)#class-map cmap-A Yamaha(config-cmap)#match access-list 1 Yamaha(config-cmap)#exit Yamaha(config)#access-list 2 permit any 192.168.20.2 0.0.0.0 any … (Traffic B) Yamaha(config)#class-map cmap-B Yamaha(config-cmap)#match access-list 2 Yamaha(config-cmap)#exit Yamaha(config)#access-list 3 permit any 192.168.30.2 0.0.0.0 any … (Traffic C) Yamaha(config)#class-map cmap-C Yamaha(config-cmap)#match access-list 3 Yamaha(config-cmap)#exit Yamaha(config)#access-list 4 permit any 192.168.40.2 0.0.0.0 any … (Traffic D) Yamaha(config)#class-map cmap-D Yamaha(config-cmap)#match access-list 4 Yamaha(config-cmap)#exit Yamaha(config)#access-list 5 permit any 192.168.50.2 0.0.0.0 any … (Traffic E) Yamaha(config)#class-map cmap-E Yamaha(config-cmap)#match access-list 5 Yamaha(config-cmap)#exit Yamaha(config)#access-list 6 permit any 192.168.60.2 0.0.0.0 any … (Traffic F) Yamaha(config)#class-map cmap-F Yamaha(config-cmap)#match access-list 6 Yamaha(config-cmap)#exit Yamaha(config)#access-list 7 permit any 192.168.70.2 0.0.0.0 any … (Traffic G) Yamaha(config)#class-map cmap-G Yamaha(config-cmap)#match access-list 7 Yamaha(config-cmap)#exit Yamaha(config)#access-list 8 permit any 192.168.80.2 0.0.0.0 any … (Traffic H) Yamaha(config)#class-map cmap-H Yamaha(config-cmap)#match access-list 8 Yamaha(config-cmap)#exit
- This reverts the CoS - transmission queue ID conversion table to the default setting.
Yamaha(config)#no qos cos-queue 0 Yamaha(config)#no qos cos-queue 1 Yamaha(config)#no qos cos-queue 2 Yamaha(config)#no qos cos-queue 3 Yamaha(config)#no qos cos-queue 4 Yamaha(config)#no qos cos-queue 5 Yamaha(config)#no qos cos-queue 6 Yamaha(config)#no qos cos-queue 7
- This generates and applies the policy to LAN port #1 (port1.1).
This sets a transmission queue with CoS value 7 to traffic-A, and a transmission queue with CoS value 6 to traffic-B.
Yamaha(config)#policy-map pmap1 Yamaha(config-pmap)#class cmap-A Yamaha(config-pmap-c)#set cos-queue 7 … (Traffic-A is local priority order 7) Yamaha(config-pmap-c)#exit Yamaha(config-pmap)#class cmap-B Yamaha(config-pmap-c)#set cos-queue 6 … (Traffic-B is local priority order 6) Yamaha(config-pmap-c)#exit Yamaha(config-pmap)#exit Yamaha(config)#interface port1.1 … (LAN port #1) Yamaha(config-if)#service-policy input pmap1 … (Apply policy to received frames) Yamaha(config-if)# exit
- This generates and applies the policy to LAN port #2 (port1.2).
This sets a transmission queue with CoS value 5 to traffic-C, and a transmission queue with CoS value 4 to traffic-D.
Yamaha(config)#policy-map pmap2 Yamaha(config-pmap)#class cmap-C Yamaha(config-pmap-c)#set cos-queue 5 … (Traffic-C is local priority order 5) Yamaha(config-pmap-c)#exit Yamaha(config-pmap)#class cmap-D Yamaha(config-pmap-c)#set cos-queue 4 … (Traffic-D is local priority order 4) Yamaha(config-pmap-c)#exit Yamaha(config-pmap)#exit Yamaha(config)#interface port1.2 … (LAN port #2) Yamaha(config-if)#service-policy input pmap2 … (Apply policy to received frames) Yamaha(config-if)# exit
- This generates and applies the policy to LAN port #3 (port1.3).
This sets a transmission queue with CoS value 3 to traffic-E, and a transmission queue with CoS value 0 to traffic-F.
Yamaha(config)#policy-map pmap3 Yamaha(config-pmap)#class cmap-E Yamaha(config-pmap-c)#set cos-queue 3 … (Traffic-E is local priority order 3) Yamaha(config-pmap-c)#exit Yamaha(config-pmap)#class cmap-F Yamaha(config-pmap-c)#set cos-queue 0 … (Traffic-D is local priority order 2) Yamaha(config-pmap-c)#exit Yamaha(config-pmap)#exit Yamaha(config)#interface port1.3 … (LAN port #3) Yamaha(config-if)#service-policy input pmap3 … (Apply policy to received frames) Yamaha(config-if)# exit
- This generates and applies the policy to LAN port #4 (port1.4).
This sets a transmission queue with CoS value 2 to traffic-E, and a transmission queue with CoS value 1 to traffic-F.
Yamaha(config)#policy-map pmap4 Yamaha(config-pmap)#class cmap-G Yamaha(config-pmap-c)#set cos-queue 2 … (Traffic-G is local priority order 1) Yamaha(config-pmap-c)#exit Yamaha(config-pmap)#class cmap-H Yamaha(config-pmap-c)#set cos-queue 1 … (Traffic-D is local priority order 0) Yamaha(config-pmap-c)#exit Yamaha(config-pmap)#exit Yamaha(config)#interface port1.4 … (LAN port #4) Yamaha(config-if)#service-policy input pmap4 … (Apply policy to received frames) Yamaha(config-if)#exit
- This sets the scheduling method for the transmission queue.
As this queue IDs 5, 6, and 7 are the defaults, there is no need to make this setting, but it is listed for purposes of clarity.
Yamaha(config)#qos wrr-weight 0 1 … (Transmission queue 0: WRR method, weight 1) Yamaha(config)#qos wrr-weight 1 2 … (Transmission queue 1: WRR method, weight 2) Yamaha(config)#qos wrr-weight 2 3 … (Transmission queue 2: WRR method, weight 3) Yamaha(config)#qos wrr-weight 3 6 … (Transmission queue 3: WRR method, weight 6) Yamaha(config)#qos wrr-weight 4 8 … (Transmission queue 4: WRR method, weight 8) Yamaha(config)#no qos wrr-weight 5 … (Transmission queue 5: SP method) Yamaha(config)#no qos wrr-weight 6 … (Transmission queue 6: SP method) Yamaha(config)#no qos wrr-weight 7 … (Transmission queue 7: SP method)
5.3 Priority control using port priority trust mode
The transmission queue is determined according to the port priority order that is specified for each reception port.
- Priority control using port priority: setting example
- Set priority for each reception port
- Set LAN port#1 (port1.1) to priority order 6.
- Set LAN port#2 (port1.2) to priority order 4.
- Set LAN port#3 (port1.3) to priority order 2.
- Enable QoS and set the trust mode for the reception ports (LAN ports #1, #2, and #3).
Yamaha(config)#qos enable … (Enable QoS) Yamaha(config)#interface port1.1 … (Settings for LAN port #1) Yamaha(config-if)#qos trust port-priority … (Change trust mode to “port priority”) Yamaha(config-if)#qos port-priority-queue 6 … (Set port priority order to 6) Yamaha(config-if)#exit Yamaha(config)#interface port1.2 … (Settings for LAN port #2) Yamaha(config-if)#qos trust port-priority … (Change trust mode to “port priority”) Yamaha(config-if)#qos port-priority-queue 4 … (Set port priority order to 4) Yamaha(config-if)#exit Yamaha(config)#interface port1.3 … (Settings for LAN port #3) Yamaha(config-if)#qos trust port-priority … (Change trust mode to “port priority”) Yamaha(config-if)#qos port-priority-queue 2 … (Set port priority order to 2) Yamaha(config-if)#exit
5.4 Bandwidth control using access list (twin rate / individual policer)
This example set bandwidth control by using the source IP address. A twin rate policer and an individual policer are used for metering.
- Bandwidth control: setting example
- Classification conditions and bandwidth limits for input frames
- Packets from 192.168.10.2 are classified as traffic A, and a reception rate (CIR) of 25 Mbps is guaranteed.
- Packets from 192.168.20.2 are classified as traffic B, and a reception rate (CIR) of 15 Mbps is guaranteed.
- Packets from 192.168.30.2 are classified as traffic C, and a reception rate (CIR) of 10 Mbps is guaranteed.
- Enable QoS, define the access lists for traffic A–C, and define the traffic classes that will be set for the LAN ports.
Yamaha(config)#qos enable … (Enable QoS) Yamaha(config)#access-list 1 permit any 192.168.10.2 0.0.0.0 any … (Traffic A) Yamaha(config)#class-map cmap-A Yamaha(config-cmap)#match access-list 1 Yamaha(config-cmap)#exit Yamaha(config)#access-list 2 permit any 192.168.20.2 0.0.0.0 any … (Traffic B) Yamaha(config)#class-map cmap-B Yamaha(config-cmap)#match access-list 2 Yamaha(config-cmap)#exit Yamaha(config)#access-list 3 permit any 192.168.30.2 0.0.0.0 any … (Traffic C) Yamaha(config)#class-map cmap-C Yamaha(config-cmap)#match access-list 3 Yamaha(config-cmap)#exit
- Generate and apply the policy to LAN port #1 (port1.1).
Individually specify metering for traffic A through traffic C.
In the twin rate policer, bandwidth for green can be allocated (guaranteed) by discarding yellow and red.
Yamaha(config)#policy-map pmap1 Yamaha(config-pmap)#class cmap-A … (Set Traffic-A metering) Yamaha(config-pmap-c)#police twin-rate 25000 25000 156 11 yellow-action drop red-action drop Yamaha(config-pmap-c)#exit Yamaha(config-pmap)#class cmap-B … (Set Traffic-B metering) Yamaha(config-pmap-c)#police twin-rate 15000 15000 93 11 yellow-action drop red-action drop Yamaha(config-pmap-c)#exit Yamaha(config-pmap)#class cmap-C … (Set Traffic-C metering) Yamaha(config-pmap-c)#police twin-rate 10000 10000 62 11 yellow-action drop red-action drop Yamaha(config-pmap-c)#exit Yamaha(config-pmap)#exit Yamaha(config)#interface port1.1… (LAN port 1) Yamaha(config-if)#service-policy input pmap1 … (Apply policy to received frames) Yamaha(config-if)#exit
- The metering setting values are shown below.
- Metering type: Twin rate policer
- Traffic-A: CIR, PIR (25,000 kbps), CBS (156 kbyte), PBS (11 kbyte)
- Traffic-B: CIR, PIR (15,000 kbps), CBS (93 kbyte), PBS (11 kbyte)
- Traffic-C: CIR, PIR (10,000 kbps), CBS (62 kbyte), PBS (11 kbyte)
The following calculation is used to find the CBS, with a round-trip time of 0.05 sec.
CBS = CIR (bps) ÷ 8 (bit) × 0.05 (second)
- The metering setting values are shown below.
5.5 Bandwidth control using access list (single rate / aggregate policer)
This example set bandwidth control by using the source IP address. A single rate policer and an aggregate policer are used for metering.
- Bandwidth control: setting example
- Classification conditions and bandwidth limits for input frames
- Packets from 192.168.10.2 are classified as traffic A.
- Packets from 192.168.20.2 are classified as traffic B.
- Packets from 192.168.30.2 are classified as traffic C.
- The reception rate is limited to 25 Mbps for traffic A, B, and C collectively.
- Bandwidth class C “yellow” is remarked as DSCP=0, and sent with low priority.
- Enable QoS, define the access lists for traffic A–C, and define the traffic classes that will be set for the LAN ports.
Yamaha(config)#qos enable … (Enable QoS) Yamaha(config)#access-list 1 permit any 192.168.10.2 0.0.0.0 any … (Traffic A) Yamaha(config)#class-map cmap-A Yamaha(config-cmap)#match access-list 1 Yamaha(config-cmap)#exit Yamaha(config)#access-list 2 permit any 192.168.20.2 0.0.0.0 any … (Traffic B) Yamaha(config)#class-map cmap-B Yamaha(config-cmap)#match access-list 2 Yamaha(config-cmap)#exit Yamaha(config)#access-list 3 permit any 192.168.30.2 0.0.0.0 any … (Traffic C) Yamaha(config)#class-map cmap-C Yamaha(config-cmap)#match access-list 3 Yamaha(config-cmap)#exit
- Set the DSCP–transmission queue ID conversion table.
Assign the lowest-priority transmission queue to the DSCP value (0) used for remarking “yellow.”
Yamaha(config)#qos dscp-queue 0 0
- Create an aggregate policer.
Yamaha(config)#aggregate-police agp1 … (Create aggregate policer) Yamaha(config-agg-policer)#police single-rate 25000 156 11 yellow-action remark red-action drop Yamaha(config-agg-policer)#remark-map yellow ip-dscp 0 Yamaha(config-agg-policer)#exit
- The aggregate policer’s metering setting values are as follows.
- Metering type: Single rate policer
- Remark “yellow” to DSCP value = 0
- CIR (25,000 kbps), CBS (156 kbyte), EBS (11 kbyte)
The following calculation is used to find the CBS, with a round-trip time of 0.05 sec.
CBS = CIR (bps) ÷ 8 (bit) × 0.05 (second)
- The aggregate policer’s metering setting values are as follows.
- Generate and apply the policy to LAN port #1 (port1.1).
Specify metering (aggregate policer) for the aggregated traffic of A through C.
Yamaha(config)#policy-map pmap1 Yamaha(config-pmap)#class cmap-A … (Set Traffic-A metering) Yamaha(config-pmap-c)#police-aggregate agp1 Yamaha(config-pmap-c)#exit Yamaha(config-pmap)#class cmap-B … (Set Traffic-B metering) Yamaha(config-pmap-c)#police-aggregate agp1 Yamaha(config-pmap-c)#exit Yamaha(config-pmap)#class cmap-C … (Set Traffic-C metering) Yamaha(config-pmap-c)#police-aggregate agp1 Yamaha(config-pmap-c)#exit Yamaha(config-pmap)#exit Yamaha(config)#interface port1.1… (LAN port 1) Yamaha(config-if)#service-policy input pmap1 … (Apply policy to received frames) Yamaha(config-if)#exit
6 Points of Caution
- LAN/SFP ports that use settings different from those shown below cannot be aggregated as a logical interface. Also, as for the settings shown below for a LAN/SFP port that belongs to a logical interface in startup config, the settings for the most recent port number will be applied to the logical interface.
- Trust mode
- Default CoS
- Port priority
- LAN/SFP ports on which policy maps have been applied cannot belong to a logical interface.
- Policy maps cannot be applied to a LAN/SFP port that belongs to a logical interface. However, if a LAN/SFP port that belongs to a logical interface in startup config has a policy map, the settings for the most recent port number will be applied to the logical interface.
- Fragment packets may not be judged correctly. Specifically, if layer 4 information (source port number, destination port number, and various TCP flags) is included in the conditions, since the information is not included in the second and subsequent fragment packets, correct judgment cannot be made. If there is a possibility of processing fragmented packets, do not include Layer 4 information in the conditions.
7 Related Documentation
None
Flow control
1 Function Overview
A switching hub initially stores received frames in memory and then performs relay processing.
When many frames are sent at the same time and relay processing cannot keep up (a congested state), exceeding the available memory capacity for storage, the frames to be relayed are discarded.
This product includes the following two functions to help mitigate such congestion.
- When ports are operating at full duplex: IEEE 802.3x flow control can be enabled.
- When ports are operating at half duplex: the back pressure function will always be enabled.
2 Definition of Terms Used
- Bit time
- On a 10BASE network, the speed is 10Mbps, so 1 bit time = 100 nsec.
In the same way, the bit time on 100BASE is 10 nsec, and on 1000BASE is 1 nsec.
- Jam signals
In half-duplex communications, where data cannot be transmitted and received at the same time, there is a possibility of data collision. The transmitting device monitors the possibility of data collision during transmission. When possible data collision is detected, the device stops transmitting and sends a jam signal. After the jam signal is sent, the device waits for a random interval before resuming transmission.
Although undefined in IEEE, jam signals that use a 32-digit alternating “1” and “0” bit sequence (such as “10101010101010101010101010101010”) are often used.
3 Function Details
3.1 IEEE 802.3x flow control
For full duplex communication, the MAC control protocol with IEEE802.3x option can be used. The MAC control frame in the diagram below is used for flow control.
MAC control frame

The following flow control operations are performed, based on the restriction start threshold and the restriction cancel threshold.
Flow control: processing flow

This product can be used for either transmitting or receiving MAC control frames. The operations for each are shown below.
- MAC control frame transmission processing
- Frames are stored in the receive buffer. When the number of frames exceeds the restriction start threshold, a PAUSE frame with a pause time of 65535 is sent.
- When the overflow in the receive buffer is resolved, and the number of frames falls below the restriction cancel threshold, a PAUSE frame with a pause time of 0 is sent.
- MAC control frame reception processing
- When a PAUSE frame with a pause time of 1–65535 is received, the transmission processing will be stopped if the corresponding bit time has elapsed, or if the a PAUSE frame with a pause time of 0 has been received.
Use the flowcontrol command to enable or disable the flow control (when transmitting/receiving MAC control frames).
This setting can be made for the system and for each transmitting/receiving LAN/SFP port, and is set to “disable” by factory default.
In order to enable flow control for an individual port, flow control must be enabled for the system.
The tail drop function is disabled when flow control is enabled in the system, except when the stack function is enabled.
If the Qos function is enabled, flow control cannot be enabled.
When the stack function is enabled, only Pause frames can be received.
3.2 Back pressure
This product sends a jam signal whenever the receiving buffer of a LAN port is about to overflow.
With this, the sender waits for a random amount of time as per the CSMA/CD, and then sends the frames.
When the LAN port is operating at half duplex, the back pressure function will always be enabled.
In addition, when the stack is enabled, jam signals are not sent for communication via the stack port.
Back pressure processing flow

4 Related Commands
The related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Set (system) flow control (IEEE 802.3x PAUSE send/receive) | flowcontrol |
| Set (interface) flow control (IEEE 802.3x PAUSE send/receive) | flowcontrol |
| Show flow control operating status | show flowcontrol |
5 Examples of Command Execution
- Enable flow control on LAN port #1.
After the function is enabled, check the flow control operating status.
Yamaha(config)#interface port1.1 Yamaha(config-if)#flowcontrol both Yamaha(config-if)#end Yamaha#show flowcontrol port1.1 Port FlowControl RxPause TxPause --------- ----------- ------- ------- port1.1 Both 0 64
6 Points of Caution
None
7 Related Documentation
None
Storm control
1 Function Overview
This product provides a storm control function as a countermeasure against L2 loops and DoS attacks.
Broadcasts, multicasts, and unicast (dlf) frames that are addressed to an unknown host are monitored for each LAN/SFP port, and frames that exceed a preset threshold value are discarded.
This prevents such frames from taking up bandwidth on the LAN/SFP port.
Using this along with the proprietary loop detection and storm control functions enhances the precision of loop detection (avoiding such frames in the first place).
2 Definition of Terms Used
- Broadcast storm/multicast storm
This means a situation where frames addressed for broadcast or multicast are continuously forwarded.
In this situation, the switch floods all ports except for the reception port with the broadcast or multicast.
When this is received by another switch, all ports except for the reception port are flooded in the same way.
When this continues, it can lead to the following symptoms.
- Bandwidth is taken up by the broadcast storm/multicast storm
- The switch’s CPU load increases, making normal operations difficult
- Devices connected to the switch become unable to communicate
- Unicast stream
This means a situation where frames addressed to an unknown unicast destination (dlf: Destination Lookup Failure) are continuously forwarded.
When the MAC address of the receiving device has not been registered in the ARP table, all ports on the switch except for the reception port are flooded.
This leads to the same symptoms occurring as with a broadcast storm or multicast storm.
3 Function Details
The operating specifications for storm control are shown below.
- The storm control function can be enabled for LAN/SFP ports.
The setting is disabled for all ports by default.
- Storm control on this product can be specified as a tolerance percentage for the bandwidth of the LAN/SFP ports that receive broadcast frames, multicast frames, and frames addressed to an unknown unicast destination.
(Control can be made in two decimal points. Specifying 100% is the same as disabling the storm function.)
The bandwidth tolerance is common for all frames, and the user can select the applicable frames.
The settings are made using the storm-control command.
- The following SYSLOG will be outputted at the time that storm control is enabled or disabled.
- When enabled: [ STORM]:inf: storm-control ENABLE (port:port1.1, type:B M U, level:50. 0%)
- When disabled: [ STORM]:inf: storm-control DISABLE (port:port1.1)
- When frames are received that exceeds the permitted bandwidth, the excessive frames are discarded.
- Use the show storm-control command to check the storm control information set for the LAN/SFP port.
4 Related Commands
The related commands are shown below.
For details on the commands, refer to the Command Reference.
List of related commands
| Operations | Operating commands |
|---|---|
| Set storm control | storm-control |
| Show storm control reception upper limit | show storm-control |
5 Examples of Command Execution
In this example, the receivable L2 broadcast packets for LAN port 1 are restricted to a port bandwidth of 30%.
Storm control command setting: example

Yamaha(config)#interface port1.1 Yamaha(config-if)#storm-control broadcast level 30 … (Limit broadcast to 30% of bandwidth) Yamaha(config-if)#end Yamaha# Yamaha#show storm-control Port BcastLevel McastLevel UcastLevel port1.1 30.00% 100.00% 100.00% port1.2 100.00% 100.00% 100.00% port1.3 100.00% 100.00% 100.00% port1.4 100.00% 100.00% 100.00% port1.5 100.00% 100.00% 100.00% port1.6 100.00% 100.00% 100.00% port1.7 100.00% 100.00% 100.00% port1.8 100.00% 100.00% 100.00% port1.9 100.00% 100.00% 100.00%
6 Points of Caution
None
7 Related Documentation
- L2 switching functions: Proprietary loop detection
- SWR2310 Series Technical Data (Basic Functions)
- Other information
- SWR2310 Series Technical Data (Basic Functions)
- Other information
- SNMP MIB Reference
SNMP MIB Reference
1 SNMP MIB List
The SNMP MIBs that are supported by this product are shown below.
1.1 MIB tree
The MIB tree for MIB groups that are supported by this product are shown below.
iso(1)
|
+--std(0)
| |
| +--iso8802(8802)
| |
| +--ieee802dot1(1)
| |
| +--ieee802dot1mibs(1)
| |
| +--ieee8021paeMIB(1) (port authentication information)
|
+--member-body(2)
| |
| +--us(840)
| |
| +--802dot3(10006)
| |
| +--snmpmibs(300)
| |
| +--lagMIB(43) (LACP link aggregation information)
|
+--org(3)
|
+--dod(6)
| |
| +--internet(1)
| |
| +--mgmt(2)
| | |
| | +--mib-2(1)
| | |
| | +--system(1) (system information)
| | |
| | +--interfaces(2) (interface information)
| | |
| | +--at(3) (mapping information for network addresses and physical addresses)
| | |
| | +--rmon(16) (RMON information)
| | |
| | +--dot1dBridge(17) (dot1dBridge information)
| | |
| | +--ifMIB(31) (additional information for interface)
| |
| +--private(4)
| |
| +--enterprises(1)
| |
| +--yamaha(1182)
| |
| +--yamahaSW(3) (private MIB Yamaha switch information)
| |
| +--yamahaSWHardware(1) (hardware information)
| |
| +--yamahaSWFirmware(2) (firmware information)
| |
| +--yamahaSWL2ms(5) (L2MS information)
| |
| +--yamahaSWErrDisable(6) (error detection function information)
| |
| +--yamahaSWRmon(7) (RMON information)
| |
| +--yamahaSWTermMon(8) (terminal monitoring information)
| |
| +--yamahaSWBridge(9) (dot1dBridge information)
|
+--ieee(111)
|
+--standards-association-numbers-series-standards(2)
|
+--lan-man-stds(802)
|
+--ieee802dot1(1)
|
+--ieee802dot1mibs(1)
|
+--lldpV2MIB(13) (LLDP information)
1.2 Standard MIB list
The standard MIB that are supported are shown below.
MIB groups and overview
| MIB group | Summary |
|---|---|
| ieee8021paeMIB group | Port authentication information |
| lagMIB group | LACP link aggregation information |
| system group | System information |
| interface group | Interface information |
| at group | Mapping information for physical addresses and network addresses |
| rmon group | RMON information |
| dot1dBridge group | dot1dBridge information |
| ifMIB group | Additional information for interface |
| lldpV2MIB group | LLDP information |
1.3 Private MIB list
Private MIBs that are supported are shown below.
All of this information is related to Yamaha switches.
MIB groups and overview
| MIB group | Summary |
|---|---|
| yamahaSWHardware group | Hardware information |
| yamahaSWFirmware group | Firmware information |
| yamahaSWL2ms group | L2MS information |
| yamahaSWErrDisable group | Error detection function information |
| yamahaSWRmon group | RMON information |
| yamahaSWTermMon group | Terminal monitoring information |
| yamahaSWBridge group | dot1dBridge information |
1.4 Standard MIB trap list
The standard MIB traps that are supported are shown below.
Traps and overview
| Trap | Summary |
|---|---|
| coldStart | Power OFF/ON notification |
| warmStart | Reload notification |
| linkDown | Linkdown notification |
| linkUp | Linkup notification |
| authenticationFailure | Notification of failed authentication |
| risingAlarm | Notification that RMON upper threshold value has been exceeded |
| fallingAlarm | Notification that RMON lower threshold value has been exceeded |
| newRoot | Notification that new root for bridge has been detected |
| topologyChange | Notification when a change in topology has been detected |
1.5 Private MIB trap list
Private MIBs traps that are supported are shown below.
Traps and overview
| Trap | Summary |
|---|---|
| ysl2msFindSlave | Notification when L2MS slave is detected |
| ysl2msDetectDown | Notification when L2MS slave is lost |
| ysedTrap | Notification of detect/cancel for error detection function |
| ystmIfTermTrap | Notification of terminal monitoring (port) detection |
| ystmIpTermTrap | Notification of terminal monitoring (IP address) detection |
2 Definition of Terms Used
- MIB access classification
The MIB access used in subsequent explanations is described below.
MIB access classification
Access name Description R/O Access to the MIB is read-only R/W Access to the MIB is read-write R/NW Although the access to the MIB is read-write as per the standards, it is read-only on this product R/C Access to the MIB is read-create R/NC Although the access to the MIB is read-create as per the standards, it is read-only on this product N/A The MIB cannot be retrieved
Note: May be used as additional information for traps (variable-bindings)
3 Obtaining a private MIB
Private MIB files may be acquired from here.
4 Standard MIBs
Standard MIBs that are supported by this product are shown below.
4.1 ieee8021paeMIB group
This MIB is related to port authentication information.
The syntax defined in the ieee8021paeMIB group is shown below.
Syntax defined in the ieee8021paeMIB group
| Syntax | Definition |
|---|---|
| PaeControlledDirections | INTEGER ・both(0) ・in(1) |
| PaeControlledPortStatus | INTEGER ・authorized(1) ・unauthorized(2) |
| PaeControlledPortControl | INTEGER ・forceUnauthorized(1) ・auto(2) ・forceAuthorized(3) |
The ieee8021paeMIB group is divided into subgroups such as those shown below.
ieee8021paeMIB(1)
|
+--paeMIBObjects(1)
|
+--dot1xPaeSystem(1)
|
+--dot1xPaeAuthenticator(2)
dot1xPaeSystem group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| dot1xPaeSystemAuthControl | 1.0.8802.1.1.1.1.1.1 | R/NW | INTEGER ・enabled(1) ・disabled(2) | Setting value for authentication function at the system level | ||
| dot1xPaePortTable | 1.0.8802.1.1.1.1.1.2 | N/A | System-level information table | |||
| dot1xPaePortEntry | 1.0.8802.1.1.1.1.1.2.1 | N/A | INDEX ・dot1xPaePortNumber | |||
| dot1xPaePortNumber | 1.0.8802.1.1.1.1.1.2.1.1 | N/A | InterfaceIndex | Port numbers for which the authentication function is enabled | ||
| dot1xPaePortProtocolVersion | 1.0.8802.1.1.1.1.1.2.1.2 | R/O | Unsigned32 | Protocol version (2, fixed) | ||
| dot1xPaePortCapabilities | 1.0.8802.1.1.1.1.1.2.1.3 | R/O | BITS | PAE functions supported by the port (0, fixed) | ||
| dot1xPaePortInitialize | 1.0.8802.1.1.1.1.1.2.1.4 | R/NW | TruthValue | Initialization control for ports (2, fixed) | ||
| dot1xPaePortReauthenticate | 1.0.8802.1.1.1.1.1.2.1.5 | R/NW | TruthValue | Re-authentication control for ports (2, fixed) | ||
dot1xPaeAuthenticator group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| dot1xAuthConfigTable | 1.0.8802.1.1.1.1.2.1 | N/A | Structural object table for Authenticator PAE for each port | |||
| dot1xAuthConfigEntry | 1.0.8802.1.1.1.1.2.1.1 | N/A | INDEX ・dot1xPaePortNumber | |||
| dot1xAuthAdminControlledDirections | 1.0.8802.1.1.1.1.2.1.1.3 | R/NW | PaeControlledDirections | Packet forwarding operation in an unauthenticated state, controlled by management | ||
| dot1xAuthOperControlledDirections | 1.0.8802.1.1.1.1.2.1.1.4 | R/O | PaeControlledDirections | Packet forwarding operation in an unauthenticated state, controlled by operation | ||
| dot1xAuthAuthControlledPortStatus | 1.0.8802.1.1.1.1.2.1.1.5 | R/O | PaeControlledPortStatus | Port authentication status | ||
| dot1xAuthAuthControlledPortControl | 1.0.8802.1.1.1.1.2.1.1.6 | R/NW | PaeControlledPortControl | Setting value for 802.1X authentication operating mode | ||
| dot1xAuthQuietPeriod | 1.0.8802.1.1.1.1.2.1.1.7 | R/NW | Unsigned32 | Setting value for authentication restriction period | ||
| dot1xAuthSuppTimeout | 1.0.8802.1.1.1.1.2.1.1.9 | R/NW | Unsigned32 | Response wait time setting value for the supplicant | ||
| dot1xAuthServerTimeout | 1.0.8802.1.1.1.1.2.1.1.10 | R/NW | Unsigned32 | Setting value for server response wait time | ||
| dot1xAuthMaxReq | 1.0.8802.1.1.1.1.2.1.1.11 | R/NW | Unsigned32 | Setting value for number of times EAPOL packets are retransmitted | ||
| dot1xAuthReAuthPeriod | 1.0.8802.1.1.1.1.2.1.1.12 | R/NW | Unsigned32 | Setting value for reauthentication interval | ||
| dot1xAuthReAuthEnabled | 1.0.8802.1.1.1.1.2.1.1.13 | R/NW | TruthValue | Setting value for reauthentication function | ||
| dot1xAuthKeyTxEnabled | 1.0.8802.1.1.1.1.2.1.1.14 | R/NW | TruthValue | Constant value (2, fixed) used by Authenticator PAE state machine | ||
| dot1xAuthStatsTable | 1.0.8802.1.1.1.1.2.2 | N/A | Statistical data object table for Authenticator PAE associated with each port | |||
| dot1xAuthStatsEntry | 1.0.8802.1.1.1.1.2.2.1 | N/A | INDEX ・dot1xPaePortNumber | |||
| dot1xAuthEapolFramesRx | 1.0.8802.1.1.1.1.2.2.1.1 | R/O | Counter32 | No. of EAPOL frames that are received, all valid types | ||
| dot1xAuthEapolFramesTx | 1.0.8802.1.1.1.1.2.2.1.2 | R/O | Counter32 | No. of EAPOL frames that are transmitted, all types | ||
| dot1xAuthEapolStartFramesRx | 1.0.8802.1.1.1.1.2.2.1.3 | R/O | Counter32 | No. of EAPOL Start frames received | ||
| dot1xAuthEapolLogoffFramesRx | 1.0.8802.1.1.1.1.2.2.1.4 | R/O | Counter32 | No. of EAPOL Logoff frames received | ||
| dot1xAuthEapolRespIdFramesRx | 1.0.8802.1.1.1.1.2.2.1.5 | R/O | Counter32 | No. of EAP Response/Identity frames received | ||
| dot1xAuthEapolRespFramesRx | 1.0.8802.1.1.1.1.2.2.1.6 | R/O | Counter32 | No. of valid EAP Response frames, excepting EAP Response/Identity frames received | ||
| dot1xAuthEapolReqIdFramesTx | 1.0.8802.1.1.1.1.2.2.1.7 | R/O | Counter32 | No. of EAP Request/Identity frames transmitted | ||
| dot1xAuthEapolReqFramesTx | 1.0.8802.1.1.1.1.2.2.1.8 | R/O | Counter32 | No. of EAP Request frames, excepting EAP Request/Identity frames transmitted | ||
| dot1xAuthInvalidEapolFramesRx | 1.0.8802.1.1.1.1.2.2.1.9 | R/O | Counter32 | No. of frames within received EAPOL frames, for which frame type has not been approved | ||
| dot1xAuthEapLengthErrorFramesRx | 1.0.8802.1.1.1.1.2.2.1.10 | R/O | Counter32 | No. of received EAPOL frames, for which the packet body length is invalid | ||
| dot1xAuthLastEapolFrameVersion | 1.0.8802.1.1.1.1.2.2.1.11 | R/O | Unsigned32 | Protocol version numbers for most recently received EAPOL frames | ||
| dot1xAuthLastEapolFrameSource | 1.0.8802.1.1.1.1.2.2.1.12 | R/O | MacAddress | Source MAC address of EAPOL frames most recently received | ||
4.2 lagMIB group
This MIB is related to LACP link aggregation information.
The syntax defined in the lagMIB group is shown below.
Syntax defined in the lagMIB group
| Syntax | Definition |
|---|---|
| LacpKey | INTEGER (1..127) Note: Although this is INTEGER (0..65535) as per the standards, on this product it is in the range of INTEGER (1..127) |
| LacpState | BITS ・lacpActivity(0) ・lacpTimeout(1) ・aggregation(2) ・synchronization(3) ・collecting(4) ・distributing(5) ・defaulted(6) ・expired(7) |
| ChurnState | INTEGER ・noChurn(1) ・churn(2) ・churnMonitor(3) |
The lagMIB group is divided into subgroups such as those shown below.
lagMIB(43)
|
+--lagMIBObjects(1)
|
+--dot3adAgg(1)
|
+--dot3adAggPort(2)
|
+--dot3adTablesLastChanged(3)
dot3adAgg group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| dot3adAggTable | 1.2.840.10006.300.43.1.1.1 | N/A | LACP information table for system | |||
| dot3adAggEntry | 1.2.840.10006.300.43.1.1.1.1 | N/A | INDEX ・dot3adAggIndex | |||
| dot3adAggIndex | 1.2.840.10006.300.43.1.1.1.1.1 | N/A | InterfaceIndex | LACP logical interface number | ||
| dot3adAggMACAddress | 1.2.840.10006.300.43.1.1.1.1.2 | R/O | MacAddress | MAC address for LACP logical interface | ||
| dot3adAggActorSystemPriority | 1.2.840.10006.300.43.1.1.1.1.3 | R/NW | INTEGER (1..65535) Note: Although this is INTEGER (0..65535) as per the standards, on this product it is in the range of INTEGER (1..65535) Same applies to other priority-related lagMIB | LACP system priority for this device | ||
| dot3adAggActorSystemID | 1.2.840.10006.300.43.1.1.1.1.4 | R/NW | MacAddress | LACP system ID for the device itself | ||
| dot3adAggAggregateOrIndividual | 1.2.840.10006.300.43.1.1.1.1.5 | R/O | TruthValue | Whether operating as Aggregate (true) or as individual links (alternate waiting ports) (false) | ||
| dot3adAggActorAdminKey | 1.2.840.10006.300.43.1.1.1.1.6 | R/NW | LacpKey | ADMIN Key (identifier ID for the LACP logical interface) used in managing this device “Used in managing” means the setting values for ADMIN properties or the config value. Same applies to other lagMIB | ||
| dot3adAggActorOperKey | 1.2.840.10006.300.43.1.1.1.1.7 | R/O | LacpKey | ADMIN Key (identifier ID for the LACP logical interface) used in operation, for this device “Used in operating” means the current values of the current operation, which are exchanged by the LACP protocol. Same applies to other lagMIB | ||
| dot3adAggPartnerSystemID | 1.2.840.10006.300.43.1.1.1.1.8 | R/O | MacAddress | LACP system ID of the opposing device | ||
| dot3adAggPartnerSystemPriority | 1.2.840.10006.300.43.1.1.1.1.9 | R/O | INTEGER (1..65535) | LACP system priority for the opposing device | ||
| dot3adAggPartnerOperKey | 1.2.840.10006.300.43.1.1.1.1.10 | R/O | LacpKey | ADMIN Key (identifier ID for the LACP logical interface) used in operation, for the opposing device | ||
| dot3adAggCollectorMaxDelay | 1.2.840.10006.300.43.1.1.1.1.11 | R/NW | INTEGER (0..65535) | Delay time from when the LACP packet is received to the time it is reflected in operation | ||
| dot3adAggPortListTable | 1.2.840.10006.300.43.1.1.2 | N/A | LACP port list table for the system | |||
| dot3adAggPortListEntry | 1.2.840.10006.300.43.1.1.2.1 | N/A | INDEX ・dot3adAggIndex | |||
| dot3adAggPortListPorts | 1.2.840.10006.300.43.1.1.2.1.1 | R/O | PortList | List of ports used by the LACP. Shown as an interface (port) bitmap. | ||
dot3adAggPort group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| dot3adAggPortTable | 1.2.840.10006.300.43.1.2.1 | N/A | Table of information for ports used by the LACP | |||
| dot3adAggPortEntry | 1.2.840.10006.300.43.1.2.1.1 | N/A | INDEX ・dot3adAggPortIndex | |||
| dot3adAggPortIndex | 1.2.840.10006.300.43.1.2.1.1.1 | N/A | InterfaceIndex | Port interface number | ||
| dot3adAggPortActorSystemPriority | 1.2.840.10006.300.43.1.2.1.1.2 | R/NW | INTEGER (1..65535) | LACP system priority for this device | ||
| dot3adAggPortActorSystemID | 1.2.840.10006.300.43.1.2.1.1.3 | R/O | MacAddress | LACP system ID for the device itself | ||
| dot3adAggPortActorAdminKey | 1.2.840.10006.300.43.1.2.1.1.4 | R/NW | LacpKey | ADMIN Key (identifier ID for the LACP logical interface) used in managing this device | ||
| dot3adAggPortActorOperKey | 1.2.840.10006.300.43.1.2.1.1.5 | R/NW | LacpKey | ADMIN Key (identifier ID for the LACP logical interface) used in operation, for this device | ||
| dot3adAggPortPartnerAdminSystemPriority | 1.2.840.10006.300.43.1.2.1.1.6 | R/NW | INTEGER (1..65535) | LACP system priority used in management, for the opposing device | ||
| dot3adAggPortPartnerOperSystemPriority | 1.2.840.10006.300.43.1.2.1.1.7 | R/O | INTEGER (1..65535) | LACP system priority used in operation, for the opposing device | ||
| dot3adAggPortPartnerAdminSystemID | 1.2.840.10006.300.43.1.2.1.1.8 | R/NW | MacAddress | LACP system ID used in management, for the opposing device | ||
| dot3adAggPortPartnerOperSystemID | 1.2.840.10006.300.43.1.2.1.1.9 | R/O | MacAddress | LACP system ID used in operation, for the opposing device | ||
| dot3adAggPortPartnerAdminKey | 1.2.840.10006.300.43.1.2.1.1.10 | R/NW | LacpKey | ADMIN Key (identifier ID for the LACP logical interface) used in management, for the opposing device | ||
| dot3adAggPortPartnerOperKey | 1.2.840.10006.300.43.1.2.1.1.11 | R/O | LacpKey | ADMIN Key (identifier ID for the LACP logical interface) used in operation, for the opposing device | ||
| dot3adAggPortSelectedAggID | 1.2.840.10006.300.43.1.2.1.1.12 | R/O | InterfaceIndex | Logical interface number selected by the port | ||
| dot3adAggPortAttachedAggID | 1.2.840.10006.300.43.1.2.1.1.13 | R/O | InterfaceIndex | Logical interface number connected to the port | ||
| dot3adAggPortActorPort | 1.2.840.10006.300.43.1.2.1.1.14 | R/O | INTEGER (0..65535) | Physical interface number of this device | ||
| dot3adAggPortActorPortPriority | 1.2.840.10006.300.43.1.2.1.1.15 | R/NW | INTEGER (0..65535) | Port priority for physical interface of this device | ||
| dot3adAggPortPartnerAdminPort | 1.2.840.10006.300.43.1.2.1.1.16 | R/NW | INTEGER (0..65535) | Physical interface number used in management, for the opposing device | ||
| dot3adAggPortPartnerOperPort | 1.2.840.10006.300.43.1.2.1.1.17 | R/O | INTEGER (0..65535) | Physical interface number used in operation, for the opposing device | ||
| dot3adAggPortPartnerAdminPortPriority | 1.2.840.10006.300.43.1.2.1.1.18 | R/NW | INTEGER (1..65535) | Port priority of physical interface used in management, for the opposing device | ||
| dot3adAggPortPartnerOperPortPriority | 1.2.840.10006.300.43.1.2.1.1.19 | R/O | INTEGER (1..65535) | Port priority for physical interface used in operation, for the opposing device | ||
| dot3adAggPortActorAdminState | 1.2.840.10006.300.43.1.2.1.1.20 | R/NW | LacpState | Actor_State used in management, for this device ActorState is a status variable that shows internal transitions | ||
| dot3adAggPortActorOperState | 1.2.840.10006.300.43.1.2.1.1.21 | R/O | LacpState | Actor_State used in operation, for this device | ||
| dot3adAggPortPartnerAdminState | 1.2.840.10006.300.43.1.2.1.1.22 | R/NW | LacpState | Actor_State used in management, for the opposing device | ||
| dot3adAggPortPartnerOperState | 1.2.840.10006.300.43.1.2.1.1.23 | R/O | LacpState | Actor_State used in operation, for the opposing device | ||
| dot3adAggPortAggregateOrIndividual | 1.2.840.10006.300.43.1.2.1.1.24 | R/O | TruthValue | Whether Aggregate (true), or individual physical interfaces (alternate waiting ports) (false) | ||
| dot3adAggPortStatsTable | 1.2.840.10006.300.43.1.2.2 | N/A | Table of statistical information for ports used by the LACP | |||
| dot3adAggPortStatsEntry | 1.2.840.10006.300.43.1.2.2.1 | N/A | INDEX ・dot3adAggPortIndex | |||
| dot3adAggPortStatsLACPDUsRx | 1.2.840.10006.300.43.1.2.2.1.1 | R/O | Counter32 | No. of correct LACPDU received by the physical interface | ||
| dot3adAggPortStatsMarkerPDUsRx | 1.2.840.10006.300.43.1.2.2.1.2 | R/O | Counter32 | No. of correct marker frames received by the physical interface | ||
| dot3adAggPortStatsMarkerResponsePDUsRx | 1.2.840.10006.300.43.1.2.2.1.3 | R/O | Counter32 | No. of correct marker response frames received by the physical interface | ||
| dot3adAggPortStatsUnknownRx | 1.2.840.10006.300.43.1.2.2.1.4 | R/O | Counter32 | No. of unknown frames received by the physical interface | ||
| dot3adAggPortStatsIllegalRx | 1.2.840.10006.300.43.1.2.2.1.5 | R/O | Counter32 | No. of frames received by the physical interface on which the EtherType was 0x8809 but the PDU was invalid | ||
| dot3adAggPortStatsLACPDUsTx | 1.2.840.10006.300.43.1.2.2.1.6 | R/O | Counter32 | No. of LACPDU transmitted from physical interface | ||
| dot3adAggPortStatsMarkerPDUsTx | 1.2.840.10006.300.43.1.2.2.1.7 | R/O | Counter32 | No. of marker frames transmitted from physical interface | ||
| dot3adAggPortStatsMarkerResponsePDUsTx | 1.2.840.10006.300.43.1.2.2.1.8 | R/O | Counter32 | No. of marker response frames transmitted from physical interface | ||
| dot3adAggPortDebugTable | 1.2.840.10006.300.43.1.2.3 | N/A | Debug information table for ports used by the LACP | |||
| dot3adAggPortDebugEntry | 1.2.840.10006.300.43.1.2.3.1 | N/A | INDEX ・dot3adAggPortIndex | |||
| dot3adAggPortDebugRxState | 1.2.840.10006.300.43.1.2.3.1.1 | R/O | INTEGER ・current(1) ・expired(2) ・defaulted(3) ・initialize(4) ・lacpDisabled(5) ・portDisabled(6) | Status of LACP protocol “Receive machine” transition variable | ||
| dot3adAggPortDebugLastRxTime | 1.2.840.10006.300.43.1.2.3.1.2 | R/O | TimeTicks | Internal time when logical interface last received data | ||
| dot3adAggPortDebugMuxState | 1.2.840.10006.300.43.1.2.3.1.3 | R/O | INTEGER ・detached(1) ・waiting(2) ・attached(3) ・collecting(4) ・distributing(5) ・collecting_distributing(6) | Status of LACP protocol “Mux machine” transition variable | ||
| dot3adAggPortDebugMuxReason | 1.2.840.10006.300.43.1.2.3.1.4 | R/O | DisplayString | Reason why most recent LACP protocol “Mux machine” transition variable was changed | ||
| dot3adAggPortDebugActorChurnState | 1.2.840.10006.300.43.1.2.3.1.5 | R/O | ChurnState | Status of “Churn Detection” transition variable for LACP protocol of this device | ||
| dot3adAggPortDebugPartnerChurnState | 1.2.840.10006.300.43.1.2.3.1.6 | R/O | ChurnState | Status of LACP protocol “Churn Detection” transition variable for the opposing device | ||
| dot3adAggPortDebugActorChurnCount | 1.2.840.10006.300.43.1.2.3.1.7 | R/O | Counter32 | No. of times that the LACP protocol “Churn Detection” status variable changed to ACTOR_CHURN status | ||
| dot3adAggPortDebugPartnerChurnCount | 1.2.840.10006.300.43.1.2.3.1.8 | R/O | Counter32 | No. of times that LACP protocol “Churn Detection” status variable changed to PARTNER_CHURN status | ||
| dot3adAggPortDebugActorSyncTransitionCount | 1.2.840.10006.300.43.1.2.3.1.9 | R/O | Counter32 | No. of times that LACP protocol “Mux machine” status variable of this device changed to IN_SYNC status | ||
| dot3adAggPortDebugPartnerSyncTransitionCount | 1.2.840.10006.300.43.1.2.3.1.10 | R/O | Counter32 | No. of times that the LACP protocol “Mux machine” status variable of the opposing device changed to IN_SYNC status | ||
| dot3adAggPortDebugActorChangeCount | 1.2.840.10006.300.43.1.2.3.1.11 | R/O | Counter32 | No. of times that the LAG ID of this device was changed | ||
| dot3adAggPortDebugPartnerChangeCount | 1.2.840.10006.300.43.1.2.3.1.12 | R/O | Counter32 | No. of times that the LAG ID of the opposing device was changed | ||
dot3adTablesLastChanged group
| MIB name | OID | Access | Syntax | Description |
|---|---|---|---|---|
| dot3adTablesLastChanged | 1.2.840.10006.300.43.1.3 | R/O | TimeTicks | Most recent time in which Dot3adAggTable, dot3adAggPortListTable, and dot3adAggPortTable was changed Note: This is always “0” on this product |
4.3 system group
This MIB is related to system information.
system group
| MIB name | OID | Access | Syntax | Description |
|---|---|---|---|---|
| sysDescr | 1.3.6.1.2.1.1.1 | R/O | DisplayString (SIZE (0..255)) | The description of the device. Device name and firmware revision |
| sysObjectID | 1.3.6.1.2.1.1.2 | R/O | OBJECT IDENTIFIER | Device OID that is defined by Yamaha’s private MIB |
| sysUpTimeInstance | 1.3.6.1.2.1.1.3 | R/O | TimeTicks | Elapsed time from boot |
| sysContact | 1.3.6.1.2.1.1.4 | R/W | DisplayString (SIZE (0..255)) | Administrator contact information Setting value for snmp-server contact command |
| sysName | 1.3.6.1.2.1.1.5 | R/W | DisplayString (SIZE (0..255)) | Administrative name Setting value for hostname command |
| sysLocation | 1.3.6.1.2.1.1.6 | R/W | DisplayString (SIZE (0..255)) | Device location Setting value for snmp-server location command |
| sysServices | 1.3.6.1.2.1.1.7 | R/O | INTEGER (0..127) | Value that indicates services the device supports |
4.4 interface group
This MIB is related to interface information.
interface group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| ifNumber | 1.3.6.1.2.1.2.1 | R/O | Integer32 | No. of interfaces | ||
| ifTable | 1.3.6.1.2.1.2.2 | N/A | Interface information table | |||
| ifEntry | 1.3.6.1.2.1.2.2.1 | N/A | INDEX ・ifIndex | |||
| ifIndex | 1.3.6.1.2.1.2.2.1.1 | R/O | InterfaceIndex | Interface ID number | ||
| ifDescr | 1.3.6.1.2.1.2.2.1.2 | R/O | DisplayString (SIZE (0..255)) | Description of the interface. Interface name If the description command is set in the interface, that value will be used | ||
| ifType | 1.3.6.1.2.1.2.2.1.3 | R/O | IANAifType ・ethernetCsmacd(6) ・l3ipvlan(136), others | Types of interfaces | ||
| ifMtu | 1.3.6.1.2.1.2.2.1.4 | R/O | Integer32 | Maximum frame size that can be transmitted/received | ||
| ifSpeed | 1.3.6.1.2.1.2.2.1.5 | R/O | Gauge32 | Interface speed | ||
| ifPhysAddress | 1.3.6.1.2.1.2.2.1.6 | R/O | PhysAddress | MAC address | ||
| ifAdminStatus | 1.3.6.1.2.1.2.2.1.7 | R/W | INTEGER ・up(1) ・down(2) | Desirable interface status | ||
| ifOperStatus | 1.3.6.1.2.1.2.2.1.8 | R/O | INTEGER ・up(1) ・down(2) | Current status of interface | ||
| ifLastChange | 1.3.6.1.2.1.2.2.1.9 | R/O | TimeTicks | Time when the interface changed to the current status (time elapsed time from boot) | ||
| ifInOctets | 1.3.6.1.2.1.2.2.1.10 | R/O | Counter32 | Total no. of octets received | ||
| ifInUcastPkts | 1.3.6.1.2.1.2.2.1.11 | R/O | Counter32 | No. of unicast packets notified to higher protocol | ||
| ifInNUcastPkts | 1.3.6.1.2.1.2.2.1.12 | R/O | Counter32 | Number of non-unicast packets notified to higher protocol | ||
| ifInDiscards | 1.3.6.1.2.1.2.2.1.13 | R/O | Counter32 | No. of packets that were discarded, despite no errors detected | ||
| ifInErrors | 1.3.6.1.2.1.2.2.1.14 | R/O | Counter32 | No. of packets not notified to higher protocol due to errors | ||
| ifInUnknownProtos | 1.3.6.1.2.1.2.2.1.15 | R/O | Counter32 | No. of discarded packets, due to an unsupported protocol | ||
| ifOutOctets | 1.3.6.1.2.1.2.2.1.16 | R/O | Counter32 | Total no. of octets transmitted | ||
| ifOutUcastPkts | 1.3.6.1.2.1.2.2.1.17 | R/O | Counter32 | No. of unicast packets requested for transmission by a higher protocol | ||
| ifOutNUcastPkts | 1.3.6.1.2.1.2.2.1.18 | R/O | Counter32 | No. of non-unicast packets requested for transmission by a higher protocol | ||
| ifOutDiscards | 1.3.6.1.2.1.2.2.1.19 | R/O | Counter32 | No. of packets that were discarded for transmission, despite no errors detected | ||
| ifOutErrors | 1.3.6.1.2.1.2.2.1.20 | R/O | Counter32 | No. of packets not transmitted due to errors | ||
| ifSpecific | 1.3.6.1.2.1.2.2.1.22 | R/O | OBJECT IDENTIFIER | Reference to MIB that defines interface media characteristics If no reference exists, this will be 0.0 | ||
4.5 at group
This MIB is related to mapping information for physical addresses and network addresses.
at group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| atTable | 1.3.6.1.2.1.3.1 | N/A | Table of mapping information for physical addresses and network addresses | |||
| atEntry | 1.3.6.1.2.1.3.1.1 | N/A | INDEX ・atIfIndex ・atNetAddress | |||
| atIfIndex | 1.3.6.1.2.1.3.1.1.1 | R/NW | INTEGER | ifIndex for the corresponding interface | ||
| atPhysAddress | 1.3.6.1.2.1.3.1.1.2 | R/NW | PhysAddress | Physical address | ||
| atNetAddress | 1.3.6.1.2.1.3.1.1.3 | R/NW | NetworkAddress | IP address corresponding to the physical address | ||
4.6 rmon group
This MIB is related to RMON information.
The syntax defined in the rmon group is shown below.
Syntax defined in the rmon group
| Syntax | Definition |
|---|---|
| OwnerString | OCTET STRING (SIZE (0..127)) |
| EntryStatus | INTEGER ・valid(1) ・createRequest(2) ・underCreation(3) ・invalid(4) |
The rmon group is divided into subgroups such as those shown below.
rmon(16)
|
+--statistics(1)
|
+--history(2)
|
+--alarm(3)
|
+--event(9)
statistics group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| etherStatsTable | 1.3.6.1.2.1.16.1.1 | N/A | Table of statistical information for Ethernet | |||
| etherStatsEntry | 1.3.6.1.2.1.16.1.1.1 | N/A | INDEX ・etherStatsIndex | |||
| etherStatsIndex | 1.3.6.1.2.1.16.1.1.1.1 | R/O | Integer32 (1..65535) | Index of entries | ||
| etherStatsDataSource | 1.3.6.1.2.1.16.1.1.1.2 | R/C | OBJECT IDENTIFIER | Interface being monitored | ||
| etherStatsDropEvents | 1.3.6.1.2.1.16.1.1.1.3 | R/O | Counter32 | Number of packets dropped | ||
| etherStatsOctets | 1.3.6.1.2.1.16.1.1.1.4 | R/O | Counter32 | Number of octets received | ||
| etherStatsPkts | 1.3.6.1.2.1.16.1.1.1.5 | R/O | Counter32 | Number of packets received | ||
| etherStatsBroadcastPkts | 1.3.6.1.2.1.16.1.1.1.6 | R/O | Counter32 | Number of broadcast packets received | ||
| etherStatsMulticastPkts | 1.3.6.1.2.1.16.1.1.1.7 | R/O | Counter32 | Number of multicast packets received | ||
| etherStatsCRCAlignErrors | 1.3.6.1.2.1.16.1.1.1.8 | R/O | Counter32 | Number of FCS error packets received | ||
| etherStatsUndersizePkts | 1.3.6.1.2.1.16.1.1.1.9 | R/O | Counter32 | Number of undersize packets received (packets smaller than 64 octets) | ||
| etherStatsOversizePkts | 1.3.6.1.2.1.16.1.1.1.10 | R/O | Counter32 | Number of oversize packets received (packets larger than 1518 octets) | ||
| etherStatsFragments | 1.3.6.1.2.1.16.1.1.1.11 | R/O | Counter32 | Number of fragment packets received (packets smaller than 64 octets with abnormal FCS) | ||
| etherStatsJabbers | 1.3.6.1.2.1.16.1.1.1.12 | R/O | Counter32 | Number of jabber packets received (packets larger than 1518 octets with abnormal FCS) | ||
| etherStatsCollisions | 1.3.6.1.2.1.16.1.1.1.13 | R/O | Counter32 | Number of collisions | ||
| etherStatsOwner | 1.3.6.1.2.1.16.1.1.1.20 | R/C | OwnerString | Name of owner | ||
| etherStatsStatus | 1.3.6.1.2.1.16.1.1.1.21 | R/C | EntryStatus | Status of statistical group | ||
history group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| historyControlTable | 1.3.6.1.2.1.16.2.1 | N/A | Table of control information for the history group | |||
| historyControlEntry | 1.3.6.1.2.1.16.2.1.1 | N/A | INDEX ・historyControlIndex | |||
| historyControlIndex | 1.3.6.1.2.1.16.2.1.1.1 | R/O | Integer32 (1..65535) | Index of entries | ||
| historyControlDataSource | 1.3.6.1.2.1.16.2.1.1.2 | R/C | OBJECT IDENTIFIER | Interface being monitored | ||
| historyControlBucketsRequested | 1.3.6.1.2.1.16.2.1.1.3 | R/C | Integer32 (1..65535) | Number of history group history saves requested | ||
| historyControlBucketsGranted | 1.3.6.1.2.1.16.2.1.1.4 | R/O | Integer32 (1..65535) | Number of history group histories saved | ||
| historyControlInterval | 1.3.6.1.2.1.16.2.1.1.5 | R/C | Integer32 (1..3600) | Interval at which history group histories are saved | ||
| historyControlOwner | 1.3.6.1.2.1.16.2.1.1.6 | R/C | OwnerString | Name of owner | ||
| historyControlStatus | 1.3.6.1.2.1.16.2.1.1.7 | R/C | EntryStatus | History group status | ||
| etherHistoryTable | 1.3.6.1.2.1.16.2.2 | N/A | Table of history information | |||
| etherHistoryEntry | 1.3.6.1.2.1.16.2.2.1 | N/A | INDEX ・etherHistoryIndex ・etherHistorySampleIndex | |||
| etherHistoryIndex | 1.3.6.1.2.1.16.2.2.1.1 | R/O | Integer32 (1..65535) | Same value as the index value of historyControlIndex | ||
| etherHistorySampleIndex | 1.3.6.1.2.1.16.2.2.1.2 | R/O | Integer32 (1..2147483647) | Index of history entries | ||
| etherHistoryIntervalStart | 1.3.6.1.2.1.16.2.2.1.3 | R/O | TimeTicks | Interval at which history group histories are saved | ||
| etherHistoryDropEvents | 1.3.6.1.2.1.16.2.2.1.4 | R/O | Counter32 | Number of packets dropped | ||
| etherHistoryOctets | 1.3.6.1.2.1.16.2.2.1.5 | R/O | Counter32 | Number of octets received | ||
| etherHistoryPkts | 1.3.6.1.2.1.16.2.2.1.6 | R/O | Counter32 | Number of packets received | ||
| etherHistoryBroadcastPkts | 1.3.6.1.2.1.16.2.2.1.7 | R/O | Counter32 | Number of broadcast packets received | ||
| etherHistoryMulticastPkts | 1.3.6.1.2.1.16.2.2.1.8 | R/O | Counter32 | Number of multicast packets received | ||
| etherHistoryCRCAlignErrors | 1.3.6.1.2.1.16.2.2.1.9 | R/O | Counter32 | Number of FCS error packets received | ||
| etherHistoryUndersizePkts | 1.3.6.1.2.1.16.2.2.1.10 | R/O | Counter32 | Number of undersize packets received (packets smaller than 64 octets) | ||
| etherHistoryOversizePkts | 1.3.6.1.2.1.16.2.2.1.11 | R/O | Counter32 | Number of oversize packets received (packets larger than 1518 octets) | ||
| etherHistoryFragments | 1.3.6.1.2.1.16.2.2.1.12 | R/O | Counter32 | Number of fragment packets received (packets smaller than 64 octets with abnormal FCS) | ||
| etherHistoryJabbers | 1.3.6.1.2.1.16.2.2.1.13 | R/O | Counter32 | Number of jabber packets received (packets larger than 1518 octets with abnormal FCS) | ||
| etherHistoryCollisions | 1.3.6.1.2.1.16.2.2.1.14 | R/O | Counter32 | Number of collisions | ||
| etherHistoryUtilization | 1.3.6.1.2.1.16.2.2.1.15 | R/O | Integer32 (0..10000) | Estimated value of network usage ratio | ||
alarm group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| alarmTable | 1.3.6.1.2.1.16.3.1 | N/A | Table of information for the alarm group | |||
| alarmEntry | 1.3.6.1.2.1.16.3.1.1 | N/A | INDEX ・alarmIndex | |||
| alarmIndex | 1.3.6.1.2.1.16.3.1.1.1 | R/O | Integer32 (1..65535) | Index of entries | ||
| alarmInterval | 1.3.6.1.2.1.16.3.1.1.2 | R/C | Integer32 | Sampling interval | ||
| alarmVariable | 1.3.6.1.2.1.16.3.1.1.3 | R/C | OBJECT IDENTIFIER | MIB object to be monitored | ||
| alarmSampleType | 1.3.6.1.2.1.16.3.1.1.4 | R/C | INTEGER ・absoluteValue(1) ・deltaValue(2) | Sampling type | ||
| alarmValue | 1.3.6.1.2.1.16.3.1.1.5 | R/O | Integer32 | Estimated value | ||
| alarmStartupAlarm | 1.3.6.1.2.1.16.3.1.1.6 | R/C | INTEGER ・risingAlarm(1) ・fallingAlarm(2) ・risingOrFallingAlarm(3) | Threshold value used for first alarm determination | ||
| alarmRisingThreshold | 1.3.6.1.2.1.16.3.1.1.7 | R/C | Integer32 | Upper threshold value | ||
| alarmFallingThreshold | 1.3.6.1.2.1.16.3.1.1.8 | R/C | Integer32 | Lower threshold value | ||
| alarmRisingEventIndex | 1.3.6.1.2.1.16.3.1.1.9 | R/C | Integer32 (0..65535) | Event index when crossing upper limit | ||
| alarmFallingEventIndex | 1.3.6.1.2.1.16.3.1.1.10 | R/C | Integer32 (0..65535) | Event index when crossing lower limit | ||
| alarmOwner | 1.3.6.1.2.1.16.3.1.1.11 | R/C | OwnerString | Name of owner | ||
| alarmStatus | 1.3.6.1.2.1.16.3.1.1.12 | R/C | EntryStatus | Alarm group status | ||
event group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| eventTable | 1.3.6.1.2.1.16.9.1 | N/A | Table of information for event group | |||
| eventEntry | 1.3.6.1.2.1.16.9.1.1 | N/A | INDEX ・eventIndex | |||
| eventIndex | 1.3.6.1.2.1.16.9.1.1.1 | R/O | Integer32 (1..65535) | Index of entries | ||
| eventDescription | 1.3.6.1.2.1.16.9.1.1.2 | R/C | DisplayString (SIZE (0..127)) | Event description | ||
| eventType | 1.3.6.1.2.1.16.9.1.1.3 | R/C | INTEGER ・none(1) ・log(2) ・snmptrap(3) ・logandtrap(4) | Event type | ||
| eventCommunity | 1.3.6.1.2.1.16.9.1.1.4 | R/C | OCTET STRING (SIZE (0..127)) | Community name | ||
| eventLastTimeSent | 1.3.6.1.2.1.16.9.1.1.5 | R/O | TimeTicks | Event execution time | ||
| eventOwner | 1.3.6.1.2.1.16.9.1.1.6 | R/C | OwnerString | Name of owner | ||
| eventStatus | 1.3.6.1.2.1.16.9.1.1.7 | R/C | EntryStatus | Event group status | ||
4.7 dot1dBridge group
This MIB is related to dot1dBridge information.
The syntax defined in the dot1dBridge group is shown below.
Syntax defined in the dot1dBridge group
| Syntax | Definition |
|---|---|
| BridgeId | OCTET STRING (SIZE (8)) |
| Timeout | Integer32 |
| PortList | OCTET STRING |
| VlanIndex | Unsigned32 |
| VlanId | Integer32 (1..4094) |
The dot1dBridge group is divided into subgroups such as those shown below.
dot1dBridge(17)
|
+--dot1dBase(1)
|
+--dot1dStp(2)
|
+--dot1dTp(4)
|
+--dot1dStatic(5)
|
+--qBridgeMIB(7)
|
+--qBridgeMIBObjects(1)
|
+--dot1qBase(1)
|
+--dot1qTp(2)
|
+--dot1qVlan(4)
dot1dBase group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| dot1dBaseBridgeAddress | 1.3.6.1.2.1.17.1.1 | R/O | MacAddress | MAC address of bridge | ||
| dot1dBaseNumPorts | 1.3.6.1.2.1.17.1.2 | R/O | Integer32 | No. of ports for bridge | ||
| dot1dBaseType | 1.3.6.1.2.1.17.1.3 | R/O | INTEGER ・unknown(1) ・transparent-only(2) ・sourceroute-only(3) ・srt(4) | Type of bridging executable by the bridge | ||
| dot1dBasePortTable | 1.3.6.1.2.1.17.1.4 | N/A | Table of port information for bridge | |||
| dot1dBasePortEntry | 1.3.6.1.2.1.17.1.4.1 | N/A | INDEX ・dot1dBasePort | |||
| dot1dBasePort | 1.3.6.1.2.1.17.1.4.1.1 | R/O | Integer32 (1..65535) | Port number | ||
| dot1dBasePortIfIndex | 1.3.6.1.2.1.17.1.4.1.2 | R/O | InterfaceIndex | Instance value for ifIndex, defined by the IF-MIB of the interface corresponding to the port | ||
| dot1dBasePortCircuit | 1.3.6.1.2.1.17.1.4.1.3 | R/O | OBJECT IDENTIFIER | Identifier used when the value of dot1dBasePortIfIndex is the same port in the bridge | ||
| dot1dBasePortDelayExceededDiscards | 1.3.6.1.2.1.17.1.4.1.4 | R/O | Counter32 | No. of frames discarded at the port due to a bridge forwarding delay Note: This is always “0” on this product | ||
| dot1dBasePortMtuExceededDiscards | 1.3.6.1.2.1.17.1.4.1.5 | R/O | Counter32 | No. of frames discarded at the port due to excessive size Note: This is always “0” on this product | ||
dot1dStp group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| dot1dStpProtocolSpecification | 1.3.6.1.2.1.17.2.1 | R/O | INTEGER ・unknown(1) ・decLb100(2) ・ieee8021d(3) | Spanning tree protocol version | ||
| dot1dStpPriority | 1.3.6.1.2.1.17.2.2 | R/NW | Integer32 (0..65535) | Bridge priority value | ||
| dot1dStpTimeSinceTopologyChange | 1.3.6.1.2.1.17.2.3 | R/O | TimeTicks | Time elapsed since detecting a change in topology | ||
| dot1dStpTopChanges | 1.3.6.1.2.1.17.2.4 | R/O | Counter32 | No. of times a change in topology has been detected | ||
| dot1dStpDesignatedRoot | 1.3.6.1.2.1.17.2.5 | R/O | BridgeId | Root bridge identifier of spanning tree | ||
| dot1dStpRootCost | 1.3.6.1.2.1.17.2.6 | R/O | Integer32 | Path cost to root bridge | ||
| dot1dStpRootPort | 1.3.6.1.2.1.17.2.7 | R/O | Integer32 | Port number with the lowest cost from bridge to root bridge | ||
| dot1dStpMaxAge | 1.3.6.1.2.1.17.2.8 | R/O | Timeout | Maximum time elapsed for spanning tree protocol information (in units of 1/100 sec.) | ||
| dot1dStpHelloTime | 1.3.6.1.2.1.17.2.9 | R/O | Timeout | BPDU transmission interval (in units of 1/100 sec.) | ||
| dot1dStpHoldTime | 1.3.6.1.2.1.17.2.10 | R/O | Integer32 | Minimum transmission interval for Configuration BPDU (in units of 1/100 sec.) | ||
| dot1dStpForwardDelay | 1.3.6.1.2.1.17.2.11 | R/O | Timeout | Forward delay time (in units of 1/100 sec.) | ||
| dot1dStpBridgeMaxAge | 1.3.6.1.2.1.17.2.12 | R/NW | Timeout (600..4000) | Setting value for maximum elapsed time | ||
| dot1dStpBridgeHelloTime | 1.3.6.1.2.1.17.2.13 | R/NW | Timeout (100..1000) | Setting value for BPDU transmission interval | ||
| dot1dStpBridgeForwardDelay | 1.3.6.1.2.1.17.2.14 | R/NW | Timeout (400..3000) | Setting value for forward delay time | ||
| dot1dStpPortTable | 1.3.6.1.2.1.17.2.15 | N/A | Table of port information for spanning tree protocol | |||
| dot1dStpPortEntry | 1.3.6.1.2.1.17.2.15.1 | N/A | INDEX ・dot1dStpPort | |||
| dot1dStpPort | 1.3.6.1.2.1.17.2.15.1.1 | R/O | Integer32 (1..65535) | Port number for spanning tree protocol | ||
| dot1dStpPortPriority | 1.3.6.1.2.1.17.2.15.1.2 | R/NW | Integer32 (0..255) | Port priority value | ||
| dot1dStpPortState | 1.3.6.1.2.1.17.2.15.1.3 | R/O | INTEGER ・disabled(1) ・blocking(2) ・listening(3) ・learning(4) ・forwarding(5) ・broken(6) | Port status | ||
| dot1dStpPortEnable | 1.3.6.1.2.1.17.2.15.1.4 | R/NW | INTEGER ・enabled(1) ・disabled(2) | Port enabled/disabled status | ||
| dot1dStpPortPathCost | 1.3.6.1.2.1.17.2.15.1.5 | R/NW | Integer32 (1..65535) | Set path cost | ||
| dot1dStpPortDesignatedRoot | 1.3.6.1.2.1.17.2.15.1.6 | R/O | BridgeId | Root bridge identifier of configuration BPDU | ||
| dot1dStpPortDesignatedCost | 1.3.6.1.2.1.17.2.15.1.7 | R/O | Integer32 | Path cost value for specified port | ||
| dot1dStpPortDesignatedBridge | 1.3.6.1.2.1.17.2.15.1.8 | R/O | BridgeId | Specified port identifier | ||
| dot1dStpPortDesignatedPort | 1.3.6.1.2.1.17.2.15.1.9 | R/O | OCTET STRING (SIZE (2)) | Port identifier for specified bridge | ||
| dot1dStpPortForwardTransitions | 1.3.6.1.2.1.17.2.15.1.10 | R/O | Counter32 | No. of times that port switched from acquisition status to forwarding status | ||
| dot1dStpPortPathCost32 | 1.3.6.1.2.1.17.2.15.1.11 | R/NW | Integer32 (1..200000000) | Path cost value for ports complying with IEEE 802.1t | ||
| dot1dStpVersion | 1.3.6.1.2.1.17.2.16 | R/NW | INTEGER ・stpCompatible(0) ・rstp(2) | Spanning tree protocol version | ||
| dot1dStpTxHoldCount | 1.3.6.1.2.1.17.2.17 | R/NW | Integer32 (1..10) | Forward hold count value | ||
| dot1dStpExtPortTable | 1.3.6.1.2.1.17.2.19 | N/A | Table of port information for RSTP | |||
| dot1dStpExtPortEntry | 1.3.6.1.2.1.17.2.19.1 | N/A | AUGMENTS ・dot1dStpPortEntry | |||
| dot1dStpPortProtocolMigration | 1.3.6.1.2.1.17.2.19.1.1 | R/NW | TruthValue | Writing “true(1)” to this object will cause the BPDU of the port to be forcibly transmitted Note: This is always “false(2)” when read | ||
| dot1dStpPortAdminEdgePort | 1.3.6.1.2.1.17.2.19.1.2 | R/NW | TruthValue | Setting value for edge port | ||
| dot1dStpPortOperEdgePort | 1.3.6.1.2.1.17.2.19.1.3 | R/O | TruthValue | Current value for edge port | ||
| dot1dStpPortAdminPointToPoint | 1.3.6.1.2.1.17.2.19.1.4 | R/NW | INTEGER ・forceTrue(0) ・forceFalse(1) ・auto(2) | Setting value for point-to-point of the port | ||
| dot1dStpPortOperPointToPoint | 1.3.6.1.2.1.17.2.19.1.5 | R/O | TruthValue | Current value for point-to-point of the port | ||
| dot1dStpPortAdminPathCost | 1.3.6.1.2.1.17.2.19.1.6 | R/NW | Integer32 (0..200000000) | Setting value for path cost of port | ||
dot1dTp group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| dot1dTpLearnedEntryDiscards | 1.3.6.1.2.1.17.4.1 | R/O | Counter32 | Amount of forwarding information that was discarded due to having exceeded the upper save limit of the forwarding database | ||
| dot1dTpAgingTime | 1.3.6.1.2.1.17.4.2 | R/NW | Integer32 (10..1000000) | Timeout duration for aging out forwarding information that was actively acquired | ||
| dot1dTpFdbTable | 1.3.6.1.2.1.17.4.3 | N/A | Table of unicast entries that have forwarding or filtering information | |||
| dot1dTpFdbEntry | 1.3.6.1.2.1.17.4.3.1 | N/A | INDEX ・dot1dTpFdbAddress | |||
| dot1dTpFdbAddress | 1.3.6.1.2.1.17.4.3.1.1 | R/O | MacAddress | Unicast MAC addresses that have forwarding or filtering information | ||
| dot1dTpFdbPort | 1.3.6.1.2.1.17.4.3.1.2 | R/O | Integer32 | Port number of port that transmitted a frame with a source address that is the same as the instance value, corresponding to the dot1dTpFdbAddress | ||
| dot1dTpFdbStatus | 1.3.6.1.2.1.17.4.3.1.3 | R/O | INTEGE ・other(1) ・invalid(2) ・learned(3) ・self(4) ・mgmt(5) | MAC address table status | ||
| dot1dTpPortTable | 1.3.6.1.2.1.17.4.4 | N/A | Table for all port information that is associated with a transparent bridge | |||
| dot1dTpPortEntry | 1.3.6.1.2.1.17.4.4.1 | N/A | INDEX ・dot1dTpPort | |||
| dot1dTpPort | 1.3.6.1.2.1.17.4.4.1.1 | R/O | Integer32 (1..65535) | Port numbers that include transparent bridge management information | ||
| dot1dTpPortMaxInfo | 1.3.6.1.2.1.17.4.4.1.2 | R/O | Integer32 | Maximum size of information fields transmitted/received by a port | ||
| dot1dTpPortInFrames | 1.3.6.1.2.1.17.4.4.1.3 | R/O | Counter32 | No. of frames received by a port | ||
| dot1dTpPortOutFrames | 1.3.6.1.2.1.17.4.4.1.4 | R/O | Counter32 | No. of frames transmitted by a port | ||
| dot1dTpPortInDiscards | 1.3.6.1.2.1.17.4.4.1.5 | R/O | Counter32 | No. of frames that are valid for reception, which were discarded during forwarding | ||
dot1dStatic group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| dot1dStaticTable | 1.3.6.1.2.1.17.5.1 | N/A | Table of filtering information that was registered statically | |||
| dot1dStaticEntry | 1.3.6.1.2.1.17.5.1.1 | N/A | INDEX ・dot1dStaticAddress ・dot1dStaticReceivePort | |||
| dot1dStaticAddress | 1.3.6.1.2.1.17.5.1.1.1 | R/NC | MacAddress | Destination MAC address for which filtering information is applied | ||
| dot1dStaticReceivePort | 1.3.6.1.2.1.17.5.1.1.2 | R/NC | Integer32 (0..65535) | Reception port no. on which filtering information is applied | ||
| dot1dStaticAllowedToGoTo | 1.3.6.1.2.1.17.5.1.1.3 | R/NC | OCTET STRING (SIZE (0..512)) | Port no. on which filtering information was applied to a transmitted frame | ||
| dot1dStaticStatus | 1.3.6.1.2.1.17.5.1.1.4 | R/NC | INTEGER ・other(1) ・invalid(2) ・permanent(3) ・deleteOnReset(4) ・deleteOnTimeout(5) | Application status for filtering information | ||
dot1qBase group
| MIB name | OID | Access | Syntax | Description |
|---|---|---|---|---|
| dot1qVlanVersionNumber | 1.3.6.1.2.1.17.7.1.1.1 | R/O | INTEGER ・version1(1) | IEEE 802.1Q version information |
| dot1qMaxVlanId | 1.3.6.1.2.1.17.7.1.1.2 | R/O | VlanId | Maximum no. of IEEE 802.1Q VLAN IDs |
| dot1qMaxSupportedVlans | 1.3.6.1.2.1.17.7.1.1.3 | R/O | Unsigned32 | Maximum no. of IEEE 802.1Q VLANs |
| dot1qNumVlans | 1.3.6.1.2.1.17.7.1.1.4 | R/O | Unsigned32 | No. of IEEE 802.1Q VLANs used |
dot1qTp group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| dot1qFdbTable | 1.3.6.1.2.1.17.7.1.2.1 | N/A | Filtering table | |||
| dot1qFdbEntry | 1.3.6.1.2.1.17.7.1.2.1.1 | N/A | INDEX ・dot1qFdbId | |||
| dot1qFdbId | 1.3.6.1.2.1.17.7.1.2.1.1.1 | N/A | Unsigned32 | Identifier for filtering database | ||
| dot1qFdbDynamicCount | 1.3.6.1.2.1.17.7.1.2.1.1.2 | R/O | Counter32 | No. of active entries in filtering database | ||
| dot1qTpFdbTable | 1.3.6.1.2.1.17.7.1.2.2 | N/A | Table of information for unicast entries that have transparent bridge forwarding or filtering information | |||
| dot1qTpFdbEntry | 1.3.6.1.2.1.17.7.1.2.2.1 | N/A | INDEX ・dot1qFdbId ・dot1qTpFdbAddress | |||
| dot1qTpFdbAddress | 1.3.6.1.2.1.17.7.1.2.2.1.1 | N/A | MacAddress | Unicast MAC addresses that have transparent bridge forwarding or filtering information | ||
| dot1qTpFdbPort | 1.3.6.1.2.1.17.7.1.2.2.1.2 | R/O | Integer32 (0..65535) | Port number of port that transmitted a frame with a source address that is the same as the instance value, corresponding to the transparent bridge dot1qTpFdbAddress | ||
| dot1qTpFdbStatus | 1.3.6.1.2.1.17.7.1.2.2.1.3 | R/O | INTEGER ・other(1) ・invalid(2) ・learned(3) ・self(4) ・mgmt(5) | Transparent bridge MAC address table status | ||
dot1qVlan group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| dot1qVlanNumDeletes | 1.3.6.1.2.1.17.7.1.4.1 | R/O | Counter32 | No. of VLAN entries that were deleted | ||
| dot1qVlanCurrentTable | 1.3.6.1.2.1.17.7.1.4.2 | N/A | Table of VLAN entry information | |||
| dot1qVlanCurrentEntry | 1.3.6.1.2.1.17.7.1.4.2.1 | N/A | INDEX ・dot1qVlanTimeMark ・dot1qVlanIndex | |||
| dot1qVlanTimeMark | 1.3.6.1.2.1.17.7.1.4.2.1.1 | N/A | TimeFilter | Time filter for VLAN entries | ||
| dot1qVlanIndex | 1.3.6.1.2.1.17.7.1.4.2.1.2 | N/A | VlanIndex | VLAN ID | ||
| dot1qVlanFdbId | 1.3.6.1.2.1.17.7.1.4.2.1.3 | R/O | Unsigned32 | Filtering database used by VLAN | ||
| dot1qVlanCurrentEgressPorts | 1.3.6.1.2.1.17.7.1.4.2.1.4 | R/O | PortList | Set of ports that output VLAN traffic as untagged or tagged frames | ||
| dot1qVlanCurrentUntaggedPorts | 1.3.6.1.2.1.17.7.1.4.2.1.5 | R/O | PortList | Set of ports that transmit VLAN traffic as untagged frames | ||
| dot1qVlanStatus | 1.3.6.1.2.1.17.7.1.4.2.1.6 | R/O | INTEGER ・other(1) ・permanent(2) ・dynamicGvrp(3) | VLAN status | ||
| dot1qVlanCreationTime | 1.3.6.1.2.1.17.7.1.4.2.1.7 | R/O | TimeTicks | sysUpTime value when creating VLAN | ||
| dot1qVlanStaticTable | 1.3.6.1.2.1.17.7.1.4.3 | N/A | Table of VLAN static setting information | |||
| dot1qVlanStaticEntry | 1.3.6.1.2.1.17.7.1.4.3.1 | N/A | INDEX ・dot1qVlanIndex | |||
| dot1qVlanStaticName | 1.3.6.1.2.1.17.7.1.4.3.1.1 | R/NC | SnmpAdminString (SIZE (0..32)) | Name assigned to VLAN | ||
| dot1qVlanStaticEgressPorts | 1.3.6.1.2.1.17.7.1.4.3.1.2 | R/NC | PortList | Set of ports assigned to VLAN output list | ||
| dot1qVlanForbiddenEgressPorts | 1.3.6.1.2.1.17.7.1.4.3.1.3 | R/NC | PortList | Set of ports prohibited from being included in the VLAN output list | ||
| dot1qVlanStaticUntaggedPorts | 1.3.6.1.2.1.17.7.1.4.3.1.4 | R/NC | PortList | Set of ports that transmit VLAN output traffic as untagged frames | ||
| dot1qVlanStaticRowStatus | 1.3.6.1.2.1.17.7.1.4.3.1.5 | R/NC | RowStatus | VLAN entry status | ||
| dot1qNextFreeLocalVlanIndex | 1.3.6.1.2.1.17.7.1.4.4 | R/O | Integer32 (0|4096..2147483647) | Next VLAN ID that can be used | ||
| dot1qPortVlanTable | 1.3.6.1.2.1.17.7.1.4.5 | N/A | Table of VLAN setting information for each port | |||
| dot1qPortVlanEntry | 1.3.6.1.2.1.17.7.1.4.5.1 | N/A | AUGMENTS ・dot1dBasePortEntry | |||
| dot1qPvid | 1.3.6.1.2.1.17.7.1.4.5.1.1 | R/NW | VlanIndex | VLAN IDs assigned to untagged or priority tag frames | ||
| dot1qPortAcceptableFrameTypes | 1.3.6.1.2.1.17.7.1.4.5.1.2 | R/NW | INTEGER ・admitAll(1) ・admitOnlyVlanTagged(2) | Frame types permitted for reception on the port | ||
| dot1qPortIngressFiltering | 1.3.6.1.2.1.17.7.1.4.5.1.3 | R/NW | TruthValue | Filtering of received frames on a port | ||
4.8 ifMIB group
This MIB is related to additional information for the interface.
The ifMIB group is divided into subgroups such as those shown below.
ifMIB(31)
|
+--ifMIBObjects(1)
ifMIBObjects group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| ifXTable | 1.3.6.1.2.1.31.1.1 | N/A | Table of additional information for interface | |||
| ifXEntry | 1.3.6.1.2.1.31.1.1.1 | N/A | AUGMENTS ・ifEntry | |||
| ifHighSpeed | 1.3.6.1.2.1.31.1.1.1.15 | R/O | Gauge32 | The speed of the interface. Mbps | ||
4.9 lldpV2MIB group
This MIB is related to LLDP information.
The lldpV2MIB group is divided into subgroups such as those shown below.
lldpV2MIB(13)
|
+--lldpV2Objects(1)
|
+--lldpV2Configuration(1)
|
+--lldpV2Statistics(2)
|
+--lldpV2LocalSystemData(3)
|
+--lldpV2RemoteSystemsData(4)lldpV2Configuration group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| lldpV2PortConfigTable | 1.3.111.2.802.1.1.13.1.1.8 | N/A | Table for managing transmitted information for each port | |||
| lldpV2PortConfigEntry | 1.3.111.2.802.1.1.13.1.1.8.1 | N/A | INDEX ・lldpV2PortConfigIfIndex ・lldpV2PortConfigDestAddressIndex | |||
| lldpV2PortConfigIfIndex | 1.3.111.2.802.1.1.13.1.1.8.1.1 | N/A | InterfaceIndex | Index for each port | ||
| lldpV2PortConfigDestAddressIndex | 1.3.111.2.802.1.1.13.1.1.8.1.2 | N/A | LldpV2DestAddressTableIndex | Source MAC address index | ||
| lldpV2PortConfigAdminStatus | 1.3.111.2.802.1.1.13.1.1.8.1.3 | R/W | INTEGER ・txOnly(1) ・rxOnly(2) ・txAndRx(3) ・disabled(4) | LLDP transmission/reception status | ||
| lldpV2PortConfigNotificationEnable | 1.3.111.2.802.1.1.13.1.1.8.1.4 | R/W | TruthValue | LLDP notification status | ||
| lldpV2PortConfigTLVsTxEnable | 1.3.111.2.802.1.1.13.1.1.8.1.5 | R/W | BITS ・portDesc(0) ・sysName(1) ・sysDesc(2) ・sysCap(3) | Basic management TLV transmission item | ||
| lldpV2DestAddressTable | 1.3.111.2.802.1.1.13.1.1.9 | N/A | Table of MAC addresses used by LLDP | |||
| lldpV2DestAddressTableEntry | 1.3.111.2.802.1.1.13.1.1.9.1 | N/A | INDEX ・lldpV2AddressTableIndex | |||
| lldpV2AddressTableIndex | 1.3.111.2.802.1.1.13.1.1.9.1.1 | N/A | LldpV2DestAddressTableIndex | Source MAC address index | ||
| lldpV2DestMacAddress | 1.3.111.2.802.1.1.13.1.1.9.1.2 | R/O | MacAddress | MAC address used for LLDP transmission | ||
lldpV2Statistics group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| lldpV2StatsRemTablesLastChangeTime | 1.3.111.2.802.1.1.13.1.2.1 | R/O | TimeStamp | Time from system initialization until remote data update | ||
| lldpV2StatsRemTablesInserts | 1.3.111.2.802.1.1.13.1.2.2 | R/O | ZeroBasedCounter32 | Total number of entries added to device management table | ||
| lldpV2StatsRemTablesDeletes | 1.3.111.2.802.1.1.13.1.2.3 | R/O | ZeroBasedCounter32 | Total number of entries deleted from device management table | ||
| lldpV2StatsRemTablesDrops | 1.3.111.2.802.1.1.13.1.2.4 | R/O | ZeroBasedCounter32 | Total number of entries that could not be set to device management table | ||
| lldpV2StatsRemTablesAgeouts | 1.3.111.2.802.1.1.13.1.2.5 | R/O | ZeroBasedCounter32 | Total number of entries that exceeded TTL time (aged out) and were deleted from device management table | ||
| lldpV2StatsTxPortTable | 1.3.111.2.802.1.1.13.1.2.6 | N/A | Table of statistical information for LLDP transmission | |||
| lldpV2StatsTxPortEntry | 1.3.111.2.802.1.1.13.1.2.6.1 | N/A | INDEX ・lldpV2StatsTxIfInde ・lldpV2StatsTxDestMACAddress | |||
| lldpV2StatsTxIfIndex | 1.3.111.2.802.1.1.13.1.2.6.1.1 | N/A | InterfaceIndex | Port index | ||
| lldpV2StatsTxDestMACAddress | 1.3.111.2.802.1.1.13.1.2.6.1.2 | N/A | LldpV2DestAddressTableIndex | Source MAC address index | ||
| lldpV2StatsTxPortFramesTotal | 1.3.111.2.802.1.1.13.1.2.6.1.3 | R/O | Counter32 | Total number of LLDP frames transmitted | ||
| lldpV2StatsTxLLDPDULengthErrors | 1.3.111.2.802.1.1.13.1.2.6.1.4 | R/O | Counter32 | Total no. of LLDP frame length errors | ||
| lldpV2StatsRxPortTable | 1.3.111.2.802.1.1.13.1.2.7 | N/A | Table of statistical information for LLDP reception | |||
| lldpV2StatsRxPortEntry | 1.3.111.2.802.1.1.13.1.2.7.1 | N/A | INDEX ・lldpV2StatsRxDestIfIndex ・lldpV2StatsRxDestMACAddress | |||
| lldpV2StatsRxDestIfIndex | 1.3.111.2.802.1.1.13.1.2.7.1.1 | N/A | InterfaceIndex | Port index | ||
| lldpV2StatsRxDestMACAddress | 1.3.111.2.802.1.1.13.1.2.7.1.2 | N/A | LldpV2DestAddressTableIndex | Source MAC address index | ||
| lldpV2StatsRxPortFramesDiscardedTotal | 1.3.111.2.802.1.1.13.1.2.7.1.3 | R/O | Counter32 | Number of LLDP frames discarded | ||
| lldpV2StatsRxPortFramesErrors | 1.3.111.2.802.1.1.13.1.2.7.1.4 | R/O | Counter32 | Number of error frames received | ||
| lldpV2StatsRxPortFramesTotal | 1.3.111.2.802.1.1.13.1.2.7.1.5 | R/O | Counter32 | No. of LLDP frames received | ||
| lldpV2StatsRxPortTLVsDiscardedTotal | 1.3.111.2.802.1.1.13.1.2.7.1.6 | R/O | Counter32 | Number of LLDP frames discarded | ||
| lldpV2StatsRxPortTLVsUnrecognizedTotal | 1.3.111.2.802.1.1.13.1.2.7.1.7 | R/O | Counter32 | Number of unrecognized TLVs received | ||
| lldpV2StatsRxPortAgeoutsTotal | 1.3.111.2.802.1.1.13.1.2.7.1.8 | R/O | ZeroBasedCounter32 | Number of entries that aged-out | ||
lldpV2LocalSystemData group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| lldpV2LocChassisIdSubtype | 1.3.111.2.802.1.1.13.1.3.1 | R/O | LldpV2ChassisIdSubtype | Subtype of chassis ID | ||
| lldpV2LocChassisId | 1.3.111.2.802.1.1.13.1.3.2 | R/O | LldpV2ChassisId | Chassis ID | ||
| lldpV2LocSysName | 1.3.111.2.802.1.1.13.1.3.3 | R/O | SnmpAdminString (SIZE (0..255)) | System name | ||
| lldpV2LocSysDesc | 1.3.111.2.802.1.1.13.1.3.4 | R/O | SnmpAdminString (SIZE (0..255)) | System description | ||
| lldpV2LocSysCapSupported | 1.3.111.2.802.1.1.13.1.3.5 | R/O | LldpV2SystemCapabilitiesMap | Functions supported by the system | ||
| lldpV2LocSysCapEnabled | 1.3.111.2.802.1.1.13.1.3.6 | R/O | LldpV2SystemCapabilitiesMap | Functions enabled by the system | ||
| lldpV2LocPortTable | 1.3.111.2.802.1.1.13.1.3.7 | N/A | Table of local port information | |||
| lldpV2LocPortEntry | 1.3.111.2.802.1.1.13.1.3.7.1 | N/A | INDEX ・lldpV2LocPortIfIndex | |||
| lldpV2LocPortIfIndex | 1.3.111.2.802.1.1.13.1.3.7.1.1 | N/A | InterfaceIndex | Port index | ||
| lldpV2LocPortIdSubtype | 1.3.111.2.802.1.1.13.1.3.7.1.2 | R/O | LldpV2PortIdSubtype | Subtype of port ID | ||
| lldpV2LocPortId | 1.3.111.2.802.1.1.13.1.3.7.1.3 | R/O | LldpV2PortId | Port ID | ||
| lldpV2LocPortDesc | 1.3.111.2.802.1.1.13.1.3.7.1.4 | R/O | SnmpAdminString (SIZE (0..255)) | Port description | ||
lldpV2RemoteSystemsData group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| lldpV2RemTable | 1.3.111.2.802.1.1.13.1.4.1 | N/A | Table of information for connected remote devices | |||
| lldpV2RemEntry | 1.3.111.2.802.1.1.13.1.4.1.1 | N/A | INDEX ・lldpV2RemTimeMark ・lldpV2RemLocalIfIndex ・lldpV2RemLocalDestMACAddress ・lldpV2RemIndex | |||
| lldpV2RemTimeMark | 1.3.111.2.802.1.1.13.1.4.1.1.1 | N/A | TimeFilter | Time filter for lldpV2RemEntry | ||
| lldpV2RemLocalIfIndex | 1.3.111.2.802.1.1.13.1.4.1.1.2 | N/A | InterfaceIndex | Port index | ||
| lldpV2RemLocalDestMACAddress | 1.3.111.2.802.1.1.13.1.4.1.1.3 | N/A | LldpV2DestAddressTableIndex | Destination MAC address | ||
| lldpV2RemIndex | 1.3.111.2.802.1.1.13.1.4.1.1.4 | N/A | Unsigned32(1..2147483647) | Remote system index | ||
| lldpV2RemChassisIdSubtype | 1.3.111.2.802.1.1.13.1.4.1.1.5 | R/O | LldpV2ChassisIdSubtype | Subtype of chassis ID | ||
| lldpV2RemChassisId | 1.3.111.2.802.1.1.13.1.4.1.1.6 | R/O | LldpV2ChassisId | Chassis ID | ||
| lldpV2RemPortIdSubtype | 1.3.111.2.802.1.1.13.1.4.1.1.7 | R/O | LldpV2PortIdSubtype | Subtype of port ID | ||
| lldpV2RemPortId | 1.3.111.2.802.1.1.13.1.4.1.1.8 | R/O | LldpV2PortId | Port ID | ||
| lldpV2RemPortDesc | 1.3.111.2.802.1.1.13.1.4.1.1.9 | R/O | SnmpAdminString (SIZE (0..255)) | Port description | ||
| lldpV2RemSysName | 1.3.111.2.802.1.1.13.1.4.1.1.10 | R/O | SnmpAdminString (SIZE (0..255)) | System name | ||
| lldpV2RemSysDesc | 1.3.111.2.802.1.1.13.1.4.1.1.11 | R/O | SnmpAdminString (SIZE (0..255)) | System description | ||
| lldpV2RemSysCapSupported | 1.3.111.2.802.1.1.13.1.4.1.1.12 | R/O | LldpV2SystemCapabilitiesMap | Functions supported by the system | ||
| lldpV2RemSysCapEnabled | 1.3.111.2.802.1.1.13.1.4.1.1.13 | R/O | LldpV2SystemCapabilitiesMap | Functions enabled on the system | ||
| lldpV2RemRemoteChanges | 1.3.111.2.802.1.1.13.1.4.1.1.14 | R/O | TruthValue | Flag indicating that a change in the MIB occurred on the remote device | ||
| lldpV2RemTooManyNeighbors | 1.3.111.2.802.1.1.13.1.4.1.1.15 | R/O | TruthValue | Flag indicating that the number of connected remote devices exceeded the limit of the management table | ||
| lldpV2RemManAddrTable | 1.3.111.2.802.1.1.13.1.4.2 | N/A | Table of remote system management addresses | |||
| lldpV2RemManAddrEntry | 1.3.111.2.802.1.1.13.1.4.2.1 | N/A | INDEX ・lldpV2RemTimeMark ・lldpV2RemLocalIfIndex ・lldpV2RemLocalDestMACAddress ・lldpV2RemIndex ・lldpV2RemManAddrSubtype ・lldpV2RemManAddr | |||
| lldpV2RemManAddrSubtype | 1.3.111.2.802.1.1.13.1.4.2.1.1 | N/A | AddressFamilyNumbers | Sub-type for management address | ||
| lldpV2RemManAddr | 1.3.111.2.802.1.1.13.1.4.2.1.2 | N/A | LldpV2ManAddress | Remote system management addresses | ||
| lldpV2RemManAddrIfSubtype | 1.3.111.2.802.1.1.13.1.4.2.1.3 | R/O | LldpV2ManAddrIfSubtype | Interface sub-type | ||
| lldpV2RemManAddrIfId | 1.3.111.2.802.1.1.13.1.4.2.1.4 | R/O | Unsigned32 | Interface ID | ||
| lldpV2RemManAddrOID | 1.3.111.2.802.1.1.13.1.4.2.1.5 | R/O | OBJECT IDENTIFIER | OID of management interface | ||
| lldpV2RemUnknownTLVTable | 1.3.111.2.802.1.1.13.1.4.3 | N/A | Table of undefined TLV information | |||
| lldpV2RemUnknownTLVEntry | 1.3.111.2.802.1.1.13.1.4.3.1 | N/A | INDEX ・lldpV2RemTimeMark ・lldpV2RemLocalIfIndex ・lldpV2RemLocalDestMACAddress ・lldpV2RemIndex ・lldpV2RemUnknownTLVType | |||
| lldpV2RemUnknownTLVType | 1.3.111.2.802.1.1.13.1.4.3.1.1 | N/A | Unsigned32(9..126) | Undefined TLV types | ||
| lldpV2RemUnknownTLVInfo | 1.3.111.2.802.1.1.13.1.4.3.1.2 | R/O | OCTET STRING (SIZE (0..511)) | Information for undefined TLVs | ||
| lldpV2RemOrgDefInfoTable | 1.3.111.2.802.1.1.13.1.4.4 | N/A | Table for OUI information | |||
| lldpV2RemOrgDefInfoEntry | 1.3.111.2.802.1.1.13.1.4.4.1 | N/A | INDEX ・lldpV2RemTimeMark ・lldpV2RemLocalIfIndex ・lldpV2RemLocalDestMACAddress ・lldpV2RemIndex ・lldpV2RemOrgDefInfoOUI ・lldpV2RemOrgDefInfoSubtype ・lldpV2RemOrgDefInfoIndex | |||
| lldpV2RemOrgDefInfoOUI | 1.3.111.2.802.1.1.13.1.4.4.1.1 | N/A | OCTET STRING (SIZE (3)) | OUI information for remote system | ||
| lldpV2RemOrgDefInfoSubtype | 1.3.111.2.802.1.1.13.1.4.4.1.2 | N/A | Unsigned32(1..255) | OUI information sub-type for remote system | ||
| lldpV2RemOrgDefInfoIndex | 1.3.111.2.802.1.1.13.1.4.4.1.3 | N/A | Unsigned32(1..2147483647) | Index for OUI information and OUI information sub-types | ||
| lldpV2RemOrgDefInfo | 1.3.111.2.802.1.1.13.1.4.4.1.4 | R/O | OCTET STRING (SIZE (0..507)) | Information defined for each organization | ||
5 Private MIB
The private MIBs that are supported by this product are shown below.
5.1 yamahaSWHardware group
This MIB is related to hardware information for Yamaha switches.
yamahaSWHardware group
| MIB name | OID | Access | Syntax | Description |
|---|---|---|---|---|
| yshMemorySize | 1.3.6.1.4.1.1182.3.1.2 | R/O | INTEGER | Memory size |
| yshFlashROMSize | 1.3.6.1.4.1.1182.3.1.3 | R/O | INTEGER | FlashROM size |
| yshMemoryUtil | 1.3.6.1.4.1.1182.3.1.4 | R/O | Gauge (0..100) | Memory usage ratio |
| yshCpuUtil5sec | 1.3.6.1.4.1.1182.3.1.5 | R/O | Gauge (0..100) | CPU usage ratio (5-second average) |
| yshCpuUtil1min | 1.3.6.1.4.1.1182.3.1.6 | R/O | Gauge (0..100) | CPU usage ratio (1-minute average) |
| yshCpuUtil5min | 1.3.6.1.4.1.1182.3.1.7 | R/O | Gauge (0..100) | CPU usage ratio (5-minute average) |
5.2 yamahaSWFirmware group
This MIB is related to firmware information for Yamaha switches.
yamahaSWFirmware group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| ysfConfigFile | 1.3.6.1.4.1.1182.3.2.2 | R/O | DisplayString (SIZE (0..255)) | Startup config | ||
| ysfRevision | 1.3.6.1.4.1.1182.3.2.3 | R/O | DisplayString (SIZE (0..255)) | Firmware version | ||
| ysfUpTime | 1.3.6.1.4.1.1182.3.2.4 | R/O | TimeTicks | Elapsed time from boot | ||
| ysfRestart | 1.3.6.1.4.1.1182.3.2.11 | R/W | INTEGER ・nothing(1) ・restart(2) | The system will reboot when the “restart” value is written | ||
5.3 yamahaSWL2ms group
This MIB is related to L2MS information for Yamaha switches.
yamahaSWL2ms group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| ysl2msNumber | 1.3.6.1.4.1.1182.3.5.1 | N/A | INTEGER | Number of switches that can be recognized Note: Used only with trap notifications | ||
| ysl2msEnableTrap | 1.3.6.1.4.1.1182.3.5.2 | R/W | INTEGER ・enabled(1) ・disabled(2) | Setting value for determining whether SNMP traps due to L2MS information are notified | ||
| ysl2msTable | 1.3.6.1.4.1.1182.3.5.3 | N/A | Table of information for devices connected via L2MS | |||
| ysl2msEntry | 1.3.6.1.4.1.1182.3.5.3.1 | N/A | INDEX ・ysl2msIndex | |||
| ysl2msIndex | 1.3.6.1.4.1.1182.3.5.3.1.1 | N/A | DisplayString (SIZE (0..6)) | MAC address of device Note: Used only with trap notifications | ||
| ysl2msProduct | 1.3.6.1.4.1.1182.3.5.3.1.2 | N/A | INTEGER ・generic(1) | Model of device Note: Used only with trap notifications | ||
| ysl2msPhysAddress | 1.3.6.1.4.1.1182.3.5.3.1.5 | N/A | DisplayString (SIZE (0..6)) | MAC address of device Note: Used only with trap notifications | ||
| ysl2msRoute | 1.3.6.1.4.1.1182.3.5.3.1.11 | N/A | DisplayString (SIZE (0..64)) | Route information to device Note: Used only with trap notifications | ||
5.4 yamahaSWErrDisable group
This MIB is related to error detection function information for Yamaha switches.
yamahaSWErrDisable group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| ysedConfigTable | 1.3.6.1.4.1.1182.3.6.1 | N/A | Table of setting information for the error detection function | |||
| ysedConfigEntry | 1.3.6.1.4.1.1182.3.6.1.1 | N/A | INDEX ・ysedConfigIndex | |||
| ysedConfigIndex | 1.3.6.1.4.1.1182.3.6.1.1.1 | N/A | INTEGER (1..2147483647) | Table index Corresponds to the ysedConfigFunction value | ||
| ysedConfigFunction | 1.3.6.1.4.1.1182.3.6.1.1.2 | R/O | INTEGER ・bpduguard(1) ・loopdetect(2) | Functions that are enabled for error detection | ||
| ysedConfigAutoRecovery | 1.3.6.1.4.1.1182.3.6.1.1.3 | R/W | INTEGER ・enabled(1) ・disabled(2) | Setting for automatic recovery from Error Disable state | ||
| ysedConfigRecoveryInterval | 1.3.6.1.4.1.1182.3.6.1.1.4 | R/W | INTEGER (10..1000000) | Frequency (seconds) at which to attempt automatic recovery from Error Disable state | ||
| ysedEnableTrap | 1.3.6.1.4.1.1182.3.6.2 | R/W | INTEGER ・enabled(1) ・disabled(2) | Setting value for determining whether SNMP traps due to error detection functions are notified | ||
| ysedIfTable | 1.3.6.1.4.1.1182.3.6.3 | N/A | Table of information for the error detection function | |||
| ysedIfEntry | 1.3.6.1.4.1.1182.3.6.3.1 | N/A | INDEX ・ysedIfIndex | |||
| ysedIfIndex | 1.3.6.1.4.1.1182.3.6.3.1.1 | N/A | INTEGER (1..2147483647) | Interface index | ||
| ysedIfStatus | 1.3.6.1.4.1.1182.3.6.3.1.2 | R/O | INTEGER ・normal(1) ・bpduguard(2) ・loopdetect(3) ・portsecurity(4) | Error Disable state of port | ||
5.5 yamahaSWRmon group
This MIB is related to RMON information for Yamaha switches.
yamahaSWRmon group
| MIB name | OID | Access | Syntax | Description |
|---|---|---|---|---|
| ysrmonSetting | 1.3.6.1.4.1.1182.3.7.1 | R/W | INTEGER ・enabled(1) ・disabled(2) | Enabled/disabled setting of RMON function |
| ysrmonEnableTrap | 1.3.6.1.4.1.1182.3.7.2 | R/W | INTEGER ・enabled(1) ・disabled(2) | Setting value for determining whether SNMP traps due to RMON functions are notified |
5.6 yamahaSWTermMon group
This MIB is related to terminal monitoring information for Yamaha switches.
yamahaSWTermMon group
| MIB name | OID | Access | Syntax | Description | ||
|---|---|---|---|---|---|---|
| ystmEnableTrap | 1.3.6.1.4.1.1182.3.8.1 | R/W | INTEGER ・enabled(1) ・disabled(2) | Setting value for determining whether SNMP traps due to terminal monitoring functions are notified | ||
| ystmIfTermTable | 1.3.6.1.4.1.1182.3.8.3 | N/A | Table of terminal monitoring functions targeted at ports | |||
| ystmIfTermEntry | 1.3.6.1.4.1.1182.3.8.3.1 | N/A | INDEX ・ystmIfTermIndex | |||
| ystmIfTermIndex | 1.3.6.1.4.1.1182.3.8.3.1.1 | N/A | INTEGER (1..2147483647) | ifIndex Note: Used only with trap notifications | ||
| ystmIfTermDescr | 1.3.6.1.4.1.1182.3.8.3.1.2 | N/A | DisplayString (SIZE (0..255)) | Terminal monitoring description Note: Used only with trap notifications | ||
| ystmIfTermStatus | 1.3.6.1.4.1.1182.3.8.3.1.3 | N/A | INTEGER ・up(1) ・down(2) ・idle(3) | Terminal monitoring status Note: Used only with trap notifications | ||
| ystmIpTermTable | 1.3.6.1.4.1.1182.3.8.4 | N/A | Table of terminal monitoring functions targeted at IP addresses | |||
| ystmIpTermEntry | 1.3.6.1.4.1.1182.3.8.4.1 | N/A | INDEX ystmIpTermIndex | |||
| ystmIpTermIndex | 1.3.6.1.4.1.1182.3.8.4.1.1 | N/A | IpAddress | IP address of monitored target Note: Used only with trap notifications | ||
| ystmIpTermDescr | 1.3.6.1.4.1.1182.3.8.4.1.2 | N/A | DisplayString (SIZE (0..255)) | Terminal monitoring description Note: Used only with trap notifications | ||
| ystmIpTermStatus | 1.3.6.1.4.1.1182.3.8.4.1.3 | N/A | INTEGER ・up(1) ・down(2) ・idle(3) | Terminal monitoring status Note: Used only with trap notifications | ||
5.7 yamahaSWBridge group
This MIB is related to dot1dBridge information for Yamaha switches.
yamahaSWBridge group
| MIB name | OID | Access | Syntax | Description |
|---|---|---|---|---|
| ysbridgeEnableTrap | 1.3.6.1.4.1.1182.3.9.1 | R/W | INTEGER ・enabled(1) ・disabled(2) | Setting value for determining whether SNMP traps due to dot1dBridge information are notified |
6 Standard MIB traps
Standard MIB traps that are supported by this product are shown below.
6.1 Traps defined by RFC1157
These are traps defined by RFC1157.
List of traps defined by RFC1157
| Trap name | OID | Additional information for trap (variable-bindings) | Description |
|---|---|---|---|
| coldStart | 1.3.6.1.6.3.1.1.5.1 | None | Notification on power OFF/ON and during firmware updates |
| warmStart | 1.3.6.1.6.3.1.1.5.2 | None | Notification while the reload command is being executed |
| linkDown | 1.3.6.1.6.3.1.1.5.3 | ifIndex ifAdminStatus ifOperStatus | Notification during linkdown |
| linkUp | 1.3.6.1.6.3.1.1.5.4 | ifIndex ifAdminStatus ifOperStatus | Notification during linkup |
| authenticationFailure | 1.3.6.1.6.3.1.1.5.5 | None | Notification when receiving an SNMP message that has an incorrect community name |
6.2 rmon group trap
This trap is related to RMON information.
rmon group trap list
| Trap name | OID | Additional information for trap (variable-bindings) | Description |
|---|---|---|---|
| risingAlarm | 1.3.6.1.2.1.16.0.1 | alarmIndex alarmVariable alarmSampleType alarmValue alarmRisingThreshold | Notification that upper threshold value has been exceeded |
| fallingAlarm | 1.3.6.1.2.1.16.0.2 | alarmIndex alarmVariable alarmSampleType alarmValue alarmFallingThreshold | Notification that lower threshold value has been exceeded |
6.3 dot1dBridge group trap
This trap is related to dot1dBridge information.
dot1dBridge group trap list
| Trap name | OID | Additional information for trap (variable-bindings) | Description |
|---|---|---|---|
| newRoot | 1.3.6.1.2.1.17.0.1 | None | Notification that a new root for bridge has been detected |
| topologyChange | 1.3.6.1.2.1.17.0.2 | None | Notification that a change in topology has been detected |
7 Private MIB traps
The private MIB traps that are supported by this product are shown below.
7.1 yamahaSWL2ms group trap
This trap is related to L2MS information for Yamaha switches.
yamahaSWL2ms group trap list
| Trap name | OID | Additional information for trap (variable-bindings) | Description |
|---|---|---|---|
| ysl2msFindSlave | 1.3.6.1.4.1.1182.3.5.0.1 | ysl2msNumber ysl2msProduct ysl2msPhysAddress ysl2msRoute | Notification when L2MS slave is detected |
| ysl2msDetectDown | 1.3.6.1.4.1.1182.3.5.0.2 | ysl2msNumber ysl2msProduct ysl2msPhysAddress ysl2msRoute | Notification when L2MS slave is lost |
7.2 yamahaSWErrDisable group trap
This trap is related to error detection function information for Yamaha switches.
yamahaSWErrDisable group trap list
| Trap name | OID | Additional information for trap (variable-bindings) | Description |
|---|---|---|---|
| ysedTrap | 1.3.6.1.4.1.1182.3.6.0.1 | ysedIfStatus | Notification when ErrorDisable is detected/cancelled |
7.3 yamahaSWTermMon group trap
This trap is related to terminal monitoring information for Yamaha switches.
yamahaSWTermMon group trap list
| Trap name | OID | Additional information for trap (variable-bindings) | Description |
|---|---|---|---|
| ystmIfTermTrap | 1.3.6.1.4.1.1182.3.8.0.1 | ystmIfTermDescr ystmIfTermStatus | Notification when terminal monitoring is detected |
| ystmIpTermTrap | 1.3.6.1.4.1.1182.3.8.0.2 | ystmIpTermDescr ystmIpTermStatus | Notification when IP address terminal monitoring is detected |
- SWR2310 Series Technical Data (Basic Functions)
- Other information
- About the licenses
About the licenses
Open-source software used in this product
- For information about the license provisions, visit the Yamaha Pro Audio website.
- SWR2310 Series Technical Data (Basic Functions)
- Other information
- Google Analytics
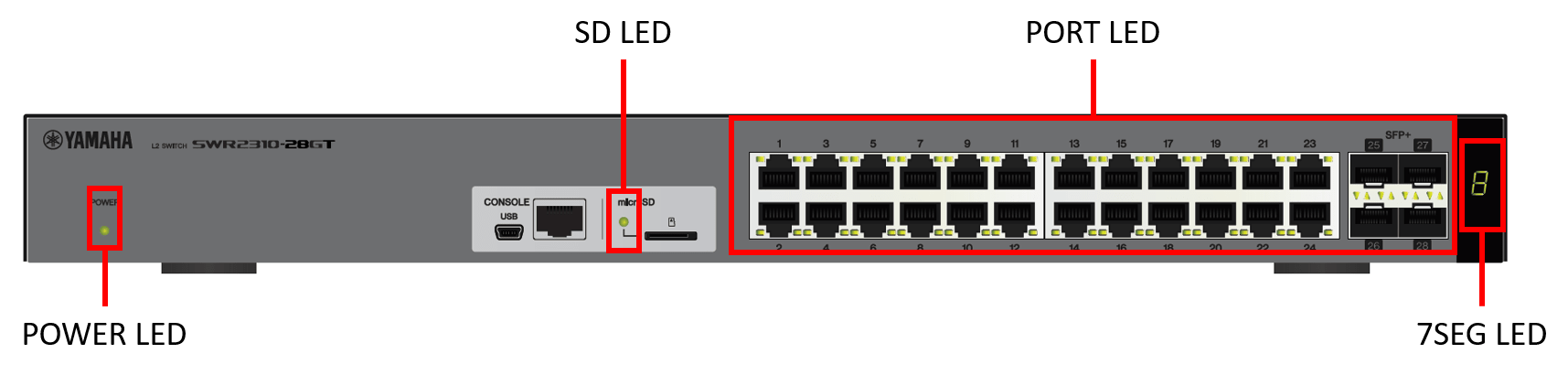

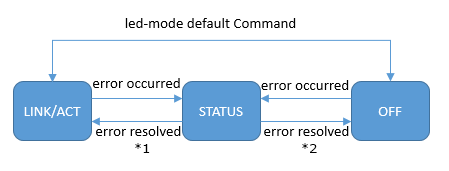

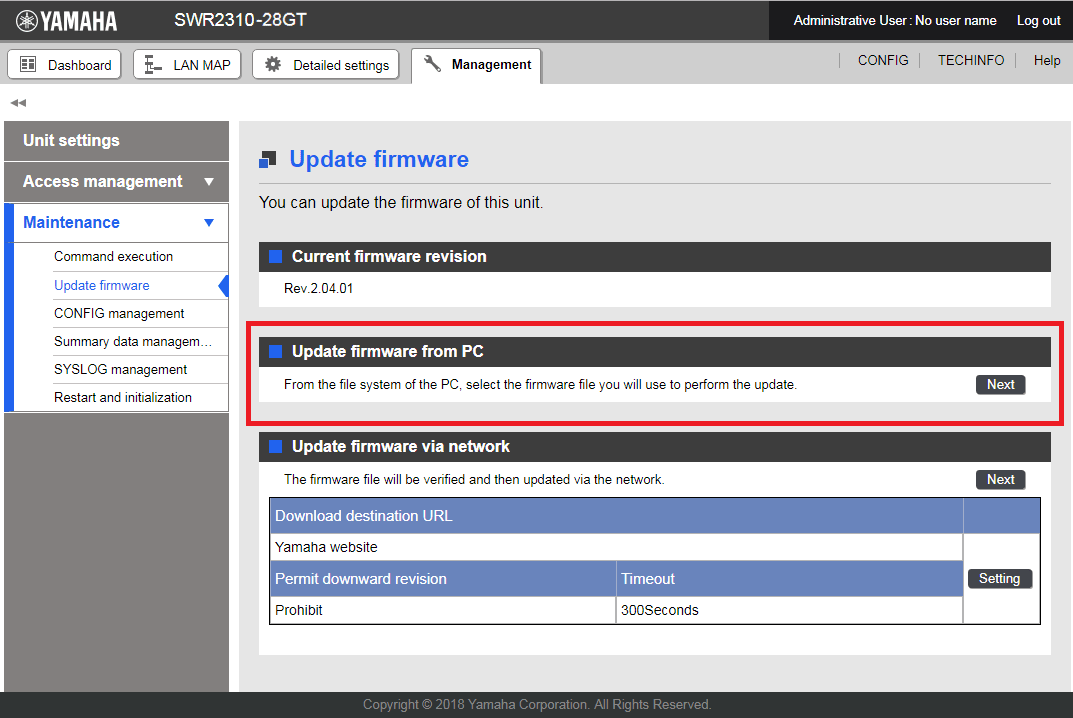





 ), and then make a selection in the following screen.
), and then make a selection in the following screen.